The U.S. Federal Bureau of Investigation (FBI) issued a warning recently that threat actors are using fake job postings to steal personally identifiable information, which is a tactic we’ve previously seen within malicious email campaigns. Proofpoint has observed multiple threat actors leveraging job and resume-themed lures in 2021, with thousands of messages associated with each of the campaigns. Although job-themed threats are often very basic, some notable campaigns observed by Proofpoint are worth highlighting for the attack complexity.
Job-themed Phishing and Unemployment Fraud
Job offers or potential employment opportunities are perennially popular threat lures. As the COVID-19 pandemic has forced many people out of work, such themes can be more alluring to a wider potential victim pool.
According to the FBI, unemployment fraud – including online campaigns – cost people more than $59 million in 2020. These types of campaigns use various methods to lure victims into clicking on malicious links, downloading attachments, or sending personal data to the threat actors. The goals of these campaigns are broad and can be used for general data theft, initial access to an organization, or to steal money from victims.
Commodity Business Email Compromises
Business Email Compromise (BEC) threat actors are leveraging job-themed threats in ongoing campaigns. BEC email fraud is one of the most financially damaging threats to businesses of all sizes and across industries.
Recently, the job-themed BEC threats observed by Proofpoint are commodity BEC threats which are typically high volume with large spread. Senders in these campaigns use free email services such as Yahoo or Outlook, and can quickly and cheaply recreate new email addresses once malicious emails are burned or blocked by security services.
For example, Proofpoint observed email threats offering work-from-home opportunities with high salaries.
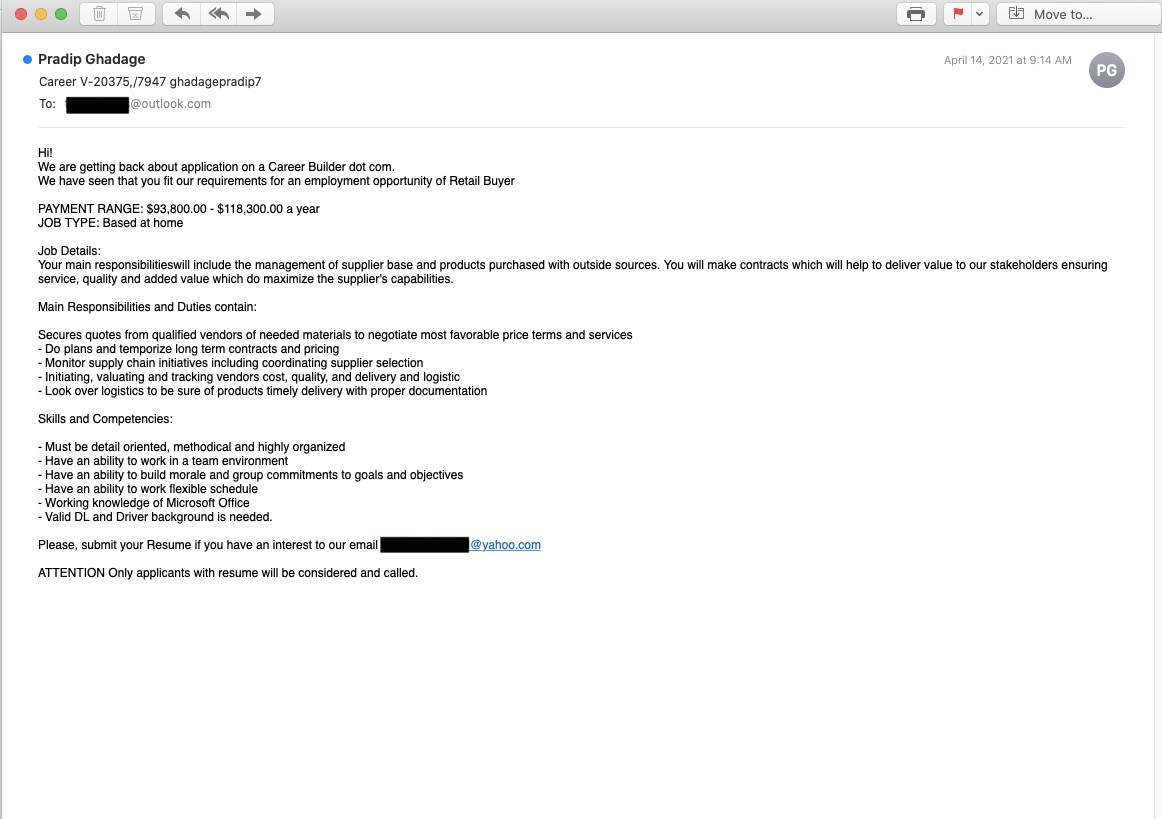
Figure 1: BEC email threat containing a high-paying job offer.
Although it is not clear the goal of the threat actors in these scenarios, there are typically multiple outcomes that are possible if the recipient replies. One possibility is using these threats to recruit Mules, or Money Mules. Money mules are a mechanism used to move funds around and obfuscate the fund origin. This person acts as an intermediary between attackers. Mule accounts are often set up under the guise of legitimate "work-from-home" offers. The victim is led to believe what they're doing is a legitimate function. The mule will often receive a portion of the money acquired during other fraudulent activities.
Another possibility is an advance-fee fraud (AFF) threat where the threat actor asks for a smaller amount of money in advance, promising a larger payout later. While there are endless variations of these types of threats, typical attacks may impersonate a government official, a legal representative, or a person in a dire situation. The threat actor will have a story for how they have received a large amount of money, for example, a fake job offer. However, the actor cannot receive that money without paying an upfront fee and require the threat recipient's help. In exchange for helping, the recipient will get their money back plus a portion of the large amount. Once the threat actor receives the advanced payment, they'll often cut all contact and disappear.
More_eggs in March 2021
Sometimes job-themed threats will use more sophisticated tactics. In March 2021, Proofpoint observed a multi-step job-themed campaign distributing the More_eggs downloader. More_eggs is a Javascript backdoor used to establish persistence, profile the machine, and drop additional payloads. Proofpoint first observed employment-related campaigns distributing this malware in 2018.
These campaigns are associated with a threat actor Proofpoint tracks as TA4557 and the group uses the More_eggs downloader to profile the victim machine and distribute additional payloads.
The new campaigns mimic previous activities and send victims messages with subjects offering a job position. The initial message is frequently a LinkedIn connection request or another benign message regarding a job. The actor subsequently follows up with an email message that contains a URL linking to a landing page that mimics a job site. The page initiates a download of an attachment that ultimately is used to execute the More_eggs downloader.
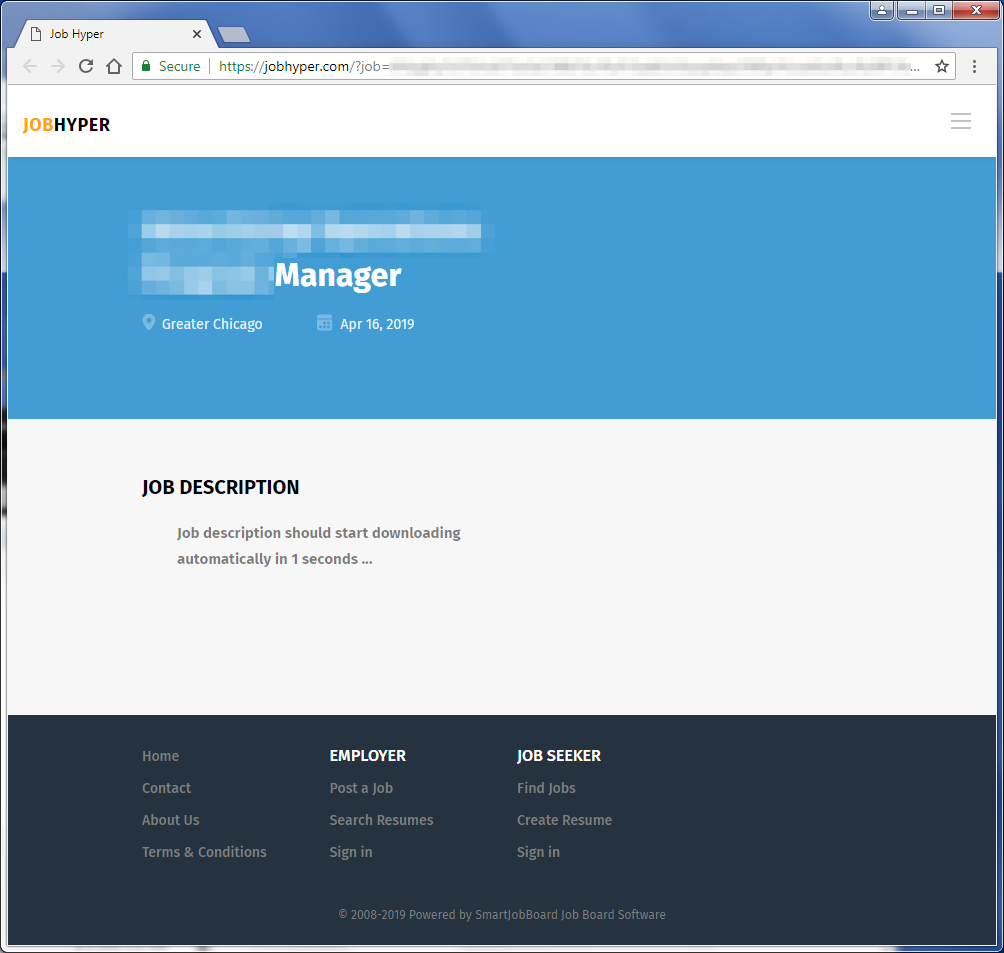
Figure 2: Sample malicious landing page that leads to the More_eggs download.
Additional 2021 employment-themed campaigns distribute the Kodiac remote access tool, Minebridge backdoor, and Osiris banking trojan.
Conclusion
Job, employment, and resume-themed phishing lures are popular mechanisms threat actors use to distribute malware, steal sensitive data, and establish initial access to target endpoints. To reduce the risk of successful exploitation, Proofpoint recommends the following:
- Educate users to identify and report suspicious email. Regular phishing training and simulated attacks can help prevent attacks as well as assist in identifying people who are especially vulnerable to attacks.
- Understand that users will eventually click some threats. Attackers are always innovating to find new ways to exploit human nature. Find a solution that spots and blocks inbound email threats targeting employees before they reach the inbox that can manage the entire spectrum of email threats. Some threats—including business email compromise (BEC) and other forms of email fraud—can be hard to detect with conventional security tools. Your solution should analyze both external and internal email—attackers may use compromised accounts to trick users within the same organization. Web isolation can be a critical safeguard for unknows and risky URLs.
- Do not accept or engage with unknown social media requests. Threat actors commonly use social media to distribute malware or establish initial connections with victims. It is best practice to not engage with, download attachments, or click on links provided by unknown users.











