Proofpoint Actionable Insights are the additional metrics and insights that the Proofpoint Threat Protection Platform can deliver through our combined data, detection and research. These insights provide the additional detail and context needed to fully understand your threats and the actions you can take to defend against them.
In the first blog post of our “Actionable Insights” blog series, we talked about insights around people risk and the meaningful actions you can take using those insights. In this second installment, we focus more on risk origination, how we can easily view this information in the Proofpoint Targeted Attack Protection (TAP) dashboard and the different actions we can take with this information.
Reduce risk from different domains through targeted controls
A lot can be gleaned about threats from the domains where they originate. For example, if we see threats coming from our company’s SharePoint/OneDrive domain, we can assume there are likely compromised internal accounts. That, in turn, gives us direction as to which actions we should take.
By seeing in-depth information about the origins of individual attacks, your team can implement targeted security controls to improve your organization’s security posture.
Proofpoint uncovers deeper insights into specific attacks such as the individuals, actors or third parties that may be tied to each threat by root domain. The Proofpoint Threat Protection Platform helps you see each of these threats across channels or attack vectors. This helps your organization reduce risk by giving your team the ability to better understand your threat landscape, respond more quickly and be more targeted in the controls they implement.
“Amazing insight. As a user of this product, and all Proofpoint services throughout multiple employers, I have been so impressed by the analytics and insight provided. I have demoed so many other products that just have such odd limitations and fall short in comparison to Proofpoint.”
Transform your approach to cybersecurity with actionable insights
Understanding the risk your organization faces from different domains is invaluable to modern cybersecurity. Attackers’ abilities to infiltrate and/or spoof domains, whether they are your domains or those belonging to third parties, are only advancing.
As we mentioned in our previous blog post around people risk, today’s security teams are also struggling with increasing demands on their time and decreasing resources, making it essential to prioritize their work. Any additional insight into your threats you can provide to your security teams can help them take more targeted, prescriptive actions to protect your organization more efficiently. Actionable insights provided by Proofpoint can help your team transform from being reactive to proactive.
Insights
The main report to look at for actionable insights into your origin risk is the “Top 10 Root Domains” report in Proofpoint TAP. This report shows you the top domains attacking your organization by volume. You can also set the report to show domains that were delivered or clicked on the most.
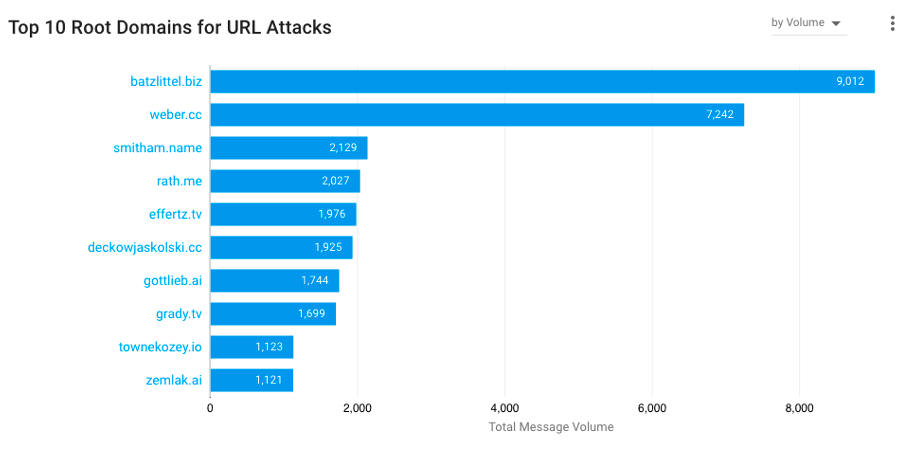
Figure 1. “Top 10 Root Domains” report in Proofpoint TAP.
A key insight from this report is the individual root domain origins for attacks. Even better, once you have that insight, you can then categorize the domains to clarify how many of your attacks are tied to specific tactics such as internal, spoofed or third-party (vendor/supplier) domains:
- Internal domains: Attacks originating from an internal domain may be coming from compromised or malicious users, or even compromised web apps.
- Spoofed domains: Use of these domains could indicate possible phishing attacks.
- Third-party (vendor/supplier) domains: Attacks from these domains suggest that a vendor or supplier has likely been compromised, and there may be potential for business email compromise (BEC) attacks.
By categorizing the domains from this report into tactics, you can use the expansive data layer from Proofpoint to dig deeper into each tactic and uncover more information, such as the individual users, threat actors or third parties that may be perpetrating these attacks.
With a security platform that can track threats across email, cloud and more, you can also understand which of these separate domains may combine into a singular attack campaign. This understanding and categorization of attack type allows security teams to take the appropriate, targeted action against those attacks.
Targeted controls
These enhanced insights on originating domain and attack types are pivotal to informing the downstream controls that you can implement to improve your security posture.
Let’s look at some of the most common tactics, and the controls that could be implemented for each:
1. Internal domains:
- Implement Proofpoint Internal Mail Defense (IMD) to protect against lateral movement of threats inside your organization’s internal mail.
- Implement Proofpoint Secure Email Relay (SER) to gain better control over transactional email from internal applications or from third-party, software-as-a-service solutions sending emails on your behalf.
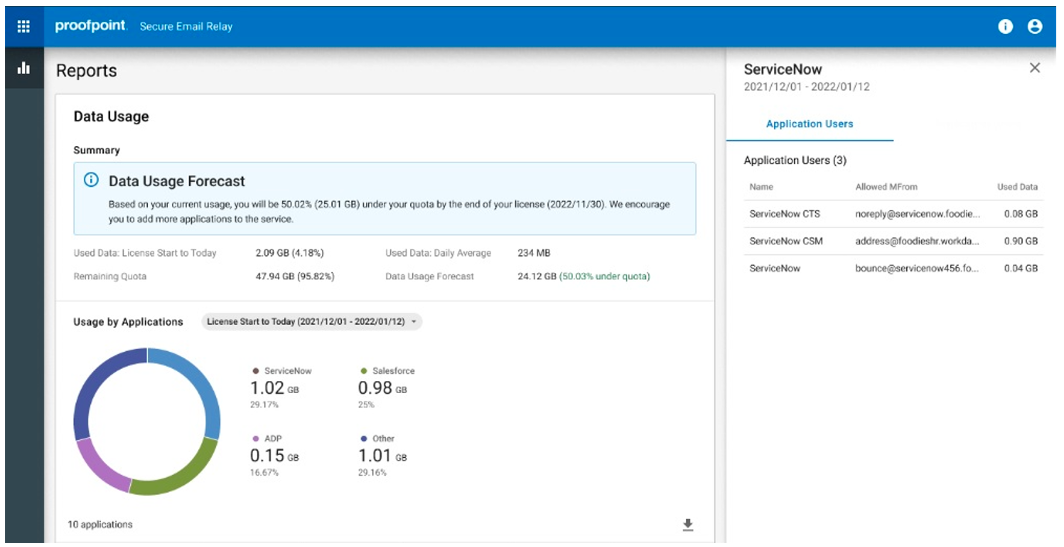
Figure 2. Secure Email Relay dashboard displaying a data usage forecast.
- Review your cloud app security protocol and compliance to check for any misuse of cloud solutions.
- Dig deeper into your people reports to understand more about users who may be compromised. For example, by using people reports in the Proofpoint TAP dashboard, you can see the actions of individual users and how often they occurred over time. This detail can help paint a picture of the attacks or intentions of an individual user.
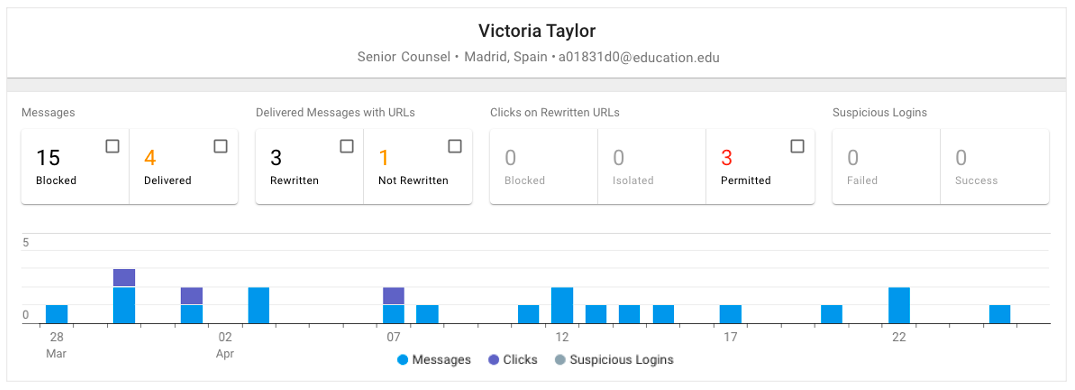
Figure 3. Example of a people report in the Proofpoint TAP dashboard.
2. Spoofed domains:
- Implement DMARC or ensure that it’s set up appropriately. Also, enforce DMARC blocking policies on inbound email where possible.
- Implement a hosted Sender Policy Framework (SPF) to better police who may and may not send email from your domain.
- Deploy Proofpoint Email Fraud Defense (EFD), including Domain Discover, which automatically identifies lookalikes of your domains and dynamically detects newly registered domains posing as your brand in email attacks or by phishing websites.
3. Supplier domains:
- The Nexus Supplier Risk Explorer (NSRE) feature within EFD, automatically identifies your suppliers, validates their DMARC records, and uncovers the risk they pose to your organization.
- Contact your supplier(s) directly to discuss their security setup. Doing so can also lead to improved relationships with your suppliers as you help them become more protected.
What are the benefits of taking the steps outlined above? For one, they can help you lower your organization’s risk exposure. By automating responses to these risks, you prevent them from ever becoming a true threat to your organization. And by decreasing spoofing attacks, you better protect your organization, your customers’ businesses and your reputation, too.
There’s also the upside of increased operational efficiency. By decreasing the need to address each of these different types of attacks, your security teams will have more time to spend on other value-adding activities for your organization.
Understand your risk exposure
If you’d like help identifying the biggest digital threats to your business, please reach out for a free digital risk assessment. Proofpoint security experts conduct these complimentary risk assessments, and they can show you how to mitigate threats like domain risk.
To learn more about the Proofpoint TAP dashboard and actionable insights see this page.











