Since it was first detected in November 2014, Dridex has been one of the most prolific pieces of malware worldwide. Even when the actors behind distribution of Dridex began distributing Locky ransomware in February, 2016, they would often switch between the two payloads or distribute them simultaneously. More recently, though, Dridex email message volumes have dropped to a relative trickle, and a new geography of interest, Switzerland, has emerged. The much lower volume suggests a higher degree of targeting, freeing the actors to pursue more lucrative attacks and leverage stolen information more effectively.
In this post we’ll investigate the recent Dridex campaigns, including their message volumes and targeting, and provide possible reasons for changes in the mode of operation.
Overall Dridex Activity
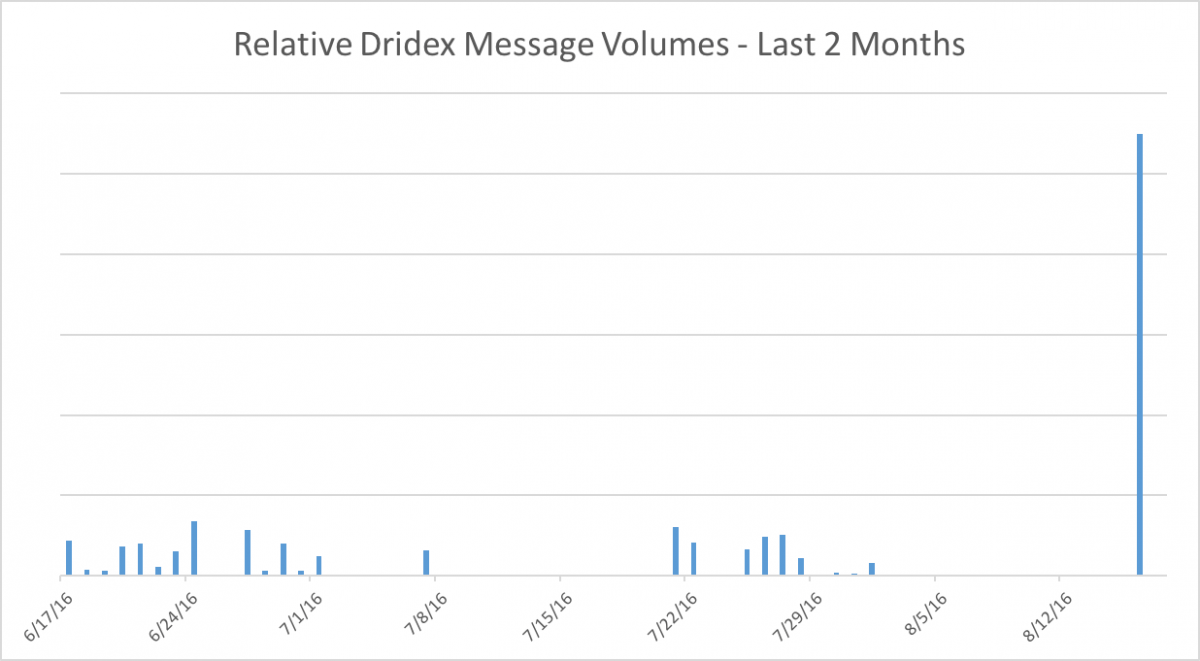
Throughout July and August 2016, we have tracked a number of very small Dridex attachment campaigns, varying from single digits to a couple thousand messages each. On August 15 and 16, the largest observed campaign since the middle of June delivered tens of thousands of messages, primarily targeting financial services and manufacturing organizations. However, this volume does not even approach the multimillion-message campaigns of May 2016. Figure 1 shows relative message volumes for Dridex campaigns over the last two months.
Figure 1: Indexed relative Dridex message volumes since mid-June 2016
While Figure 1 above represents the email message volume since June 15, the following is a listing of example botnet IDs observed during in this period:
Dridex botnet 1124 (Switzerland targeting) - August 17
Dridex botnet 228 (UK, AU, FR targeting) - August 15-16
Dridex botnet 144 (Switzerland targeting) - August 11
Dridex botnet 1024 (Switzerland targeting) - August 10
Dridex botnet 1024 (Switzerland targeting) - August 9
Dridex botnet 1024 (Switzerland targeting) - August 2-3
Dridex botnet 1024 (Switzerland targeting) - July 29
Dridex botnet 1024 (Switzerland targeting) - July 26-27
Dridex botnet 124 (Switzerland targeting) - July 15
Dridex botnet 302 (UK targeting) - July 12
Dridex botnet 38923 - (Switzerland targeting) - July 7
Example Campaign: Dridex 228
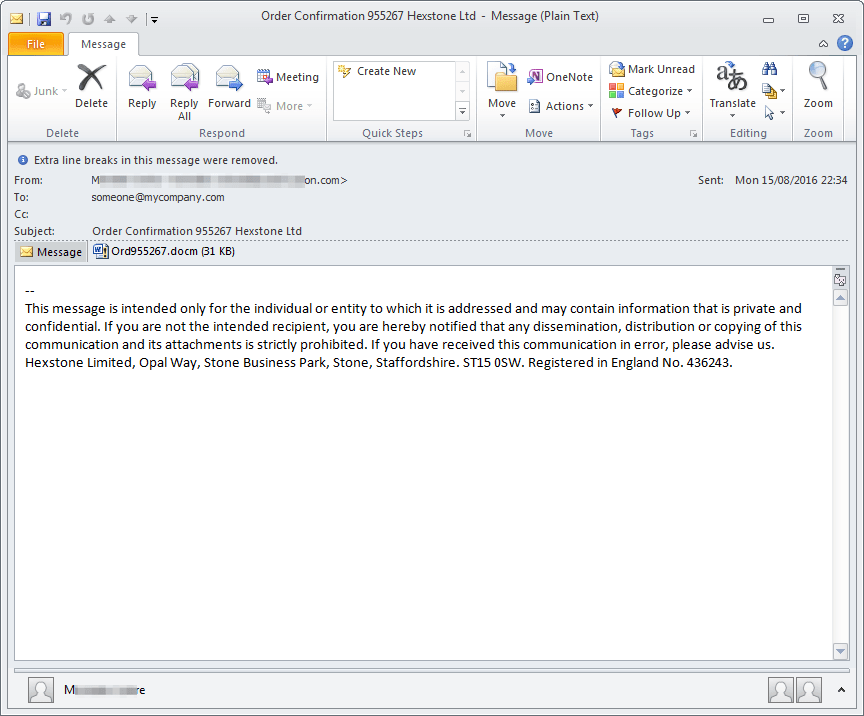
The August 15-16 Dridex (botnet ID 228) campaign is of particular interest due to its larger than average message volume. This botnet contained configurations for banking sites in the United Kingdom, Australia, France, and the United States. The emails distributing the botnet contained macro-laden Word attachments (.docm files). Figure 2 shows an example email with an “order confirmation” lure.
Figure 2: English-language email delivering the Dridex 228
The digits after "Order Confirmation" in the subject are random and match those in the file name.
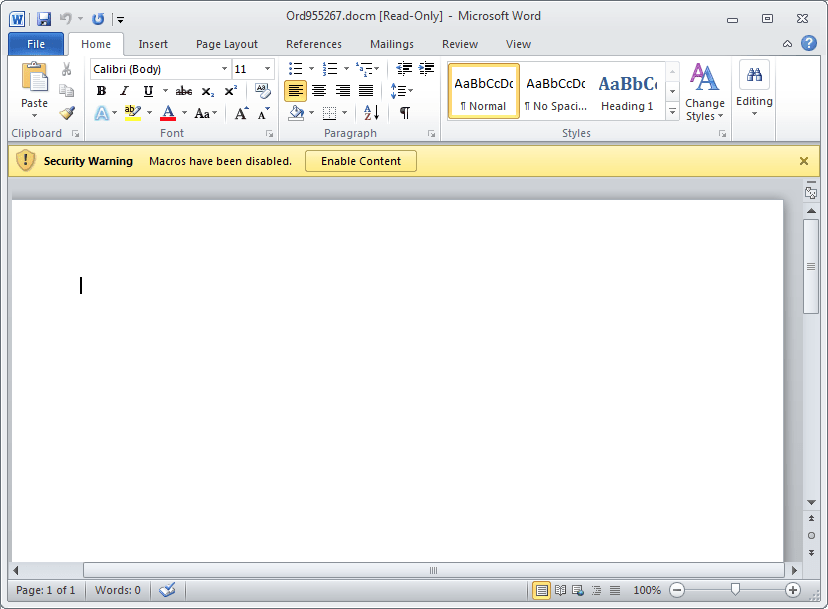
Figure 3: Example of malicious document attachment. The .docm files still require users to enable the embedded macros. In this case, enabling the macros allows the malicious documents to download Dridex (botnet ID 228).
This instance of Dridex targets a number of back-end payment processing and transfer, Point of Sale (POS), and remote management applications. While the expansion of targeted Windows applications was already pointed out by MELANI [1], Appendix A provides the the latest full list that we observed in this campaign.
However, targeting applications is not new and Dridex has targeted POS, banking, and other applications in the past. Appendix B includes an example of application targeting from July 2015. The current targeted list is substantially expanded by comparison.
Example Campaign: Dridex 144
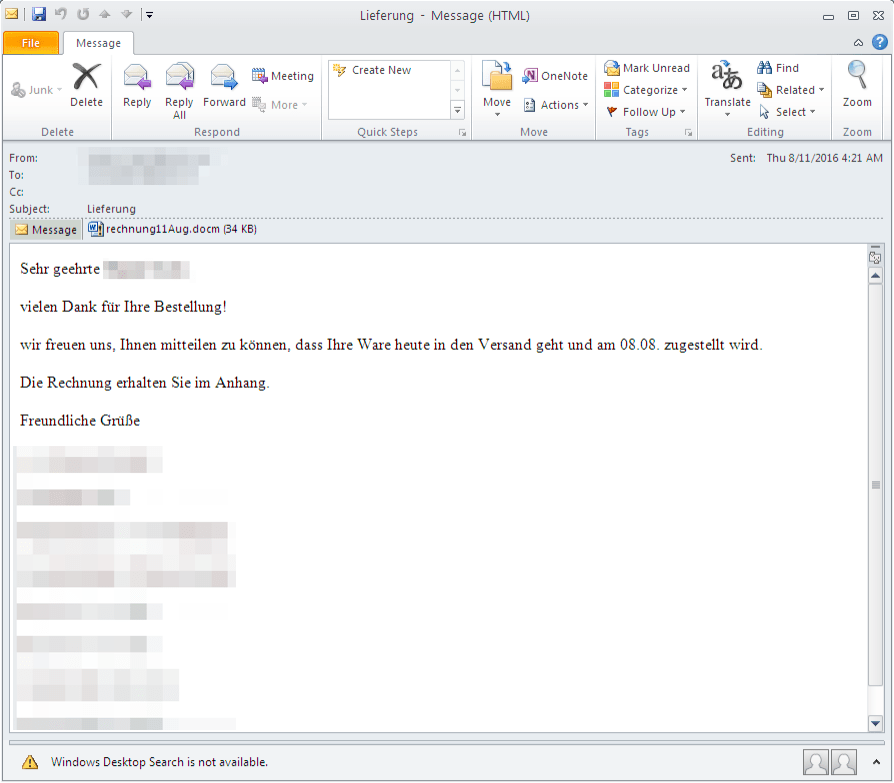
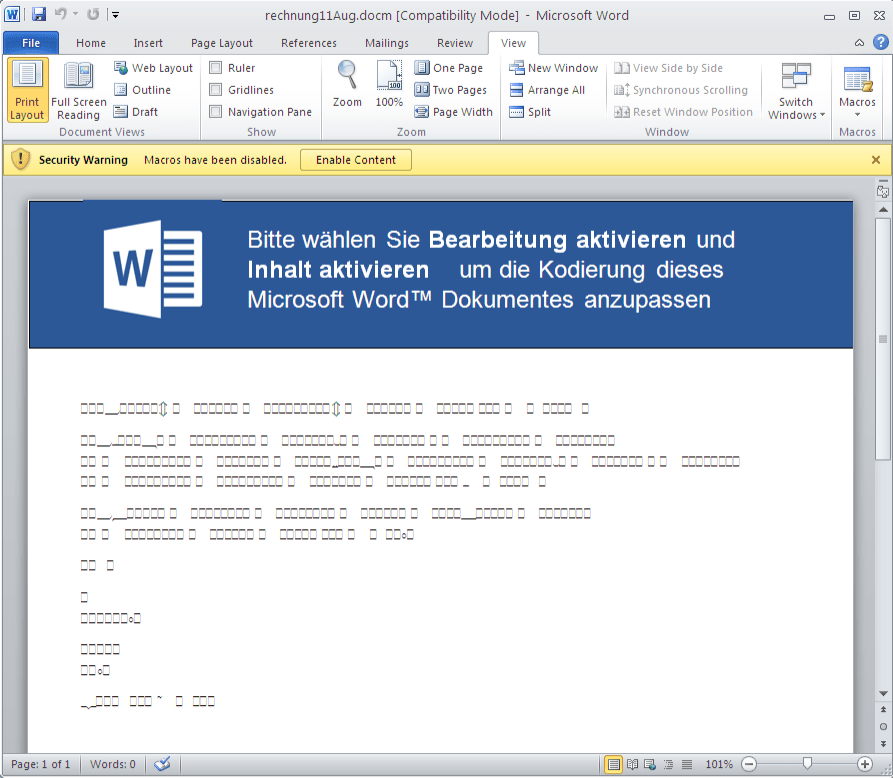
On August 11, we observed a Dridex campaign with Microsoft Word .docm attachments. If opened and their macros are
enabled, these attachments download and install Dridex botnet ID 144 with configuration targeting various banking sites, including several in Switzerland. The messages in this campaign had the subjects "Lieferung” (“Delivery” in German) with various attachment names, including “rechnung11Aug.docm” (“bill11Aug” in German). Note that German is one of the primary languages used in Switzerland.
Figure 4: German-language email delivering Dridex 144
Figure 5: Example of malicious document attachment, which downloads Dridex (botnet ID 144) if the user enables the macro.
This instance of Dridex targets the same banking back-end and other applications as the 228 botnet. Example banking sites targeted by the injects include raiffeisen.ch and postfinance.ch.
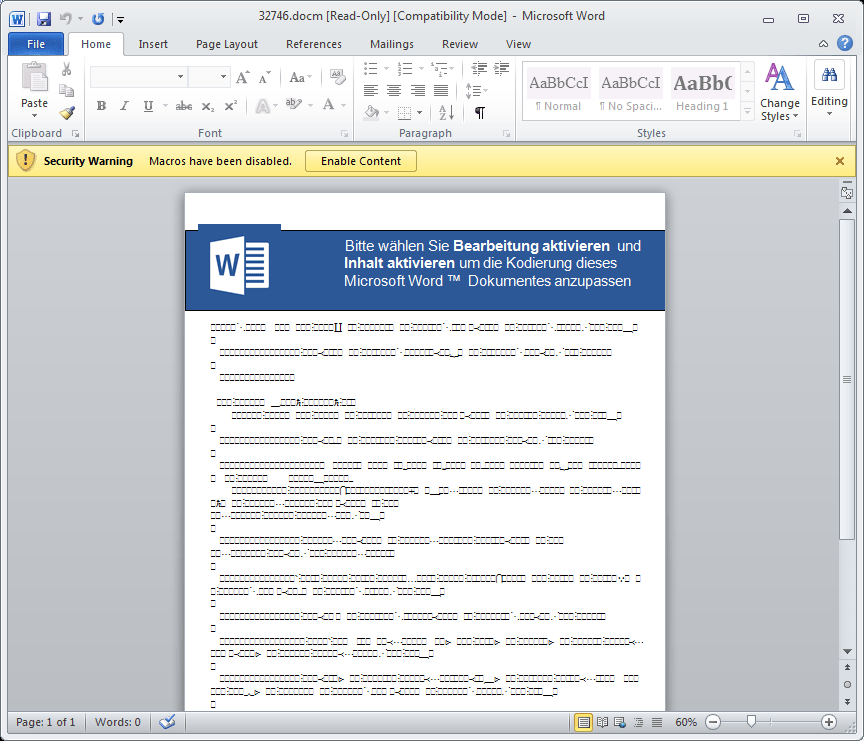
Example Campaign: Dridex 124
On July 15, we observed yet another Dridex campaign with Microsoft Word .docm attachments. If opened, and macros enabled, these attachments download and install Dridex botnet ID 124. Configurations in this instance also include targeting for various Swiss banking sites. The messages in this campaign had the subjects "WG: Gutschriftsanzeige zu RG 123456 // 7654321 Arvato Geburtstagskarten Art. 12345" (random digits) and attachments named "RECHNUNG Nr. 654321.zip" containing "54321.docm" (random digits). Again, both the email and attachment were written in German.
Figure 6: German-language email delivering Dridex 124
Figure 7: Example malicious document attachment, downloads Dridex (botnet ID 124).
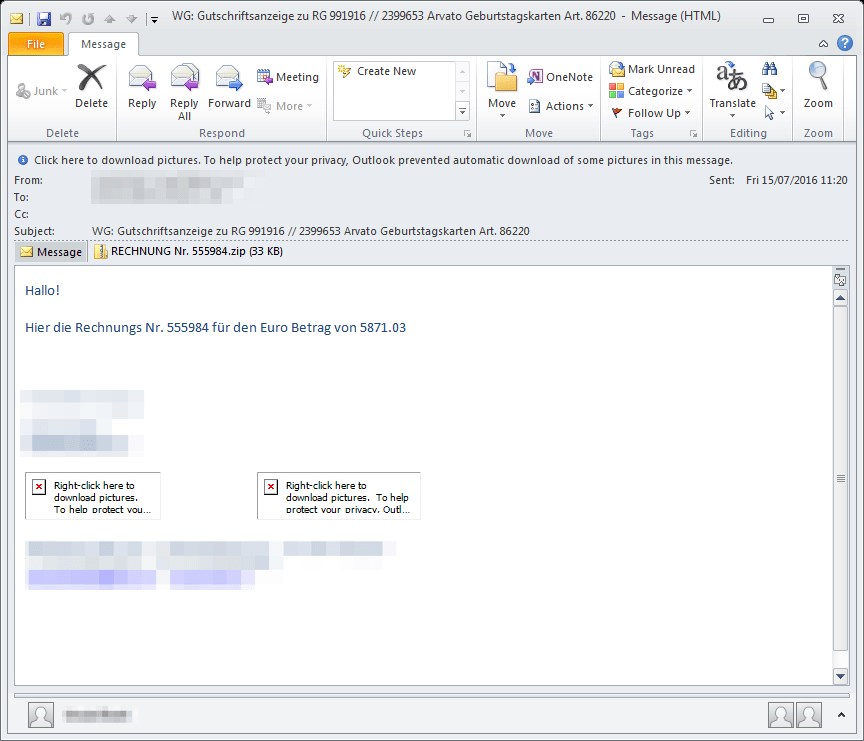
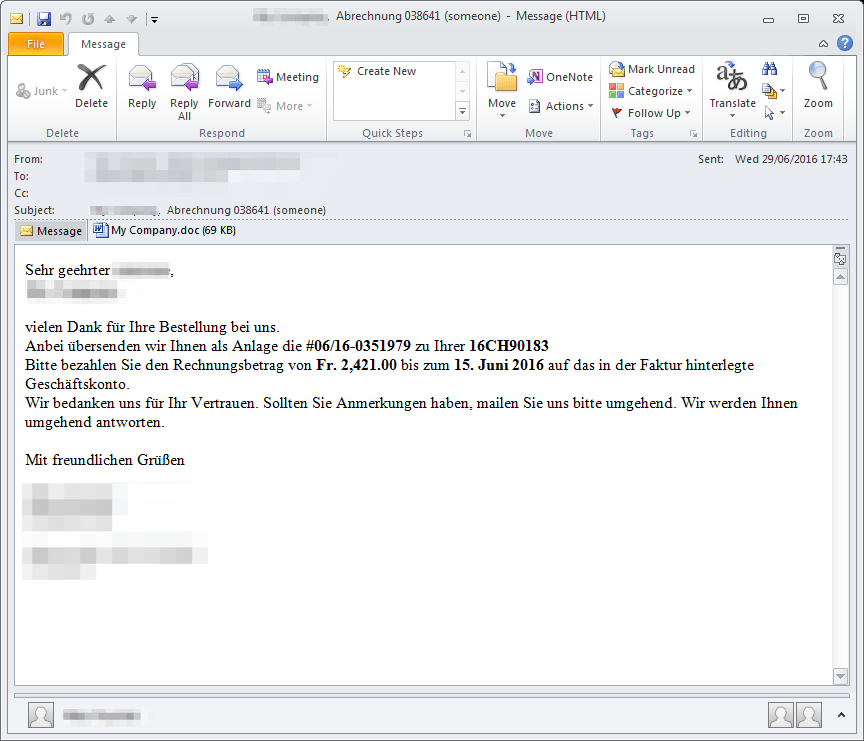
Example Campaign: Dridex 38923
On June 29, we observed a small Dridex campaign with MS Word .doc attachments. If opened, and macros enabled, these attachments download and install Dridex botnet ID 38923 with configuration targeting various banking sites, including those in Switzerland. The messages in this campaign had the subjects "[Company], Abrechnung 038641 [someone]" and attachment "[Company].doc". Once again, both the email and attachment were in German.
Figure 8: German-language email delivering Dridex 38923
Figure 9: Example malicious document attachment, downloads Dridex
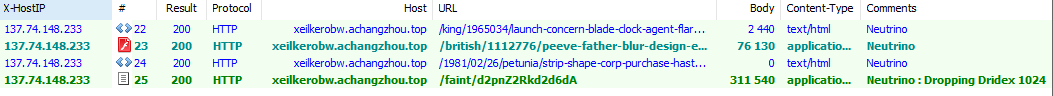
Dridex Via Exploit Kits
Finally, we continue to see Dridex spreading via exploit kits. For example, on August 9, we observed Neutrino Exploit Kit dropping Dridex botnet ID 1024 in Switzerland and the United Kingdom.
Figure 10: Network capture showing Neutrino infection leading to Dridex 1024
Conclusion
The Dridex banking Trojan has been thoroughly analyzed by Proofpoint and other researchers worldwide due to its substantial footprint and impact and prominent place in the high-volume email malicious document campaigns of 2015 and early 2016. However, the recent shift to more targeted distribution and a growing set of capabilities suggest that Dridex may be taking on a new life even as the high-volume campaigns shift to distributing almost exclusively Locky and its associated payloads. While these large campaigns may have saturated many target countries, Dridex actors are still looking to monetize the malware by targeting a smaller number of large organizations, many in financial services.
As to the drivers behind this shift in tactics, our investigations suggest that the current mode of operation involves identifying systems of interest (containing back-end payment software) automatically with specific Trojan configurations and then allowing the operators to make a decision as to what malware to download next or investigate the system manually through VNC.
References
Indicators of Compromise (IOC’s)
|
IOC |
IOC Type |
Description |
|
313e2282bffcd2df612404c7ab6e7e913495c13b6f3011c1a2739e289b5451b6 |
SHA256 |
June 29 Dridex 38923 document “[name].doc” |
|
1fe24808cabd3fa69e58824a58a1e302ce677362603d4f26240cff7c145421b5 |
SHA256 |
July 15 Dridex 124 document “1666.docm” |
|
1a6859d265b94a2109d690999f62fdbadd8cb1894205e2e1b260a9f3bdcd8639 |
SHA256 |
August 11 Dridex 144 document “rechnung11aug.docm” |
|
026b724fe9d07d47f8fcdf02f7e1072a74bc518e415430a2c23881fb179b4a99 |
SHA256 |
August 15/16 Dridex 228 document “Ord191878.docm” |
|
10cf55031c31f8a615b93cec9d3675b6af2fb7d9aa4ef5163723b55e43b9a9f4 |
SHA256 |
Dridex 38923 Loader |
|
207b4ae38b3a5c51614aacd6b9d09bff242b23fab777446e9f752eefde57bac8 |
SHA256 |
Dridex 124 Loader |
|
75717e7acf4f41de953e0c6f57986844bc21dcda546d5a37371ad8d5a7952782 |
SHA256 |
Dridex 144 Loader |
|
160c95261abba3e71c52195251db075ed922acdf010aa85fef1760e8fa198bd8 |
SHA256 |
Dridex 228 Loader |
|
bcaa57c93dc973aabd419b65dcdc4e9ae68bcae5ddfe920070cc2b2ae9dbaf3f |
SHA256 |
Dridex 1124 Loader |
|
2d9c2edc8d1cfb2b5691b0f6a938d17d5adf1e7797ab401dfa12bd29df79af44 |
SHA256 |
Dridex 302 Loader |
|
fc39a8ef9567ce977215b8699762843d4f8a98504d9495bf9f8edad0a60b5fcb |
SHA256 |
Dridex 1024 dropped by Neutrino |
Select ET Signatures that would fire on such traffic:
2022627 || ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex)
2404306 || ET CNC Feodo Tracker Reported CnC Server group 7
2404312 || ET CNC Feodo Tracker Reported CnC Server group 13
Appendix A: Applications Targeted by Dridex 228 on August 16, 2016
crealogix | multiversa | abacus | ebics | agro-office | cashcomm | softcrew | coconet | macrogram | mammut | omikron | multicash | quatersoft | alphasys | wineur | epsitec | myaccessweb | bellin | financesuite | moneta | softcash | trinity | financesuite | abrantix | starmoney | sfirm | migrosbank | migros bank | online banking | star money | multibit | bitgo | bither | blockchain | copay | msigna | armory | electrum | coinbase | magnr | keepkey | coinsbank | coolwallet | bitoex | xapo | changetip | coinapult | blocktrail | breadwallet | luxstack | airbitz | schildbach | ledger nano | mycelium | trezor | coinomi | bitcore | WinBacs | albacs | Albany.EFT.Corporate.Client | wpc | eSigner | StartStarMoney | StarMoney | acsagent | accrdsub | acevents | acCOMpkcs | jp2launcher | sllauncher | cspregtool | RegisterTool | OEBMCC32 | sfirm | Bbm24win | wip | paypen | mammut_tb | telelink | translink | deltaworks | dfsvc | bitcoin-qt | multibit | BacscomIP2 | runclient | paycentre | accesspay | PaymentStudio | DiasClient | SynIntegrationClient | QuestLauncher | RemoteAdminServer | SymForm2App | plink | launch | PaygateWpfClient | terminal | Telelink | EBsec | ftrskr | Suite Entreprise | rbpmain2 | rbpmain | tkc | ecbl-nxbp | sagedirect | turbo_teletransmission | cedripack | cedrisend | QikDesktop | QikDesktopCitrix | ConfigurationEditor | InteractFastConfig | otscm-client | ecb-sg | crs1 | GbpSV | pstw32 | MopaMaes | ldcptv10 | gslshmsrvc | launcher | tokensharesrv | universe | ifrun60 | roiwin31 | guawin32 | intwin31 | kb_pcb | spawin31 | cziwin31 | czawin31 | sta2gpc | etsr | tellerlauncher | prowin32 | dirclt32 | PLT1751 | PLT1151 | cegidebics | CCS3 | CCMPS3 | ComSX | keepass | c_agent | transac | relaisbtp | telebanking | ewallet | mstsc | cardentry | TPComplianceManager | TPWorkstation | BancLine 2.0 | MS000000 | BancLine 3.0 | BancLine 4.0 | BancLine 5.0 | SFW | ptw1151 | fedcomp | sfmain | VRNetWorld | KDS | Kasir | ICS | mpkds | pspooler | ipspool | POS-CFG | callerIdserver | EftTray | dpseftxc | EFTSERV | QBPOS | APRINT6 | POSCONFG | jRestaurant | AFR38 | rmpos | roi | AxUpdatePortal | Firefly | InitEpp | SM22 | xfsExplorer | XFSSimulator | WosaXFSTest | kiosk | CRE2004 | aspnet_wp | javav | XChrgSrv | rpccEngine | PTService | Rpro8 | UTG2Svc | Active-Charge | javaw | DDCDSRV1 | alohaedc | dbstpssvc | XPS | Transnet | posw | NCRLoader | PSTTransfer | TSTSolutions | wndaudit | TSTAdmin | TellerDR | merapplauncher | contact manager | goldtllr32 | goldtrakpc | farm42phyton | fx4cash | bpcssm | vp-ebanking | LLB Online Banking | efix | iberclear | AMBCN | SGO | SQLpnr | vmware-view | banktelapk | SynJhaIntService | uniservice | client32 | CanaraCustMaintenance | legaclt | pcsfe | pcscmenu | cwbtf | srvview | pcsmc2vb | cwb3uic | trcgui | cwbsvstr | rtopcb | cwbujcnv | cwbujbld | cwbuisxe | pcsws | cwbsvd | cwblog | cwbdsk | securID | jhaintexec | appupdate | SGNavigatorApp | dbr | WINTRV | bsaadmin | encompass | eautomate | link | adminconsole | commandclientplugin | commandclientplugin_gui | mfmanager | verex director-server manager | verex director-communication manager | notes | nlnotes | notes2 | sacmonitor | netterm | fspnet | bridgerinside | cardserver | si | dais.ebank.client.offlineclient | BGFWIN31 | BGDWIN31 | BGXWIN31 | bocusertool | CLXReader | UBSPay | Migros_Bank_E-Banking | Bank linth Online Banking | java | abastart | abamenu | abajvm | sage200.finanz.gui | vpxclient | htmlshell | mmc | e3K.Main | QOPT | cresus | wineur | abaeb | efinance | GestionPE | BCN-Netkey | Sage 30 | ISL_light_client | msaccess | proffix.v4 | pxShowThread
Appendix B: Applications Targeted by Dridex 120 in July 2015
Uniface | bankline | Aptos | Hyposwiss | episys quest | bancline | tellerplus | ACE Software Solutions | ACI Worldwide | Alliance Enterprise | Bottomline Technologies | Broadridge | China Systems | CMA Small Systems | Clear2Pay | Adaptor Payments | Decillion Group | EastNets | Infosys | Flexcube | ECS Financials | FircoSoft | Fiserv | Kyriba | Premium Technology | Smartstream Technologies | Sopra Banking | Surecomp | Tieto Payment | TONBELLER | Wall Street Systems | Western Union | MoneyGram | Unistream | Direct Link | Abacus | agro-twin | coconet | crealogix | macrogram | mammut soft | omikron | quatersoft | experian payment gateway | softcrew | WinBacs | albacs | Albany.EFT.Corporate.Client | wpc | eSigner | StartStarMoney | StarMoney | acsagent | accrdsub | acevents | acCOMpkcs | ac.sharedstore | jp2launcher+ | sllauncher | cspregtool | RegisterTool | OEBMCC32 | sfirm | Bbm24win | wip | paypen | mammut_tb | telelink | translink | deltaworks | dfsvc | bitcoin-qt | multibit | BacscomIP2 | runclient | paycentre | accesspay | PaymentStudio | DiasClient | SynIntegrationClient | QuestLauncher | RemoteAdminServer | SymForm2App | plink | launch | PaygateWpfClient | terminal | Telelink | EBsec | ftrskr | Suite | Entreprise | rbpmain2 | rbpmain | tkc | ecbl-nxbp | sagedirect | turbo_teletransmission | cedripack | cedrisend | QikDesktop | QikDesktopCitrix | ConfigurationEditor | InteractFastConfig | javaw | otscm-client+ | ecb-sg | crs1 | GbpSV | pstw32 | MopaMaes | ldcptv10 | gslshmsrvc | launcher | tokensharesrv | sage