The need to increase investment in corporate security operations center (SOC) teams is intensifying as high-profile attacks become more frequent and sophisticated.
According to the Identity Theft Resource Center, the number of publicly reported data compromises through September 30, 2021, had already exceeded the total number of events in fiscal year 2020 by 17%. More importantly, attackers are becoming more systematic in their targeting and tactics, making security even more challenging.
Meanwhile, recent research from The Enterprise Strategy Group (ESG) and the Information Systems Security Association (ISSA) found that over the last decade, the cybersecurity professional skills gap has continued to increase, impacting over half (57%) of organizations. That same research found that the top ramifications of the skills shortage include an increasing workload (62%), unfilled open job requisitions (38%) and high burnout among staff (38%).
All of this together creates a dire situation if companies don’t do something soon to help their security teams. But what can they do?
Easing the SOC team workload
Many corporations are recognizing the need to help SOC teams by investing in ways to decrease their overall workload. In the study mentioned above, 31% of cybersecurity professionals rated “overwhelming workload” among the top three most stressful aspects of their job.
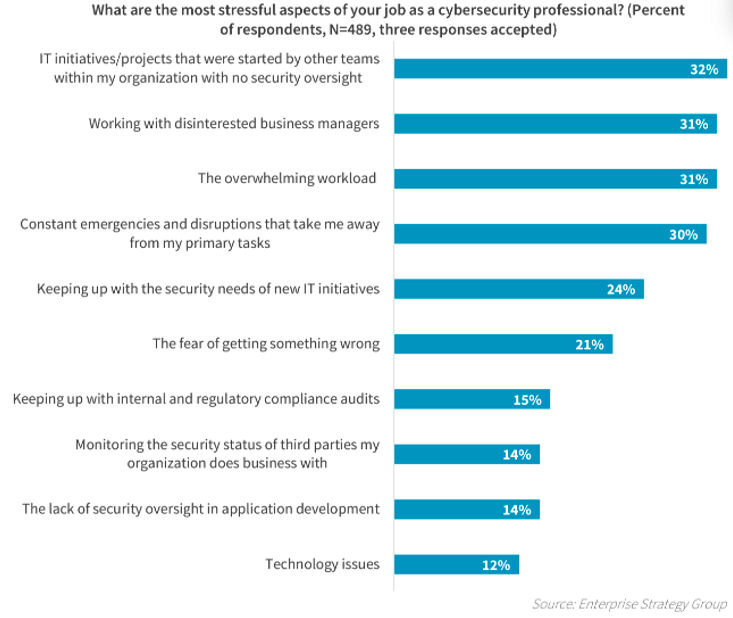
Figure 1. The top 10 most stressful aspects of cybersecurity professionals’ jobs. (Source: ESG and ISSA’s joint research project, “The Life and Times of Cybersecurity Professionals 2021,” Volume V.)
One way that companies are trying to invest more in their security amid staffing shortages is by outsourcing some activities using services like managed detection and response (MDR). Proofpoint even offers our own managed services for email security and security awareness training. However, these services can sometimes be an afterthought, as corporate budget holders generally have less insight and are less invested than SOC teams in recognizing the need.
Another method, which many SOC teams are turning to themselves, is automation, which can ease their workload and also improve their security strategy by providing additional information and insights. Automation can help security teams become more efficient by accurately detecting most initial threats, so teams can focus their time on the highest-risk threats hitting the organization.
Automating multiple aspects of email security
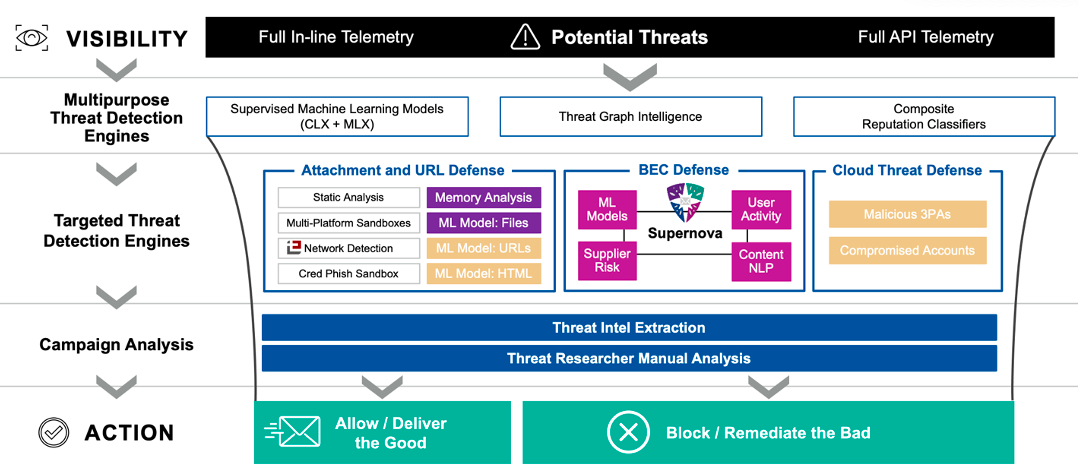
Figure 2. Details of the email security detection ensemble from Proofpoint, which helps detect and prevent phishing, email fraud, supplier attacks, ransomware and other advanced threats.
Threat detection: The first ingredient to a successful threat detection and prevention system is the ability to accurately detect the threats that are targeting your people before they can become real threats to your organization. These threats can be as simple as common spam or malware that is relatively easy to recognize, or they can be more sophisticated multi-stage malware attacks or advanced business email compromise (BEC) and supplier risk threats. Effective threat detection can be used to recognize and stop these threats so that SOC teams don’t need to worry about additional threats entering their environment.
One Proofpoint customer, The University of Oklahoma was feeling the pain of both an increase in the number of attacks and the lack of resources to handle them.
"We were drowning in phishing attacks. We needed help reducing not just the quantity of attacks, but also the amount of time spent responding to attacks."
- Aaron Baillio, CISO, The University of Oklahoma
By using automation offered through Proofpoint, the university’s security team saw immediate and concrete results. Proofpoint identified between 50% and 70% of all email sent to the university as malicious, bulk or otherwise unwanted, and stopped it from being delivered to users. This automatically reduced the SOC team’s workload by eliminating the need for security personnel to manually triage or remediate each one of those emails.
Automated remediation: Once the majority of threats are stopped, SOC teams can focus their energy on more advanced threats before they can cause harm.
For any threats that do get through the initial detection, an automated abuse mailbox monitoring solution like the CLEAR solution from Proofpoint can work together with your end users to remove risks from your organization faster than would normally be possible.
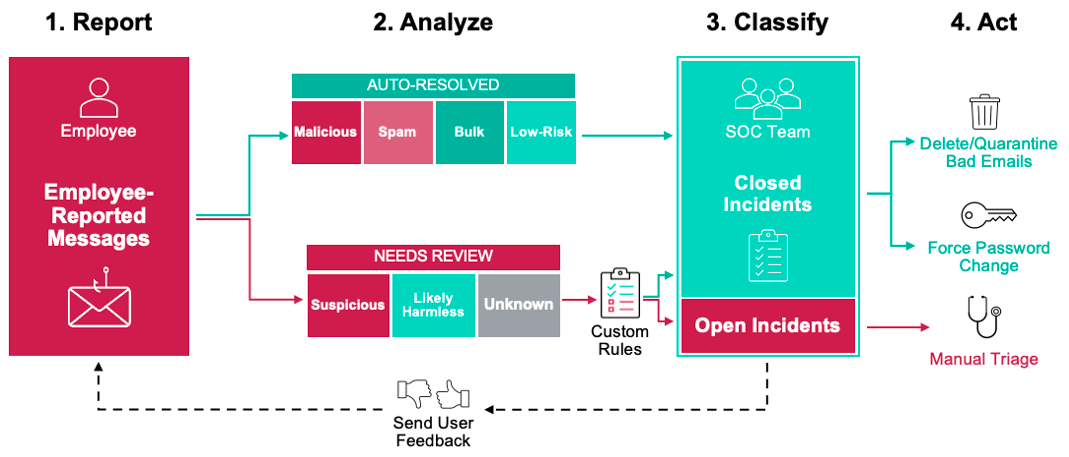
Figure 3. An overview of the Proofpoint Closed-Loop Email Analysis and Response (CLEAR) solution, which automates the analysis, classification and response to end user-reported suspicious emails.
By using automation in this way, SOC teams can spend their time on manually triaging the more advanced attacks that can be the most difficult and time-consuming to address. Less time spent triaging smaller incidents also means SOC teams are spending more time honing their skills and expertise to become even better analysts.
Deploying automation into your security workflows
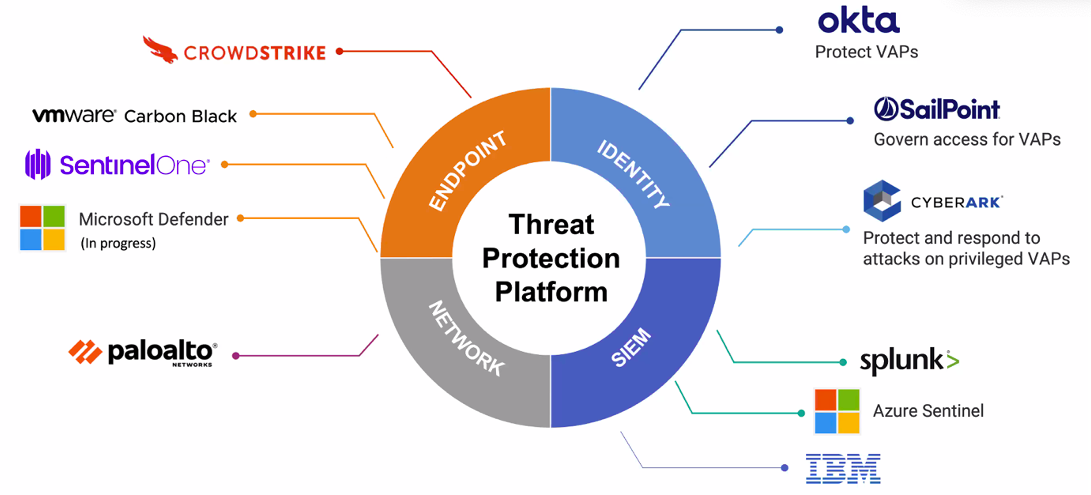
Figure 4. Proofpoint works with various other cybersecurity leaders to share and enhance threat intelligence while streamlining workflows.
It’s one thing to speak about the benefits of a robust, automated system, but it’s another to actually put it in place within your organization. More than half (58%) of survey respondents in the study from ESG and ISSA agreed that security professionals spend too much time on the technical aspects of cybersecurity and not enough time on how cybersecurity aligns with the corporate mission.
This process works best when the automation is fully integrated into your existing workflows and security solutions. Once again, timesaving and efficiency can be realized in multiple ways:
Installation and maintenance
We understand that beyond the time spent on critical mitigation efforts, security teams can also spend a lot of their time just maintaining their security solutions.
Proofpoint is continually investing in the development of our platform to make it simpler to deploy, maintain and use. As more organizations move their security infrastructure into the cloud, we continue to build out our cloud-based architecture across products.
In February of this year, we released the cloud-based version of our Threat Response Auto-Pull (TRAP) product for automated threat remediation called Cloud Threat Response. This cloud-based product works together with our on-premises solution to enhance our current capabilities and bring even more flexibility for any type of deployment.
Our customers have seen immediate benefits to this new deployment option:
“This was the best, easiest product on-boarding I’ve ever done.”
“Exactly how I imagined a cloud-based TRAP to be.”
Decreased workload
Now we know that automation can improve SOC team workloads by decreasing both the number and complexity of remediation tasks. However, it can also provide more detail about each threat. Having additional information about a threat helps incident responders understand it more quickly and spend less time remediating it. This, in turn, opens up more time for the SOC team to focus on corporate goals.
Proofpoint also has the integrated security platform that cybersecurity professionals need. Managing every aspect of cybersecurity from a single interface reduces the time needed to move from one task to another. The ability to share underlying data and analytics is another benefit, as shared data and infrastructure help enable many automation capabilities.
"Today, we have a single place to go to protect email users, secure critical environments and react to incidents. . . . This level of integration has increased our IT team’s productivity. We now see valuable, tangible results."
- Aaron Baillio, CISO, The University of Oklahoma
To summarize, automation can help ease the burden on SOC teams and make them more effective by:
- Reducing workloads by detecting and stopping the majority of incoming threats
- Remediating threats automatically and thus, more quickly, before they become real concerns
- Organizing threats and alerting SOC teams, helping them better focus their scarce resources
- Creating new policies and actions automatically to reduce future threats
- Freeing up the time and capacity for SOC teams to focus on high-risk threats while enhancing their experience and expertise in recognizing and remediating those threats
Get a clearer picture of your organization’s risk posture
Interested in seeing phishing threats in your environment? Take the free Email Rapid Risk Assessment from Proofpoint. In less than five minutes, our assessment can help you better understand your risk posture, helping you uncover threats your email security solution is missing, gain visibility into which people in your organization are being targeted, and see how Proofpoint can provide your organization with the best integrated, layered protection against evolving threats.











