Key takeaways
- ThreatFlip is a one-click, AI-powered phishing simulation workflow.
- It creates phishing lures based on real-world threats, transforming them into safe, ready-to-use templates.
- Sensitive information and PII are automatically removed for privacy and compliance.
- Teachable Moments enhance learner training and improve phishing detection skills.
Security teams know that phishing remains one of the most persistent and effective attack vectors. That’s not because defenses don’t exist—it’s because attackers continuously adapt how they target people.
Every day, security operations center (SOC) teams detect and investigate highly tailored phishing emails that are aimed at roles such as human resources (HR), finance, and IT help desks. These roles are targeted by threat actors because they have access to critical data and critical systems.
The job for the analyst is to identify malicious messages, understand the threat, and reduce risk as quickly as possible. At the same time, security awareness and human risk management teams are under pressure to prepare employees to recognize and respond to those same attacks. Their job is to deliver timely, relevant training that actually helps change behavior.
The challenge is the jobs to be done for analysts and the risk management teams rarely connect through a single, integrated workflow. And that lack of connection results in inefficient manual processes, poor alignment, and extended execution timelines. As a result, it can take days to generate content that positively impacts employees and security resilience across the organization.
Proofpoint’s AI ThreatFlip Workflow can help. Built into the Proofpoint Collaboration Security Prime platform, ThreatFlip enables teams to create phishing lures that are based on real-world threats with just one click. So, training content is both timely and relevant.
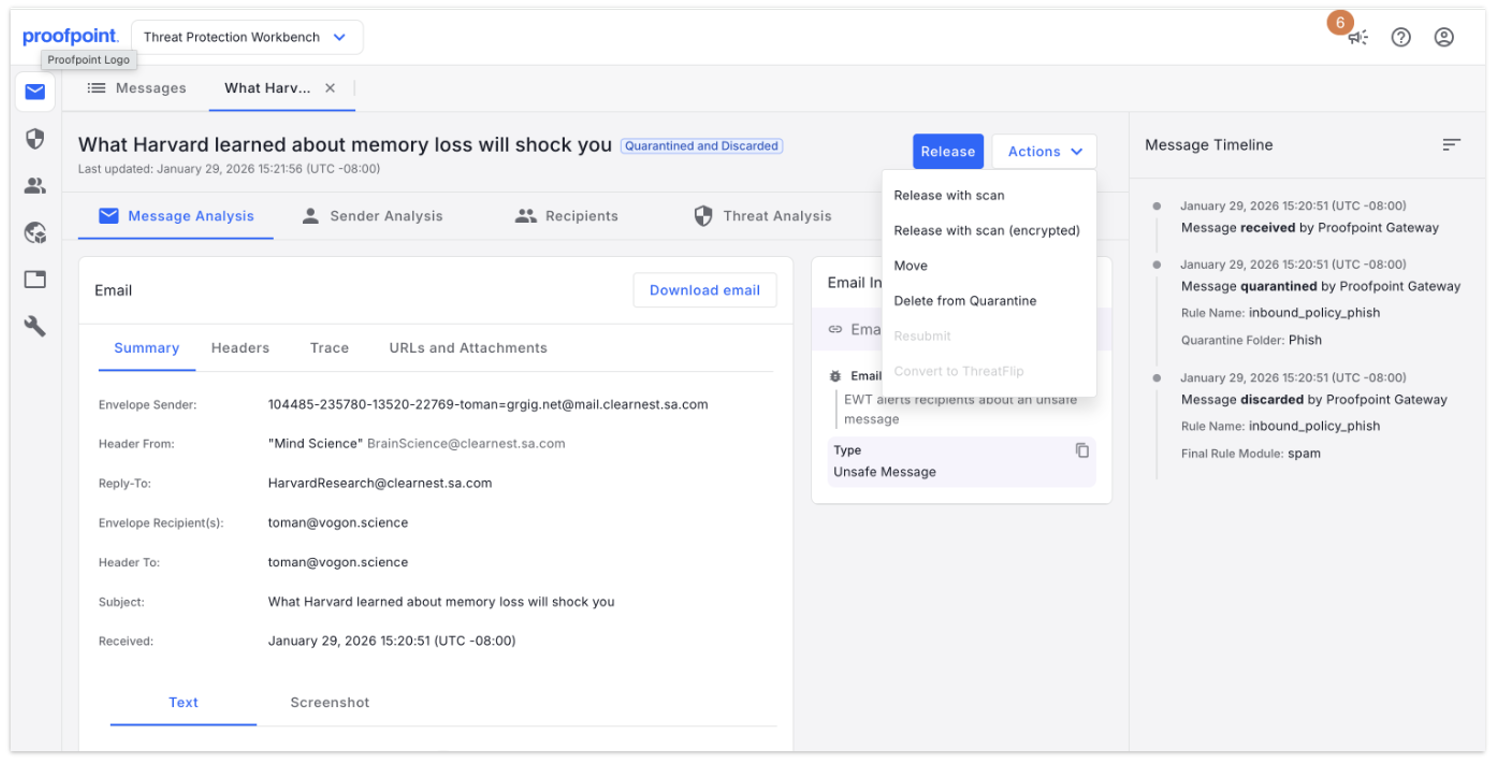
Figure 1. AI ThreatFlip Workflow transforms malicious emails into phishing simulations.
The gap between detection and readiness
Phishing attacks are constantly evolving. Threat actors may not change their target, but they will certainly change the type of attack they are using. Many organizations today are struggling to detect and stop phishing attacks. The challenge isn’t just visibility—it’s what happens next.
In environments without an integrated collaboration security solution, turning a real phishing attack into training is a highly manual, cross-team process. SOC and security awareness teams often rely on ad hoc coordination to bridge the gap between detection and education.
A typical process may look like this:
- The SOC team detects or investigates a phishing email.
- Threat context—such as lures, language, and intent—is manually documented.
- Meetings are scheduled between teams that don’t regularly work together.
- The security awareness team recreates the email as a safe simulation, removes malicious elements, and builds training content from scratch.
Each step creates more delay and friction. And context can be lost in translation. By the time training is delivered, employees may already have been exposed to similar attacks.
While both teams are working toward the same goal—reducing human risk—the lack of an integrated workflow slows response. What’s more, it consumes valuable time and makes it difficult to deliver training while an attack pattern is still active.
That gap—between live threat detection and employee readiness—is where risk persists.
Connecting the jobs to be done
At its core, the problem isn’t effort or intent. It’s workflow alignment.
- SOC team. For the security analyst who’s looking for a fast, low-friction way to share email phishing insights, ThreatFlip automates the process. It eliminates manual intervention and effectively removes the communication silo.
- Security awareness team. For the security awareness practitioner who needs realistic, ready-to-use simulations—without waiting days or rebuilding emails manually—ThreatFlip provides lightning-fast delivery of phishing templates.
Without automation, SOC teams become intermediaries and awareness teams become threat translators. Valuable time is spent coordinating work outside each team’s core responsibilities.
AI ThreatFlip workflow was designed to eliminate these handoffs entirely.
What is AI ThreatFlip workflow?
AI ThreatFlip workflow is a one-click, AI-powered phishing simulation workflow that seamlessly connects SOC and security awareness teams.
- For the SOC team, the job is simple: select a real phishing email that’s been detected and with the click of a button move it into the ThreatFlip workflow. From there, AI handles the rest.
- For the security awareness team, ThreatFlip automatically transforms the malicious email into a safe, sanitized and customizable phishing simulation template that’s ready to use.
Instead of downloading suspicious emails, manually recreating templates, scrubbing malicious content, and coordinating handoffs, the entire process is automated. This allows each team to stay focused on what they do best.
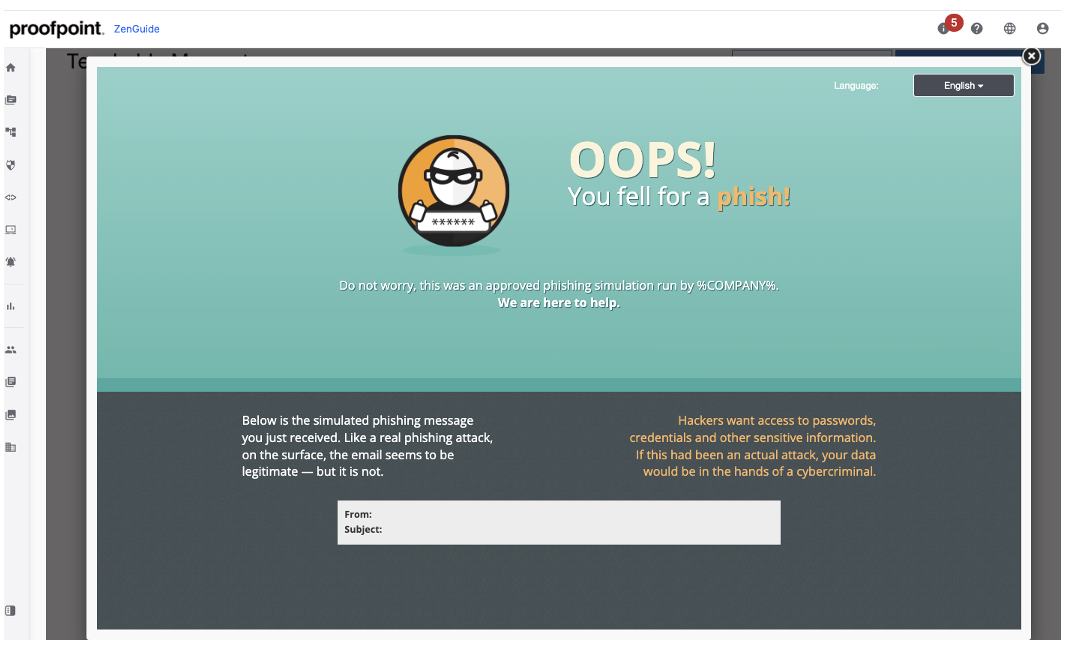
Figure 2. AI Phish Hooks generates Teachable Moments to help users improve detection skills.
How ThreatFlip works
- Clones real phishing emails received by your organization to preserve authentic structure, tone, and context
- Removes malicious elements to ensure simulations are safe and non-operational
- Automatically identifies and highlights phish hooks, which are email cues such as a sense of urgency or emotional triggers based on the categories in the NIST Phish Scale
- Strengthens engagement using AI suggested Phish Hooks to provide in-the-moment teachable experiences, when users interact with simulations
For the security awareness team all of this happens with a single action. No manual customization. No template rebuilding. No delays.
The result is phishing training content that looks and feels like the attacks your users are most likely to face—because it’s based on those exact threats.
From manual effort to operational efficiency
Traditionally, teams spend significant manual effort on creating effective phishing simulations. The challenge is that the work of the SOC and security awareness training teams happens in silos. This results in poor communication, wasted effort, and lost time, which adversely impacts the organization’s security resilience program.
AI ThreatFlip workflow collapses this process.
By automating the transformation of real phishing attacks into training simulations, organizations can move from detection to deployment in hours rather than days—without sacrificing realism or safety.
As a result, the SOC team no longer acts as an intermediary or gets pulled into manual template creation processes. And the security awareness team gets realistic, ready-to-use phishing templates without delay.
ThreatFlip allows both teams to focus on higher-value work, such as investigating threats, optimizing training programs, and strengthening organizational resilience.
Training that mirrors how attackers operate
Modern phishing attacks are rarely one-size-fits-all. As previously noted, threat actors tailor messages based on department, role, and business context:
- HR teams receive messages related to benefits, hiring, or internal policy.
- Finance teams see invoice fraud and payment requests.
- Help desk and IT staff are targeted with credential and access-based lures.
AI is being used by threat actors every day to scale their phishing attacks. They use it to analyze public data so they can quickly identify employee roles, relationships, and business scenarios. Based on their research, they use AI to generate personalized phishing attacks that mimic trusted senders. For threat actors, AI provides infinite scale that enables them to launch highly targeted campaigns while continuously testing and iterating to improve their success rates.
Generic phishing simulations fail to capture these nuances. ThreatFlip changes that by enabling organizations to repurpose real attacks—safely—across similar roles or departments.
For example, a phishing email that targets an HR employee can quickly be converted into a simulation that trains other HR staff. The same approach applies to finance, healthcare operations, retail environments, or enterprise IT teams.
By mirroring real-world lures, language, and tactics, ThreatFlip increases relevance—and relevance is what drives behavior change.
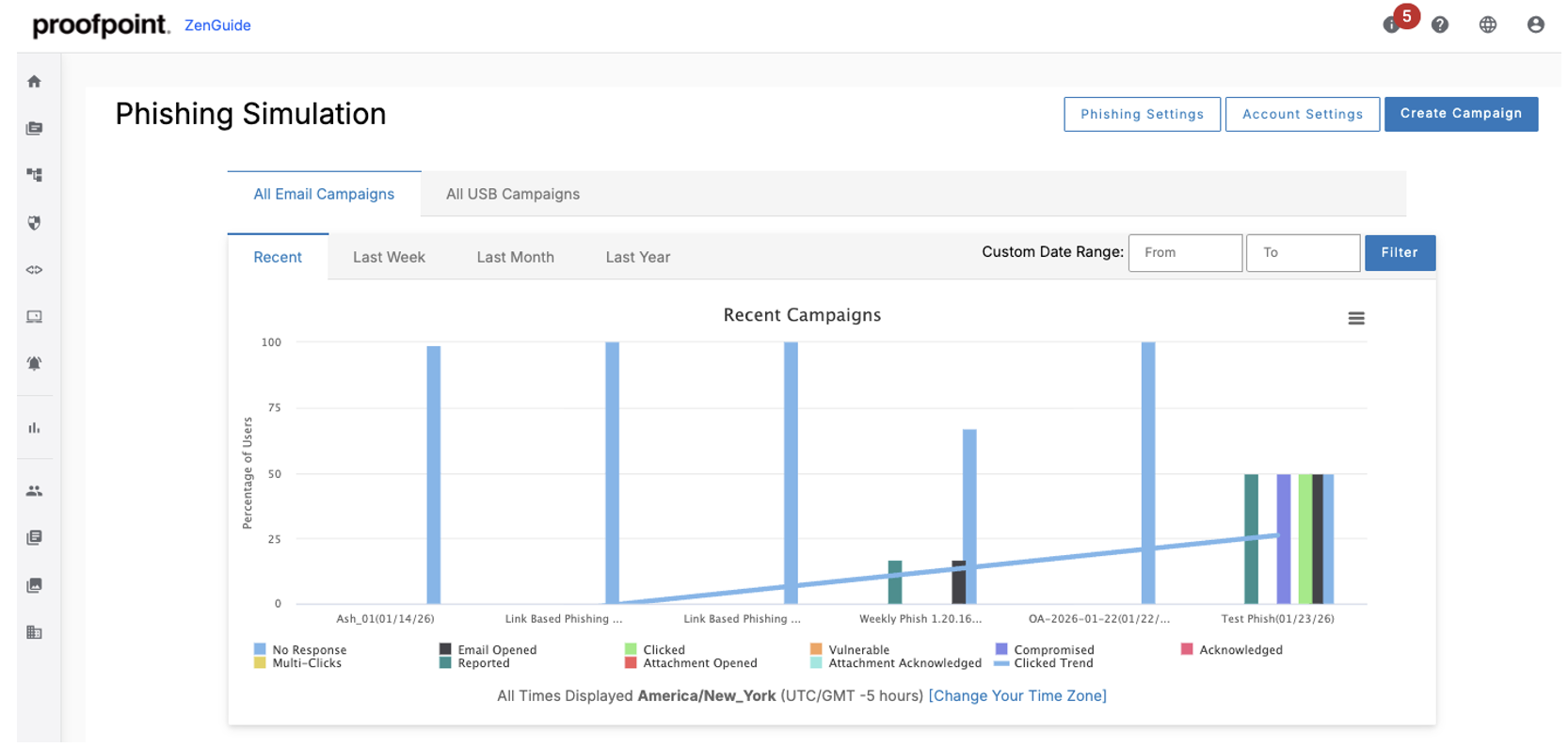
Figure 3. The Phishing Simulation dashboard provides immediate visibility to assess your phishing campaigns.
Addressing common concerns head-on
Security leaders are understandably cautious when it comes to automation and AI, especially when real threat data is involved. ThreatFlip was designed with these concerns in mind.
Is this safe?
Yes. ThreatFlip removes malicious payloads and strips personally identifiable information (PII) before simulations are created. Templates are safe representations, not live threats.
Can AI-generated simulations be trusted?
ThreatFlip doesn’t invent scenarios. It starts with real phishing emails that are detected in your environment, preserving authenticity while removing risk.
Does this add complexity to SOC workflows?
No. It removes complexity by eliminating manual handoffs and coordination. The workflow is initiated with a single click.
How is sensitive data handled?
Sensitive information and PII are automatically removed as part of the transformation process to ensure privacy and compliance.
Built with human oversight and threat intelligence
ThreatFlip is powered by AI, but it isn’t unsupervised. It’s built with human oversight and aligned with Proofpoint’s threat intelligence and security controls.
Outputs are validated by teams responsible for quality assurance, threat research, product security, and infrastructure reliability. This ensures that simulations are accurate, safe, and operationally sound.
For CISOs and security leaders, this balance between automation and governance is critical—and central to how ThreatFlip was designed.
Turning threat intelligence into measurable behavior change
Ultimately, the goal of phishing simulations isn’t to catch employees—it’s to help them recognize and respond to real threats more effectively.
By transforming live attacks into training experiences, ThreatFlip helps organizations:
- Shorten the gap between threat detection and employee readiness
- Increase awareness using attacks that employees are most likely to encounter
- Strengthen resilience through realistic, role-relevant simulations
- Drive measurable behavior change using real-world threat data
This approach moves security awareness from static training to a dynamic, intelligence-driven discipline.
See AI ThreatFlip Workflow in action
ThreatFlip is a powerful, integrated capability within Proofpoint Collaboration Security Prime—a unified platform that shares threat intelligence across security teams and streamlines day-to-day operations.
If you’re an existing customer using Proofpoint Core Email Protection and Proofpoint ZenGuide you can take advantage of ThreatFlip today. For customers with only Core Email Protection or ZenGuide, ThreatFlip is yet another compelling reason to upgrade and unlock the full value of our integrated platform.
To learn more about driving real behavior change—and see how ThreatFlip transforms real phishing attacks into effective, timely training—visit the Proofpoint ZenGuide page.
To explore how Proofpoint helps secure trusted interactions across multiple channels and stages of an attack, check out the Proofpoint Collaboration Security Prime page.











