Sometimes, when we have top performing human-centric security solution in place, we can forget just how much value it’s delivering to our business. If we don’t see threats infiltrating our organization, we stop believing that they even exist in the first place. Leadership may push security teams to cut costs or consolidate vendors for better licensing terms. And often this means email security solutions are replaced without an organization fully understanding the potentially negative long-term impact. Eventually, threats start making their way past your new defenses and causing havoc. They may be saving your organization money, but at what cost?
A former Proofpoint customer in the drilling industry had some budget constraints after leadership changes. Although they had been happy with Proofpoint, pressure to consolidate vendors caused them to switch to a Microsoft E5 license. After making the change, they began struggling to keep up with an influx of new threats, which concerned their security team. So, they decided to rethink their security strategy. While this customer considered several vendors, eventually they selected Proofpoint again as their top choice.
Their decision shows why it’s so important to choose a leading human-centric security vendor. If you choose one that delivers comprehensive email security, reliable customer support and visibility and controls, then the behavior of your riskiest users is effectively neutralized. Here’s why they came back to Proofpoint.
The goal: implementing better threat protection
After switching from Proofpoint to Microsoft E5, this customer began seeing an influx of new threats penetrating their Microsoft defenses. This overwhelmed their security team. As a result, the team had to spend significantly more time managing emails and security incidents.
Email security is at the top of the team’s list of priorities—it gets a lot of visibility and allocated budget. They needed a solution that could help with:
- Advanced phishing. In these attacks, bad actors try to trick people into handing over their login credentials, financial information or personal data. They often include malicious links or attachments that redirect users to hoax websites. Examples include spear phishing and business email compromise (BEC).
- Account takeovers. Bad actors use stolen credentials to gain unauthorized access to user accounts. Once inside, they can exfiltrate data, commit financial fraud or deploy malware into the organization. 99% of organizations experience account takeover attempts. So, this is a big concern for every security team.
- Malware attacks. Malware is malicious software or code. Bad actors use it to disrupt, damage or access networks, systems and devices. Examples include ransomware, rootkits and botnets.
- Social engineering. Designed to exploit human behavior, bad actors use social engineering tactics to manipulate their victims to perform an action that is harmful to their victim or the organization. Often, fear and urgency are driving factors. Actions may include sending money or handing over sensitive data or credentials. Pre-texting, vishing and impersonation are examples.
Results: Proofpoint helps with adopting a human-centric security approach
In addition to high threat detection efficacy, the customer also wanted better visibility into the behavior of their riskiest users. Another decision criterion was to manage their costs by consolidating their vendors. This would also enable their security team to work more efficiently. They also wanted a vendor that provided strong customer support. And finally, they wanted to seamlessly integrate security awareness into their environment so that their users would learn to make better decisions.
Detection efficacy for inbound threat detection: Proofpoint wins
The security team understood that Microsoft’s email platform is highly targeted by attackers. The rise of AI has enabled threat actors to rapidly develop sophisticated threats. So the team was looking to augment their defenses with a pre-delivery threat detection solution.
They felt confident in choosing Proofpoint because analysts like Gartner consistently position Proofpoint as a leader in the market. Our solution has a 99.99% detection efficacy rate. We feed threat intelligence observed across our 2.1 million global customers into our AI-powered detection stack. This enables it to detect and protect against the widest variety of threats before they reach users’ inboxes.
This unmatched global visibility is the foundation of Proofpoint Nexus, our AI-powered detection stack. Nexus uses content and reputation analysis, look-alike domain identification, predictive sandboxing, large language models (LLMs), behavioral and semantic analysis, and computer vision technology for parsing image-based threats.
After coming back to Proofpoint, the customer noticed a significant increase in their threat detection efficacy. Our pre-delivery email security solution decreased the amount of suspicious and unwanted mail that was delivered to user inboxes by 30%.
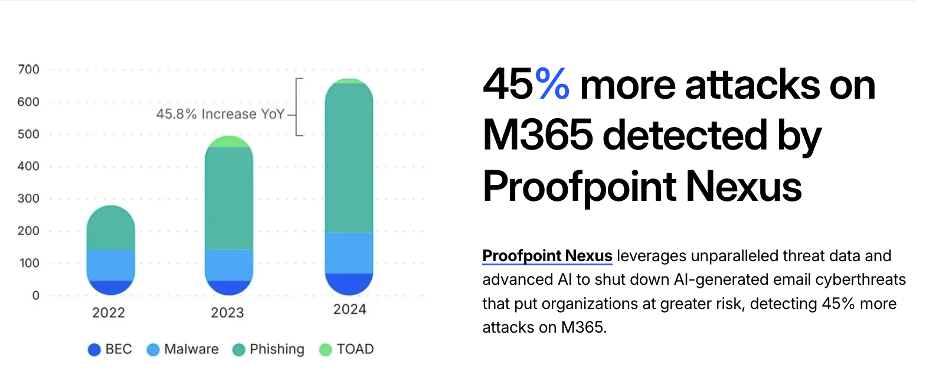
Proofpoint augments Microsoft security defenses.
Visibility and insights: Proofpoint wins
One big criterion for the customer was to have better visibility into their users’ behaviors. They wanted to be able to create risk profiles of their employees and proactively mitigate potential threats.
Proofpoint Targeted Attack Protection (TAP) enabled our customer to detect, analyze and block advanced threats before they reached users’ inboxes. It also helped them to gain insights into their users. This included users’ attack exposure and how well they performed in training and phishing tests.
90% of all breaches involve the human element. It makes sense that frequently attacked employees are more likely to click-on or respond to malicious emails. When it comes to assessing Very Attacked People™ (VAPs) and high-risk users, real-world behaviors are important factors. Security teams need to understand how users handle sensitive data as well as the privileged access that they have to sensitive information or systems. This provides insights into what makes them attractive targets for attacks, like credential phishing and malware.
Proofpoint provides deep user-risk insight and pre-build integrations. As a result, the customer’s security can identify high-risk users and VAPs as well as the types of attacks that target them. Once our customer identifies their VAPs, they can use Proofpoint targeted adaptive controls—like browser isolation, security awareness training and step-up authentication—to better protect their people and business.
Enabling a more efficient SOC team: Proofpoint wins
The customer was experiencing inefficiencies with Microsoft’s email security system. These included long ticket resolution times as well as a lack of understanding about how the system worked. The SOC team felt they didn’t have enough insight to troubleshoot how email was being routed or to provide answers when users had questions about what was happening in their inboxes.
In contrast, Proofpoint provides a more seamless support experience for the customer. The senior manager of enterprise security noted: “After three quarters, we could count on a single hand the number of escalations that we required with Proofpoint. Things work the way they’re supposed to. And when they don’t, we get an answer to why.”
The security team saw a significant reduction in spam emails and advanced attacks making their way into inboxes. This led to a big reduction in the amount of time that the team had to spend managing emails and incidents. As a result, their operational efficiency improved considerably, which allowed them to focus on other high priority tasks.
The customer also wanted to embed security awareness within their platform. They wanted it to go beyond training to encourage employees to make safer choices. In contrast, Microsoft’s approach focuses solely on training metrics and does not assess actual user behavior.
The customer really liked Proofpoint’s ZenGuide. It enabled their team to create a tailored security awareness learning experience that was based on a user’s roles, behaviors, attack exposure and risk profile. What’s more, high-risk users and VAPs can be automatically enrolled into real-time, adaptive learning paths that include timely threat-based guidance and phishing tests. By connecting education to behavior, Proofpoint enables customers to drive meaningful, sustained behavior change. This, in turn, reduces the downstream burden on security teams to remediate threats.
Cost savings with more comprehensive protection: Proofpoint wins
The customer was intrigued by Proofpoint’s additional security capabilities beyond protecting email. While email remains the primary threat vector, cybercriminals are exploiting new channels like messaging platforms, collaboration tools, cloud apps and file-sharing services. Beyond targeting employees, attackers can hijack trusted business communications, disrupting relationships with suppliers and customers.
Proofpoint Prime Threat Protection delivers a unified solution to defend against all human-centric threats. Our customer loved that we offered a solution to safeguard users across collaboration tools and messaging platforms. As part of Prime, Proofpoint Collab Protection extends phishing defense beyond email. Powered by Proofpoint’s industry-leading threat intelligence, we perform real-time URL reputation checks and automatically block malicious links at click-time, ensuring threats are neutralized before they reach users.
Another component of Prime, Proofpoint Supplier Threat Protection addresses vulnerabilities that are often missed by traditional security measures. It proactively identifies and monitors supplier and third-party email accounts for signs of compromise—before they can impact your organization. This is vital because it reduces the risk of financial loss, data breaches and business disruption from supply chain attacks.
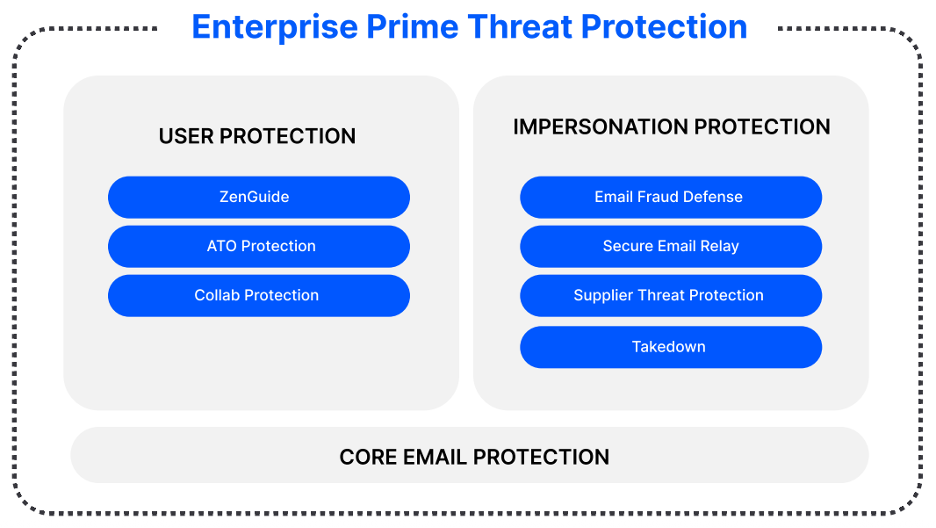
Prime Threat Protection bundles together more protection at a lower price.
Finally, the customer has many different applications within their environment that they use to automatically generate and send emails on their behalf. Proofpoint Secure Email Relay (SER) allowed them to offload that traffic from their Core Email Protection solution. Offloading application email traffic to SER helps separate human and system-generated email flows. This, in turn, made policy enforcement, monitoring, and troubleshooting cleaner and more precise for the customer’s security team.
By consolidating all these additional user and impersonation protection capabilities within Prime Threat Protection, the customer achieved significant cost savings. They also streamlined security management by consolidating their vendors. This helped to minimize administrative overhead, simplify support and decrease the organization’s attack surface. The customer was able to add new layers of protection from a single, trusted provider while staying on budget.
With human-centric cybersecurity, not all solutions are the same
People are a critical component in cybersecurity. Human-centric security solutions enable organizations to take a broader, more effective approach to improving their security posture. It doesn’t matter if human actions are accidental or malicious—it’s important to have the right controls and processes in place to manage human behavior and protect against evolving threats that target them.
Not all solutions can secure your organization to the same degree. Proofpoint enables you to stop a wide variety of threats across different attack surfaces. This includes email, collaboration and messaging platforms, and third-party apps. Plus, it supports SOC teams with insights into risky employee behavior and controls to neutralize them.
Our multilayered detection stack, Proofpoint Nexus, is powered by threat intelligence, machine learning, behavioral AI, sandboxing and semantic analysis. It detects 99.99% of threats from pre-delivery to post-delivery and at the time users click.
To learn more about how Proofpoint can strengthen your organization’s defenses, download our Proofpoint Prime Threat Detection solution brief.











