Business Email Compromise (BEC) and Email Account Compromise (EAC) afflict businesses of all sizes across every industry. More money is lost to this type of attack than any other cybercriminal activity. The FBI reported that from June 2016 to June 2019, companies reported $26.2B in losses. And in 2019 alone, BEC scams accounted for more than half of all cybercrime losses—an estimated $1.77B. The average loss per BEC incident in 2019 was $74,723.
An indication of how pervasive a problem BEC/EAC is: Proofpoint blocks over 15,000 BEC/imposter messages a business day or nearly 4 million messages a year.
In this series, we cover BEC/EAC attack types that Proofpoint considers the most important for a business to be aware of. In each of these posts, we explain what the attack is and how it works so that you can better understand these BEC/EAC attacks and can better protect yourself. In this post, we focus on BEC/EAC gift card scams.

What Are BEC/EAC Gift Card Scams?
BEC/EAC gift card scams are similar to other BEC/EAC attacks by relying on impersonation and social engineering to convince the target victim to send money to the attackers. In this case, though, the attackers try to convince the target victim to send money to them using popular retail gift cards rather than through wire transfers. In gift card scams, the attackers will frequently impersonate the CEO or other high-level executive in the business as part of the scam.
Attackers abuse gift cards in BEC/EAC attacks because it is a quick and easy way to for them to get money from their targeted victims: the victims don’t have to navigate complicated wire transfer instructions, they just go and purchase gift cards from well-known, recognized and trusted retailers.
Abusing gift cards like this is also a quick, easy and simple way for attackers to effectively launder stolen money. Instead of receiving the stolen money directly, the attackers receive the money by way of the retailer whom the targeted victim purchased the gift card from.
Using gift cards has another benefit for attackers: potential victims may not be aware of the role of gift cards in BEC/EAC attacks because wire transfers are more commonly been associated with BEC/EAC attacks. With potential victims being less wary of requests for gift cards than they might be for wire transfer requests, they may be more likely to fall for this particular type of BEC/EAC attack, especially when the scam email is impersonating the CEO or other high-level executive.
Abusing gift cards like this is not something that’s new or unique to BEC/EAC attacks. Cybercriminals have been effectively using gift cards as a payment and laundering method for a number of years in other types of attacks. BEC/EAC attackers have picked up this tactic because it has worked well in other attacks and they have adopted it aggressively for their use. The FBI’s IC3 reported 1,164 gift card attack complaints accounting for US$1,021,919 in losses between January 1st, 2017 and August 31st, 2018, representing a 1,240% increase in these kinds of complaints. They noted that over 90% of these incidents reported in the five-month period between March and August 2018 alone.
How BEC/EAC Gift Card Scams Work
BEC/EAC gift card scams are very straightforward in their approach. Like other types of BEC/EAC attacks, the attackers impersonate a trusted person like the CEO, send information to the targeted victim as that impersonated party explaining how much money needs to be transferred, why it has to be transferred and how it has to be transferred. In the case of gift card scams the “how” is by purchasing retail gift cards and sending the information on to the attackers. Figure 1 shows the sequence of a BEC/EAC gift card attack.
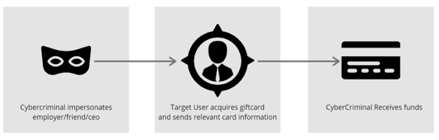
Like all BEC/EAC attacks, gift card scams rely heavily on a combination of both authority and urgency. Figure 2 shows an example of this with a BEC/EAC attack email sent by an attacker impersonating the CEO of the company to an employee of the company. This email is the first of a series of exchanges that will culminate in the attacker giving the targeted victim instructions on what gift cards to purchase and how to send the relevant information to the attacker so they can cash those gift cards out.
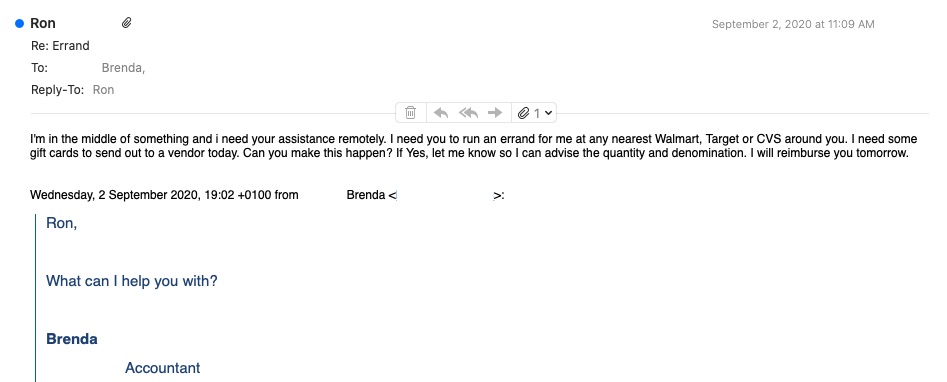
CEO impersonation like you see in this example is a common tactic. Proofpoint research has shown that since March 2020, over 7,000 CEOs or other executives have been impersonated. In 2020 over 50% of Proofpoint customers have had some VIP impersonated. Looking at the last 90 days, on average a CEO specifically has been impersonated 102 times.
How Proofpoint Protects Against BEC/EAC Gift Card Scams
Proofpoint provides a multi-layered solution to help organizations protect against gift card scams. First, as part of Proofpoint Email Protection, Impostor Classifier dynamically analyzes a wide range of message attributes, including the sender/receiver relationship, header information, domain, and message body to determine if a message is an impostor message. Proofpoint Email Protection delivers unique value to Proofpoint customers in the following ways:
- Being in mail flow allows Proofpoint’s BEC detectors to understand the sender/target relationship, which is a critical detection ingredient.
- Analyzing and blocking 15,000 BEC messages per day globally gives each Proofpoint customer an unfair advantage as Impostor Classifier has a large corpus of prior BEC attacks to compare message body contents against.
- Configuring arbitrary combinations of VIP display names (e.g. Michael or Mike) doesn’t force customers to choose where to apply protections against display name impersonation attacks.
Second, in the event there isn’t enough data to identify a message as an impostor message, Proofpoint alerts the user that the message is suspicious using email warning tags. These visual cues help users take extra precautions with the email in question. In addition to the impersonated sender alert, Proofpoint’s email warning tags support other situations including external sender, new sender and newly registered domains.
Last, but not least, Proofpoint provides security awareness training to help organizations turn users into part of their defense. Because BEC/EAC gift card scams rely on social engineering to trick end users, it’s critical to train employees about gift card scams. Not only can Proofpoint help organizations teach users to spot BEC/EAC gift card scams, but we can also enable those users to report those messages as suspicious and automate the investigation and remediation of those reported messages.
Are You Protected?
BEC/EAC gift card scams are just one of many different kinds of BEC/EAC attacks out there. They’re also one of the most successful kinds of BEC/EAC attacks. This makes BEC/EAC gift card scams one of the most common forms of BEC/EAC attacks out there.
One of the most important things you can do to help protect against BEC/EAC gift card scams is to understand how prepared your organization is to combat them. Find out by taking our BEC/EAC readiness assessment here.











