All the buzz on Bumblebee downloader malware. Tracking the latest Follina exploits. And a cyber attack causes chaos in one of Italy’s largest cities.
This week on The Threat Hub: In a new episode of the Discarded podcast, hosts Selena Larson and Crista Giering discuss Bumblebee downloader. They’re joined by Kelsey Merriman and Pim Trouerbach from the Proofpoint Threat Research team, for an investigation into Bumblebee’s growing popularity among crimeware actors, many of whom have switched from BazaLoader in recent months. Check out the episode for the lowdown on Bumblebee’s sophisticated evasion techniques and to find out what the sudden appearance of this new malware has to do with March’s spate of leaks from the Conti ransomware group.
Also of note this week, Threatpost has a write-up of our latest research into government-aligned attackers exploiting the Follina vulnerability. U.S. and E.U. government workers are being targeted with fake recruitment pitches promising a 20% salary increase. If they download and execute the malicious file included in the bogus email, the threat actor conducts extensive reconnaissance into the user’s machine and software. This follows on from Follina-related activity associated with TA413 that we reported last week.
And on this week’s Five-Minute Forecast, Apple blocks over 1.6 million malicious and untrustworthy apps from iPhones, Europol shuts down the FluBot Android malware, and Daniel Blackford from the Proofpoint Threat Research team discusses insights from this year’s Human Factor report.
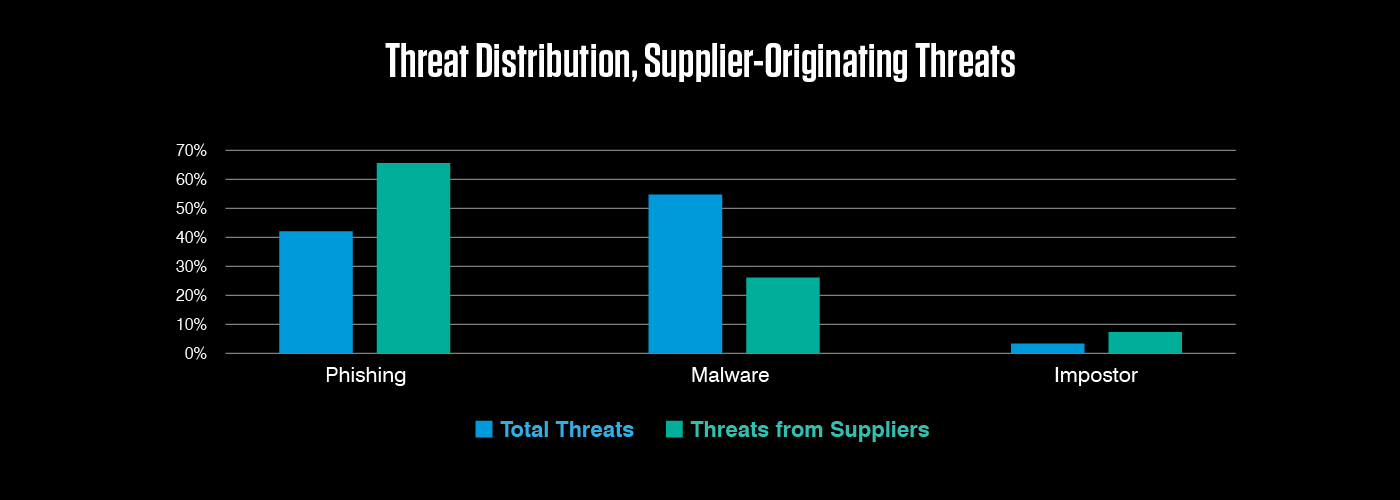
As data from this year's Human Factor reveals, attacks originating from compromised or spoofed suppliers look a little different to the rest of the threat landscape. Supplier-originating attacks are much less likely to distribute malware, instead over-indexing on phishing and imposter threats.
Get the reportEquip your team with threat intelligence
Go Deeper with Proofpoint Threat Intelligence Services
Connect with threat analysts, understand threats with intelligence specific to your situation, and gain 24/7 visibility into the latest threat discoveries.
Learn MoreCyberattackers target people. They exploit people. Ultimately, they are people. That’s why the Human Factor report focuses on how technology and psychology combine to make people so susceptible to modern cyber threats. In this first volume, we take a closer look at attacks that rely on social engineering, including business email compromise (BEC) threats, email fraud and phishing.
In 2021 the spotlight of global attention fell on cyber criminals like never before. In our first semiannual threat update, we explore new techniques and old tricks in a rundown of the year's biggest themes and schemes.
About The Threat Research Team
Our threat researchers are responsible for tracking shifts in the cybersecurity landscape, identifying new attacks as they emerge, and monitoring how threat actor tactics, techniques and procedures change over time. The threats they detect and the signatures they write feed into our platforms and are keystones in a system that analyzes more than 2.6 billion emails, 49 billion URLs and 1.9 billion attachments every single day.
By studying what cyber criminals are doing now, our threat researchers are better able to anticipate what they’ll do next. Every day, their work keeps our customers protected—not just from today’s attacks, but tomorrow’s threats as they evolve.