

Keep data secure
Discovery of Abandoned Data
Locate and eliminate abandoned data in multi-cloud environments.
Abandoned data increases risk and cost
Abandoned data is information that remains in storage but is no longer used, accessed or needed by an organization. It can include snapshots of databases from discontinued projects, files from former employees or information left behind after migration to new platforms.
This redundant, obsolete or trivial data can arise from lack of oversight or visibility, poor understanding of what data is ready for archiving or deletion or inadequate data management policies. It drives up cloud storage and backup costs. It also increases attack surface without delivering value.
Save up to $324k a year for every petabyte of data
Proofpoint research shows that 27% of data volumes are abandoned. This means that for every petabyte (PB) of data an organization stores in the public cloud, 270 terabytes (TB) might be unused. By using Proofpoint Data Security Posture Management (DSPM) to locate and eliminate unused data, your organization can save up to $324k a year on storage and backup costs.
Identify abandoned data in multi-cloud environments
Organizations commonly use multiple public cloud providers to store data. Much of this data might be unknown to IT, making it challenging for data security teams to protect it. DSPM identifies abandoned data stores across cloud platforms such as Amazon Web Services, Microsoft Azure and Google Cloud Platform.
Reduce your attack surface and storage costs
By eliminating low-value, ungoverned data, DSPM reduces your attack surface and cloud storage spend.
Lower your risk, strengthen your compliance
Due to poor governance, internal users and service accounts often retain write access to abandoned data. Sometimes this also extends to third-party users and services, posing significant risk. DSPM reveals access permissions for your abandoned data. This enables precise access revocation, reducing your exposure and closing compliance gaps.
Key features for discovery of abandoned data
Continuous scanning
DSPM continuously scans across your environments to identify obsolete, abandoned or redundant data.
Flagging of stale data
DSPM highlights stale storage objects and backups that are suitable for archival or deletion. Targeted filters help you prioritize high-cost, high-risk abandoned data for triage.
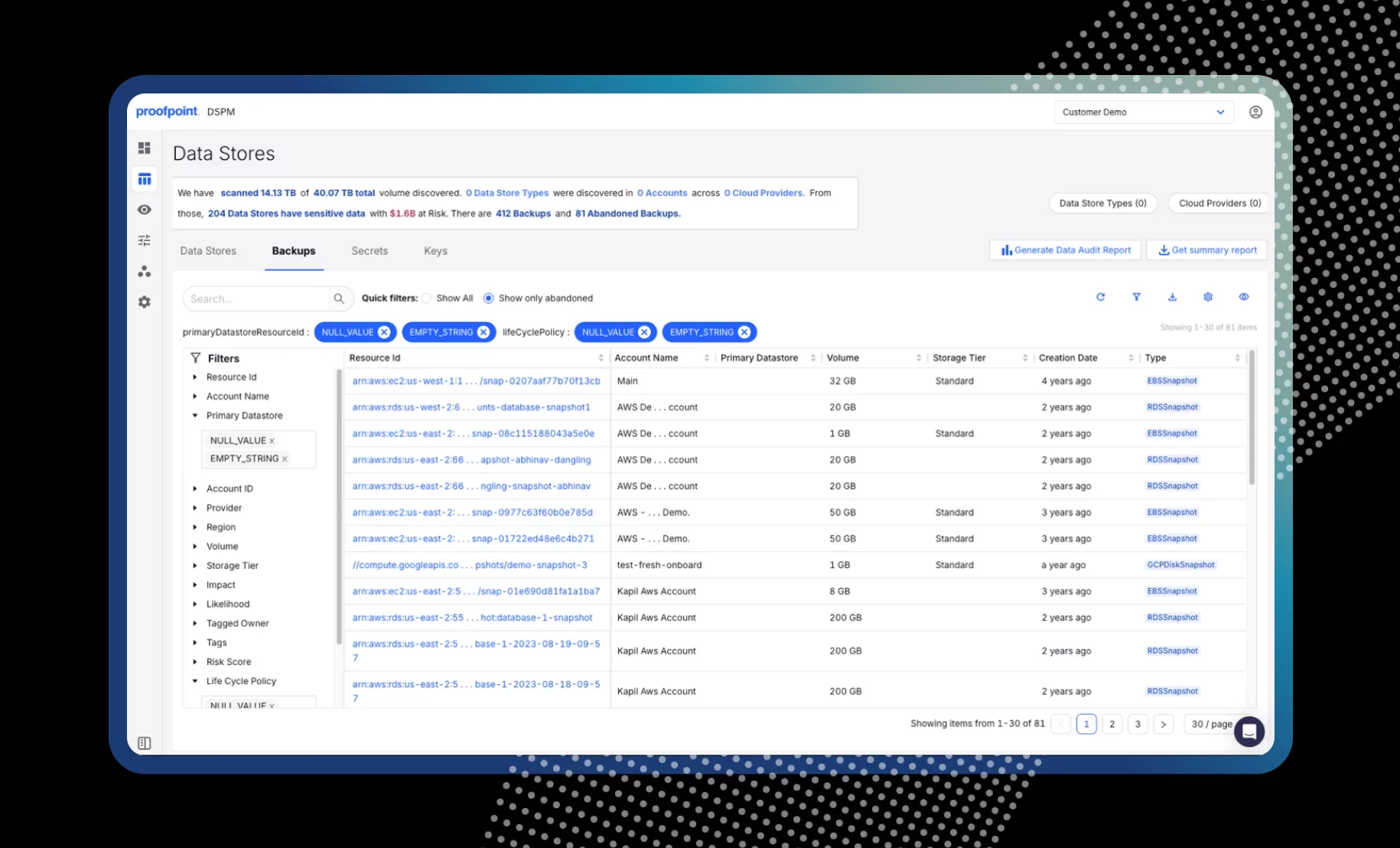
Risk evaluations
For every abandoned data store or backup that it uncovers, DSPM evaluates associated risks. This gives you the context you need to act.
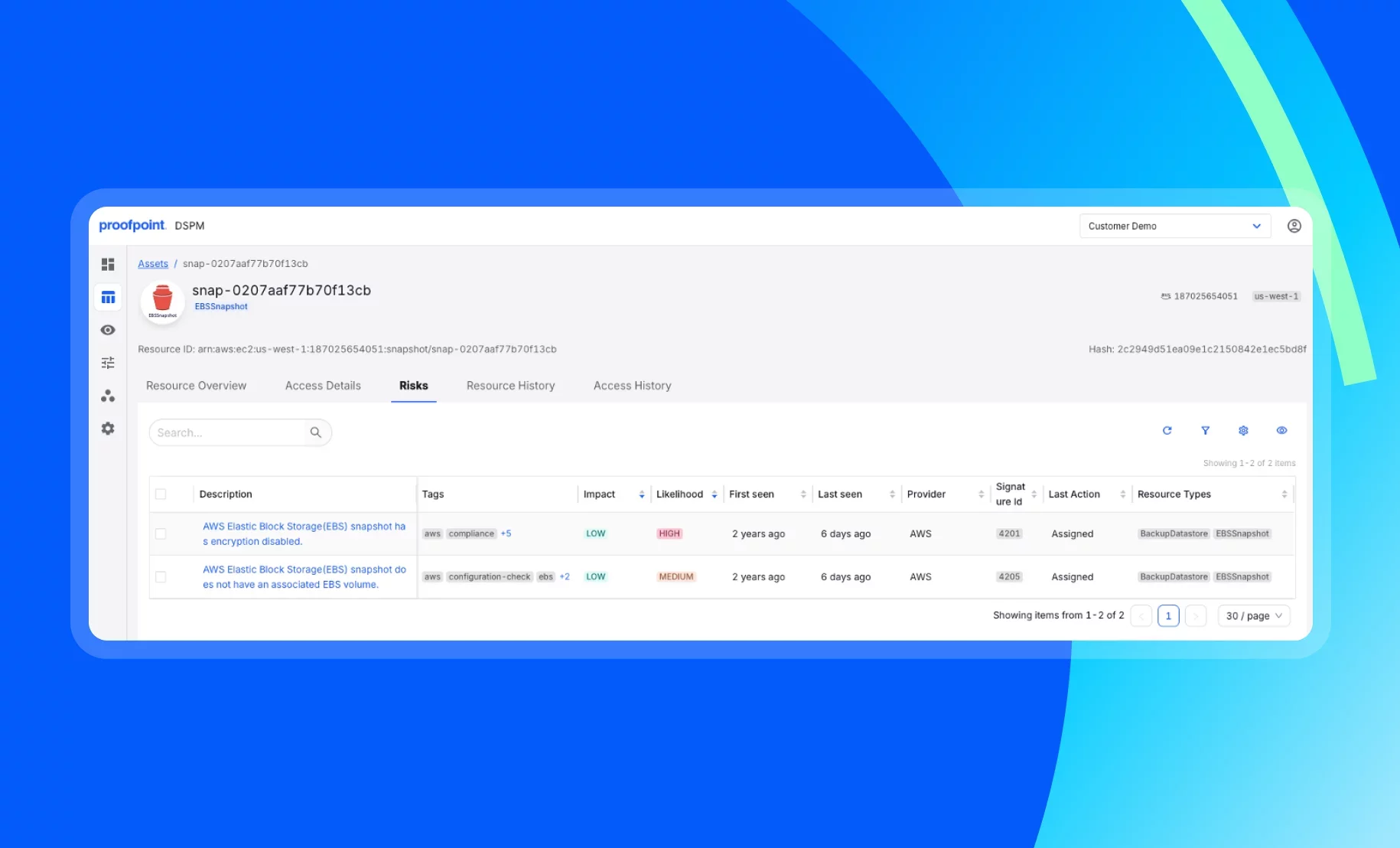
Detailed access views
Using detailed access views, see which users and roles can access your abandoned data stores. This includes external users and roles. By knowing when each role last accessed data, you can precisely revoke permissions.
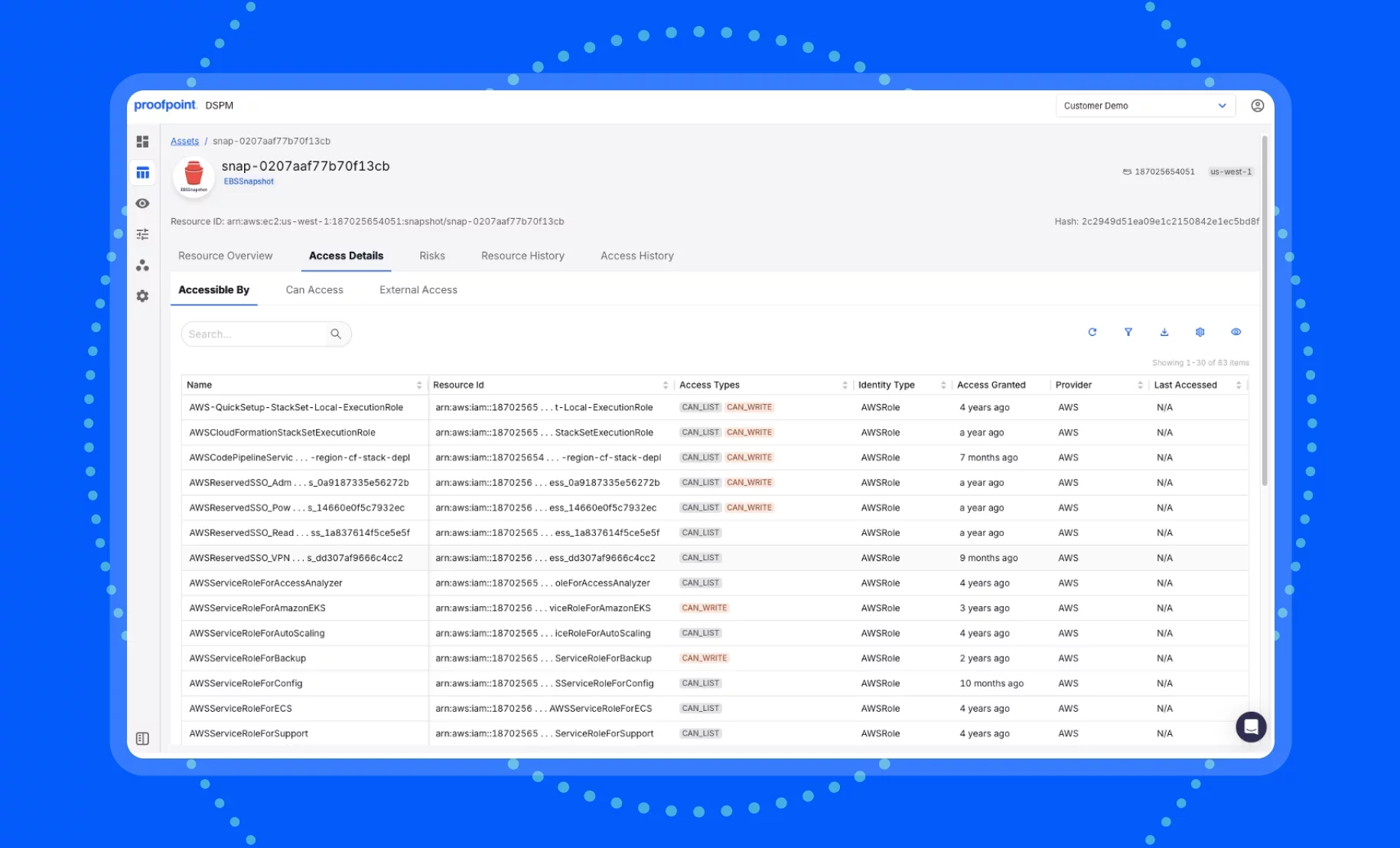
Access histories
See a detailed access history for each of your abandoned data stores and backups. This context helps you decide what data is safe to clean up.
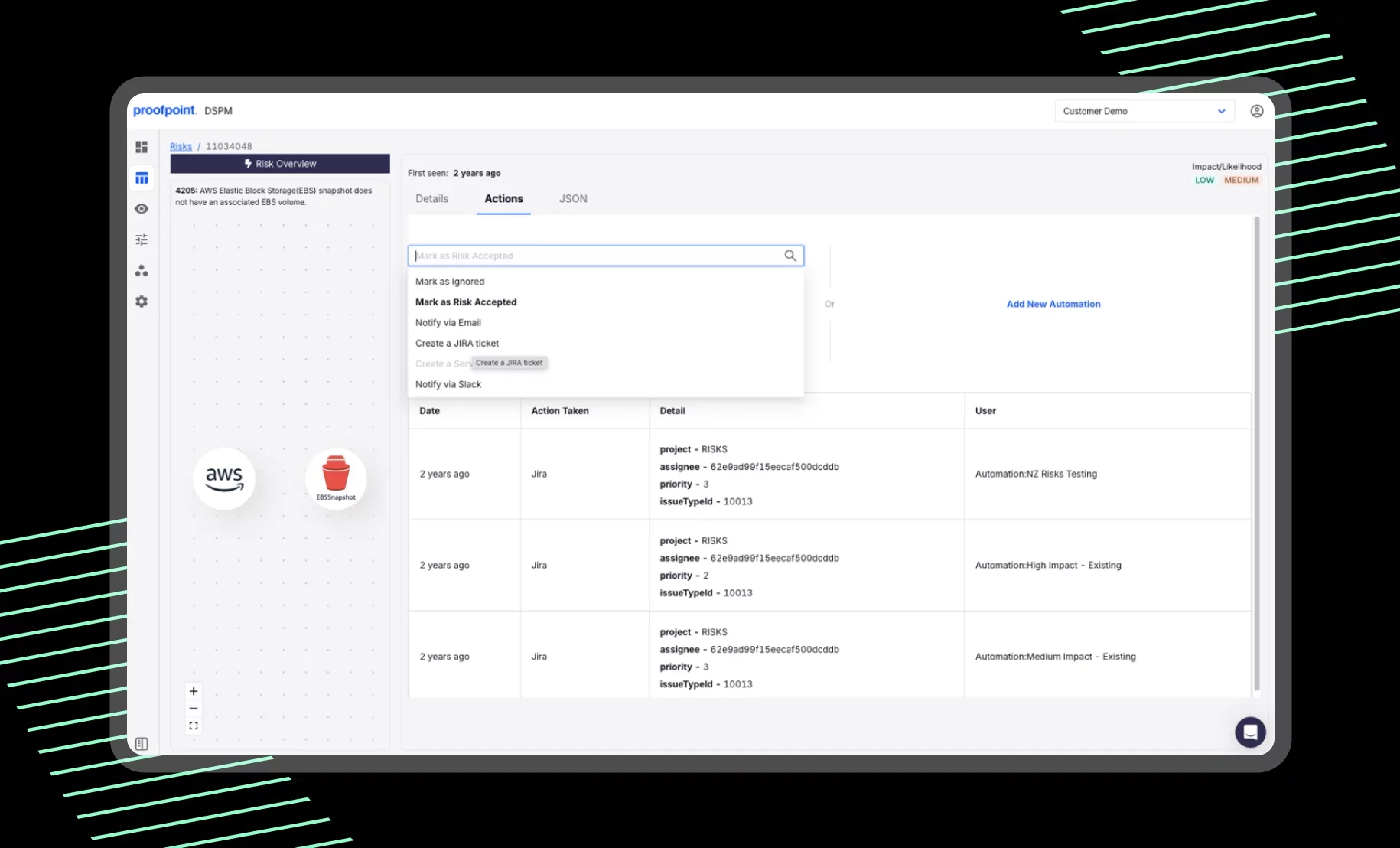
Guided risk remediation and audit trails
Proofpoint turns analysis into action. DSPM enables security teams to triage risks and launch guided remediation actions such as opening Jira tickets or creating email and Slack notifications. Proofpoint preserves audit logs for every decision made, ensuring traceability and compliance.
The latest resources on securing your data

Continuously Strengthen Your Data Security Posture with Proofpoint DSPM
Read More










