
We often write in our Breaking Scams section about phishing emails. They are almost always scams containing a malicious link. This week’s scam is a malicious attachment instead of a link. The end result of infected attachment scams is the same as their malicious link cousins; you’ll be phished for login credentials or other data and/or you’ll be infected with malware. This week’s scam is much of the same but with some slight variations.
What the employee benefits scam looks like
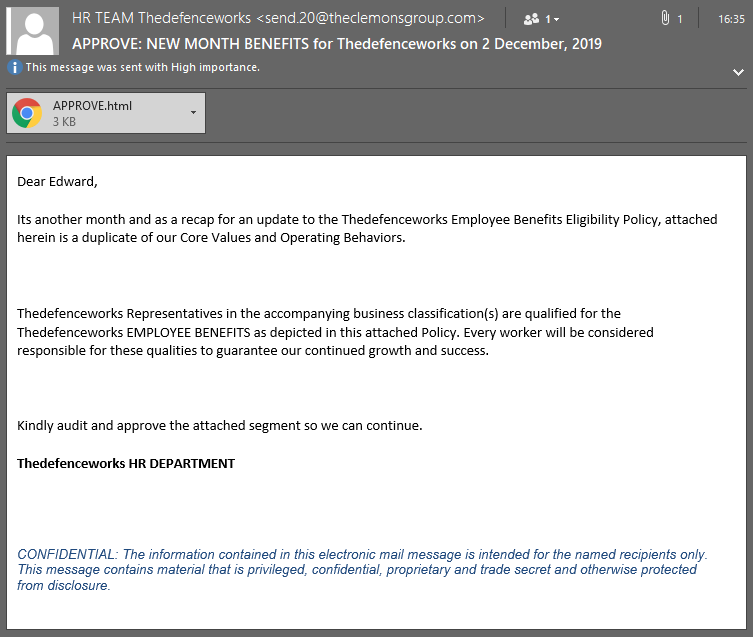
The scam arrived in email form. It was said to be from The Defence Works HR Team. The email required that the recipient download the HTML attachment which contained details of a new employee benefits policy.
This is a typical behaviour manipulation tactic. The hope is the recipient thinks,
“oooo benefits, for me, let’s see”
Use of the “HR Department” and a setting of “High Importance” is part of the overall scam to build trust and urgency that the message could be real and important.
How did I know it was a scam?
HR Department-based scams are fairly common. This usually means that they have a good success rate, so be wary – sorry HR staff. However, there are signs that should jump out at you to make you wary of these types of emails.
Besides the fact that this was sent to The Defence Works Managing Director, who knew that he had not authorised such an email, there were other tell-tale signs this was a phishing email:
- The ‘from’ email address was highly suspicious and not a The Defence Works email address.
- The company’s name “The Defence Works” was formatted incorrectly. The email referred to “Thedefenceworks”. This is likely because the email was automatically generated, taking the domain from the email address and parsing it into the email body content.
- The grammar was poor, our HR department would never send out an email with “Its another month”, forgetting the all-important apostrophe. Nor would they use superfluous words like ‘herein’. Just sayin’…
What was in the malicious attachment?
HTML attachments are being used increasingly in phishing scams. The reason being they can very cleverly circumvent security tools like spam filters, URL reputation checkers, and anti-malware. When a recipient opens the HTML form, it converts to a webpage that is hosted on the device and not a web server. The page has an external URL that it links to.
The form asks you to enter various personal data. Once entered, there is a submit button. If the recipient enters their data and clicks submit, the data is sent to the fraudster behind the scam to commit identity fraud.
How to stop being scammed
Cybercriminals are cunning. They work tirelessly to find workarounds to our security tools and to find ways to manipulate us into doing their bidding. Whilst security tools are important, you need to also use a mix of security awareness with good technology. Your user behaviour is your front-line defence and your fall-back position; use security awareness training to help stop cybercriminals scamming your staff.
Why not help your colleagues stay safe and send them this little reminder. Feel free to edit, copy/paste the advice below:
Employee Benefits Malicious Attachment Scam
You may receive an email that looks like it is from your HR Department talking about employee benefits. The email contains an HTML attachment. Be wary, this email may be a phishing attempt.
DO NOT OPEN THE HTML ATTACHMENT. IF YOU DO, DO NOT ENTER ANY PERSONAL DATA AND CLICK THE SUBMIT BUTTON
For more information on what to do if you receive a phishing email check out “What to Do if you receive a phishing email?”
Don’t forget to share this with your colleagues and friends and help them stay safe.
Let’s keeping breaking scams!











