Overview
Fast Flux is a method for rapidly changing DNS entries using a botnet of compromised hosts to hide malicious activities like phishing and malware distribution. Since December 2017, Proofpoint researchers have observed a new Fast Flux infrastructure, dubbed SandiFlux, used to spread malware and recently acting as a proxy for GandCrab ransomware infrastructure.
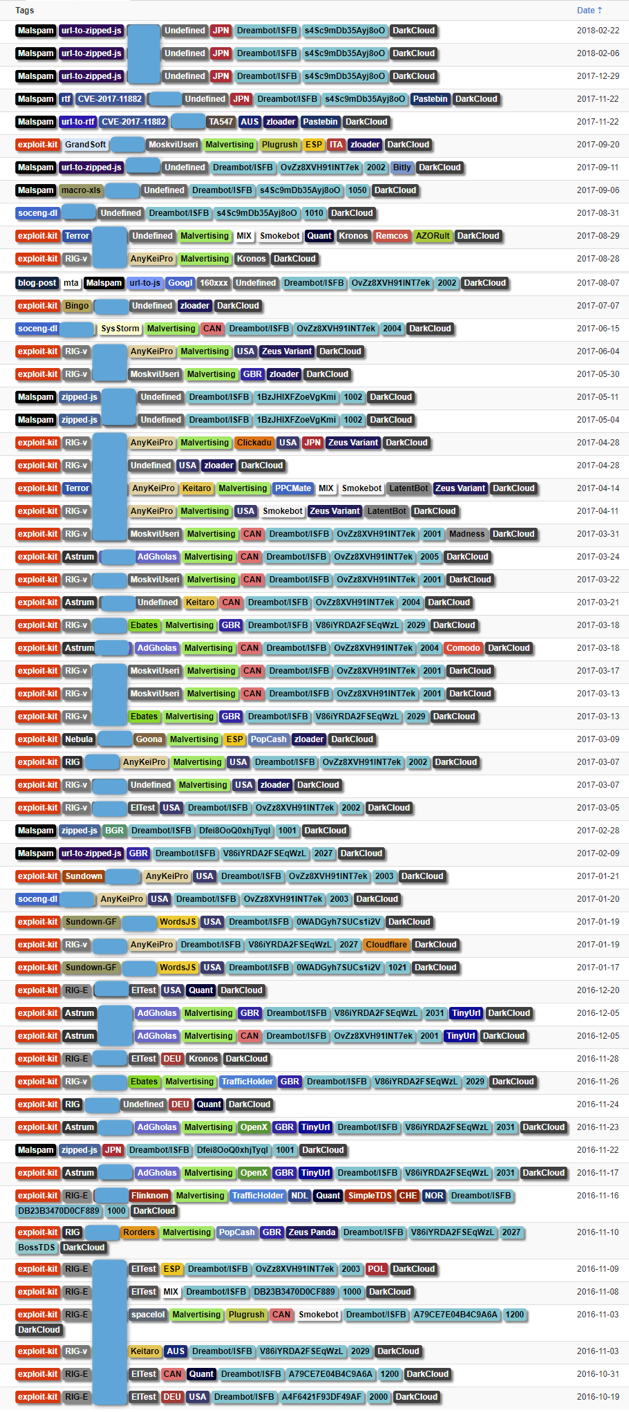
DarkCloud/Fluxxy is a well documented [1 to 12] Fast Flux infrastructure that has been in use since at least 2014. We monitor DarkCloud and witness associated traffic daily, as shown in Figure 1. Note that DarkCloud has been used in association with exploit kits, malicious spam, malvertising, web-based social engineering schemes, command and control (C&C) infrastructure, and more, all with the aim of hiding hosted malware, malicious websites, and other malicious operations.
Figure 1: Selection of events involving the use of the DarkCloud/Fluxxy infrastructure for distributing malware, modules, and plugins or proxying the C&C infrastructure for malware operators
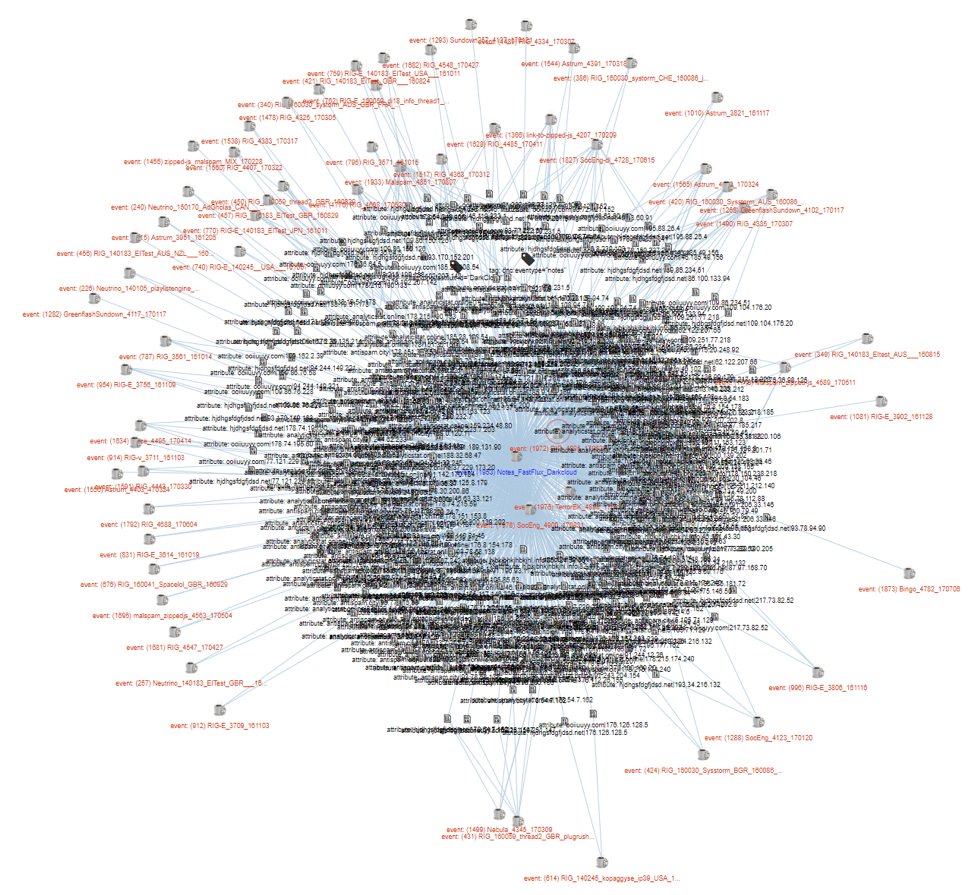
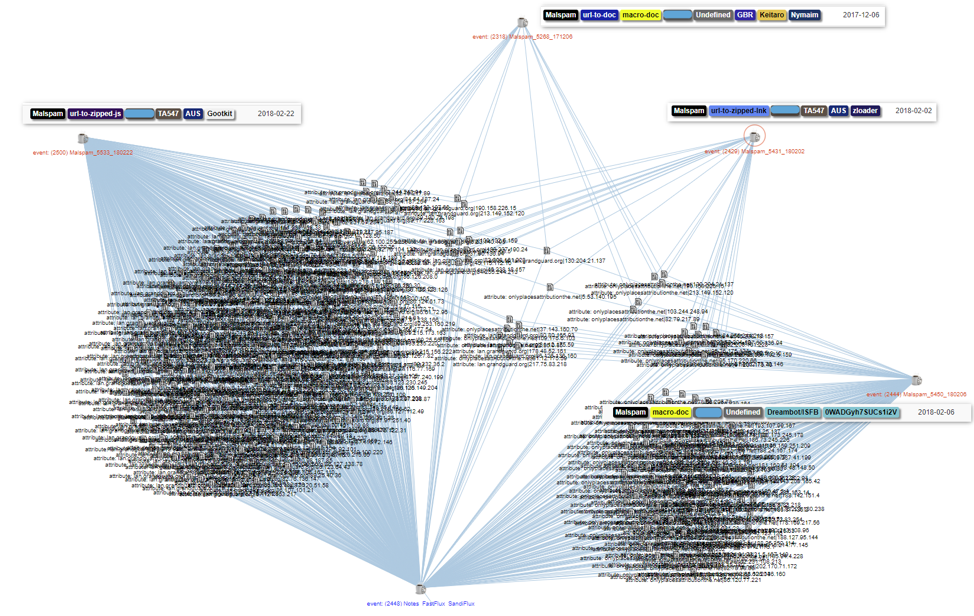
Figure 2 shows another view of DarkCloud/Fluxxy infrastructure in an MISP correlation graph.
Figure 2: MISP correlation graph showing a selection of events involving the DarkCloud/Fluxxy infrastructure
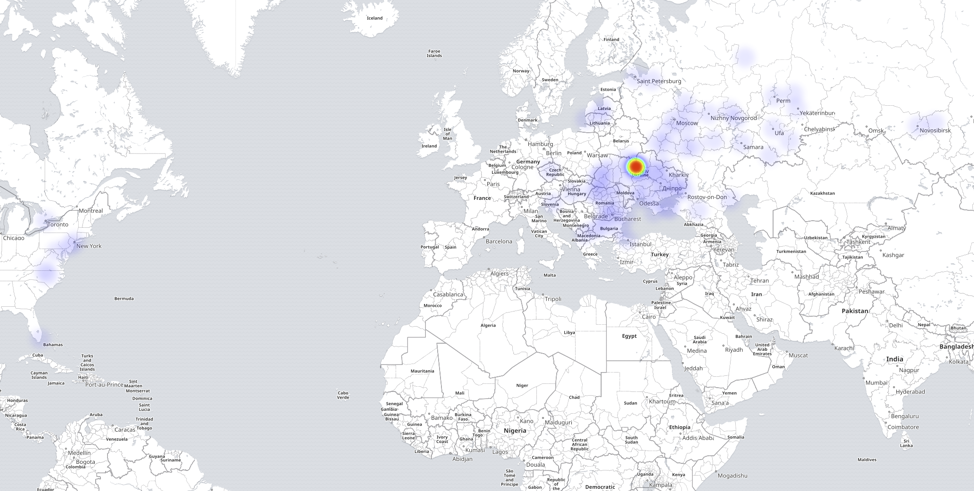
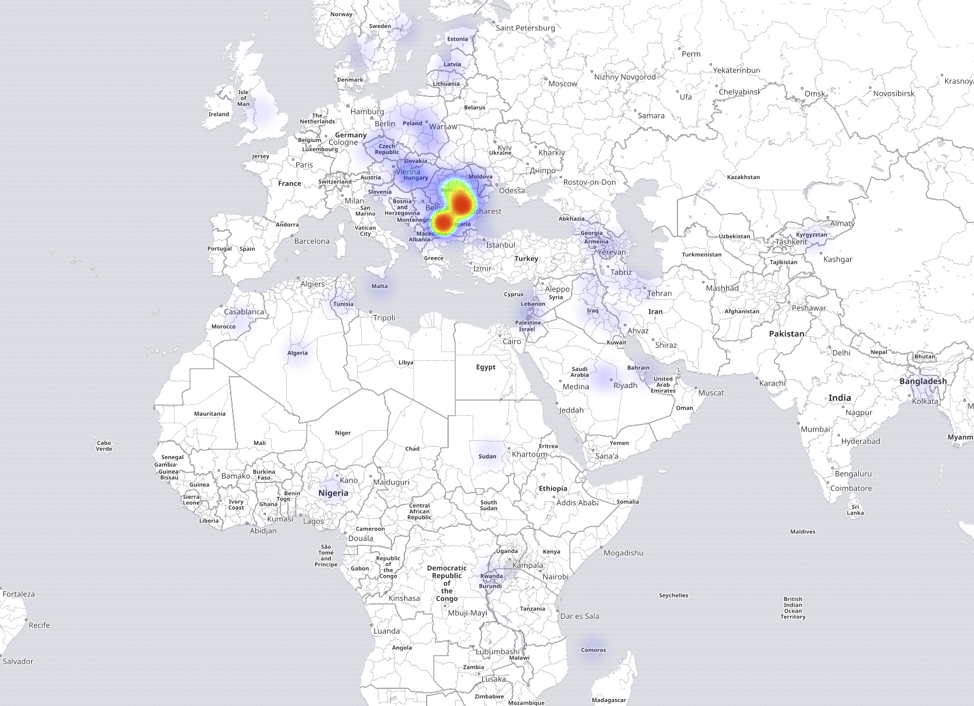
In Figure 3, we can see that most of the compromised hosts that make up the DarkCloud/Fluxxy botnet are centralized in Ukraine and Russia (77.4% and 14.5%, respectively).
Figure 3: Heatmap showing the distribution of DarkCloud/Fluxxy nodes
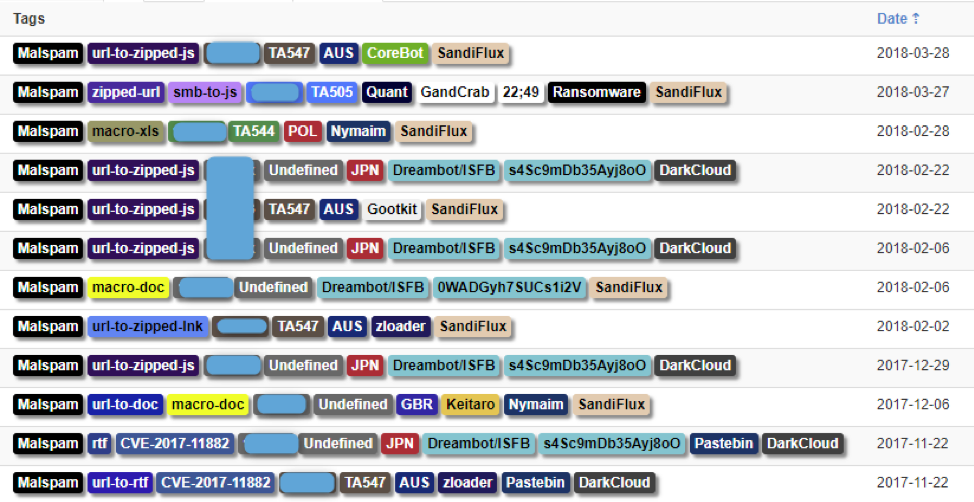
In December we noticed that some Fast Flux domains we observed were not overlapping at all with known DarkCloud/Fluxxy nodes. We decided to map and monitor this infrastructure separately; a selection of events from DarkCloud and the new infrastructure, since named SandiFlux, are shown in Figure 4.
Figure 4: Selection of event involving the use of DarkCloud/Fluxxy and SandiFlux in the past four months. Note one actor (TA547) who migrated from DarkCloud to SandiFlux by February.
Figure 5 is another MISP correlation graph showing selected events involving SandiFlux infrastructure.
Figure 5: MISP correlation graph showing some events involving the SandiFlux infrastructure
Unlike DarkCloud/Fluxxy, SandiFlux nodes are concentrated in Romania and Bulgaria (46.4% and 21.3% of the botnet, respectively), with additional compromised hosts elsewhere in Europe, Africa, the Middle East, and southern Asia.
Figure 6: Heatmap showing the distribution of SandiFlux nodes
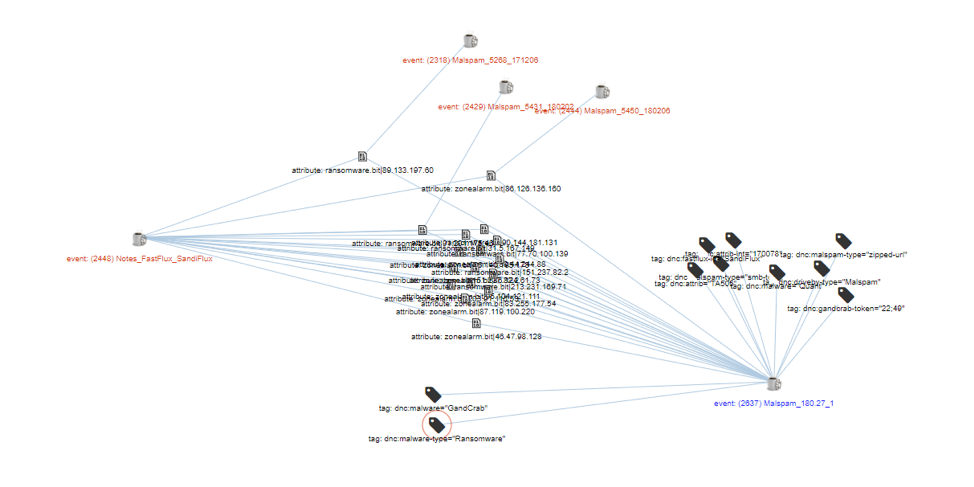
On March 27, 2018, we noticed that command and control for GandCrab ransomware was now using SandiFlux as a proxy, as shown in Figure 7.
Figure 7: Correlation graph showing GandCrab C&C proxyfied by the SandiFlux infrastructure on March 27, 2018
Although we have not observed a single overlap between DarkCloud and SandiFlux in the last four months, we cannot confirm that the two infrastructures are unrelated. Instead, we believe the same actor is operating both infrastructures. Both may be based on the same underlying skeleton that may have been split for operational reasons. We will continue to monitor these botnets to determine potential connections.
Conclusion
Fast Flux DNS has proved to be a powerful tool for threat actors looking to hide dark web sites, malicious infrastructure, and other web-based operations from researchers and law enforcement. While DarkCloud/Fluxxy is the best documented, a new Fast Flux botnet has emerged with nodes of compromised hosts distributed much more widely. It is likely that both DarkCloud and SandiFlux are operated by the same actor who rents capabilities to other actors. GandCrab ransomware in particular now has its command and control proxied behind SandiFlux, although a number of other actors we track are making use of the infrastructure to mass their operations. While direct effects on compromised hosts include performance and bandwidth degradation, the more significant global impact is increased capacity for providing Fast Flux DNS to threat actors.
Acknowledgement
Thanks to @malc0de for his input during this study.
References (for DarkCloud/Fluxxy)
[1] https://krebsonsecurity.com/2016/05/carding-sites-turn-to-the-dark-cloud/
[3] https://riskanalytics.com/2016/08/17/dark-cloud-network-facilitates-crimeware/
[4] https://blog.ensilo.com/furtim-the-ultra-cautious-malware
[5] https://archive.li/3Libi (Dambala on Furtim)
[6] http://www.kernelmode.info/forum/viewtopic.php?f=16&t=4341
[7] http://www.malware-reversing.com/2016/05/geographical-distribution-of-furtim.html
[8] https://www.sentinelone.com/blog/sfg-furtims-parent/
[9] https://malware.news/t/analyzing-furtim-malware-that-avoids-mass-infection/8076
[10] https://www.bleepingcomputer.com/news/security/akamai-identifies-14k-strong-fast-flux-botnet/
[11] https://www.trendmicro.com/vinfo/us/threat-encyclopedia/malware/troj_carberp.ywq
[12] http://blog.talosintelligence.com/2018/03/gozi-isfb-remains-active-in-2018.html
Indicators of Compromise (IOCs)
One set of domain|ips|context for each Fast Flux.