Overview
Beginning on June 1, Proofpoint researchers observed that malicious email campaigns with Dridex and Locky payloads essentially stopped. These campaigns have consistently been among the largest we have ever observed, with volumes reaching into the hundreds of millions of messages across our customer base. At the same time, multiple outlets [1] documented a significant disruption in the Necurs botnet, widely believed to be one of the largest botnets functioning today. This confirmed our suspicion that the threat actors behind Locky ransomware and Dridex banking Trojans have been using the Necurs botnet to distribute their massive email campaigns.
Figure 1 shows typical relative sending volumes of malicious emails distributing Locky ransomware by country prior to the June 1 disruption, the majority of which we expect were sent via the Necurs botnet. This parallels the heatmap showing worldwide infections with Necurs that Anubis published in [1].
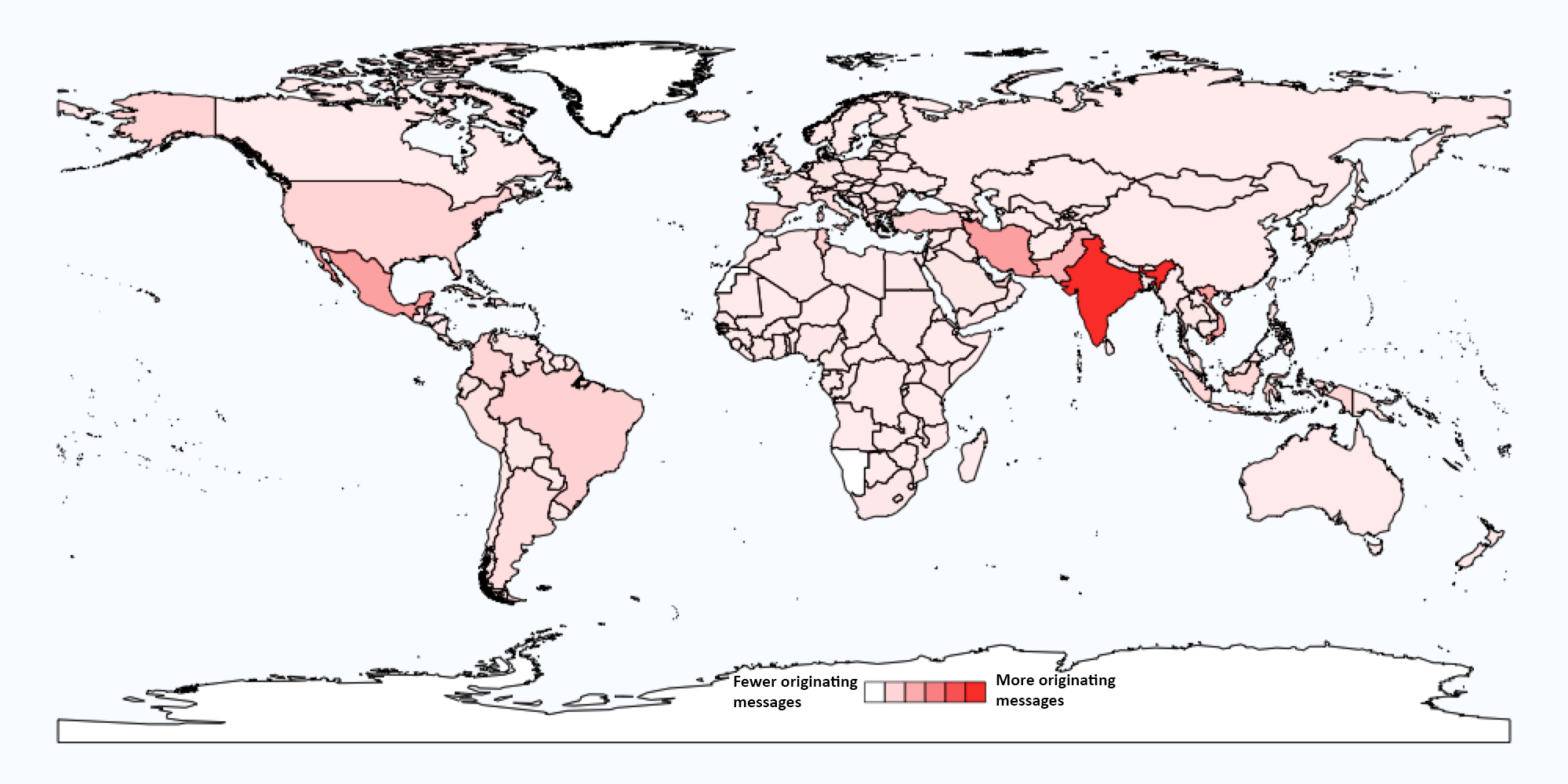
Figure 1: Relative sending volumes by country for recent malicious email campaigns distributing Locky.
Background
Necurs is a large botnet, or network of computers, infected with the Necurs rootkit. It can be used by threat actors for a variety of purposes. Botnets are generally used for sending spam or launching distributed denial of service (DDoS) attacks. Necurs has most recently been documented as a peer-to-peer (P2P) hybrid botnet. P2P botnets allow limited communication between infected "worker" computers and nodes that function as distributed command-and-control (C&C) servers.
Necurs employs a domain generation algorithm (DGA) that allows nodes and workers to find a new C&C when the active one goes down. Data from a variety of sources show that Necurs bots are actively looking for a new C&C, but we have no evidence that the Necurs botmaster has been able to retake control of the botnet.
Analysis
Figure 2 shows the number of unique IP addresses sending emails bearing malicious document attachments over time, most of which are presumably part of the Necurs botnet. The chart shows very high levels of botnet activity up to June 1, when the botnet went dark, along with associated malicious email activity. Figure 3 shows malicious email volumes across our customer base over the same period, demonstrating very similar directionality and periods of inactivity. Shaded regions represent weekends, when we typically see little to no activity.
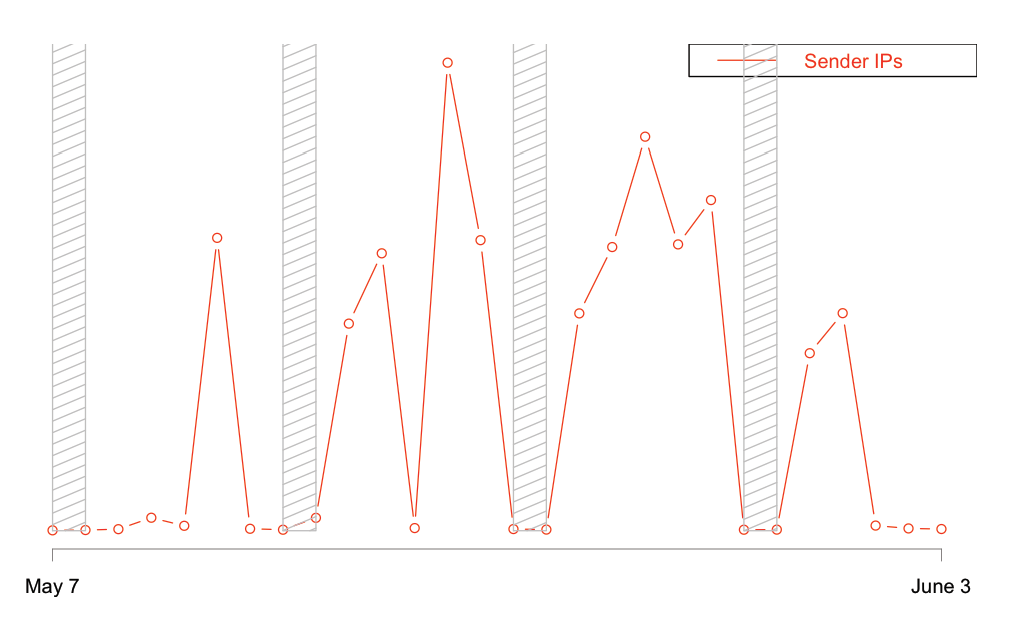
Figure 2: Number of IPs sending malicious document attachments (presumably from the Necurs botnet) over time
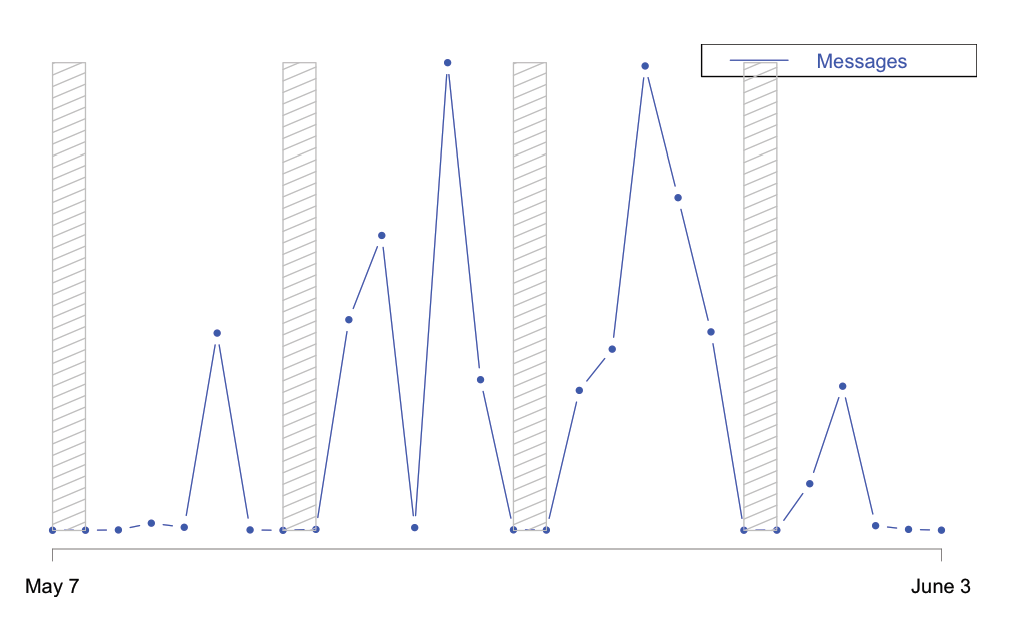
Figure 3: Malicious document attachment carrying email message volume over time
A look at unique IP addresses sending email with malicious attachments to our customers over a four-week period shows a far lower volume of malicious activity on June 1, corresponding with the report of the Necurs botnet outage.
It also suggests that previous days of low malicious email activity may correspond to days that the botnet was not operating.
These dips in Dridex and Locky campaign volumes, shown in the right-hand panel of Figure 4, parallel apparent Necurs outages. Necurs activity is shown in the left-hand panel. On average, we have been seeing a roughly 50:1 ratio of messages to sending IPs.
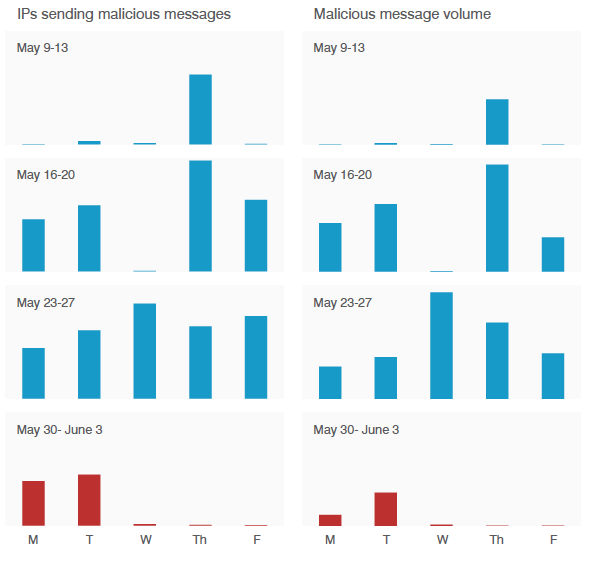
Figure 4: Number of IPs sending malicious document attachments (left) vs. malicious email volumes detected across the Proofpoint customer base. Note that the left and right scales are different with a ratio of malicious emails to sending IPs on average of 50:1.
As our colleagues at Anubis Networks reported on June 1 [1], the bots appeared to begin searching for a new C&C server on June 1, showing substantial spikes in Anubis' Necurs sinkhole. For P2P botnets in general, reestablishing connections between compromised PCs and new C&C infrastructure is a gradual process as new C&C information propagates through the botnet. Whether or when that will happen here is not clear.
We are also beginning to see the first small Dridex campaigns across our customer base since the reported Necurs outage began. However, we have not seen a return to large-scale campaigns. We expect that these campaigns are being distributed through mechanisms other than the Necurs spam cannon.
It is worth noting that we have observed significant disruptions to Dridex spam operations in the past [3,4] but the actors have re-emerged shortly thereafter.
Conclusion
The Necurs outage last week is our most obvious evidence to date of its use in the massive Locky and Dridex campaigns that we have been tracking this year. While this is not the first apparent Necurs outage we have seen, available data suggest that it involved a significant and ongoing failure of the C&C infrastructure behind the botnet.
At the same time, sinkhole data from other researchers confirms the resilience for which these very large malicious networks were designed, as very large numbers of bots look for new C&C servers. Whether the Necurs botmasters will succeed in retaking control of their botnet remains to be seen. In the meantime, we have seen limited Dridex campaigns, and we expect Dridex spam will continue regardless of the state of Necurs. We will continue to monitor the threat and provide updates on the related threat landscape if things change.
References
Subscribe to the Proofpoint Blog

