According to Verizon’s 16th annual Data Breach Investigation Report (DBIR), business email compromise (BEC) is the largest cybersecurity threat to companies today. And data from the recent FBI Internet Crime Complaint Center report backs this up. The FBI found that last year companies lost more than $2.7 billion due to BEC scams alone.
The 2023 Verizon DBIR dataset analyzed 16,312 security incidents that occurred across more than 20 industries worldwide. Of those incidents, Verizon confirmed that 5,199 were data breaches.
Here are the top three takeaways from the latest Verizon DBIR report, which provides insight into BEC, social engineering and other industry trends.
Takeaway #1: Socially engineered BEC attacks are on the rise
Over the past few years, socially engineered BEC attacks have been steadily on the rise. The 2023 DBIR report highlights that this trend is shows no signs of slowing down. In fact, BEC attacks doubled over the past year, representing nearly 60% of social engineering incidents.
A BEC attack involves a threat actor using email or an email campaign to steal money or gain access to sensitive company information. BEC attacks typically don’t use malicious URL links or attachments to deliver their dangerous payloads. This makes them exceedingly difficult to detect, mitigate and remove with simple, email security add-on solutions. And that’s why businesses are vulnerable to these types of attacks.
Cyber criminals have a wide array of tools and methods at their disposal to attack businesses. Yet, they tend to prefer a “tried and tested” approach: social engineering. Social engineering attacks exploit the tendency for humans to trust each other. Attackers manipulate, build trust and create a sense of urgency to trick users into making security mistakes or giving away sensitive data.
Social engineering attacks come in various forms. But they always involve interacting with people. Common attacks include:
- Baiting
- Scareware
- Pretexting
- Phishing
- Spear phishing
In the past year, Verizon found that pretexting based BEC attacks have almost doubled across the globe. Pretexting is one of the most popular social engineering tactics. In this type of attack, a cyber criminal gets a user to reveal sensitive information through a series of cleverly crafted lies.
This scam often starts with an attacker pretending to be an executive, coworker or other authorized person who needs sensitive information from the user to do a specific or critical task. The attacker starts to establish trust with the user by asking them personal questions that confirm the user’s identity, like their Social Security number, personal address or phone number.
The Verizon DBIR notes that these attacks now represent more than 50% of all social engineering incidents. The median loss for each incident is more than $50,000. A related fact: financial motives drive a whopping 94.6% of all breaches.
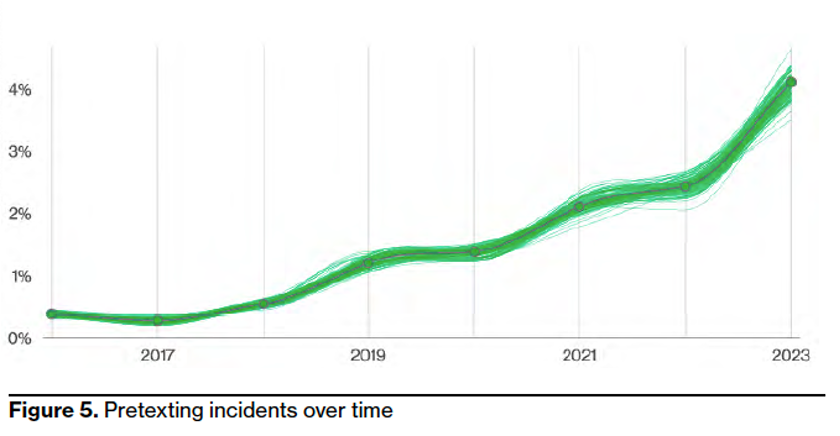
Pretexting incidents over time, from 2016-2023. (Source: 2023 Verizon DBIR.)
One of the reasons threat actors are so successful with pretexting is that businesses simply aren’t prepared to stop them. Many email security add-on solutions are not very effective when it comes to identifying, blocking and remediating BEC emails. And that includes supplier threats, impersonation and telephone-oriented attack delivery (TOAD) attacks.
Takeaway #2. Threat actors continue to target and exploit people
Threat actors don’t want to break into your company—they want to log into it. This is the primary reason cyber criminals are targeting and exploiting the weakest link in your security infrastructure: your people.
While your security and risk professionals build and deploy more complex security defenses, your employees are under siege. Users need to be right 100% of the time when encountering different types of email attacks. One misstep, and your business could be the next data breach headline.
Last year, most data breaches involved the human element or some type of human error, privilege misuse, compromised credentials, or individuals falling victim to social engineering attacks. Verizon reports that 74% of data breaches include the human element.
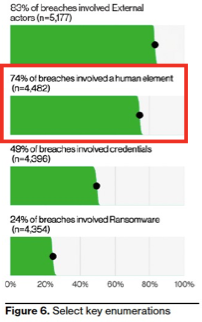
Most data breaches (74%) include the human element. (Source: 2023 Verizon DBIR.)
Proofpoint is different from mere add-on solutions for email security. We have more than 20 years of experience contextually analyzing identify threats, which means we can stop threats fast. Our threat detection engines use artificial intelligence and machine learning to analyze data that we collect from our deployments around the globe at a massive scale. On a daily basis, we analyze 2.6 billion email messages, 49 billion URLs, 1.9 billion attachments, 28 million cloud accounts, 1.7 billion suspicious SMS and more. Together, this amounts to trillions of data points across all digital channels. As a result, we are able to identify today’s most advanced email threats, including BEC, social engineering attacks and compromised identities.
The recent Proofpoint 2023 Human Factor report confirms Verizon’s findings that we have an “identity crisis.” In our research for this year’s Human Factor report, we found that “as many as 40% of shadow administrator identities can be exploited in a single step, such as resetting a domain password to elevate privileges. And 13% of shadow admins were found to already have domain admin privileges.”
These findings show that there’s a critical need for robust security measures—like user awareness training and access controls—and other proactive strategies for detecting and mitigating threats. These can all help keep companies safe from data breaches, unauthorized access, and financial and reputational damage.
Takeaway #3. Stolen credentials and ransomware drive attackers’ access
Cyber criminals lean heavily on stolen or compromised credentials because they are easy to obtain. They can be bought off the dark web or acquired through poor user password hygiene, including password reuse over multiple applications (both business and personal).
The point is that threat actors want to take the easiest path to gain access to your company’s network. And that path most often involves exploiting stolen credentials. The Verizon DBIR report notes that stolen or compromised credentials are at the root of just over 50% of all breaches.
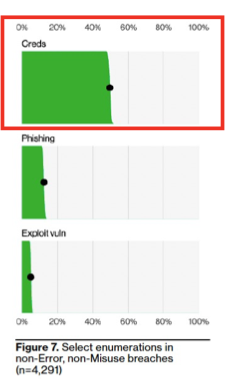
Stolen credentials are the primary method threat actors use to access a business. (Source: 2023 Verizon DBIR.)
Findings for the latest Verizon DBIR report show that ransomware continues its reign as one of the top action types present in breaches. Ransomware is responsible for 24% of all data breaches, the report says.
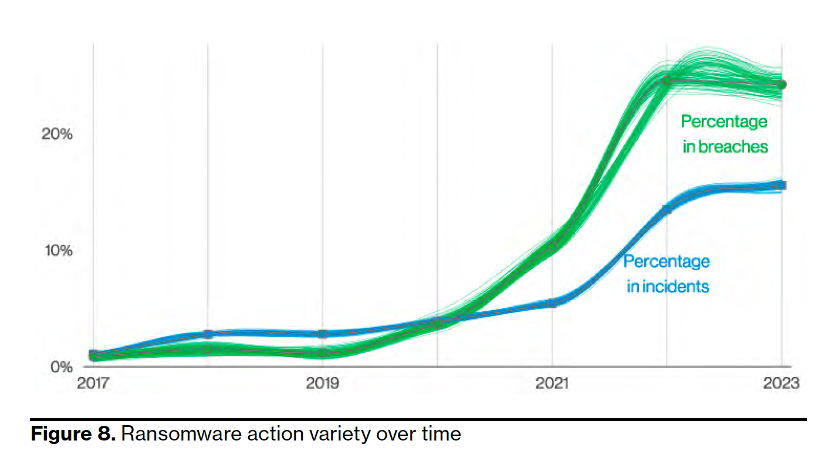
Ransomware is responsible for 24% of all data breaches. (Source: 2023 Verizon DBIR.)
Our 2023 State of the Phish report supports Verizon’s findings. Our research found that ransomware infections are widespread among companies of all sizes and in all industries. Last year, ransomware was so widely used and effective that 90% of companies affected by ransomware held a cyber insurance policy. And 64% of those infected by ransomware paid a ransom.
The key takeaway here is that threat actors use a potent one-two punch method (stolen credentials and ransomware) to gain access to business applications, systems and services.
Protect your business
Proofpoint provides a modern, end-to-end email security solution to help your company address sophisticated threats like BEC, social engineering and ransomware attacks. It’s time to break the attack chain and better protect your people and data. Visit our email fraud defense page to learn more. You can also take our free rapid risk assessment to understand your company’s preparedness for these types of attacks.
Never stop learning
Today’s threat landscape is dynamic and complex. To keep pace, you need to stay on top of the latest industry research. So, in addition to reviewing the latest DBIR report from Verizon, we encourage you to check these resources from Proofpoint.
- Proofpoint Named a Leader in the Forrester Wave: Enterprise Email Security, Q2, 2023 report
- Proofpoint 2023 Voice of the CISO report
- Proofpoint 2023 Human Factor report
- Proofpoint 2023 State of the Phish report
Contact us to find out more about how Proofpoint can help you to break the attack chain.











