The cybersecurity landscape is constantly evolving and keeping up with the changes can feel overwhelming.
Because security has a direct impact on the brand reputation and bottom-line business outcomes of enterprise organizations, it’s more important than ever to break down complex security topics and challenges in a way that even non-technical colleagues can understand.
In honor of cybersecurity awareness month, we are doing just that with a series of educational blog posts and videos exploring the basics of key cybersecurity topics. The first post in our series answers a question every organization needs to be asking: Is the cloud secure?
Security Risks of Cloud Computing
Cloud computing has transformed the way companies use, store, and share data. This transformation has introduced new security threats and challenges. Because of the volume of data stored within the cloud, it is a natural target for cybercriminals.
For example, cloud tools like Office 365 and GSuite can be great for workplace collaboration and efficiency. But if the wrong person gets access to one of these employee accounts, your organization is at serious risk.
Not only will the attacker have access to sensitive data in the cloud, but they can also spoof the identity of employees at your organization. A hijacked cloud account can lead to wire fraud, data breaches, and much more.
Top Company Targets
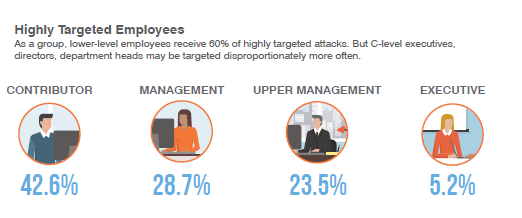
While you may expect that your executives and upper-level managers are the only targeted employees at your organization, Proofpoint research reveals that individual contributors and lower-level managers account for about 60% of highly-targeted cybersecurity attacks.
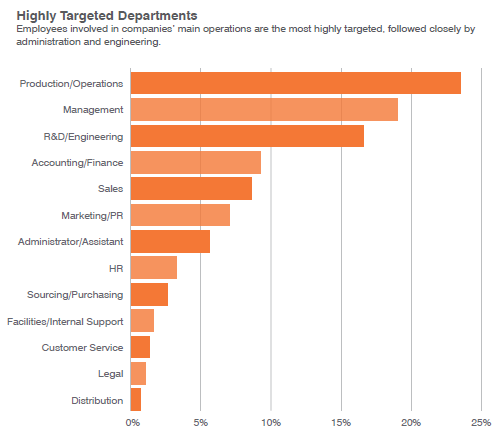
The most highly targeted departments include production and operations, management and R&D.Engineering.
Attacker Techniques
Criminals use a variety of techniques to gain unauthorized access to the cloud. Here are three of the most common:
1. Data Breaches
A data breach is the intentional (or unintentional) release of confidential information to a public or unsafe environment. While the risk of a data breach is not unique to cloud computing, it consistently ranks as a top concern for cloud customers. Data breaches can involve a criminal exposing confidential company data, personal health information, financial information, trade secrets, intellectual property or more.
2. Credential Phishing Attack
The goal of a credential phishing attack is what its name suggests: to steal credentials from targeted users. To succeed, a cybercriminal usually spoofs the identity of a trusted company and asks you to login to your account in the cloud by sending you to a fake website.
Nearly one in four people who receive a phishing email will open it. And more than 10% will click on the malicious link or open the weaponized attachment that the phishing email contains. That means an attacker has to send only 10 messages to have a 90% probability of catching and compromising a user.
3. Brute Force Attack
A brute force attack is a trial-and-error method that enters a combination of usernames and passwords over and over again until the attacker gains access to a cloud account. While they can take longer than a traditional phishing attack, they are often very effective in gaining access to multiple cloud accounts, as many users still use the same password across various accounts.
Want to dive deeper? Learn more about how you can build an effective cloud security strategy by clicking here.











