Anyone reading this knows just how complex managing a large computer network can be. To make that challenge a bit easier, Microsoft Active Directory (AD) uses the concept of domains and trusts to enable administrators to manage and secure systems in large environments more effectively.
Domain and trust vulnerabilities are a critical consideration in identity security. They have a major impact on your ability to control access to resources and data. But as a certain superhero might put it, with great power comes great responsibility; as helpful as they are, domain and trust relationships can also be vulnerable to a bevy of cyber threats and vulnerabilities.
Since Illusive became part of Proofpoint in late December, we’ve continued to see growing demand among Proofpoint and Illusive customers for modern ways to protect and detect identity vulnerabilities that exploit common vulnerabilities in domains and trusts. In our research, 80% of organizations are breached by identity-based attacks. Illusive’s leading-edge technology—now the Proofpoint Identity Threat Defense Platform—will continue to evolve to help organizations break the attack chain.
In this blog post, we summarize some of these vulnerabilities and how we remediate them. We also explain how we decided to implement these approaches within our product.
Domains and trusts: terms to know
Before we dive into this topic further, let’s define some key terms:
- A domain refers to a collection of networked computers that share a common database managed by a central authority, known as a domain controller (DC). The DC is responsible for authenticating users and ensuring that they have the proper permissions to access network resources.
- A domain forest is a hierarchical structure of domains that share a common global catalog and common administration.
- Having a trust relationship between two domains allows users from one domain to access resources in the other domain.
Understanding different types of trusts
It’s important to know about different types of trusts, as well:
- One-way trusts allow users from one domain to access resources in another domain, but not vice versa.
- Two-way trusts enable two-way access.
- Transitive trusts allow users in one domain to access resources in other domains that trust the first domain. Here’s a simple explanation of this trust type: If I trust you, and you trust her, then I will trust her automatically.
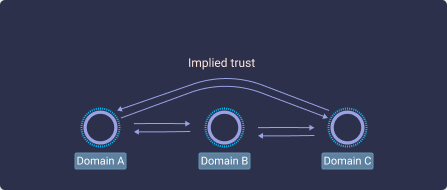
The concept of implied trust.
People don’t normally trust each other transitively. Even so, there have been more than a few times in history when that type of trust has benefited humanity. Peace treaties—in which entire populations trust another based on agreements between their leaders—is just one example.
Let’s examine some of the associated risks with trust:
The power and vulnerability of a two-way trust
When two companies manage a business relationship, or when one company acquires another, a two-way trust relationship can be established between their respective domains. A two-way trust relationship can be useful in certain situations. But it also presents vulnerabilities that must be carefully managed to ensure the security of the domains involved.
One famous story of a two-way trust vulnerability is a retailer’s data breach in 2013. In that breach, attackers gained access to the retailer’s network by first compromising the network of a third-party HVAC vendor that had a two-way trust relationship with the retailer’s domain.
The attackers stole login credentials from the vendor’s network. They then used those credentials to gain access to the retailer’s domain. And once they were inside the network, they were able to move laterally and gain access to sensitive customer data, including credit card information.
This incident highlights the vulnerability of two-way trust relationships, particularly in situations with third-party vendors. In this case, the attackers could exploit a weakness in the vendor’s network to gain access to the organization’s domain. The result was a major data breach that we still talk about today.
A picture is worth a thousand words
As a product manager, co-author Hila Chen was challenged to create a module to surface this vulnerable area shortly after returning from a customer visit to one of the largest financial organizations in Europe. That visit reinforced our belief that it would take more than words and data tables to deliver strong and clear value to our customers, whether they’re large enterprises or smaller organizations.
If you have hundreds or thousands of domains and trusts, reading about them can be a tedious task (TL;DR)! But what if you could simply look at a map? Graphically displaying domains and trusts relationships on a map can quickly and effectively reveal the kind of insights that can help to prevent incidents like the breach we discussed above.
Mergers and acquisitions (M&A) are another classic use case of the domains and trusts feature.
One business acquiring another could pose critical security risks once trust has been established between the two organizations if the acquirer doesn’t properly manage the trust or there’s a breach of trust.
Therefore, before establishing trust with the acquired domain, we recommend running a risk analysis on it and remediating the risks. Only then should you establish trust relationships.
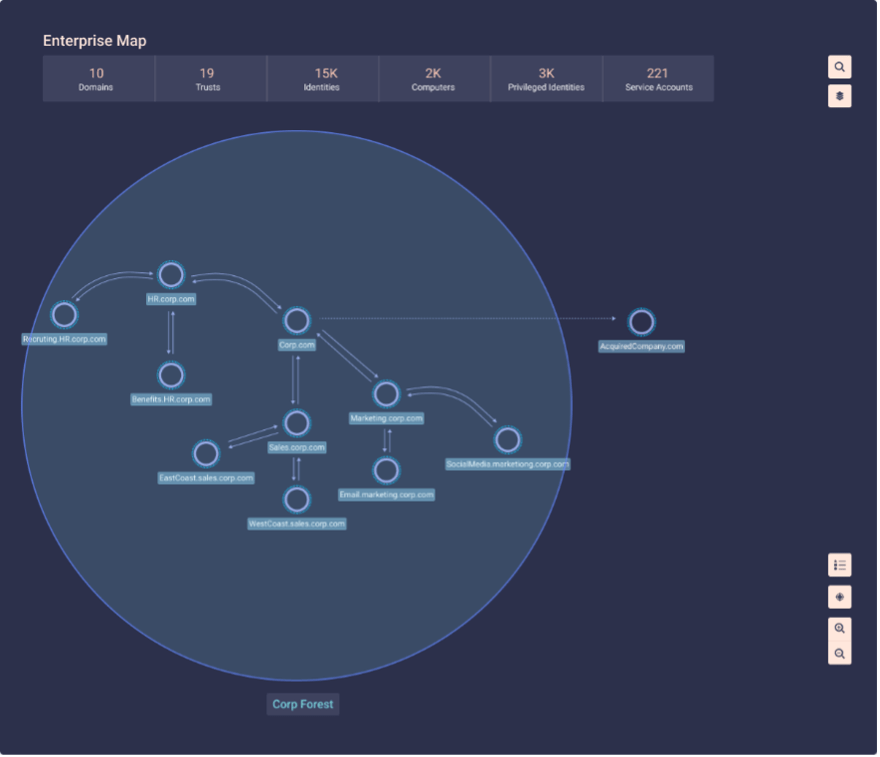
An enterprise map as shown by Proofpoint Identity Threat Defense.
Almost every time we speak with customers who use this feature, they say they love it. Here’s a typical quote: “When I saw the enterprise map, I noticed that I had two-way trust with domains that should only have one-way trust, which can be exploited by attackers for lateral movement.”
The importance of an enabled SID filtering
One of the exploitable features in trusts is security identifier (SID) history. SID history is a feature in Active Directory that allows administrators to maintain the SID of a user or group account when it’s moved from one domain to another within a domain forest.
SID filtering is a security feature for preventing unauthorized access. When there’s an access attempt, the system checks the SID of the user against the permissions set for the resource. If the SID isn’t on the list of authorized SIDs, the user is denied access.
Now, say that a large financial institution doesn’t follow best practices for SID filtering. An attacker aware of this weakness can manipulate the source IP address of a network packet to match a trusted IP address allowed to communicate with the network. As a result, the firewall allows the attacker to gain access to the network. Once inside the network, the attacker can move laterally, compromising multiple systems and accessing sensitive information. The attacker can then use this information to carry out fraudulent transactions, causing significant financial losses for the institution.
Our first recommendation when surfacing a SID filtering disabled on trust is to enable SID filtering. It is also necessary to perform a deeper audit of the environment and ensure SID filtering is enabled across all forests and domain trusts.
Domains and trusts are essential components of an Active Directory infrastructure but they can also be vulnerable to various threats. Monitoring and reviewing domain and trust management regularly can help your organization become aware of vulnerabilities. That insight will help you to implement effective security measures to protect your systems.
To learn more about your organization's identity risk, sign up for a free assessment here.











