Email fraud is more pervasive than ever. Companies of all sizes, in all industry verticals, and in all locations are at risk of falling victim to these highly-targeted, socially engineered attacks.
To better understand the scope of the problem, Proofpoint conducted extensive research to assess the state of email fraud in 2017. We analyzed a larger email fraud dataset than ever before, including more than 160 billion emails sent to more than 2,400 companies, spanning 150 countries. Here’s a summary of our findings.
Email Fraud Was Rife in 2017
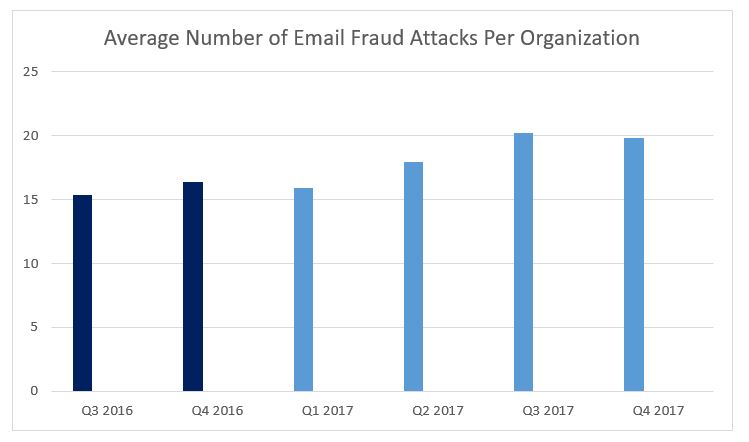
The number of companies impacted by email fraud steadily grew in 2017. By Q4, 88.8% of all organizations were targeted by at least one of these attacks. This is a significant jump from the 75% of organizations targeted in Q4 of 2016. And while these attacks are sent in low volumes, fraudsters are expanding their reach within organizations – spoofing more identities and targeting more people, across more business units.
On average, organizations were targeted by 17% more attacks in 2017 than in the previous year. The number of identities spoofed within the average organization hovered around 5 in 2017 but spiked to about 10 in Q4.
Within a given organization, 13 people were targeted on average throughout 2017.
Key Email Fraud Tactics and Trends
While email fraud tactics vary, all attackers prey upon human emotion – fear, or the desire to please – in order to steal money and valuable information away from organizations.
Our analysis revealed that the majority of attackers aimed to commit wire transfer fraud, as nearly one in every three email fraud messages included some variation of the word “payment” within the subject line. In addition, there was a spike in W2 scams in Q1, presumably correlating with the U.S. tax deadline. And we saw a similar spike in Q1 of 2016.
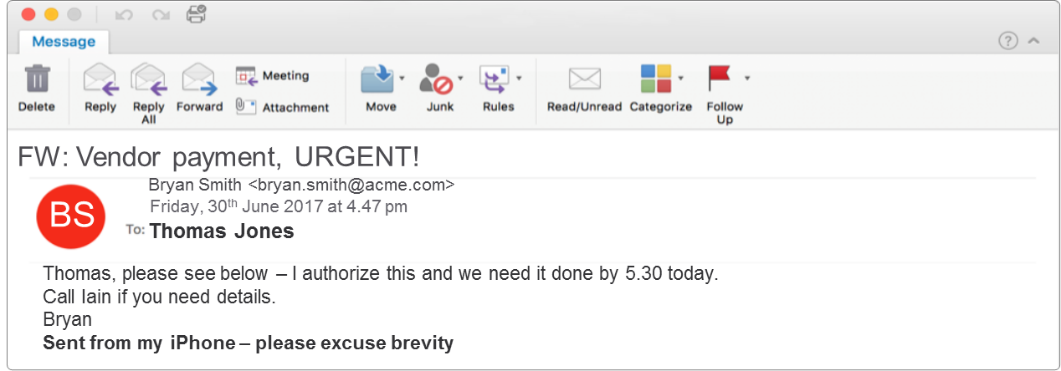
To sound legitimate, the attackers manipulate the tone of their email copy. They take on different personalities, including “the authoritarian” who uses a direct and urgent approach, or “the conversationalist” who builds a dialogue before asking for the request.
We also saw an increase in the number of “fake email chain” messages, where the attacker will create a false email history to give a realistic experience and appear more credible. By Q4, more than 11% of all email fraud attacks included a variation of this tactic.
Fighting Back with DMARC
Towards the end of 2017, we saw some big initiatives to help organizations fight back against email fraud. In October, the Department of Homeland Security gave a mandate (BOD 18-01) to all civilian federal agencies to increase their security postures, including the requirement to implement Domain-based Message Authentication Reporting & Conformance, or DMARC, within 12 months. At the time of the directive, nearly 1 in every 8 emails from a .gov email address was fraudulent.
DMARC authentication prevents cybercriminals from hijacking an organization’s trusted email domains in an effort to trick employees, customers, or business partners. While a significant percentage of these agencies are behind the timelines given by the DHS, agency DMARC adoption rates increased from 17% in October to about 52% in mid-January 2018. Shortly after BOD 18-01 was announced by the DHS, National Health Information Sharing and Analysis Center (NH-ISAC) asked its members to pledge to implement DMARC authentication in 2018.
How You Can Prevent Email Fraud
While implementing DMARC is a great first step, email fraud attacks are constantly evolving. Cybercriminals leverage various spoofing techniques in an effort to reach the intended target and trick them into acting on their behalf. These include domain spoofing, addressed above, but also include display name spoofing and lookalike domain spoofing techniques as well. Organizations need a multi-layered solution to stop all forms of email fraud including dynamic classification, email authentication, lookalike domain discovery, and data loss prevention.
To read our complete email fraud analysis and learn more about how you can stop attacks at your organization, download the 2017 Email Fraud Threat Report.











