Supply chains have become a focal point for cyberattacks in a world where business ecosystems are increasingly connected. Email threats are a significant risk factor, as threat actors are keen to use compromised email accounts to their advantage. Every month, a staggering 80% of Proofpoint customers face attacks that originate from compromised vendor, third-party or supplier email accounts.
Known as supplier account compromise, or vendor email compromise, these attacks involve threat actors infiltrating business communications between trusted partners so that they can launch internal and external attacks. Their ultimate goal might be to steal money, steal data, distribute malware or simply cause havoc.
In this blog post, we’ll explain how vendor emails are compromised and how you can stop these attacks. Finally, we’ll tell you how Proofpoint can help.
What’s at stake
Supply chain compromise attacks can be costly for businesses. IBM, in its latest Cost of a Data Breach Report, says that the average total cost of a cyberattack that involves supply chain compromise is $4.76 million. That is almost 12% higher than the cost of an incident that doesn’t involve the supply chain.
In addition to the financial implications, compromised accounts can lead to:
- Phishing scams that result in even more compromised accounts
- Reputational and brand damage
- Complex legal liabilities between business partners
How does vendor email compromise occur?
Supply chain compromise attacks are highly targeted. They can stretch out over several months. And typically, they are structured as a multistep process.
The bad actor initiates the assault by gaining access to the email account of a vendor or supplier through various means. Phishing attacks are one example. Once the attacker gains access, they will lay low for an extended period to observe the vendor’s email communications. During this time, the adversary will study the language and context of messages so that they can blend in well and avoid detection.
Attackers might also use this observation period to establish persistence. They will create mail rules and infrastructure so that they can continue to receive and send messages even after the vendor has regained control of the account.
Once they establish access and persistence, the attackers will begin to insert themselves into conversations within the supplier’s company as well as with external partners and customers. By posing as the sender, the attacker takes advantage of established trust between parties to increase their chances of success.
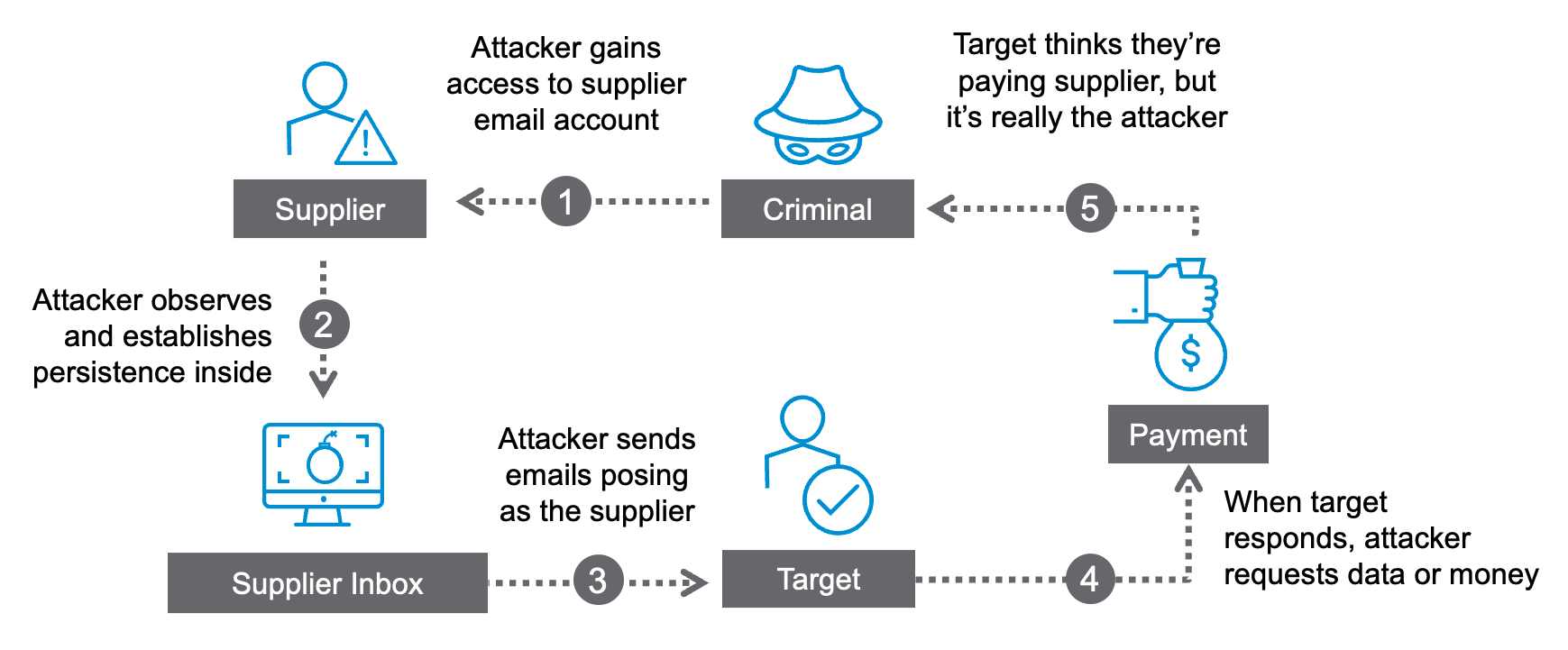
Overview of a vendor email compromise attack.
Proofpoint has observed a growing trend of attackers targeting accounts within smaller businesses and using them to gain entry into larger companies. Threat actors often assume that small businesses have less protection than large companies. They see them as targets that can help them achieve a bigger payday.
How to stop vendor email compromise
If you want to defend against these attacks, it’s critical to understand the methods behind them. Such a formidable problem requires a strategic and multilayered solution. The four broad steps below can help.
Step 1: Know your suppliers
Your first line of defense against these email attacks sounds simple, but it’s challenging. It is the ability to intimately “know your supplier” and understand their security strategy. This requires more than a one-time vendor assessment. Your security teams will need to prioritize continuous monitoring of your company’s business partnerships.
On top of that knowledge, you need a thorough understanding of the access and privileges that your business grants to each vendor. Compromised accounts that have uncontrolled access may be able to exfiltrate sensitive data or upload malware like ransomware. So, when you know what your suppliers can (and can’t) access, you can identify a data breach faster.
Other steps, like requiring multifactor authentication (MFA) for vendor accounts, can help mitigate the risk of supply chain compromise. Keep in mind, though, that there is no silver bullet.
Also, while you may want to develop a thorough understanding of all your business partners’ security practices, it can be extremely difficult to achieve this goal. Many companies work with hundreds to thousands of third-party vendors and suppliers. Knowing who they are, and monitoring and prioritizing the riskiest parties among them, is a dynamic and ongoing process. For teams to keep up, they need automated tools at the very least.
Step 2: Know when your suppliers are compromised
You need to know more than just who your suppliers are. You must be aware when their accounts are compromised. And you must know as quickly as possible.
Smaller vendors often don’t realize that their accounts harbor attackers. That is why bad actors tend to linger in these compromised accounts. How long will they linger? IBM reports that the average time spent before detection is 233 days—or about seven and a half months.
Unfortunately, even the most prepared cybersecurity teams may rely solely on notifications from suppliers to learn about potential breaches. That leaves them in a reactive security stance. They must react to incidents after they’ve already happened rather than preventing them.
To shift the balance toward proactive defense, security teams should have access to mechanisms that provide timely visibility and insights into the security status of suppliers. Fostering a culture of prevention rather than reaction is the best way to secure users.
Step 3: Create layers of advanced protection
Scammers continually refine their tactics. That’s why traditional security methods struggle to identify vendor email compromise attacks. These threats are designed to evade conventional detection. They feature “normal” and non-urgent language. And they rely on manipulating people rather than code.
Employing DMARC to prevent fraudulent email spoofing is a step in the right direction. But it can’t prevent attacks from compromised accounts. Increasing employee security awareness is crucial, too. However, these threats can deceive even vigilant users due to the inherent trust in communication with suppliers.
These attacks are subtle until they’re not. If you want to defend against them, you need advanced protection measures like:
- Artificial intelligence (AI)-driven detection
- Advanced behavioral analysis
- Adaptive controls that offer the right protection at the right time by limiting communication with compromised accounts or blocking it altogether
Any method of protection must also have high levels of sensitivity. Otherwise, you could risk stopping legitimate business communications that are necessary for your company to operate.
Step 4: Streamline your investigation process
Email threats that stem from supply chain compromise demand an investigation process that is efficient and streamlined. These attacks often lead to data and financial loss. So, investigations by your security team will require a meticulous examination of the scope of communications.
The threat actor’s chosen vector is the starting point for examination. Vectors include email, network, cloud and third-party apps. Your analysts must also develop a thorough understanding of the access privileges associated with the compromised account. (Sadly, many analysts find that this manual task is both time-consuming and error-prone.)
Even when an attack is blocked, it is critical to have a retrospective review of prior messages. Most security controls focus on “message level” safety, or the likelihood that an individual message contains a threat. But analysts must look more broadly to know the sender’s level of security and whether an entire account may be compromised. Only then will they be able to understand which suppliers pose a risk or are susceptible to patterns of bad behavior.
Investing in tools that automate and expedite the investigative process will help your business address these challenges. When you consolidate investigative undertakings, you can help your security teams respond more effectively. And you can use the insights you gain to fortify your defenses and prevent future attacks from vendor email compromise.
Protect your business from vendor email compromise
Proofpoint can help your business address the challenges above and tackle the complex issue of supplier risk. Proofpoint Supplier Threat Protection automatically identifies suppliers and monitors their accounts to detect potential account compromise. When suspicious activity is detected, it can send alerts to your security teams—even if your users haven’t been attacked yet.
Thanks to the recent integration of Proofpoint Supplier Threat Protection and Proofpoint Isolation, isolating links in messages from potentially compromised suppliers is now automated. This can stop attacks that lead to account takeover and ransomware by making sure that users can’t:
- Download malware
- Access malicious phishing sites
- Upload credentials
With help from Proofpoint, your security team can become proactive—and prevent attacks. To learn more about Proofpoint Supplier Threat Protection, see this data sheet. You can also check out the video below to learn more about how to protect your supply chain from compromised senders.











