Key takeaways
- Proofpoint threat researchers have recently uncovered an active account takeover (ATO) campaign, tracked as UNK_SneakyStrike, using the TeamFiltration pentesting framework to target Entra ID user accounts.
- Using a combination of unique characteristics, Proofpoint researchers were able to detect and track unauthorized activity attributed to TeamFiltration.
- According to Proofpoint findings, since December 2024 UNK_SneakyStrike activity has affected over 80,000 targeted user accounts across hundreds of organizations, resulting in several cases of successful account takeover.
- Attackers leverage Microsoft Teams API and Amazon Web Services (AWS) servers located in various geographical regions to launch user-enumeration and password-spraying attempts.
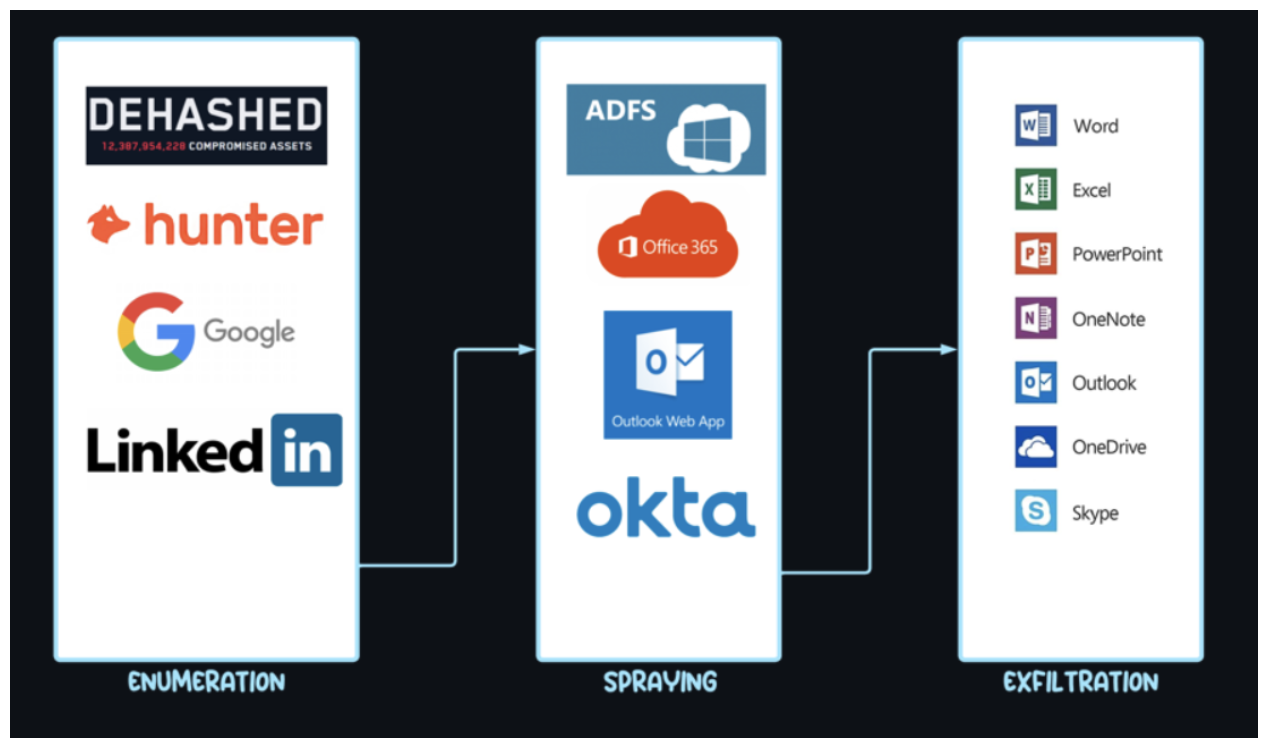
- Attackers exploited access to specific resources and native applications, such as Microsoft Teams, OneDrive, Outlook, and others.
Attack tool overview
Penetration testers and security experts continuously develop and share tools that simulate intrusions against cloud environments. One such tool, TeamFiltration, has gained significant traction since its release. It offers a robust framework for Office 365 Entra ID account takeover, data exfiltration, and persistent access.
Created by a threat researcher in January 2021 and publicly released at DefCon30, TeamFiltration helps automate several tactics, techniques, and procedures (TTPs) used in modern ATO attack chains. As with many security tools that are originally created and released for legitimate uses, such as penetration testing and risk evaluation, TeamFiltration was also leveraged in malicious activity.
Key features and capabilities
TeamFiltration provides multiple features, including:
- Account enumeration: Identifies valid user accounts within a target environment.
- Password spraying: Attempts to compromise accounts using common or systematically varied passwords.
- Data exfiltration: Extracts information such as emails, files, and other valuable data.
- “Backdooring” via OneDrive: Enables persistent access and potential lateral movement by uploading malicious files to the target’s OneDrive and replacing existing files (e.g., on the desktop) with lookalikes. These files can contain malware or macro-enabled payloads to re-establish access or further compromise targets.
Execution flow of TeamFiltration, as displayed on GitHub (github.com/Flangvik/TeamFiltration).
The hunt for TeamFiltration
In order to identify activities associated with TeamFiltration, Proofpoint threat researchers analyzed its publicly available GitHub documentation and default configuration file. This allowed us to find a distinctive user agent, linked to an outdated version of Microsoft Teams: (“Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Teams/1.3.00.30866 Chrome/80.0.3987.165 Electron/8.5.1 Safari/537.36”).
Since this user agent is rarely observed in the wild, researchers hypothesized that its appearance in legitimate environments which coincided with malicious activity could serve as an initial indicator that TeamFiltration was being used illegitimately.
In addition, Proofpoint threat researchers identified another unique indicator of TeamFiltration activity: attempted access to a specific sign-in application originating from devices incompatible with that application. This unexpected behavior indicates user agent spoofing and is meant to obfuscate the real client or device from which the intrusion originated.
Lastly, Proofpoint researchers analyzed the sign-in application affected by suspected TeamFiltration-driven targeting attempts. This revealed a clear correlation between observed ATO attempts and a distinct list of application IDs, which was pre-configured in TeamFiltration’s logic, according to its public code documentation. This choice of client applications is explained by the fact that they belong to a group of Microsoft OAuth client applications that can obtain special “family refresh tokens” from Entra ID. Those refresh tokens can then be exchanged for valid bearer tokens, like any other client in the family, and subsequently leveraged for access exploitation.
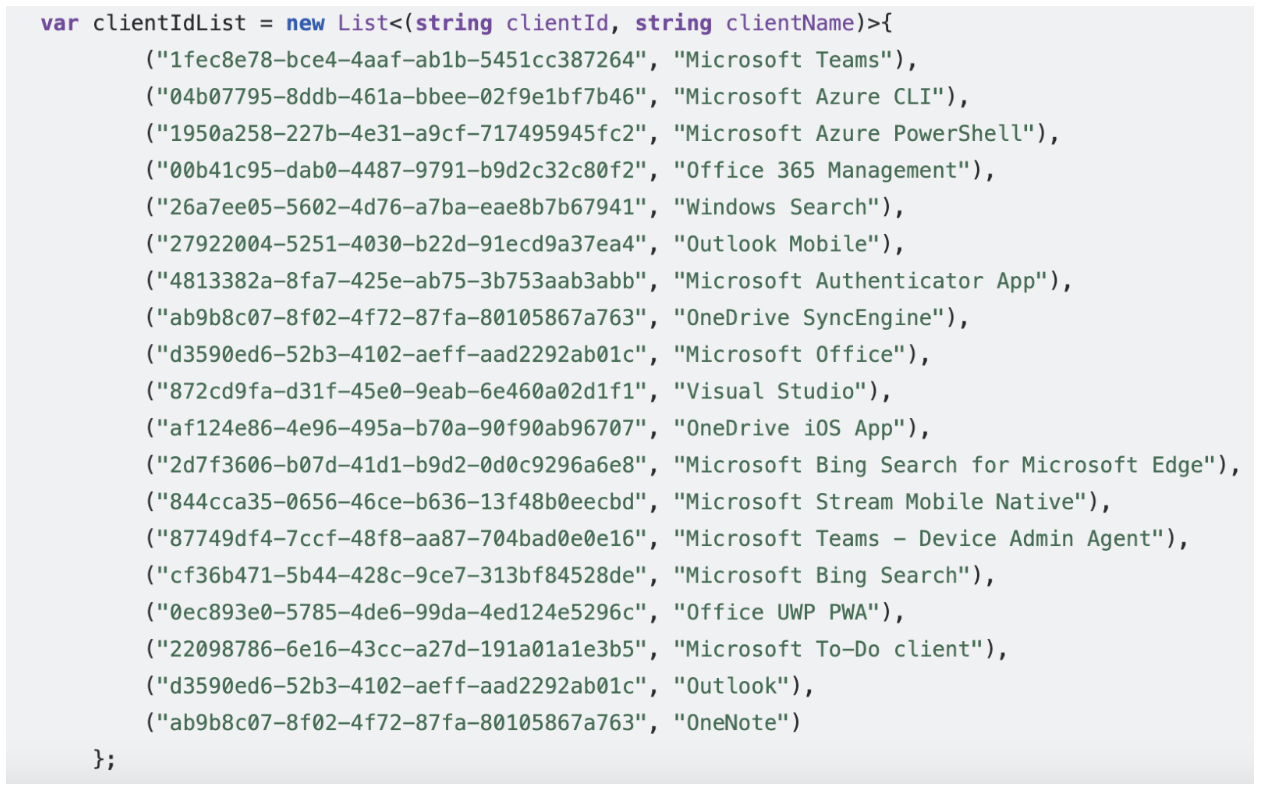
Snippet of TeamFiltration code displaying a list of client application IDs used in targeting.
However, the list of applications configured into TeamFiltration’s latest version appears to contain an error. The application IDs for both ‘Outlook’ and ‘OneNote’ are incorrect, and their listed IDs actually correspond to ‘Microsoft Office’ and ‘OneDrive SyncEngine’, respectively, which are already listed earlier in the code.
Excluding these two incorrect entries, TeamFiltration’s ‘clientIdList’ appears to be a partial version of the one found in Secureworks’ GitHub project Family of Client IDs Research (FOCI). It is possible that the TeamFiltration tool used an outdated snapshot of the list from the FOCI research repository, before it was updated to its current version (as of March 2025).
As a result, the parallels between client ID lists provide another strong attribution indicator, linking suspicious access activity to TeamFiltration.
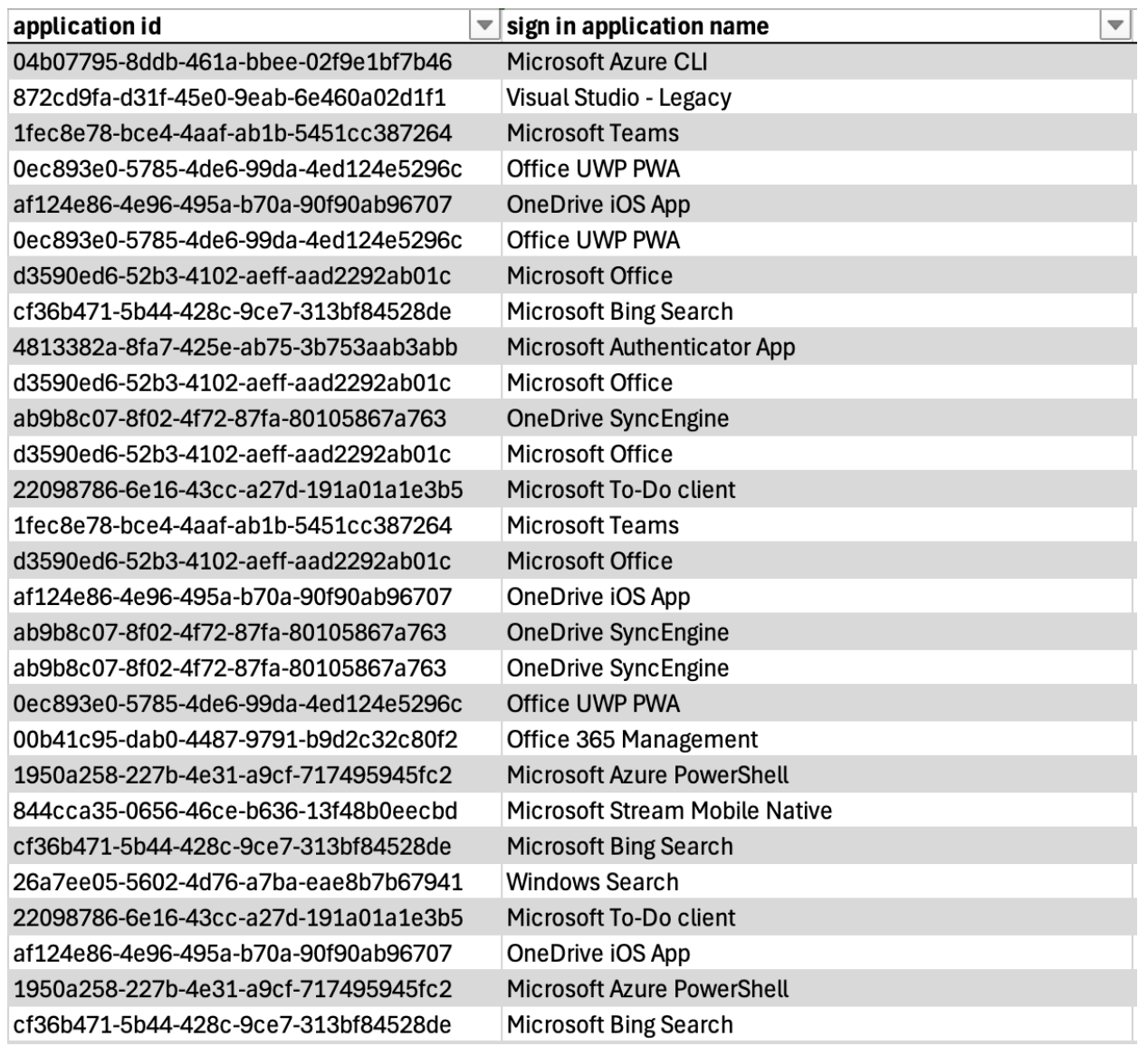
List of native sign-in apps targeted by an ATO attempt attributed to TeamFiltration.
Amazon Web Services and Azure accounts
By default, TeamFiltration requires an Amazon Web Services (AWS) account to initiate an intrusion simulation, with its password spraying function supporting rotation across different AWS Regions.
Additionally, the tool necessitates a so-called "sacrificial" Office 365 user account with a valid Microsoft 365 Business Basic license to enable its enumeration function. In this case, the sacrificial account is a dedicated expendable asset used to enable potentially detectable actions. TeamFiltration’s enumeration function leverages the disposable account and the Microsoft Teams API to verify the existence of user accounts within a given Microsoft Entra ID environment before launching password spraying attempts. A recent update to the tool’s code introduced a OneDrive-based enumeration method, enhancing its enumeration capabilities.
Consistent with these requirements, targeting attempts attributed to TeamFiltration have also relied on AWS infrastructure, operating across multiple AWS Regions. These attempts systematically rotate AWS Regions, ensuring each password spraying wave originates from a different server in a new geographic location.
UNK_SneakyStrike
Condemning malicious activity using TeamFiltration
One of the key challenges Proofpoint researchers encountered was distinguishing between simulated intrusions conducted with TeamFiltration and real-world malicious activity leveraging the same tool.
Despite these challenges, Proofpoint researchers successfully identified a distinct activity set, now tracked as UNK_SneakyStrike, which has been actively targeting Microsoft Entra ID accounts since December 2024. This activity set exhibited unauthorized behaviors closely aligned with TeamFiltration’s known features, including large-scale user enumeration and password spraying attempts.
To distinguish legitimate penetration testing from actual threats, researchers analyzed the distribution of targeting attempts across multiple tenants within a defined timeframe. Unlike controlled security assessments, malicious activity tends to follow a broader, more indiscriminate targeting pattern.
Campaign analysis
Proofpoint’s research indicates that while simulated intrusions using TeamFiltration date back nearly to the tool’s initial release in 2021, there has recently been a surge in login attempts associated with its use. This increase in activity, attributed to UNK_SneakyStrike’s ongoing campaign, began in December 2024 and peaked in January 2025. So far, over 80,000 user accounts across roughly 100 cloud tenants have been targeted, resulting in multiple account takeover instances.
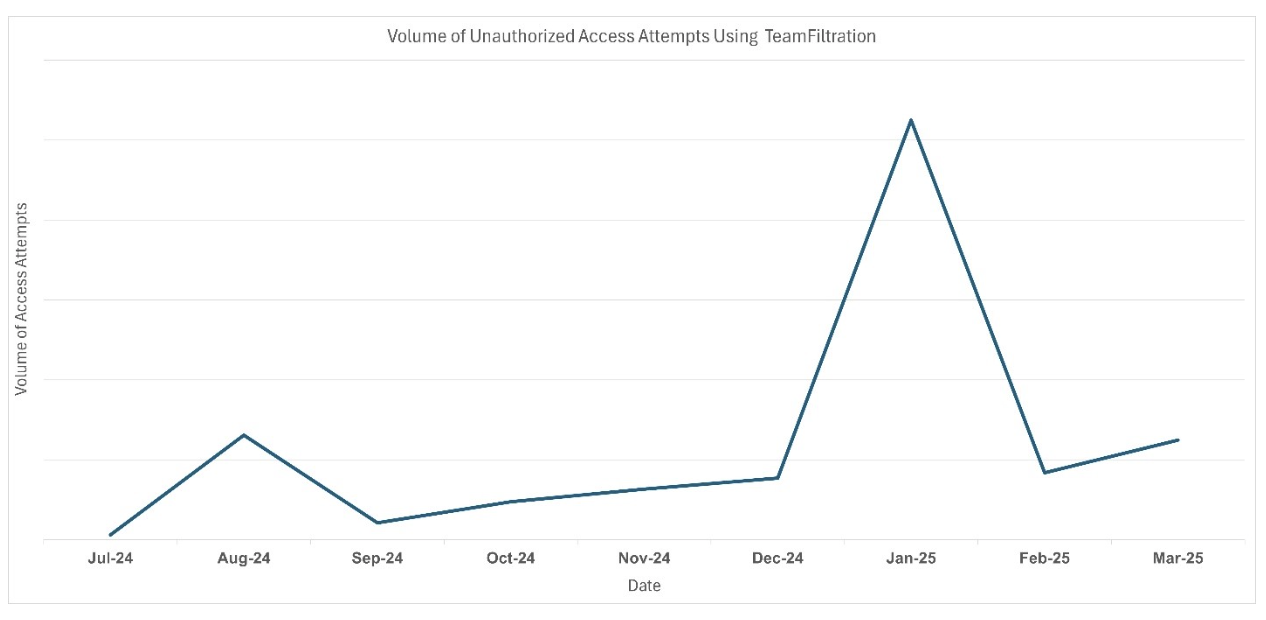
UNK_SneakyStrike velocity by volume of unauthorized access attempts using TeamFiltration over time.
(July 2024 – March 2025)
Activity pattern and victimology
Unauthorized access attempts attributed to UNK_SneakyStrike tend to occur in highly concentrated bursts. Most bursts target a wide range of users within a single cloud environment, followed by quiet periods that typically last around four to five days.
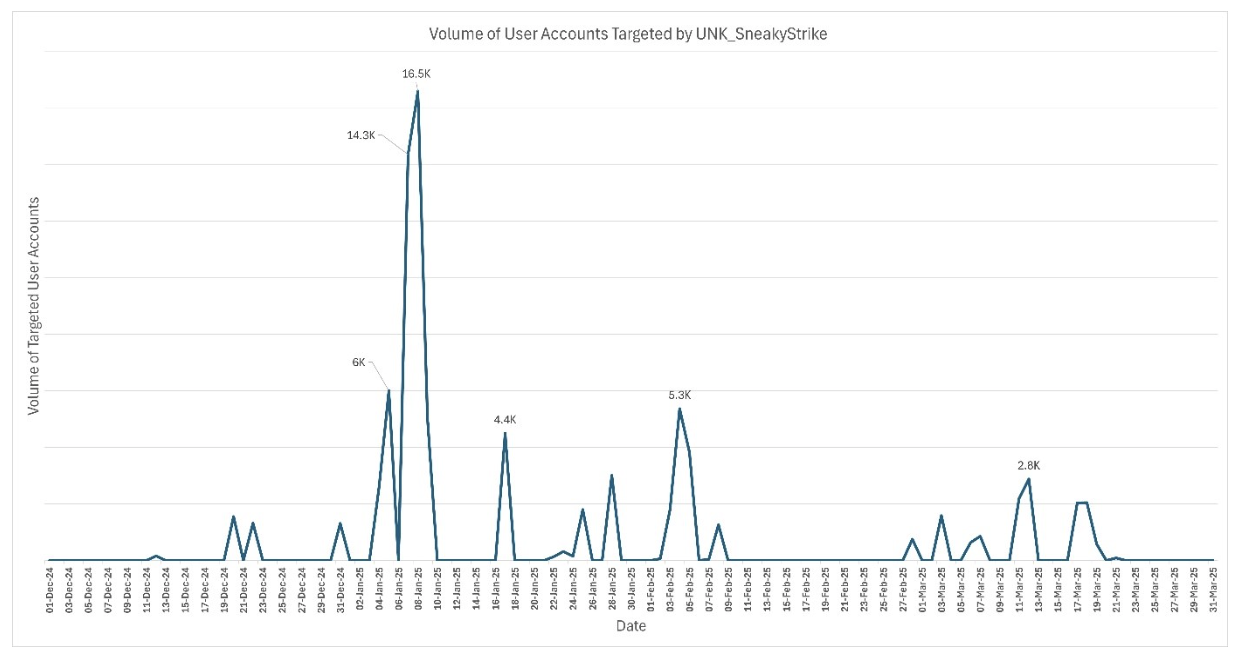
UNK_SneakyStrike velocity by volume of targeted user accounts over time.
(Dec 2024 - March 2025)
UNK_SneakyStrike's targeting strategy suggests they attempt to access all user accounts within smaller cloud tenants while focusing only on a subset of users in larger tenants. This behaviour matches the tool's advanced target acquisition features, designed to filter out less desirable accounts.
While observed access attempts originate from AWS infrastructure across multiple regions, the three primary source geographies (by number of IP addresses) linked to the malicious activity are as follows:
- United States (42%)
- Ireland (11%)
- Great Britain (8%)
Conclusion
While tools such as TeamFiltration are designed to assist cyber security practitioners in testing and improving defense solutions, they can easily be weaponized by threat actors to compromise user accounts, exfiltrate sensitive data, and establish persistent footholds.
Proofpoint anticipates that threat actors will increasingly adopt advanced intrusion tools and platforms, such as TeamFiltration, as they pivot away from less effective intrusion methods.
IOCs
Proofpoint recommends correlating the following indicators with additional context, such as behavioral analytics and threat intelligence, to ensure accurate detections.
The IP addresses listed below represent a subset of the observed operational infrastructure. Due to the nature of observed access sources, activity originating from these IPs during the specified timeframe may be benign.
|
Indicator |
Type |
Description |
First Seen |
|
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Teams/1.3.00.30866 Chrome/80.0.3987.165 Electron/8.5.1 Safari/537.36 |
User Agent |
Default user agent associated with TeamFiltration activity |
- |
|
44.220.31[.]157 |
IP Address |
Source IP associated with UNK_SneakyStrike activity |
04/01/2025 |
|
44.206.7[.]122 |
IP Address |
Source IP associated with UNK_SneakyStrike activity |
07/01/2025 |
|
3.255.18[.]223 |
IP Address |
Source IP associated with UNK_SneakyStrike activity |
28/02/2025 |
|
44.206.7[.]134 |
IP Address |
Source IP associated with UNK_SneakyStrike activity |
07/01/2025 |
|
44.212.180[.]197 |
IP Address |
Source IP associated with UNK_SneakyStrike activity |
05/01/2025 |
|
3.238.215[.]143 |
IP Address |
Source IP associated with UNK_SneakyStrike activity |
04/01/2025 |
|
44.210.66[.]100 |
IP Address |
Source IP associated with UNK_SneakyStrike activity |
20/12/2024 |
|
3.216.140[.]96 |
IP Address |
Source IP associated with UNK_SneakyStrike activity |
07/01/2025 |
|
44.210.64[.]196 |
IP Address |
Source IP associated with UNK_SneakyStrike activity |
20/12/2024 |
|
44.218.97[.]232 |
IP Address |
Source IP associated with UNK_SneakyStrike activity |
04/01/2025 |











