Research for the “2022 Voice of the CISO” report from Proofpoint found that 50% of chief information security officers (CISOs) believe the Great Resignation—an ongoing economic trend where a high number of employees are leaving their jobs voluntarily—has made protecting data more challenging.
Organizations often find out too late that a “leaver” has taken sensitive business information—or worse, intellectual property—when they exited the company. Security teams then need to engage in a long manual hunt to collect answers on the “who, what, where and when” of this insider-related data loss.
Human resources (HR), legal and information security teams are often challenged in their ability to coordinate on information about leavers — let alone put effective monitoring policies in place without insider threat management solutions. But now that Proofpoint has expanded our visibility to cover insider threats with unmanaged devices, organizations can stay on top of data protection issues related to leavers more effectively.
Proofpoint Information Protection can now detect anomalous file activity by leavers on cloud apps on unmanaged devices and provide a 30-day file activity timeline for these users. Several customers are already using these capabilities to identify previously invisible data exfiltration by leavers. These capabilities complement our existing market-leading solution against insider threats (focused on managed endpoints).
High-risk insider: Monitor leavers before they exit
Meet Camila. She’s a high-flying executive who will soon leave the firm. She wants to take sensitive information from her current employer to her next one so she can continue her successful career. Camila feels her hard work at her current organization entitles her to take some of the customer lists, product pricing and product architecture diagrams. For the organization, this behavior would violate many corporate policies.
Below is a timeline of Camila’s activity and how Proofpoint helped the security team protect the organization.
|
Timeline of Activity |
The Actions of Camila, the Leaver |
|
Security Measures (Using Proofpoint) |
|
A month ago |
Attempts to copy sensitive pricing files onto an unapproved USB device |
|
Proofpoint blocks the USB file transfer in real time |
|
25 days ago |
Searches and applies for jobs online |
|
Proofpoint collects this telemetry |
|
A week ago |
Gives a two-week notice to leave the firm |
|
HR moves the executive into a designated Active Directory group during the notice period |
|
A few days ago |
Uses a personal laptop to download an unusually large number of files from cloud apps |
|
Proofpoint detects this file activity to a personal device by Camila as anomalous compared to the organization and Camila’s past behavior |
|
A few days ago |
|
|
Proofpoint provides a timeline of Camila’s past activity across cloud, email, endpoint and web for investigations |
|
Now |
|
|
HR and Legal suspend Camila before she can leave the organization on her own |
Figure 1. Overview of an example leaver’s activity and how the organization responded to it with help from Proofpoint.
Let’s take a closer look at each step of this insider threat journey.
Preventing data exfiltration to USB devices
In this phase, Camila knows she wants to leave the firm and wants to prepare before she turns in her departure notice. Camila has just attempted to copy sensitive pricing files onto an unapproved USB device. In real time, Proofpoint Information Protection blocked the file transfer.
With legacy, endpoint data loss prevention (DLP) solutions, your teams deal with more complexity to achieve the same result: Set up DLP detectors for each channel separately, create a policy for each type of data and create exceptions for specific users. This is a consequence of legacy DLP solutions being data-centric models.
You can set up people-centric DLP prevention rules in Proofpoint Information Protection so that your team can easily understand and monitor risky users. (Learn more about how to detect and prevent data loss to USB devices in our deep-dive webinar.)
Granular user behavior visibility
Camila searched and applied for jobs online on her managed endpoint, and Proofpoint Information Protection captured her web activity. This was before Camila even turned in her departure notice.
Telltale signs of leaver behavior go beyond data activity. (To find out more about various user and data activities to watch for, check out our insider threat webinar.)
These behaviors on their own may not be concerning enough to any security team inundated with high priority alerts. Similarly, Camila searching and browsing new job postings is only important as further context to the other security violations by Camila.
Personal devices: Detecting anomalous file activity from the cloud
Camila attempts to download an unusually large number of sensitive files from Microsoft 365 apps onto her personal laptop. A few days earlier, she had given her departure notice, and HR had changed her Microsoft Azure Active Directory group to reflect that. Through proprietary machine learning models leveraging data from Microsoft 365 services, Proofpoint Information Protection identifies Camila as a leaver and detects the file download activity as anomalous.
Proofpoint is constantly monitoring for anomalous file activity by users on managed and unmanaged devices in Microsoft 365 apps. Anomalies are calculated using machine learning models based on a user’s activity profile relative to their own past profile, the organization’s profile and the nature of the files involved—including file sensitivity, file ownership and number of files.
Proofpoint is also monitoring Active Directory groups to identify leavers in every organization. Leavers includes those who’ve recently left the organization and those leaving soon, such as Camila.
When Camila’s anomalous file activity is detected, a security alert is generated with rich forensics, as shown below.
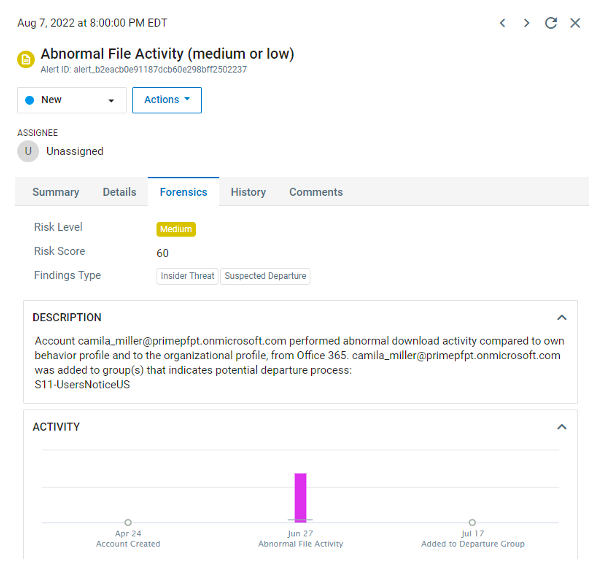
Figure 2. Anomalous file activity by the leaver (“Camila”).
The activity graph indicates that Camila downloaded a statistically significantly larger number of files (purple bar) than the normal bounds of activity for her own profile and the organization’s profile (represented by the gray line that crosses the bar toward the bottom). Proofpoint would identify the anomalies even if Camila started her malicious activity before giving her departure notice, by the way.
You can identify whether Camila downloaded the files to her managed or unmanaged endpoints. Unmanaged devices refer to desktops, laptops, mobile phones and tablets that the organization doesn’t manage or own. In the screenshot below, with sensitive data masked, you can see how client device properties are used to identify whether the device is managed or unmanaged. It would be more incriminating if Camila downloaded this information while connecting into the Microsoft 365 app using a competitor’s network or IP address space.
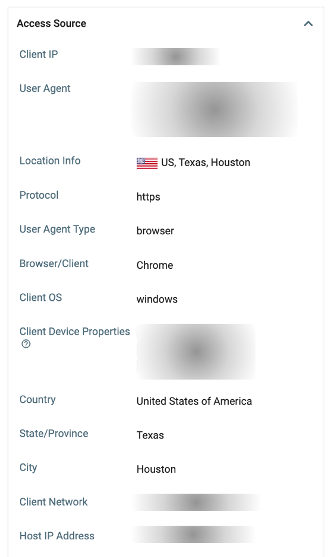
Figure 3. Identifying device details, including whether the device is managed or unmanaged.
In Camila’s case, the files also happened to be sensitive in nature, as we can see below in Figure 4. Eleven percent of the files Camila downloaded were sensitive in nature, containing Social Security numbers and credit card information. Only 22% of the files downloaded were not owned or created by Camila. An alert of anomalous file activity containing a significant amount of sensitive information would naturally be a higher priority.
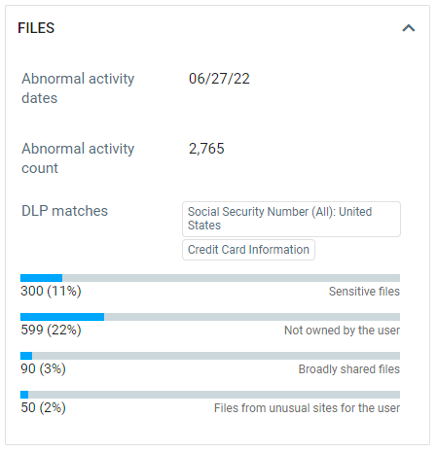
Figure 4. Overview of the types of files downloaded by the leaver.
Without detection capabilities like these, security teams need to stitch together the visibility from cloud apps, DLP tools and HR information. Often, they’re left with incomplete information and the manual processes break down.
Sometimes, detecting anomalous file activity by leavers can be the first time security teams are aware of data exfiltration by a user. Teams using legacy DLP tools are inundated with data-centric alerts without user context. Anomalous activity alerts from Proofpoint are tied to high-risk users such as leavers, which raises the risk profile for security teams beyond ordinary DLP alerts
Accelerating insider investigations
At this point, the security team is in full swing investigating Camila’s behavior and every hour saved is precious. Proofpoint Information Protection can provide a consolidated view across Camila’s behavior in the cloud, on email, on her endpoint and on the web in a single user timeline. You would see Camila’s attempted USB file transfer, job search web activity, anomalous file activity in Microsoft 365 as well as any of her other day-to-day activity in one timeline.
Check out our visual guide to compare insider threat investigations using Proofpoint Information Protection versus ad-hoc investigations. With Proofpoint, you can eliminate hours or even days of manual data collection on a user’s activity across the technologies they used. Proofpoint Information Protection also provides uninterrupted visibility of user behavior and file activity without the need to go to IT for assistance—and potentially, delaying an investigation.
Proofpoint Information Protection provides comprehensive protection against leavers taking your organization’s sensitive data. Security teams can set up policy-based and machine learning-based detection to identify activities they might otherwise miss. They can prevent obvious out-of-policy data movement and suspend leavers’ cloud accounts. And when there’s a need to investigate users, the power of one platform accelerates decision-making for the appropriate response alongside HR and legal.
Want to learn more about how Proofpoint can protect your organization and its assets from malicious leavers? Check out the Proofpoint Information Protection solution demo.











