In my last post on the Proofpoint Attack Index, we reviewed how to Use the Proofpoint Attack Index in the TAP Dashboard.
Today, we’ll reveal how you can find the answers to the following important questions with the Proofpoint Attack Index within the TAP Dashboard:
- Which Very Important Persons (VIPs) are also Very Attacked Persons (VAPs)?
- Which people within a specific subdomain or domain are most attacked?
- What people are most at risk for credential phishing?
- Who received vertically or geographically targeted threats and what are they?
- Who was targeted by the most impactful / potentially dangerous threats?
- Who received RATs, or ransomware, or <insert favorite malware variant here>?
Below, we reveal, step-by-step how to leverage the product to gain these valuable insights.
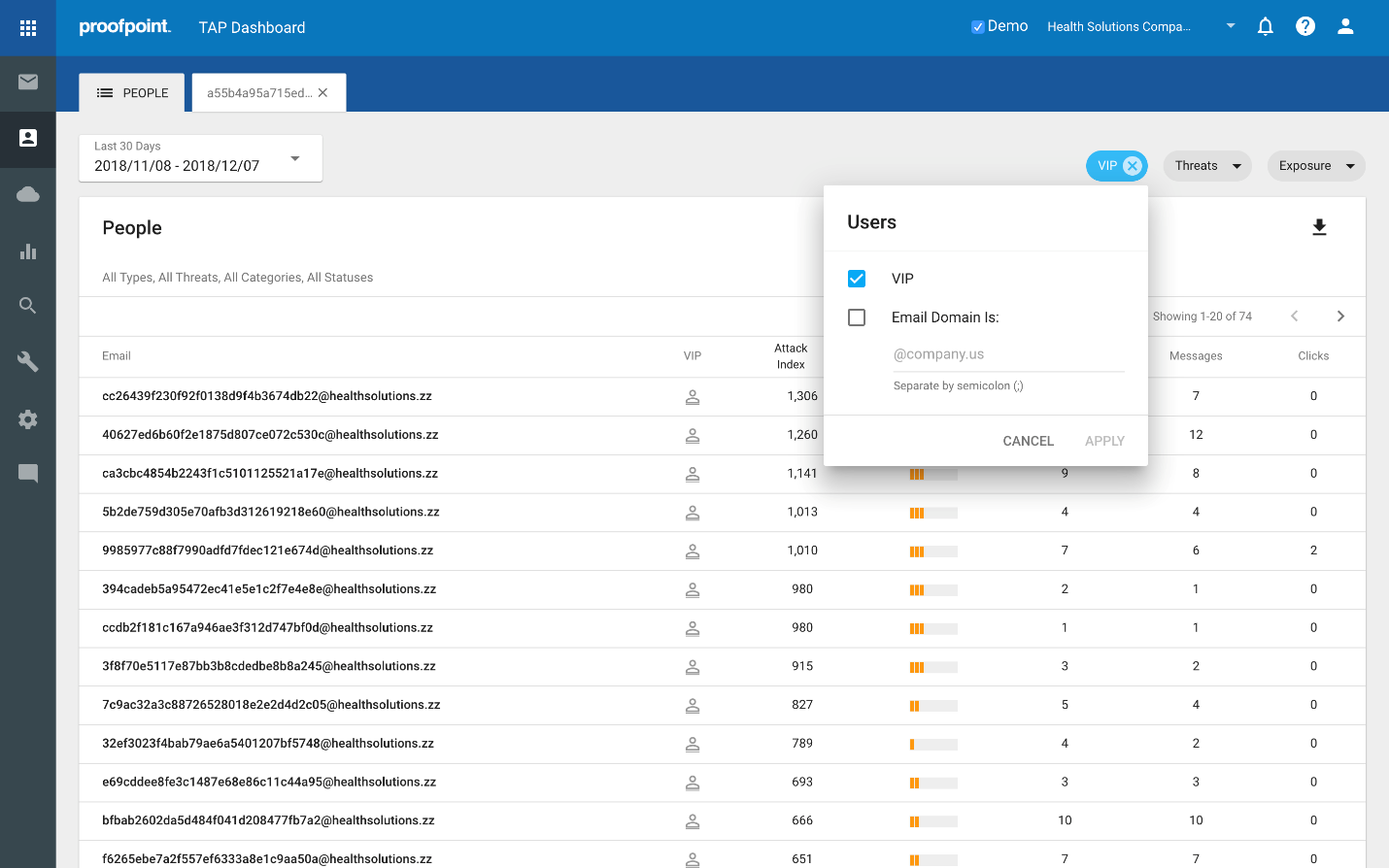
- Which Very Important Persons (VIPs) are also Very Attacked Persons (VAPs)?
Click the Users filter and check the VIP box. It will list all VIPs, as follows:
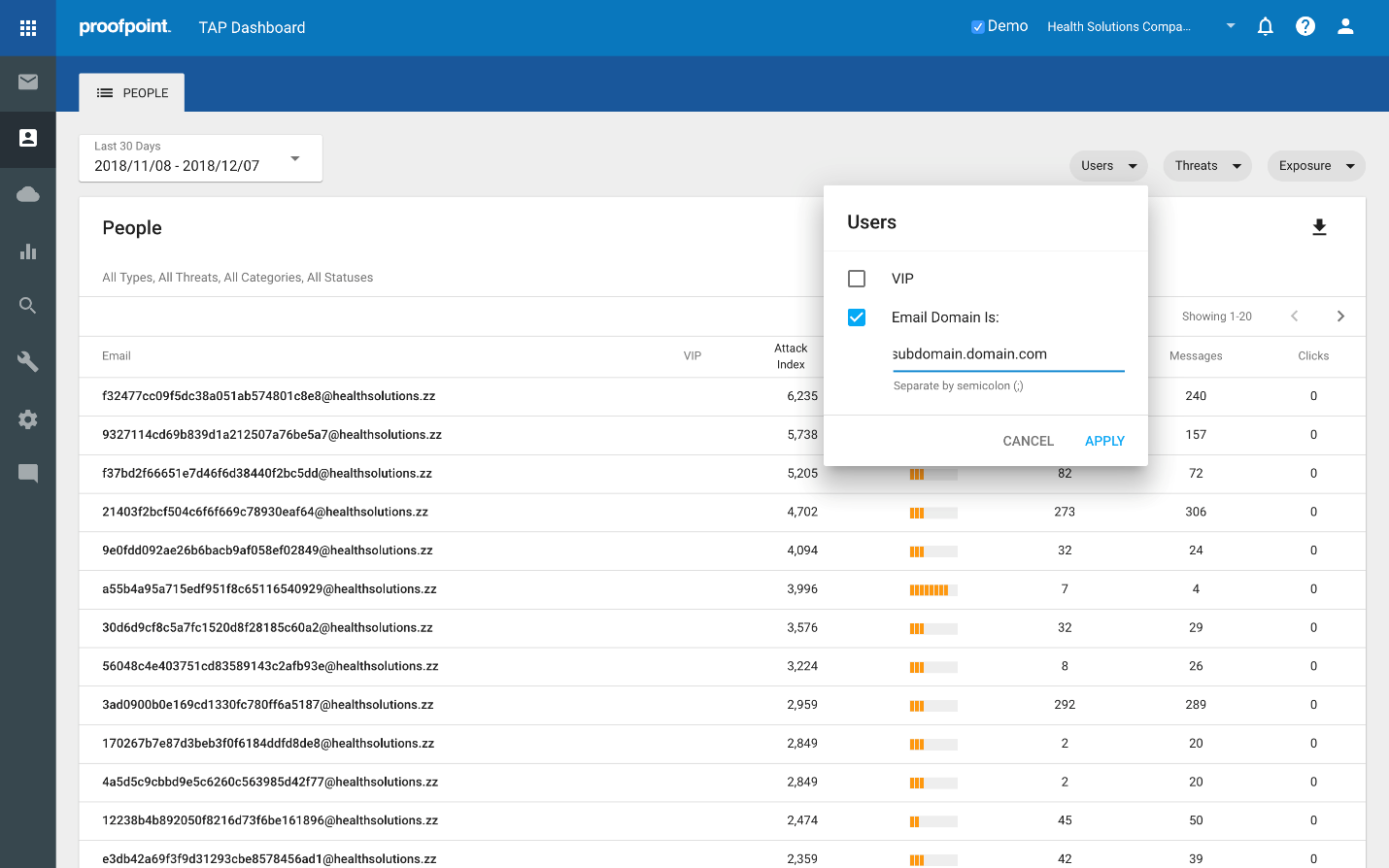
- Which people within a specific subdomain or domain are most attacked?
Click the Users filter and check the Email Domain box, then enter the subdomain or domain you want to inspect. It will list all VIPs, as follows:
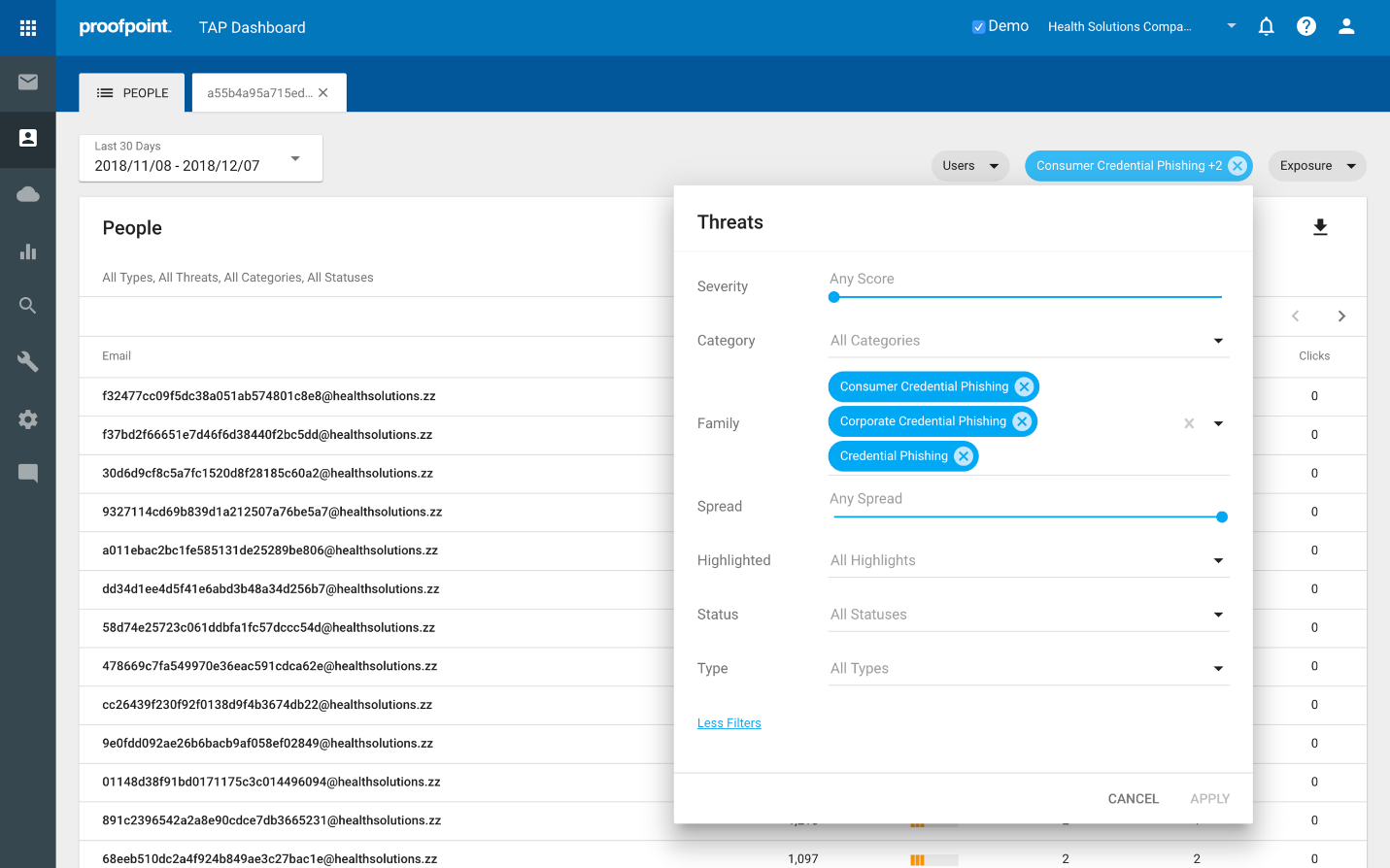
- What people are most cred phished?
Click the Threats filter, select Family, and check each of the 3 Cred Phishing boxes. It will list those people with the highest scoring Cred Phish attacks, as follows:
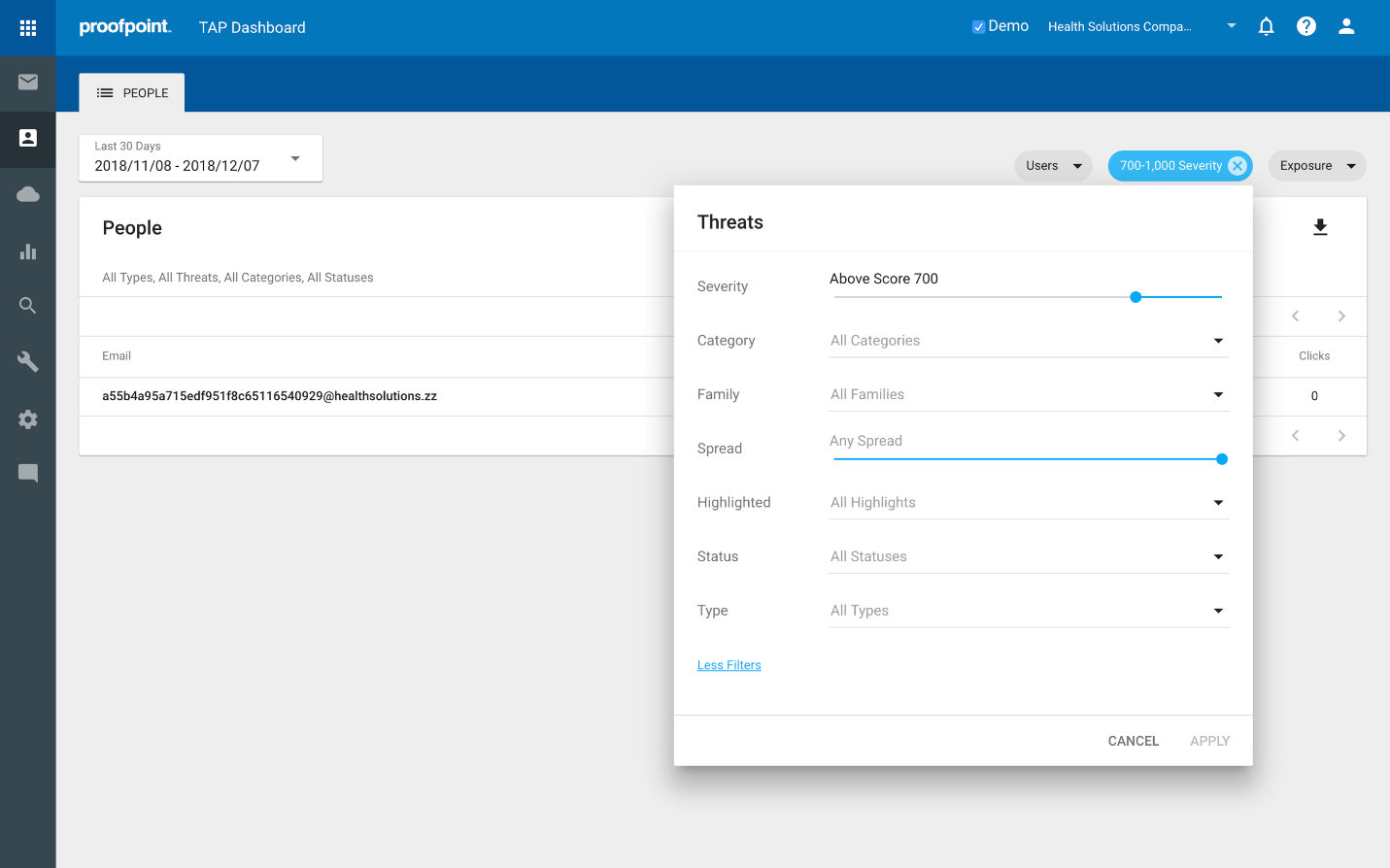
- Who was targeted with the most impactful / potentially dangerous threats?
Click the Threats filter, select Severity, and slide the selector dot to the right, e.g. above score 900. If it does not surface anything, increment to the left, e.g. above score 800. Remember, this number reflects the highest score for any single threat. A threat receives a score of 0 – 1000 on the basis of multiple factors including the sophistication of the actor, how targeted the threat is, and the type of attack.
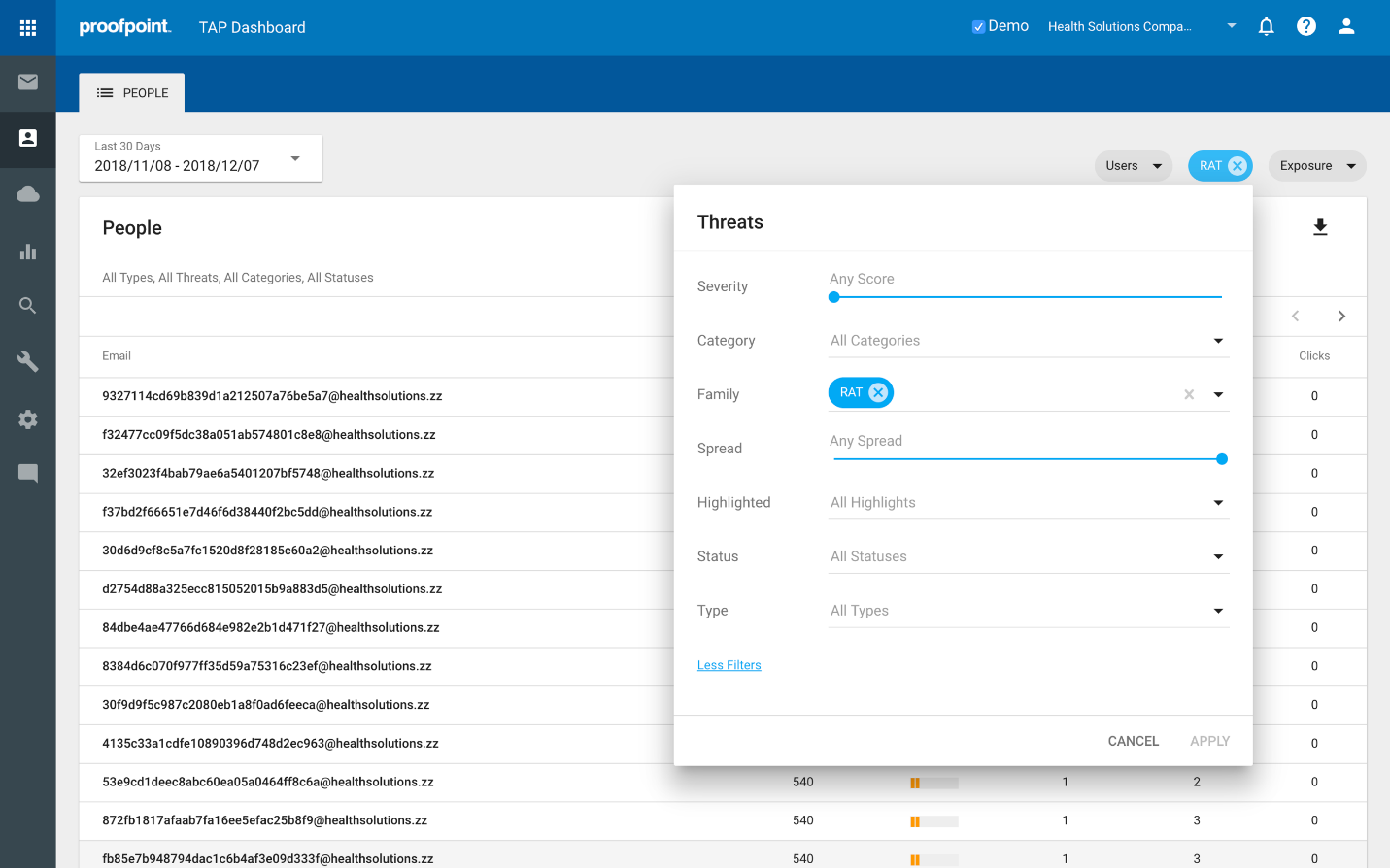
- Who received RATs, or ransomware, or <insert favorite malware variant here>?
Click the Threats filter, select Family, and check the box for the desired malware type, in this case, RAT. It shows those people attacked by RATs, as follows:
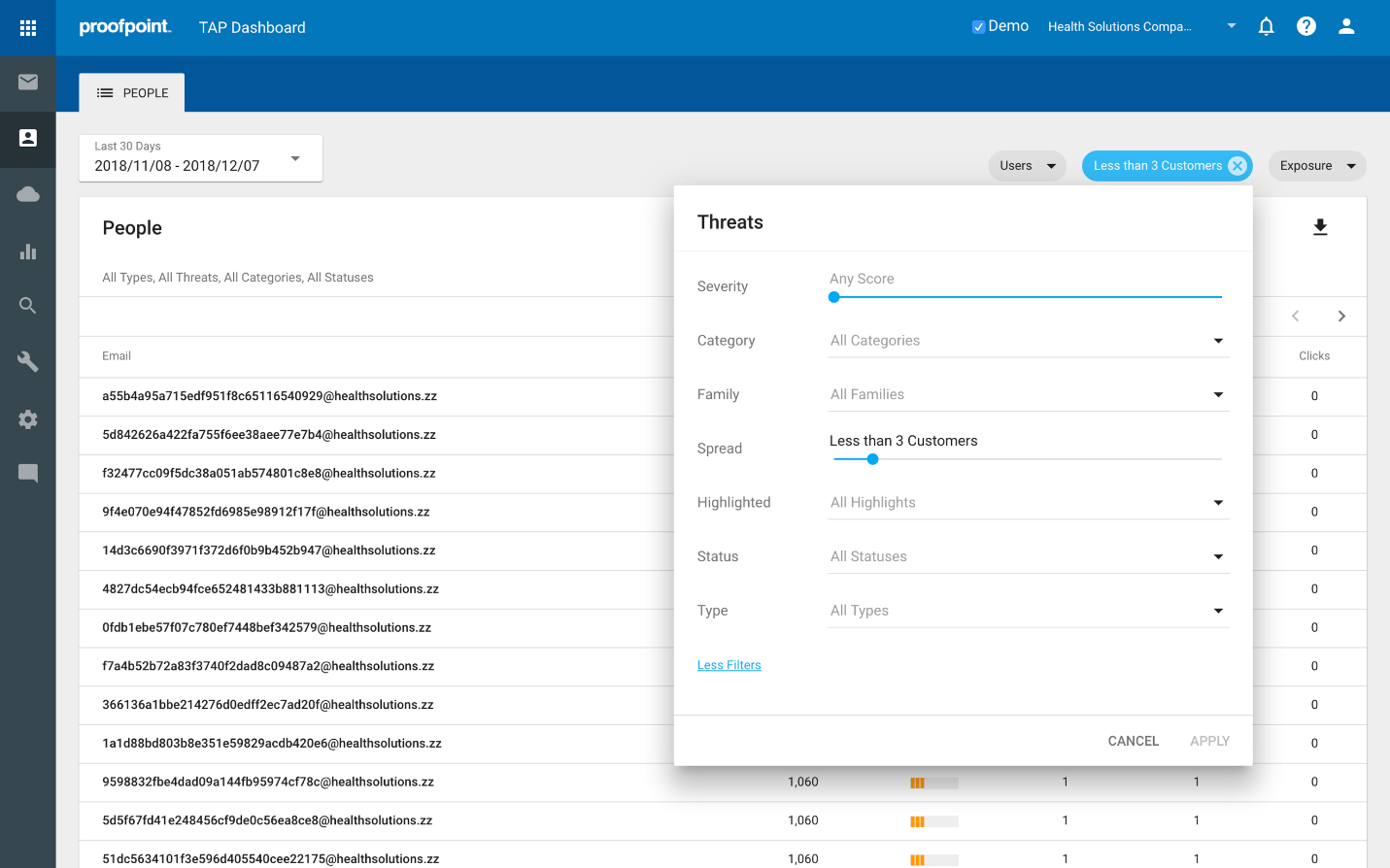
- Who are recipients of very targeted attacks?
Click the Threats filter, select Spread, and slide the selector dot to the left, to find the most highly targeted users and associated threats. If it does not surface anything, increment to the right, to loosen it up a bit.
Once you get answers to the questions above, you can then use TAP to surface additional forensic and contextual info helpful in understanding the patterns of the attacks, and characterizing the threats, the campaigns, as well as the actors.
Let’s take a step back and briefly consider what we’ve done in the past three posts. We started by introducing the concept of building a security model around people. To identify and prioritize those people representing the most risk, we introduced the Attack Index, available in the Targeted Attack Protection (TAP) Dashboard. Next, we walked through the mechanics of how you can use this capability to gain more visibility and insight into your Very Attacked People, and to answer key questions about them.
For a free trial of the Proofpoint Attack Index and TAP Dashboard, sign up here.











