With the shift to remote work and the potential employee and insider, conduct and compliance risks that it poses, companies are becoming aware of the need to implement proactive controls to detect problematic employee behavior. A Risk Mitigation Program ("RMP") or Risk Management Framework may include the monitoring activity on websites, file shares, and communication channels.
Proofpoint recently hosted a webinar to provide guidance and best practices for protecting against remote worker and insider risk and the balance between privacy considerations with a risk-based approach. For convenience, we will provide a summary of the Risk Mitigation framework webinar here.
This post will discuss the latest risk assessment and mitigation approaches to protect your organization from remote worker risk while covering:
- What a true holistic Risk Mitigation Program looks like
- Why a proactive, Risk Mitigation Program is critical for your organization
- How Proofpoint can help you implement your overall Risk Mitigation Program
Who is considered a Remote Worker and What are their Risks?
First, it is important to define what encompasses an "insider" and "remote worker" and the types of 'risk' they pose.
Remote workers and insiders are not just employees, but contingent or 'temp' workers, contractors, consultants, and any individual who would have some kind of privileged access to internal systems, where distinguishing their activity from a clear 'outsider' may prove difficult. This definition is important to keep in mind when putting together an RMP to ensure you have the proper monitoring population.
'Flavors' of Insider Risk
It will be surprising for some to learn that risk from insiders make up the majority of issues. In fact, 74% of security incidents come from the extended enterprise...not from hacking groups. IT security incidents as a result of employee's actions alone account for 42% of occurrences. With companies spending, on average, $644,852 on each serious incident, establishing an RMP often pays for itself after one prevented incident.
But are all insiders nefarious? The answer is actually, 'no'; security incidents come in usually these flavors:
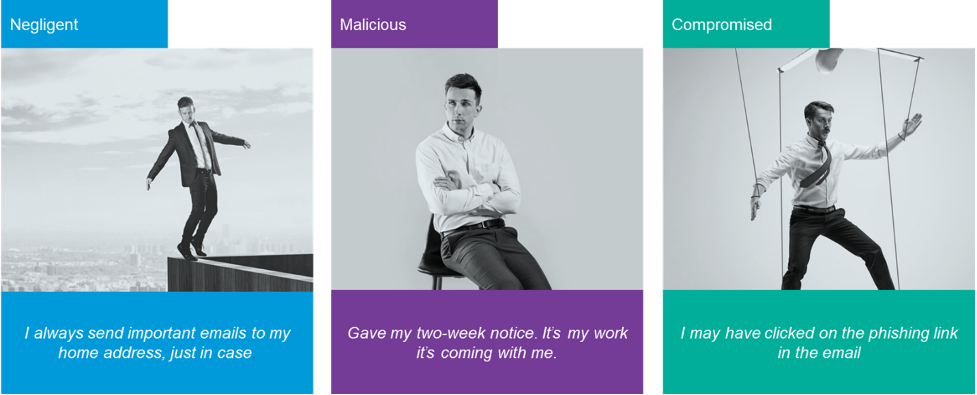
Insider Risk to be Concerned About
Next, it is important to address all potential, reasonable risks posed by remote workers realizing that each could have one or more mitigating controls.
|
Risk Category |
Description |
Examples |
|
Compliance Risk |
Compliance risk may be defined as the threat posed to a company's financial, organizational, or reputational standing resulting from violations of laws, regulations, codes of conduct, or organizational standards of practice. |
|
|
Conduct Risk |
According to regulators like the UK FCA, conduct risk can be considered as the risk that decisions and behaviors lead to detrimental or poor outcomes for their customers, and the risk that the firm fails to maintain high standards of market behavior and integrity. |
|
|
Legal Risk |
This is the potential loss that a company or individual could face as the result of a legal issue. It could be a claim made against them, a change in the law, or failure to take the proper legal measures to protect themselves |
|
|
Insider Cyber Threats |
Malicious threats to an organization that come from people within the organization, such as employees, former employees, contractors or business associates, who have inside information concerning the organization's security practices, data and computer systems. The threat may involve fraud, the theft of confidential or commercially valuable information, the theft of intellectual property, or the sabotage of computer systems.
|
|
A key challenge to securing the 'people perimeter' is that people cannot be accurately described by just looking at their activity logs. Understanding people requires understanding behavior and intent. Understanding intent means understanding context. These requirements make Insider Threat detection within a risk mitigation framework more difficult to uncover, as persons have access to systems and data for legitimate reasons yet can use it in corrupt and illegitimate ways. Therefore, context is extremely critical.
To understand context and intent within a risk assessment and mitigation framework, organizations are increasingly employing holistic monitoring programs that utilize "insiders" communications, in addition to behavioral data from system endpoints, such as file and web access, to form a complete picture of potential issues, often before they occur.
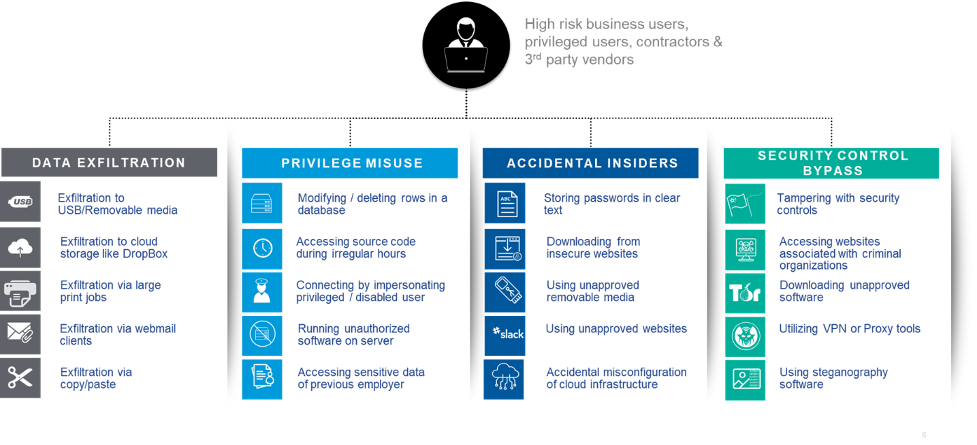
What A Holistic Communications Monitoring Program Looks Like
Here is a simple scenario on how communications and behavioral data work together to provide context for appropriate risk mitigation measures:
Scenario 1: Endpoint Behavioral Detection with Communications for Context
Insider A first downloads a 'Client List', renames the file, and then zips the contents with a password. Next, Insider A installs Dropbox, uploads the file, then emails the .zip file to their personal Gmail account for good measure.
Now, all the “about series of actions” were recorded via Insider Threat Management Endpoint detection, but the question is 'why' is it happening, and should it take precedence over other alerts? Here is where context provides insight when looking holistically at Insider A's behavior.
Compliance and Conduct Risk Detection uncovers potentially problematic communications involving Insider A, Insider B, and Insider C where Insider A is triggering risk detection models indicative of a 'toxic employee' where negative sentiment and intent to resign are found.
With the benefit of context, Incident Analysts would now place Insider A on a 'watch list' for further exfiltration, as well as prioritize and investigate the Client List leak.
How Proofpoint Can Help
Many more examples are shared in the webinar, but the net is that in today's Work From Home environment, we are drowning in endpoint data but are starving for information. Here, Proofpoint can help by offering a complimentary risk assessment to:
- Assess current compliance, legal, regulatory, and insider risks
- Identify and rank individuals by risk
- Inventory data sources needing monitoring and protection
- Assess current risk monitoring tools and incident response
- Outline the complete build of an insider threat program
- Create board-ready insights and reporting
No risk assessment and mitigation program is complete without technology to accompany the 'people' and 'process', so Proofpoint will also supply the systems to capture, monitor, retain, and investigate data required for your Risk Management Program.
What to do Next?
Reach out to Compliance@Proofpoint.com to schedule a complimentary risk assessment and look for our next post on how to build a Risk Mitigation Program for those that do not yet have one.











