In this ongoing blog series, we examine how human-centric threats continue to evolve—and how some may bypass Microsoft’s traditional email defenses. These attacks can result in significant financial and operational impacts for organizations. We’ll do a deep dive into several types of attacks, including:
- Microsoft Missed Business Email Compromise (BEC) Attacks
- Microsoft Misses Ransomware Attacks
- Microsoft Misses Supplier Attacks
- Microsoft Misses Account Compromise Attacks
Subscribe to our blog at the bottom of this post to stay updated on these misses that may be impacting your organization. Also, use our rapid risk assessment to better understand your organization’s risks.
The ubiquity of weaponized file sharing
Weaponized file-sharing attacks are one of the most common tactics in URL-based attacks. Proofpoint’s internal threat data—analyzing over 49 billion URLs daily—shows that file-sharing URLs are used in more than half of these attacks.
Given the widespread trust and adoption of services like Microsoft OneDrive and SharePoint, attackers increasingly exploit these platforms to target users. As a result, Microsoft’s productivity platforms may inadvertently host malicious files that bypass its native email security controls.
In 2021 we found more than 45 million threats that were sent to Proofpoint customers with malicious content hosted by Microsoft. This underscores the need for layered defenses that complement Microsoft’s built-in security.
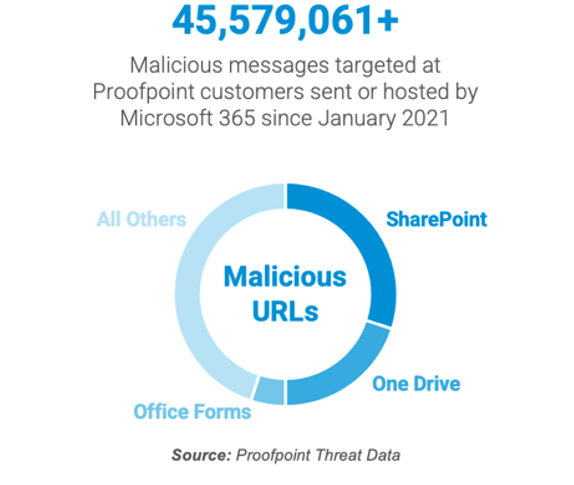
Figure 1. Microsoft hosts most of the malicious URLs sent to our customers. Since January 2021, Microsoft 365 has sent or hosted more than 45 million threats targeting Proofpoint customers.
Attacks that compromise accounts can cost organizations significant amounts of money. For example, according to the “The 2021 Ponemon Cost of Phishing Study,” a large, 10,000-seat organization will lose millions annually in prevention, remediation and user downtime from phishing attacks. With more than half of URL-based threats originating from malicious content on file-sharing sites, this is an expensive problem to fix.
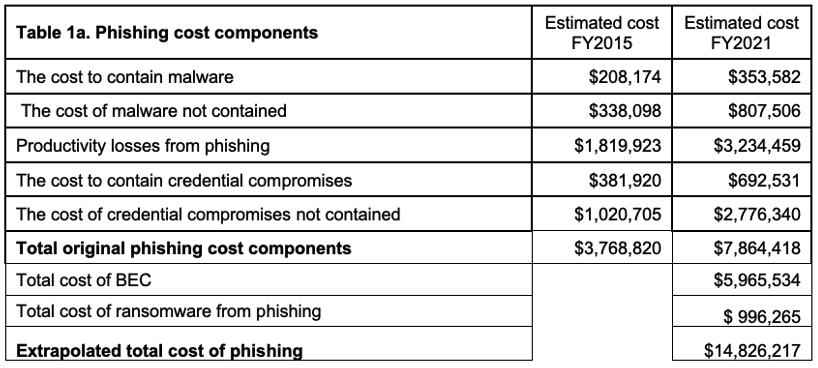
Figure 2. Overview of phishing-related costs for a 10,000-seat organization. (Source: Ponemon Institute’s “2021 Cost of Phishing Study.”)
During a one-month period of targeted Rapid Risk Assessments, Proofpoint detected more than 13,000 URL-based threats from file sharing and other legitimate websites that bypassed Microsoft’s native email security controls. Proofpoint also detected more than 3.8 million email threats sent using Microsoft mail servers and about 370,000 threats hosted by services like Office 365 OneDrive, SharePoint and Azure.
These findings underscore the importance of layered protection, as threat actors increasingly exploit trusted infrastructure like Microsoft’s to launch attacks that may persist for extended periods, even after being flagged. Proofpoint’s advanced detection capabilities are designed to complement Microsoft’s security ecosystem, helping organizations close these gaps and respond faster to emerging threats.
Here are some file-sharing attack types that can bypass Microsoft email security.
1: Credential theft hosted on Microsoft
As highlighted in our “Human Factor Report,” Proofpoint found that attackers increased their use of CAPTCHA by 50x year-over-year. In one proof of concept (POC) assessment, an attacker used Microsoft OneDrive and CAPTCHA to target a shared mailbox. Their goal was to harvest user credentials by sending what appeared to be a link to a legitimate OneDrive document.
Here’s the example:
- Environment. Microsoft 365
- Threat Category. File-Sharing URL-Based
- Attack Type. Credential Theft
- Target. Shared Mailbox Work Request

Figure 3. Users are taken to a OneNote page, with a link to a fake Word document. When they click on the link, they’re presented with a CAPTCHA. After checking the box, they’re taken to a fake Microsoft page in an attempt at credential theft.
Anatomy of the attack
The attacker pretended to be as a third-party vendor with a work request. They sent that request to a telecom organization’s shared mailbox with the goal of stealing credentials. In our risk assessment with this customer, we protected them from the attack after the threat slipped through Microsoft’s email security.
This credential theft attack not only bypassed native Microsoft email security controls, but more than a month after we condemned the attack, the OneDrive page was still live and actively hosting a malicious credential theft attack impersonating Microsoft’s brand. This is one of millions of abused file-sharing pages that Microsoft hosts malicious content on every month.
While this threat bypassed native Microsoft email security controls, Proofpoint’s layered detection capabilities identified and mitigated the risk. This demonstrates how our solutions complement Microsoft’s infrastructure to protect users against increasingly sophisticated social engineering tactics.
2: Branded credential theft on legitimate file-sharing site
Office 365 credential theft is a common lure that attackers use to attempt to compromise users’ accounts. These attacks are extremely dangerous, as the attacker assumes the corporate identity of their victim, which can cause untold damage.
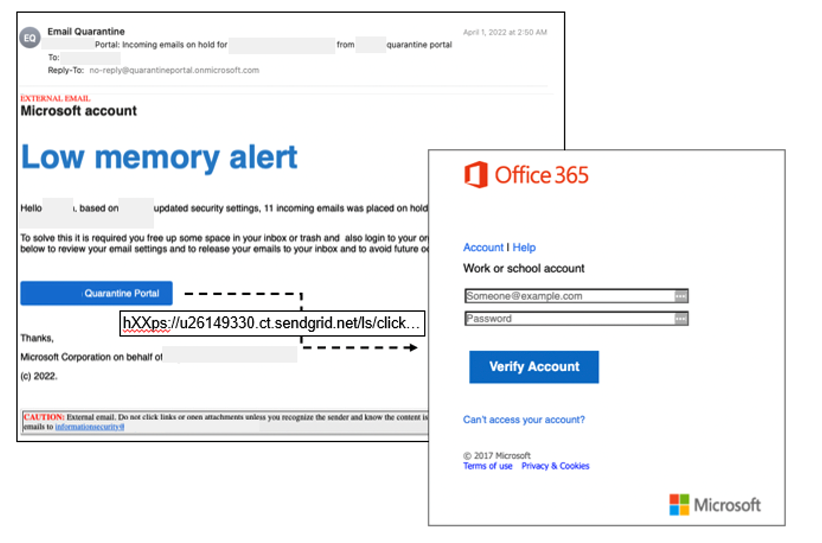
Figure 4. An attempt at credential theft where attackers imitate the Microsoft brand, hosted on a legitimate file-sharing site.
Here’s the example:
- Environment. Microsoft 365
- Threat Category. File-Sharing URL-Based
- Attack Type. Credential Phishing
Anatomy of the attack
Credential phishing campaigns that mimic email or IT notifications are increasingly common. In one example, an attacker abused a legitimate cloud service—SendGrid—to host a credential theft attack. The message was sent from a spoofed Microsoft domain (onmicrosoft.com). It appeared authentic and even included a greeting signed on behalf of the Microsoft Corporation.
This attack used brand impersonation and trusted infrastructure to bypass native Microsoft email security controls. Reputation-based analysis, such as Microsoft Safe Links, may not consistently detect novel threats that are hosted on legitimate platforms.
Proofpoint’s click-time URL sandboxing, powered by machine learning (ML) classifiers, successfully identified and blocked the attack. This demonstrates how our multilayered detection capabilities enhance Microsoft’s security ecosystem and protect users from emerging threats.
3: Credential theft hosted on Microsoft
Why aren’t baseline security controls enough? Threat actors continue to evolve their tactics, as shown in this next multilayered attack. In this case, the attacker exploited two file-sharing platforms, nesting a Microsoft phishing lure within a message sent from a compromised account.
The attack successfully bypassed Microsoft native email security and an API-based solution designed to detect these threats. Proofpoint’s advanced threat detection identified and blocked the threat—reinforcing the importance of multilayered protection that complements Microsoft’s security infrastructure.
Here’s the example:
- Environment. Microsoft 365
- Threat category. File-sharing URL-based
- Attack type. Credential phishing
- Target: Loan officer
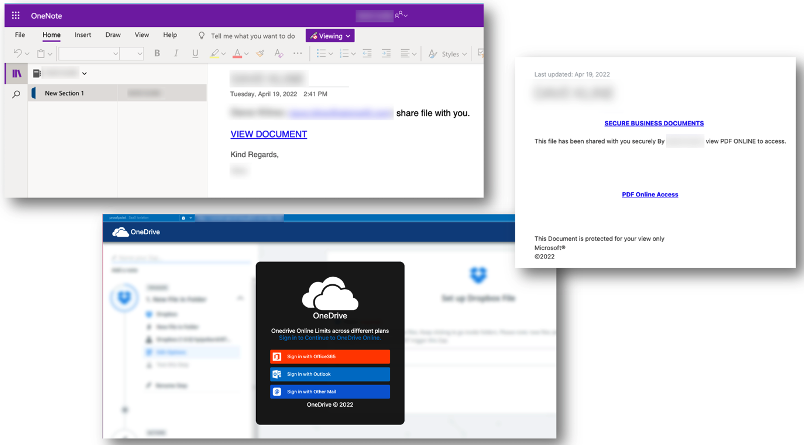
Figure 5. Attackers using two file-sharing services to evade Microsoft security.
Anatomy of the attack:
In one targeted attack, a threat actor used a compromised account belonging to a local real estate agent to send a forwarded message to a loan officer—likely related to a transaction or closing. The message included a link hosted on Microsoft OneDrive, which redirected to another file-sharing site, Evernote. When clicked, the Evernote document led users to a fake OneDrive login page designed to steal Microsoft credentials.
More than a month after this attack was spotted and flagged by Proofpoint, all the pages with links to malicious content are were still live. This incident illustrates how threat actors can exploit trusted platforms and nest malicious content across multiple services to evade detection.
The attack bypassed both Microsoft’s native email security and an API-based solution for detecting such threats. Proofpoint’s multilayered detection successfully identified and blocked the threat—reinforcing the need for complementary, layered protection that strengthens Microsoft’s security infrastructure and speeds up threat response.
How Proofpoint stops file-sharing attacks
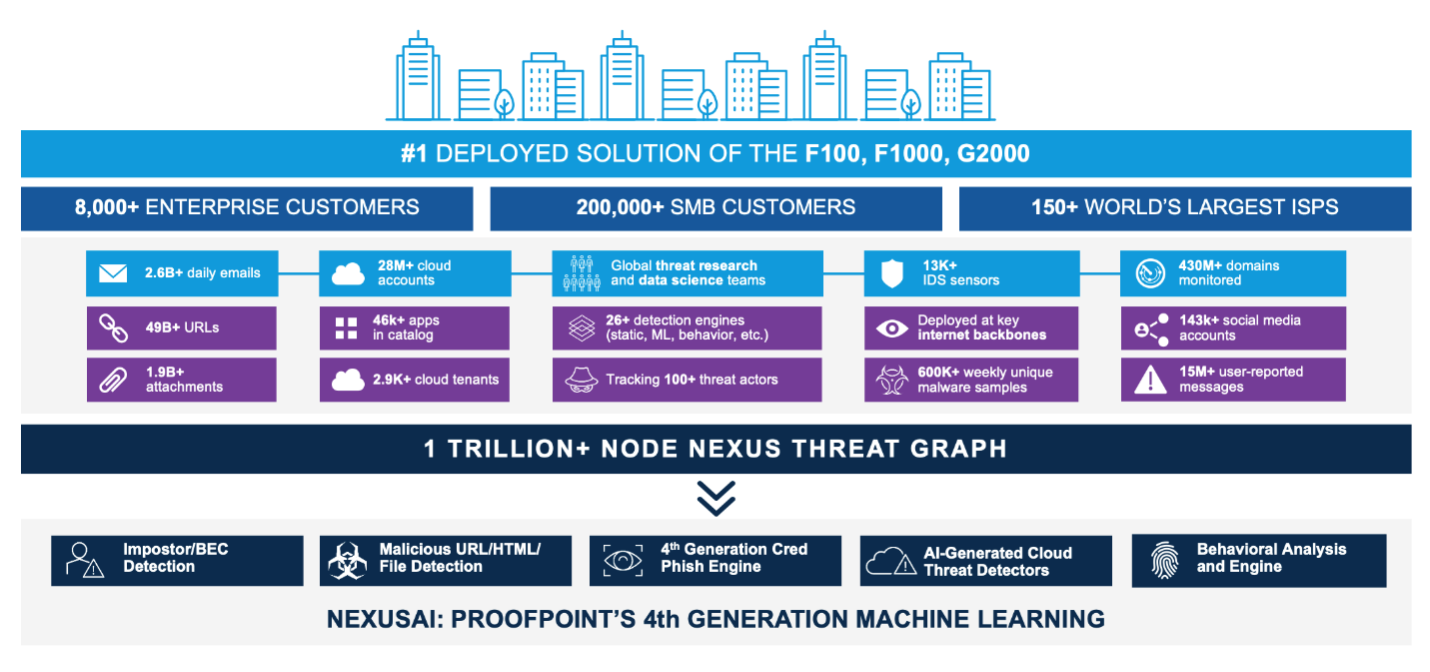
Figure 6. AI and ML are less effective without a large corpus of data powering the models. The Proofpoint Nexus Threat Graph includes threat protection insights from 75+ of the F100, 60%+ of the F1000 and 200,000+ SMB organizations, in addition to a growing information and cloud threat protection presence.
Proofpoint provides an end-to-end, integrated advanced threat protection solution with multiple layers of protection to detect file-sharing attacks. We use a detection ensemble with more than 26 layers for email threat protection to detect advanced techniques like nested attacks, CAPTCHA, or password-protected files and URLs by attackers attempting to evade security.
Our ML and artificial intelligence (AI) models for detection are fed by 2.6 billion daily emails, 1.9 billion attachments and over 49 billion URLs. Also, our growing information protection solution includes threat insights on more than 28.2 million active cloud accounts, giving us details about how attackers are attempting to weaponize cloud applications like file-sharing accounts.
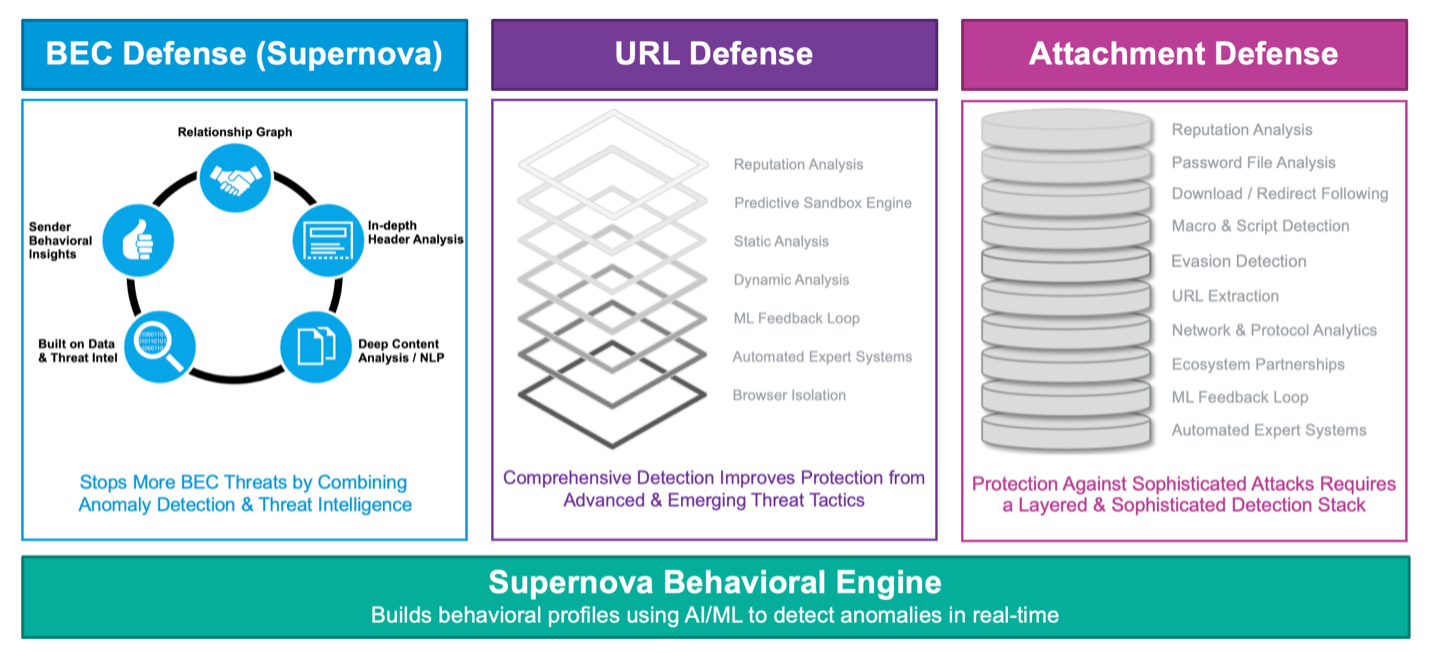
Figure 7. The detection stack from Proofpoint has more than 26 layers, including advanced detection for URL-based threats like file-sharing and attachments.
Recommendations to stop account compromise attacks
Proofpoint takes a multilayered approach to stopping file-sharing attacks with our Proofpoint Threat Protection Platform alongside our Information Protection Platform.
There is no silver bullet to stop these threats. That’s why a multilayered, integrated threat protection solution is necessary.
To learn more about how Proofpoint Threat Protection can help you can stop these threats in your environment, take a free Email Rapid Risk Assessment.











