Overview
Proofpoint researchers have discovered over 100,000 Bitcoin-related domains as of the beginning of this year. The majority of these domains are considered suspicious and could be used for typo-squatting, social engineering, and malware distribution. As the value of Bitcoin increased, we also saw the number of related suspicious domains increase.
Bitcoin Domains
Proofpoint researchers discovered over 102,000 “Bitcoin-related” domains as of January 12, 2018. We define Bitcoin-related domains as domains that contain the word “bitcoin” or variations of that word in the domain. Variations of the word “bitcoin” may include various typo-squatting techniques, such as:
- Homoglyph attacks, including the replacement of a letter by a similar character, as in “bitc0ins.com”, where the letter “o” is replaced by the number zero. Our analysis identified approximately 50 domains that fell into this category.
- Common typographic errors, such as replacing a letter in the domain with a character in close proximity on the keyboard, accounted for over 95% of the domains analyzed. One such example is “bitcoim.com”, where the “n” is replaced with “m” due to their relative location on the keyboard. Other common typos include: repeating a character twice, as in “biitcoin.com”, and omission of a character, such as “btcoin.com”, where the “i” is omitted.
- Punycode spoofing, a technique for representing Unicode with ASCII characters for Internet host names. For instance, the domain “xn--bicoin-j17b[.]com”, which as-is appears related to “bitcoin”; converted to Unicode it is in fact rendered as “biṭcoin[.]com”. Less obviously, the domain “xn--9naa4azkq66k5ba2d[.]com” appears clearly unrelated to Bitcoin, but in Unicode is rendered as “ʙɪᴛᴄᴏɪɴ[.]com.”. Our analysis detected over 200 such domains.
The majority of domains in our dataset contain the word “bitcoin” itself, but with other words associated with it, with such innocuous examples as “bitcoinpay[.]com” or “bitcoinbank[.]com”. We found that over 98,000 domains are of this variety. Employing the origin domain, “bitcoin” in combination with other words in order to carry out a range of attacks is a common form of social engineering.
Our analysis also discovered domains that were registered by the same user. We have seen over 300 Bitcoin-related domains registered by the same user, and at least 600 users registered 10 or more Bitcoin-related domains. While this does not imply malice by the domain owners, it does highlight the increased interest in the cryptocurrency.
Suspicious Domains
We found over 30,000 domains in our sample to be suspicious, almost 30 percent of the total. Proofpoint researchers employ numerous criteria to determine if a domain is malicious, including but not limited to WHOIS information and sandbox analysis. Analyzing one such domain, instantbitcoinbuy[.]com, quickly reveals why. When users visit this website a Mac using the Safari browser, the site presents a prompt to download an update for Adobe Flash Player:
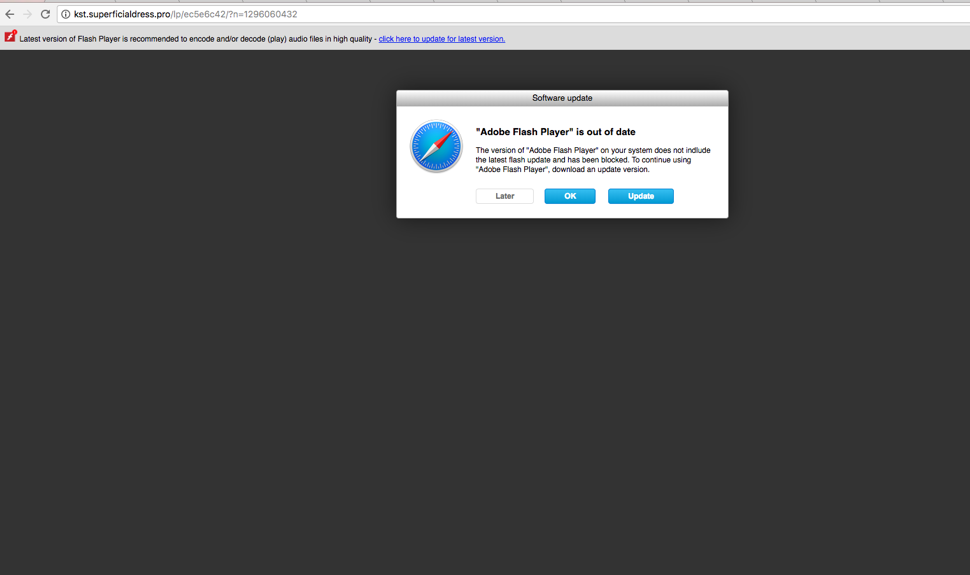
Figure 1: Visiting a suspicious Bitcoin-related domain on Mac
The popup dialog bears a reasonable similarity to a common notification dialog that the user’s Adobe Flash Player is out of date. Compare this with the real popup message displayed by Safari on a site prompting a legitimate update:

Figure 2: Legitimate Safari popup message
While the language in the two dialogs is similar, clicking any of the buttons in the popup on the suspicious domain downloads the file “Adobe Flash Update.dmg,” which is actually malware:
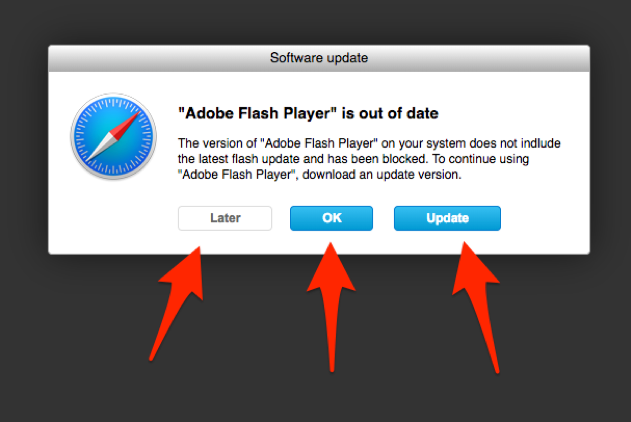
Figure 3: Malicious Adobe Flash Player popup
We should also note the warning message at the top of the user’s browser. This message is not a part of the browser, and the link at the end of this notification also downloads the same malware file:
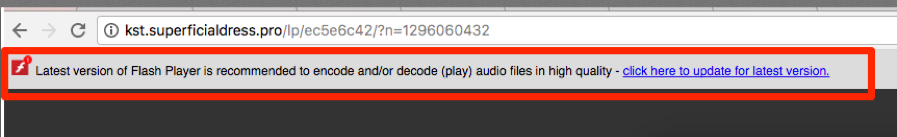
Figure 4: Malicious Adobe Flash Player warning
When users visit instantbitcoinbuy[.]com with a different browser, they are redirected to a different site. Here is one such redirect in Chrome:
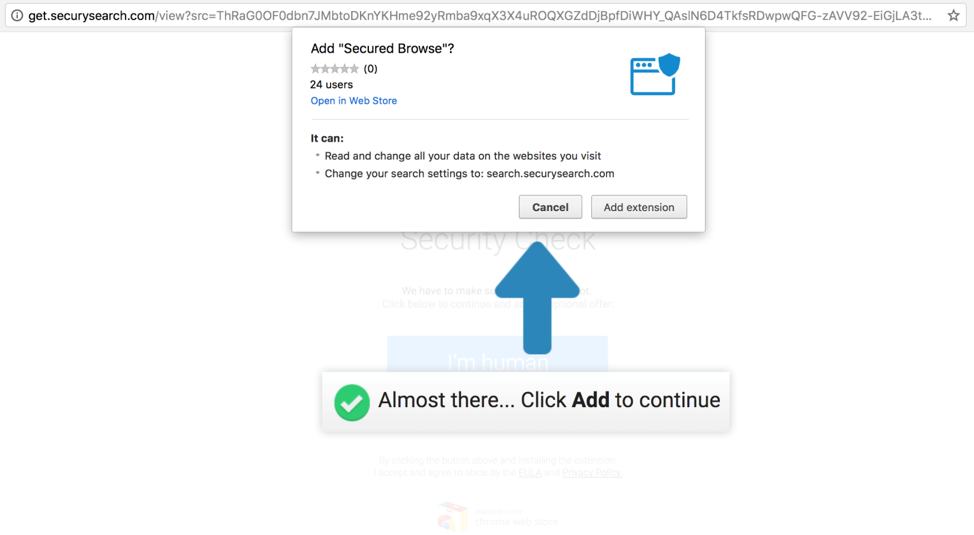
Figure 5: Visiting the same site on Chrome
When visited on Chrome, notice that the user is prompted to install a plug-in extension, and that this software is asking for permissions to read and change all the data on the websites the user visits. Moreover, all of the user’s searches are sent to the site “search[.]securysearch[.]com,” (note the missing “it” on “securysearch”) which is a fake Internet search engine that claims to give the user a more secure browsing experience and protect them from malicious websites and phishing attacks. However, the installed extension modifies the user’s browser options and records their browsing activity, including private information. While analyzing the 500 most recently registered domains as well as the last 100 registered in 2017, we identified 11 that are known to be malicious based on our internal data. While this is not indicative of all of the threats that may reside on these domains, this does highlight the domains that are known to Proofpoint as being malicious.
Bitcoin Price vs. Number of Suspicious Domains
Comparing the volume of suspicious domain registrations with the price of Bitcoin through 2017, we identified a strong relationship between the number of registered domains per month and the price of Bitcoin for that month:
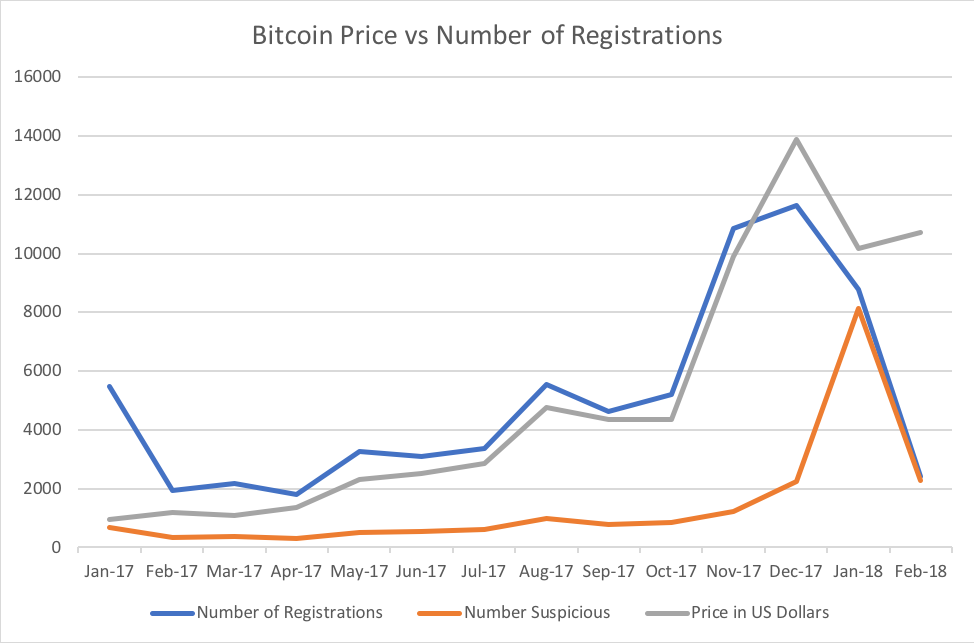
Figure 6: Bitcoin price vs. Bitcoin-related domain registrations and registration of suspicious Bitcoin-related domains
As Figure 6 shows, as the price of Bitcoin increased so did the number of suspicious domain registrations. Suspicious domain registrations increased faster than Bitcoin-related domain registrations as a whole. Of note, the number of registered domains maintained a roughly one-to-one ratio with the US Dollar price for Bitcoin for that month (notice that we chose to use only one y-axis for these two lines). Much like the exponential growth of Bitcoin’s price, the number of domains skyrocketed towards the end of 2017.
Conclusion
Threat actors continue to capitalize on trends and public interests to improve their social engineering schemes. Cryptocurrency in particular has provided new opportunities for criminals to “follow the money” – in this case they have collectively assembled over 100,000 Bitcoin-related domains that can be used for a variety of malicious purposes. While Bitcoin values have dropped off dramatically in recent months, cryptocurrency remains the currency of choice for threat actors and blockchain-based technologies are here to stay. We will continue to monitor these trends as the landscape evolves.
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
instantbitcoinbuy[.]com |
URL |
Example URL used in a Bitcoin lure to deliver malware |











