The much-anticipated State and Local Cybersecurity Grant Program (SLCGP) funding and criteria was released on September 16, 2022. The grant provides state, local and tribal governments with funding to address cybersecurity risks and threats to information systems. As a condition of the funding, state administrative agencies must deliver 80% of the funding to local government with at least 25% passing to rural communities.
The main requirement of the program is to develop and implement a cybersecurity plan. The plan is not required for Year One of funding ($185 million), but a plan will need to be reviewed and approved by 2023. With the ongoing federal focus on Zero Trust Architecture (ZTA), the plan must address seven best practices:
- Multifactor authentication
- Enhanced logging
- Data encryption for data at rest and in transit
- End use of unsupported and end-of-life software and hardware that are accessible from the internet
- Prohibit use of known, fixed and/or default passwords and credentials
- The ability to reconstitute systems (backups)
- Migration to the .gov internet domain
Building an effective cybersecurity plan that provides results to outlast the grant program
The U.S. Department of Homeland Security (DHS) recommends states build cyber plans based on the Cybersecurity and Infrastructure Security Agency (CISA) Cyber Essentials Starter Kit. The kit provides a holistic approach to cyber planning and readiness and outlines several key elements for building a culture of cyber readiness, which include:
- Yourself. Drive cybersecurity strategy, investment and culture.
- Your staff. Develop security awareness and vigilance.
- Your systems. Make sure only those who belong on your digital workplace have access.
- Your data. Make backups and avoid the loss of information critical to operations.
- Your crisis response. Limit damage and quicken the restoration of normal operations
The essential actions rely on your most vulnerable resource and first line of defense: yourself, your staff, the users. With the funding spread over four years, states and local governments will need to build plans that maximize the funds allocated and secure and establish plans that extend beyond federal funding.
Securing, training and protecting users across an organization can help budget and resource constraints extend beyond the four years. Not everyone in an organization is attacked equally, but anyone can be attacked and be a Very Attacked Person™ (VAP).
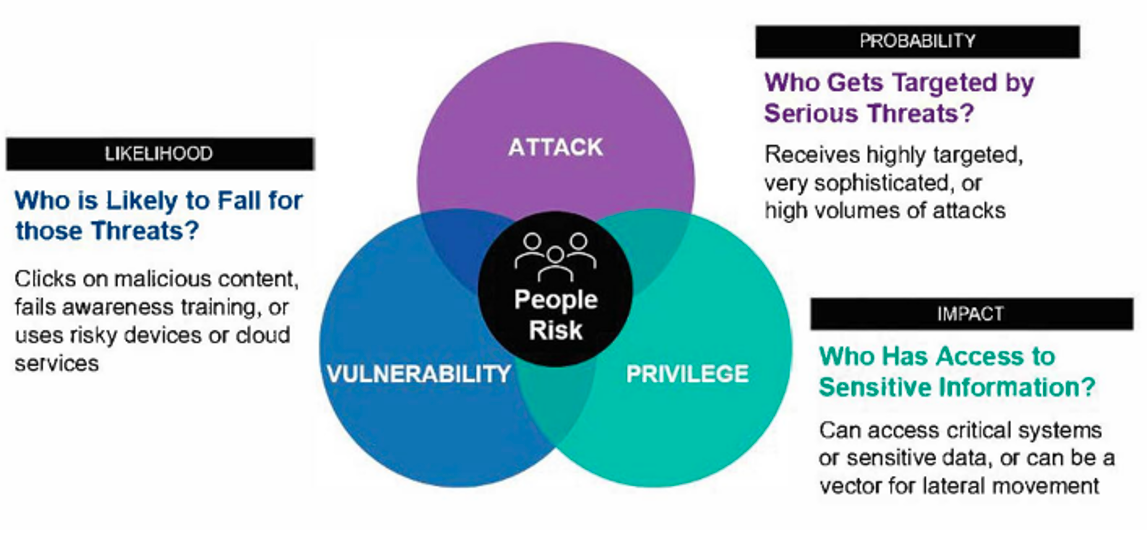
Figure 1. People risk Venn diagram: attack, vulnerability and privilege.
1. Protect your No. 1 threat vector and gain visibility into your VAPs
Start by solving your email threats across the entire attack chain, from detection to response. Gain visibility into who is being attacked, how they’re being attacked, whether they click on or report phishing, and whether they’re already compromised.
2. Expand your people-centric protections and start securing your cloud accounts
This will help you protect against threats and data loss in all people-centric threat vectors, including external email, cloud accounts, personal webmail and internal email. Train users to be your first and last line of defense. Equip them to recognize and report on phishing attacks, and educate them on best practices to keep their identities, credentials and data secure.
3. Build a comprehensive people-centric security program
Broaden protection to cover your entire human attack surface, including your business ecosystem. Make sure the people you do business with aren’t putting your organization at risk. Also, integrate your security ecosystem to make the most of existing investments. Protect your VAPs through more integrated, isolative and adaptive controls.
State administrative agencies have a deadline of November 15, 2022, at 5:00 p.m. ET, to submit applications for Year One, and December 31, 2022, is the expected award announcement date.
The Proofpoint public sector team is ready to provide a proposal and cyber plan support to state administrative agencies and local governments. Local government involvement during the application proposal process is integral to improving cyber readiness and protection across jurisdictions. Reach out to the Proofpoint team today.











