Last updated: August 15, 2018
Apps on mobile devices have proven to be very popular, with millions of apps and billions of downloads. Apps can make use of a mobile device’s capabilities, accessing our current location, contact list, call logs, and more. Some apps use these capabilities to improve the functionality and usefulness of apps. However, other apps surreptitiously use these same capabilities in surprising and often privacy-invasive ways.
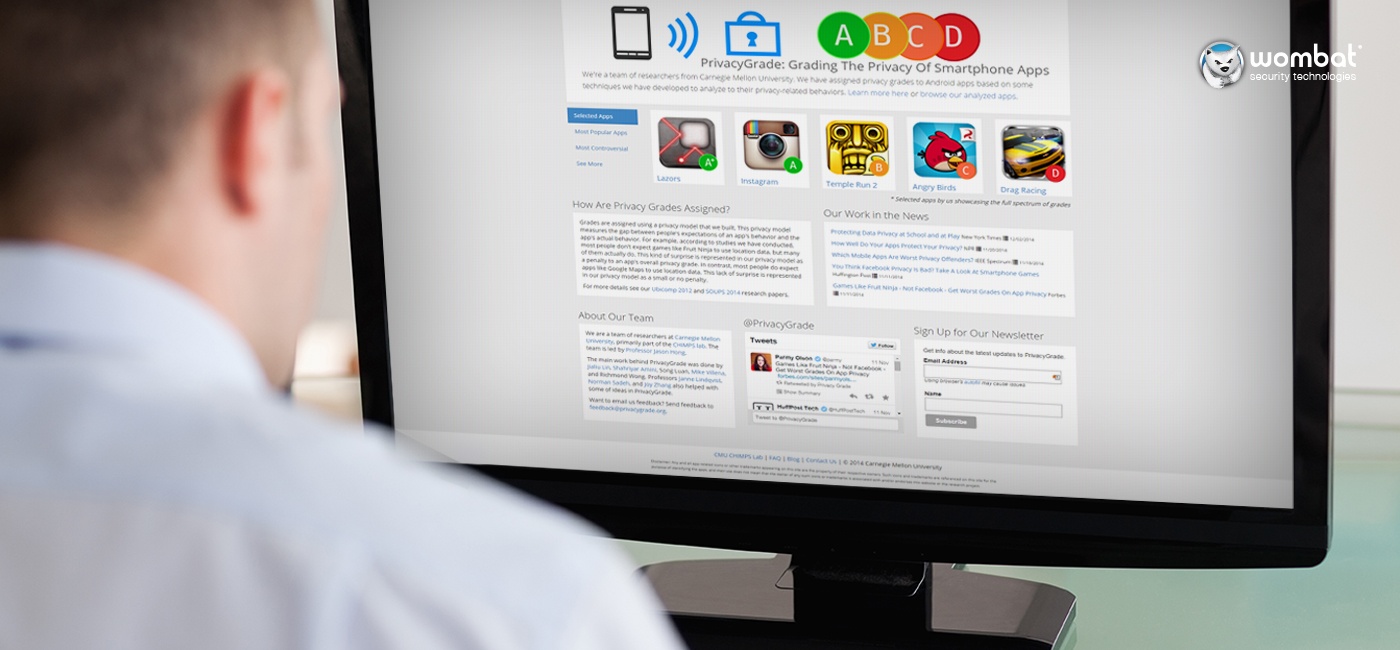
Right now, it’s not easy for everyday people to understand what an app is actually doing with one’s data. To address this problem, one of Wombat Security’s co-founders, Jason Hong, led a team at Carnegie Mellon University in creating PrivacyGrade.org. PrivacyGrade is a website that analyzes the privacy of more than one million Android mobile device apps. The resource been featured in the New York Times, CNN, Forbes, US News and World Reports, CNBC, IEEE Computer, and more.
This blog post looks at how PrivacyGrade works, as well as what steps you can take to protect yourself and your end users from overly intrusive apps.
Q: How does PrivacyGrade work?
A: Apps are assigned grades based on how much sensitive data they use and how expected those uses are. For example, according to studies we have conducted, most people would not expect a Black Jack game to use location data, but there are some that actually do. This kind of surprise is represented in our privacy model as a penalty to an app’s overall privacy grade. In contrast, most people do expect apps like Google Maps to use location data. This lack of surprise is represented in our privacy model as a small or no penalty.
Q: What are some surprises you’ve seen with apps and privacy?
A: The biggest surprise most people have is that many ad-based games use location data. I’ve given lots of talks about our team’s privacy research, and people have come up to me afterward telling me how they deleted some games during my talk because they were so surprised by their app’s behaviors.
Now, it’s important to emphasize that many free apps are free because of advertising. These developers need a way of making money from their hard work. Another surprise we’ve seen, based on interviews and surveys we’ve conducted, is that app developers often aren’t aware of the privacy-intrusive behaviors of their own apps.
If you imagine that an app is made out of Lego blocks, some of the Lego blocks are made by other developers. These are called third-party libraries, and they offer useful functionality like connecting to Facebook or connecting to advertising services. It’s often the case that it’s these third-party libraries that are making use of the device owner’s data, rather than the app itself. The problem is that app developers often don’t know what these third-party libraries do.
Q: What can a non-technical person do to help protect their privacy?
A: You can double check what permissions an app uses. For Android phones, you can see what permissions it uses before installation. For iOS, apps request for permission right before sensitive data is used the first time.
A second option is to put your mobile device in airplane mode, which makes it so that apps can’t access the network or location data. This is obviously pretty inconvenient (because you can’t receive or make phone calls in airplane mode), but some apps still work perfectly fine in airplane mode.
Q: What other kinds of risks are there with apps on mobile devices?
A: There are also fake apps and malware on app stores. The most popular app stores try to remove these as quickly as they can, but sometimes bad apps still get through.
Fake apps are ones that pretend to be real apps. Most fake apps are real apps that have been modified. For example, a thief might download a real app, modify it so that the thief gains the advertising revenue rather than the actual developer, and then upload it back to an app store.
Apps that contain malware are generally designed to steal information. Sometimes these are custom apps for spying on people, sometimes they are real apps that have been modified, and sometimes they are fake apps.
For example, a few years ago, there was a fake Netflix app that used the Netflix icon, but just ended up stealing your password.
Q: How can people protect themselves from these fake apps and malware?
The key here is to look for signals that are hard for bad guys to fake. For example, an attacker can name their app anything, and can give the app any description they want. However, they can’t change the upload date on app stores, or the number of downloads. So these latter two are pretty good signals for differentiating between legitimate apps and fake apps. That is, the older the app, and the more downloads, the higher the odds that the app is safe.
Several Wombat interactive training modules focus on key components of mobile device security, including the safe use of mobile apps. It’s important to recognize that app permissions are just one of many potential dangers to the data stored on mobile devices. These cybersecurity education modules will help users make better decisions about the apps they install as well as help them understand appropriate physical and technical safeguards; best practices for secure communications; and tips for safe use of GPS, WiFi, and Bluetooth features.












