Identity deception scams have been used for years and email has perpetuated this problem by enabling identity deception to become digital. One form of email-based identity deception is business email compromise/email account compromise (BEC/EAC). These attacks involve social engineering to target people, rather than technology or infrastructure, and are making a big impact on organizations of all sizes, in all industries and locations around the world.
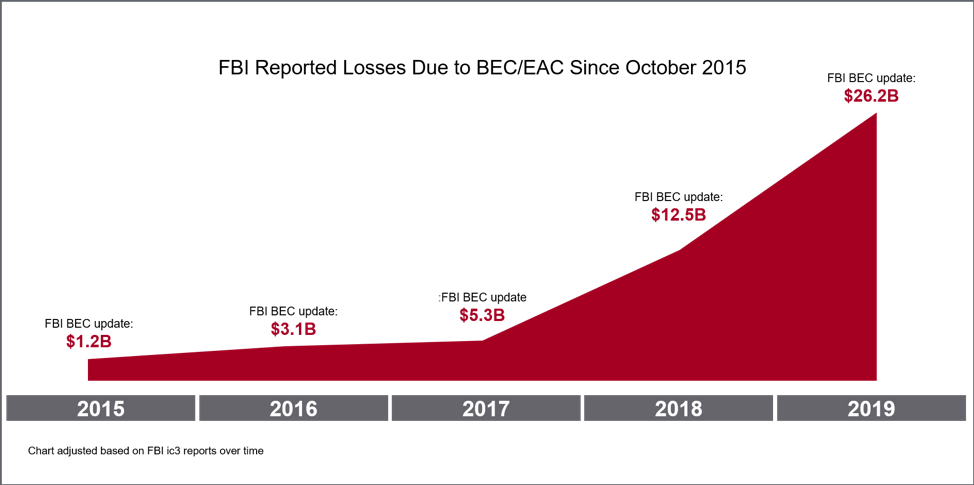
According to the FBI’s latest ic3 report, BEC/EAC has cost organizations around the world more than $26 billion since 2016. That’s an average of about $157K per attack based on the 166,349 incidents reported to the FBI in that time. There is no sign of these attacks slowing down anytime soon.
According to Proofpoint’s own research based on more than 160 billion emails sent across 3,900 companies in 150 countries in 2018, the number of impostor emails (like BEC) detected and blocked have increased more than 400% year-over-year. And while these are highly targeted attacks that are sent to specific people within organizations - that have the authority to execute wire transfers or send sensitive information - companies were targeted 120% more frequently by these impostor email attacks in Q1 2019 vs. the same quarter in 2018.
Why are these attacks so successful?
First, these attacks are highly targeted. Fraudsters are opportunistic and will insert themselves into high dollar transactions. They’ve shown they will impersonate trusted identities to target an organization’s own employees, their business partners, and their customers. Because these attacks are sent in low volumes, anti-spam technologies cannot detect these attacks.
Second, these attacks often don’t include a payload. The malicious content is simply the request made by the criminal within the email itself. Because there is no malicious URL or attachment to analyze or sandbox, anti-virus technologies aren’t looking to detect these attacks.
Finally, these attacks prey on human nature. Criminals using identity deception to steal money and valuable information are targeting people within organizations that can execute the attacker’s requests. They are asking the victim to simply do their job. These requests are often even expected by the victim and don’t raise any red flags. Because of these factors, policy configurations at the email gateway often can’t detect these attacks.
How to protect your organization and people
Attackers use various identity deception tactics to target an organization’s employees, partners, and customers with impostor email attacks, like BEC. We recommend you implement a multi-layered security approach to stop these attacks before they reach the people you are trying to protect.
Email authentication. It is common practice to authenticate things we need to trust such as devices, applications, financial transactions, and even physical access. As the number one threat vector to organizations today, email should be authenticated as well. Email authentication is an important identity verification layer and can block fraudulent emails before they reach the gateway.
Dynamic email classification. Once you’ve validated the identity of the email sender, dynamic email classification will look at the content and context of the email coming into your organization. This layer of security will look at the sender’s reputation, email relationship history, the email’s subject line, and more. You can score an email based on the likelihood that it is fraudulent and then decide what to do with emails based on their scores.
Security awareness and training. Because impostor attacks are designed to bypass traditional security layers, your people are often left as the last line of defense. You need a BEC and EAC solution that can simulate real-world impostor email attacks. You can track who is responding to these simulated attacks and train them accordingly. Give your people the knowledge and skills they need to protect your organization against these advanced attacks.
To learn more about how to protect people against email-based identity deception, read our Guide to Stopping Email Fraud.











