Key Takeaways
Proofpoint researchers have uncovered several new ways of effectively abusing Microsoft Teams, including:
- Post account compromise impersonation and manipulation techniques
- Using tabs for phishing users
- Using tabs for instant malware download
- Weaponizing meeting invites by replacing default URLs with malicious links
- Weaponizing messages by replacing existing URLs with malicious links
Overview
Microsoft is a major productivity partner for many organizations and enterprises. These organizations widely trust Microsoft Office’s suite of products as a reliable foundation for their daily cloud ecosystem needs. However, as Proofpoint has shown in the past, this migration to the cloud also introduces new kinds of threats.
Today, attackers set their sights on cloud environments and services and try to leverage existing security flaws and vulnerabilities for various nefarious purposes. We have published extensively about these trends, showing how threat actors are using Microsoft services for attacks, and disclosing how attackers could effectively weaponize Microsoft Sway while bypassing security measures. Alarmingly, Sway is not the only app to be targeted and abused by threat actors.
Proofpoint’s threat researchers recently analyzed over 450 million malicious sessions, detected throughout the second half of 2022 and targeting Microsoft 365 cloud tenants. According to our findings, Microsoft Teams is one of the ten most targeted sign-in applications, with nearly 40% of targeted organizations having at least one unauthorized login attempt trying to gain access.
Figure 1 - Top 10 most targeted Sign-in apps in the second half of 2022
In this blog post we will uncover multiple methods to abuse one of the most popular (and most targeted) native cloud applications: Microsoft Teams. These techniques allow malicious actors to effectively execute Office 365 credentials phishing, deliver malicious executables, and expand their foothold within a compromised cloud environment.
Abusing the Default Tabs Mechanism
Microsoft Teams platform provides a personal and group messaging mechanism, through Teams channels or chats. Each channel or chat can contain additional tabs created by different applications. An example of a default tab appearing in personal and group chats is the “Files” tab, associated with SharePoint and OneDrive (Figure 2). We have found that tabs manipulation could be part of a potent and largely automated attack vector, following an account compromise.
Usually, users may rename tabs however they choose, as long as the new name does not overlap with an existing tab’s name (for example: “Files”). In addition, users are supposedly restricted from re-positioning tabs in a way that places them before default tabs (e.g., “Files”).
However, we have discovered that using undocumented Teams API calls, tabs may be reordered and renamed so that the original tab can be swapped with a new custom tab.
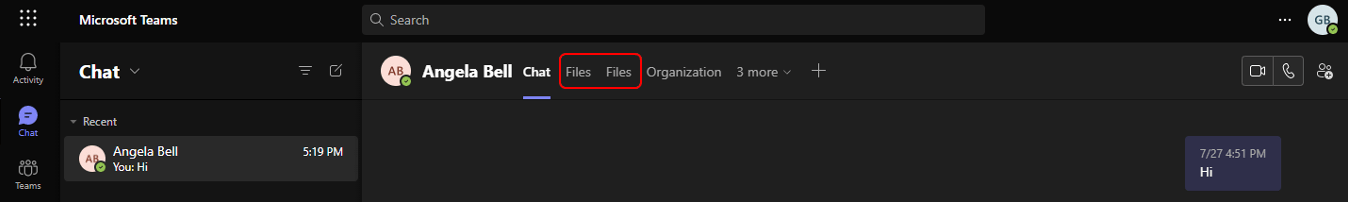
Figure 2 - A fake 'Files' tab created and placed before the original tab
One way that this seemingly benign “feature” can be leveraged by threat actors is by using a native app, “Website”, which allows users to pin a chosen website as a tab at the top of a Teams channel or chat (Figures 3 & 4).
After pinning a “Website” instance as a tab, an attacker can manipulate the tab’s name, changing it to an existing tab’s name, and then repositioning it. This effectively allows the attackers to push the native tab out of view, and therefore increase the chances of using the fraudulent tab.

Figure 3 - Adding a new tab to a Teams chat
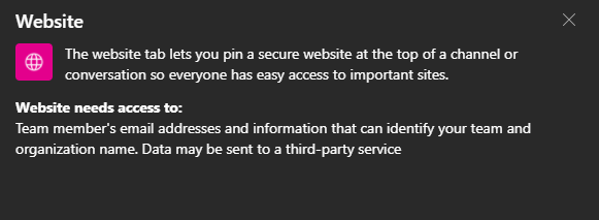
Figure 4 - Informative description of the Website app tab, as given in Teams
This new tab could be used to point to a malicious site, such as a credential phishing webpage posing as a Microsoft 365 sign-in page (Figure 5). This could be extremely attractive for attackers, seeing as, by design, a website tab’s URL is not displayed to users unless they deliberately visit the tab’s ‘Settings’ menu.
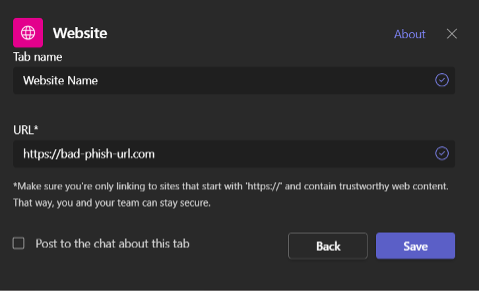
Figure 5 - Setting a new tab pointing to a nefarious web page, using Teams’ user interface
Although browser security best practices educate users to closely examine key indicators (such as the URL bar) and to not click on suspicious links, in this case all those instructions are irrelevant, as Teams does not provide a visible URL bar. Therefore, unsuspecting victims are unlikely to notice that the web page they access is, in fact, malicious.
As our simulation shows (Figure 6), when combined, the above-mentioned hazardous functionalities allow threat actors to seamlessly plant malicious content within compromised Microsoft 365 environments, with minimal risk of exposure.
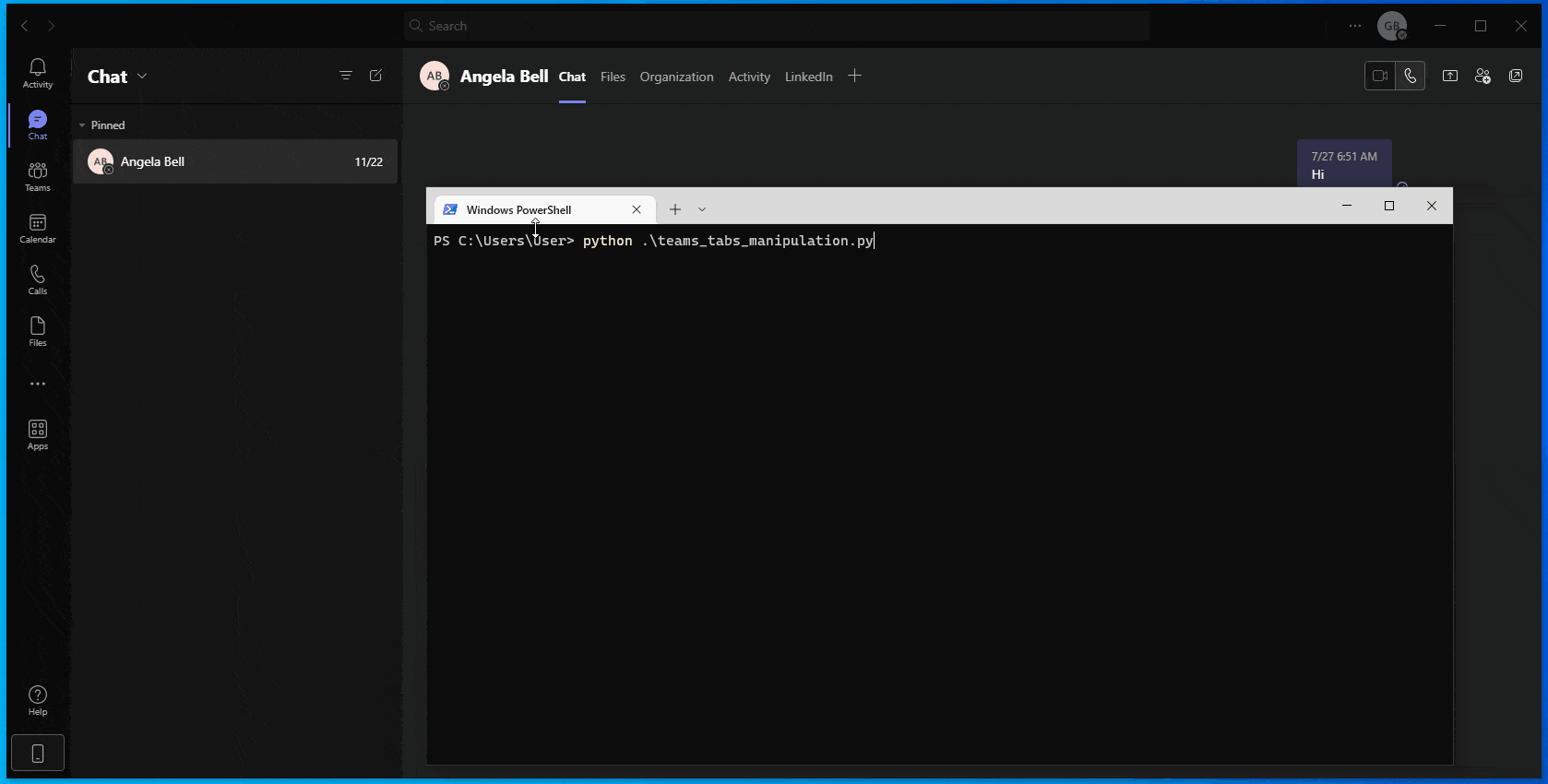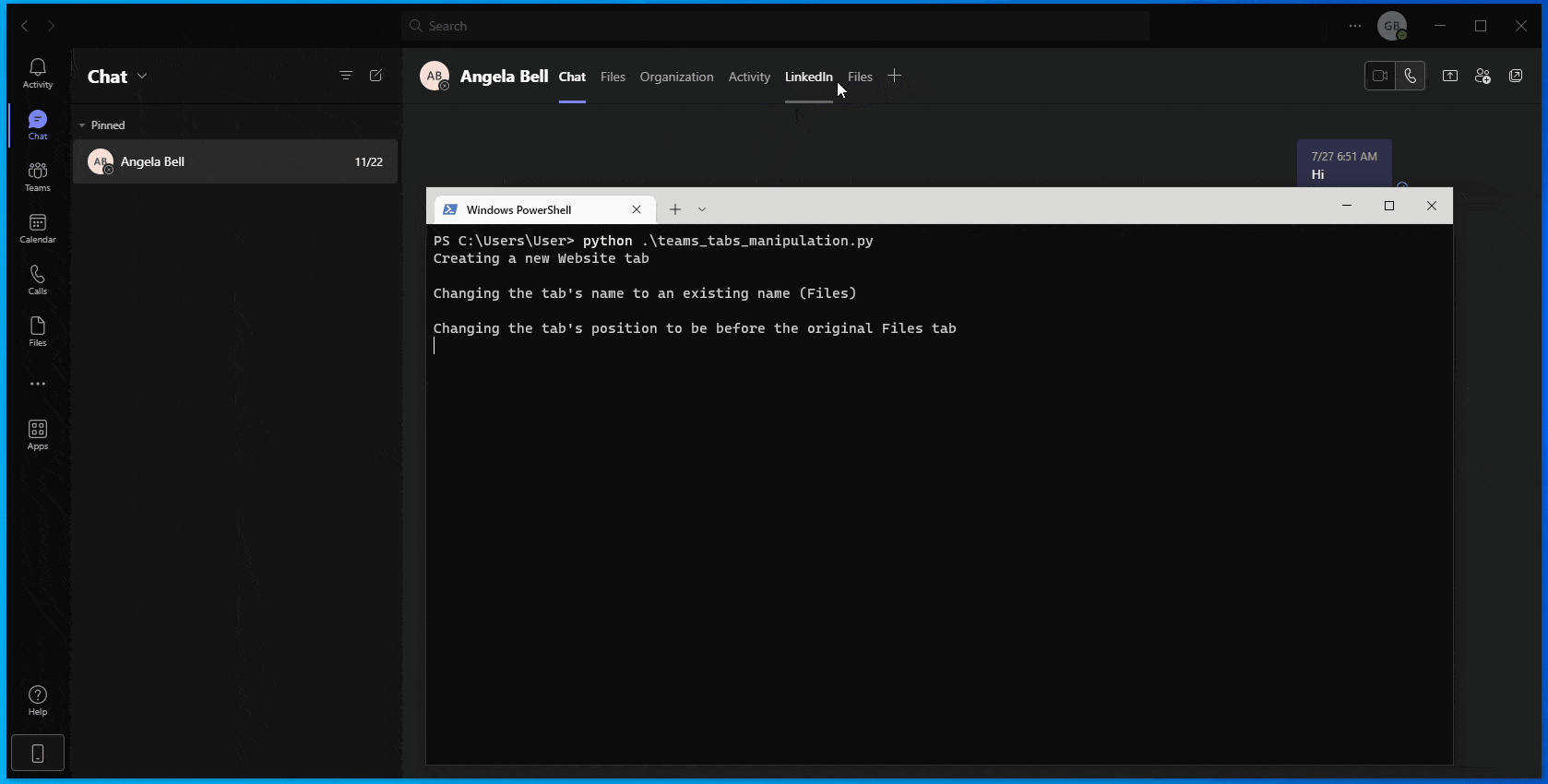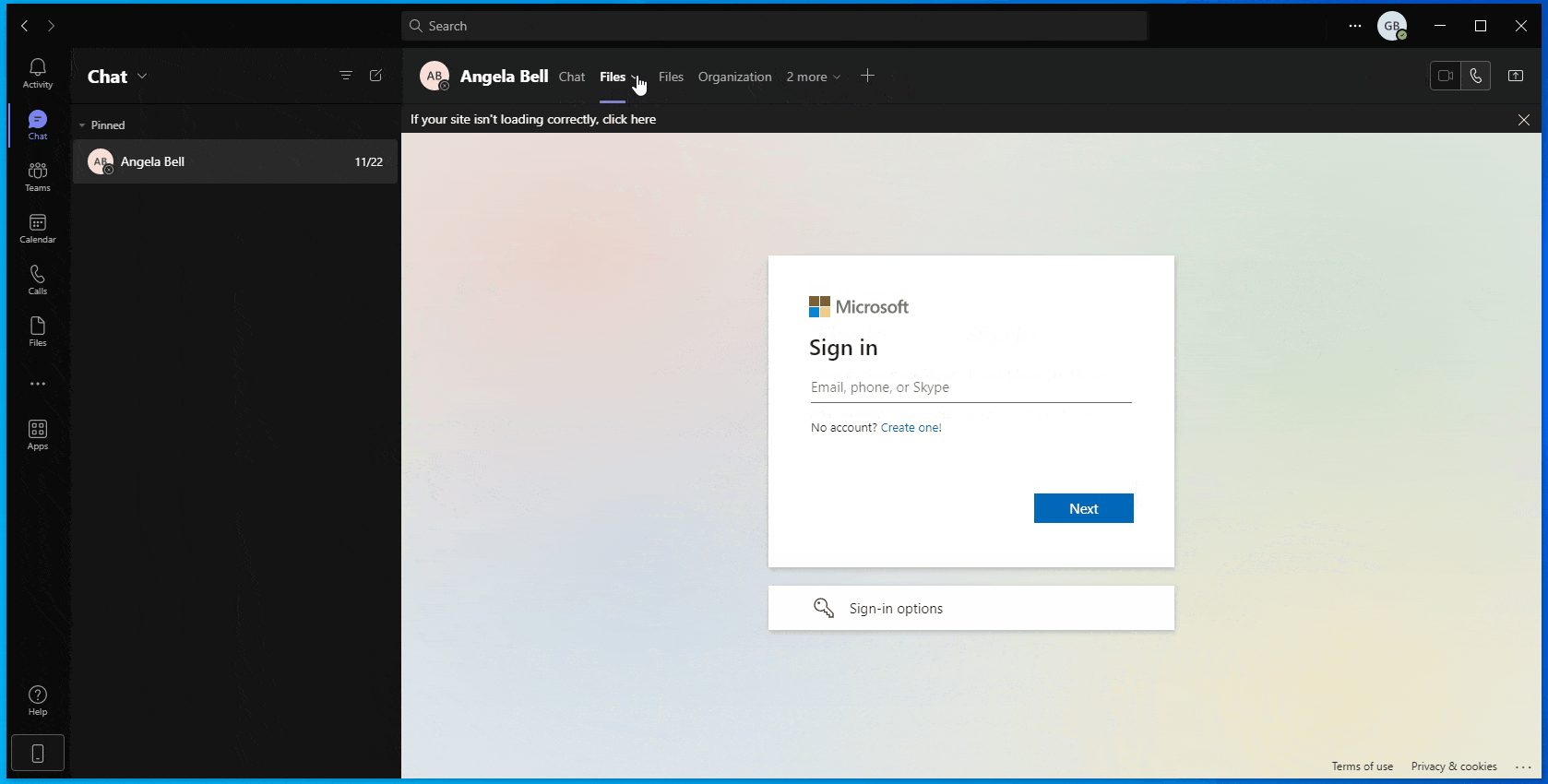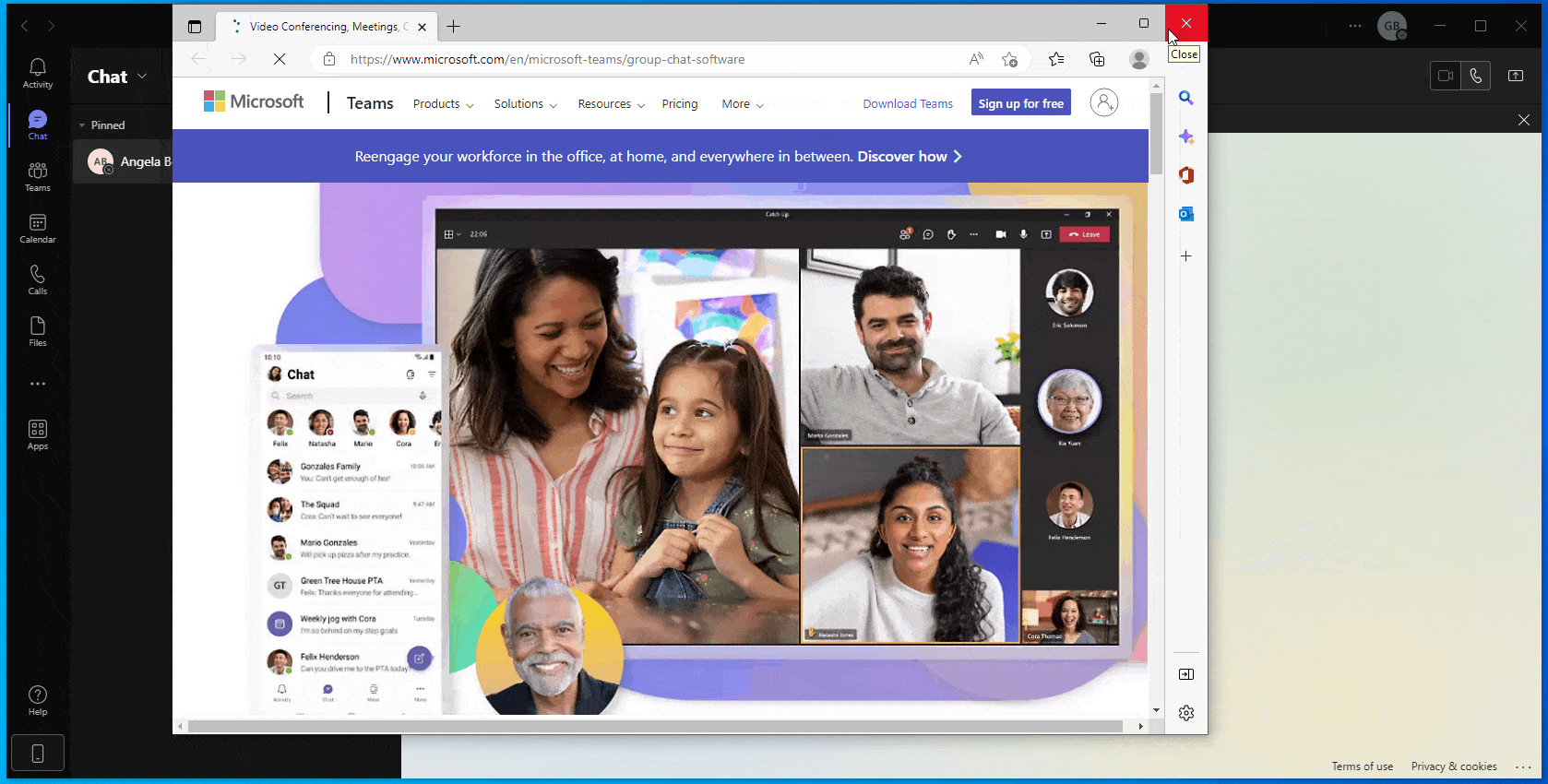
Figure 6 – Tabs manipulation using undocumented API calls:
(1) Creation of a new ‘Website’ tab; (2) Change of tab name from (‘Website’) to impersonate a default tab (‘Files’); (3) Change the new tab position before the original tab; and (4) Change the tab’s target URL to refer to nefarious\legit web page
But we are not done yet. Another way of easily abusing the same mechanisms is by using the Website tab to point to a file. This causes Teams (desktop or web client) to automatically download the file to the user’s device, potentially placing malicious droppers inside victims’ corporate devices and networks (Figure 7).
Figure 7 – Simulation of tabs manipulation using undocumented API calls:
Automatic download of malicious file linked to our fake ‘Files’ tab. In this case, our new tab refers to a benign URL in order to conceal its “malicious” intent.
Weaponizing Meeting Invites
Tabs are not the only Teams feature open to exploitation and abuse by malicious actors. The Microsoft Teams platform can also sync with a user’s calendar to display, create, and edit scheduled meetings. By default, when creating a Teams online meeting, several links are generated and sent within the meeting’s description (Figure 8). These allow users to join the online meeting or download Teams’ desktop client.
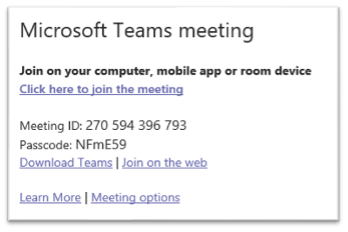
Figure 8 - Default links included in a Microsoft Teams meeting invite
Whereas usually an attacker would need access to Outlook or Microsoft Exchange in order to manipulate the content of a meeting invite, once attackers gain access to a user’s Teams account, they can manipulate meeting invites using Teams API calls, swapping benign default links with malicious ones.
As shown in our simulation below (Figure 9), a sophisticated attacker may automatically alter the default links within a meeting invite so that users, both outside and inside the organization, are referred to phishing pages or to malware-hosting sites, thus causing instant download of malware posing as Teams installation files.
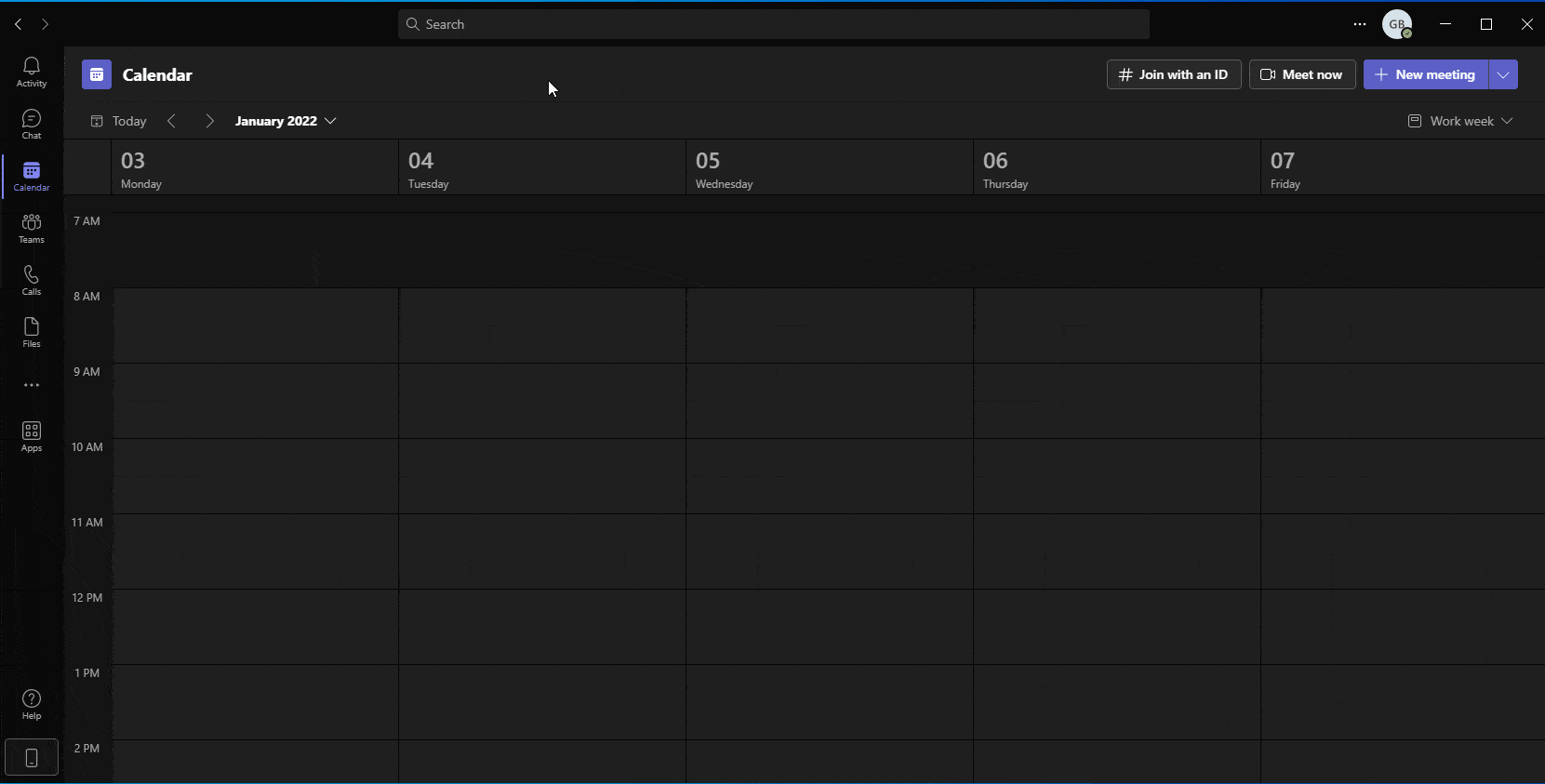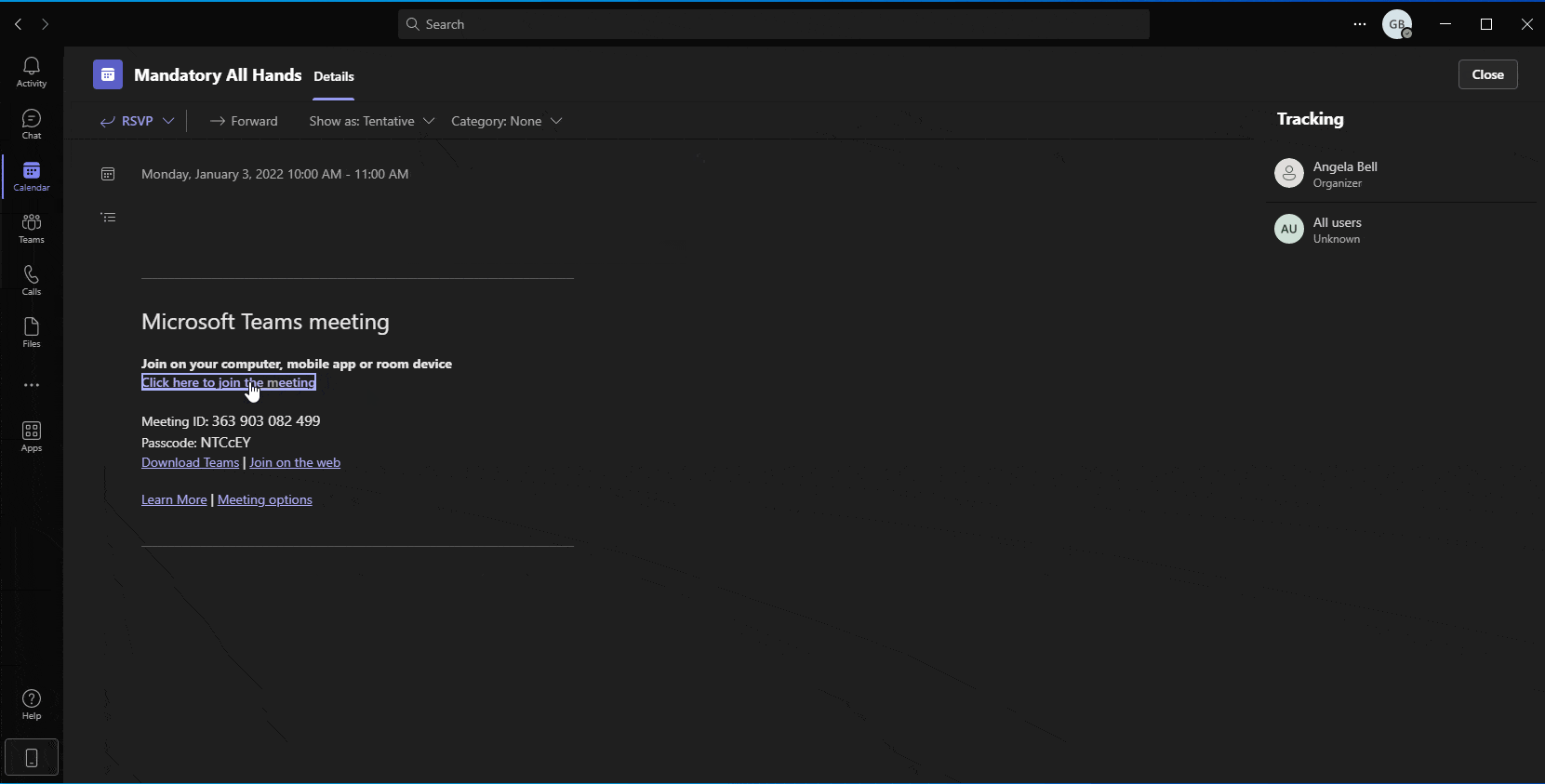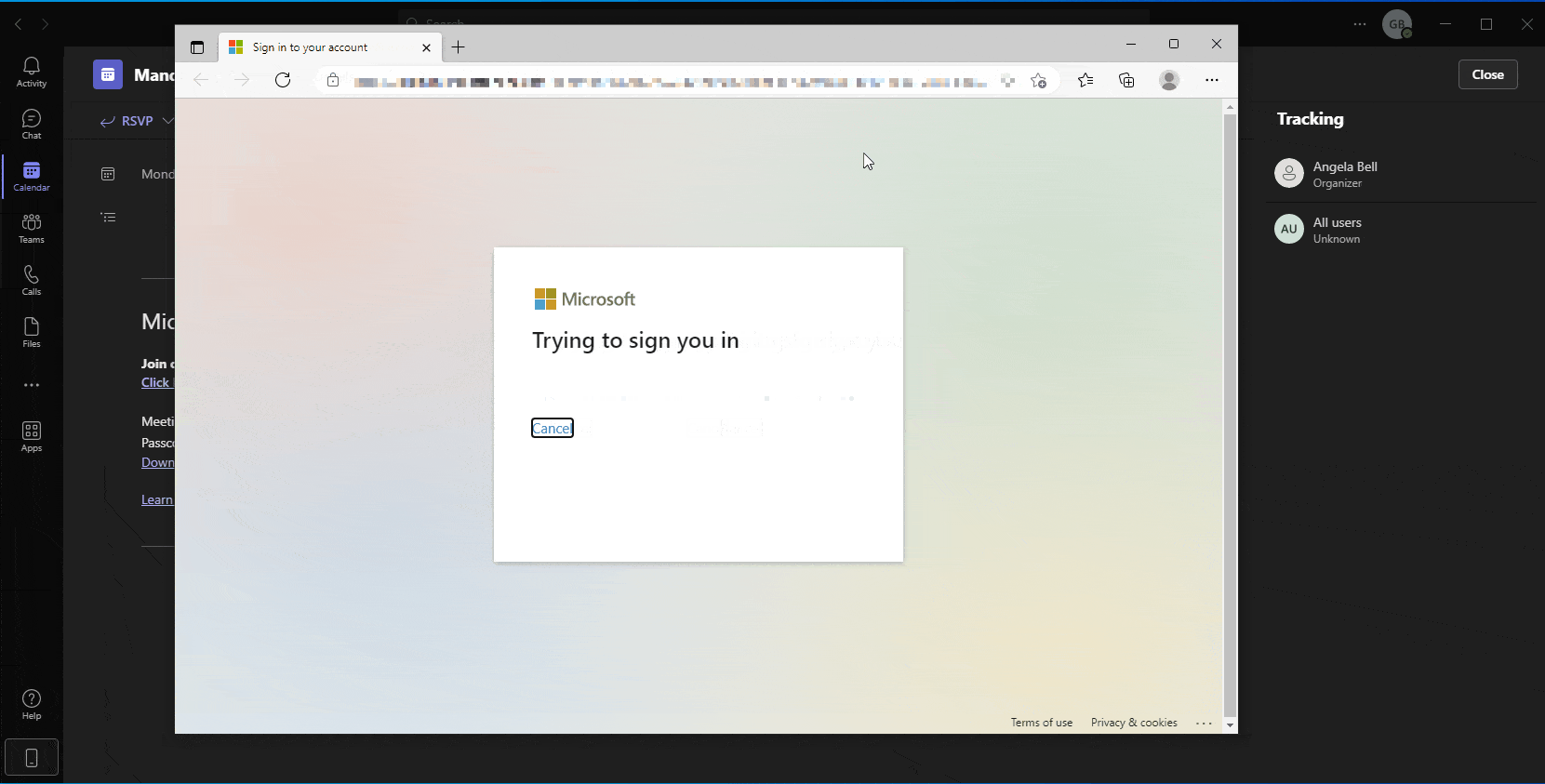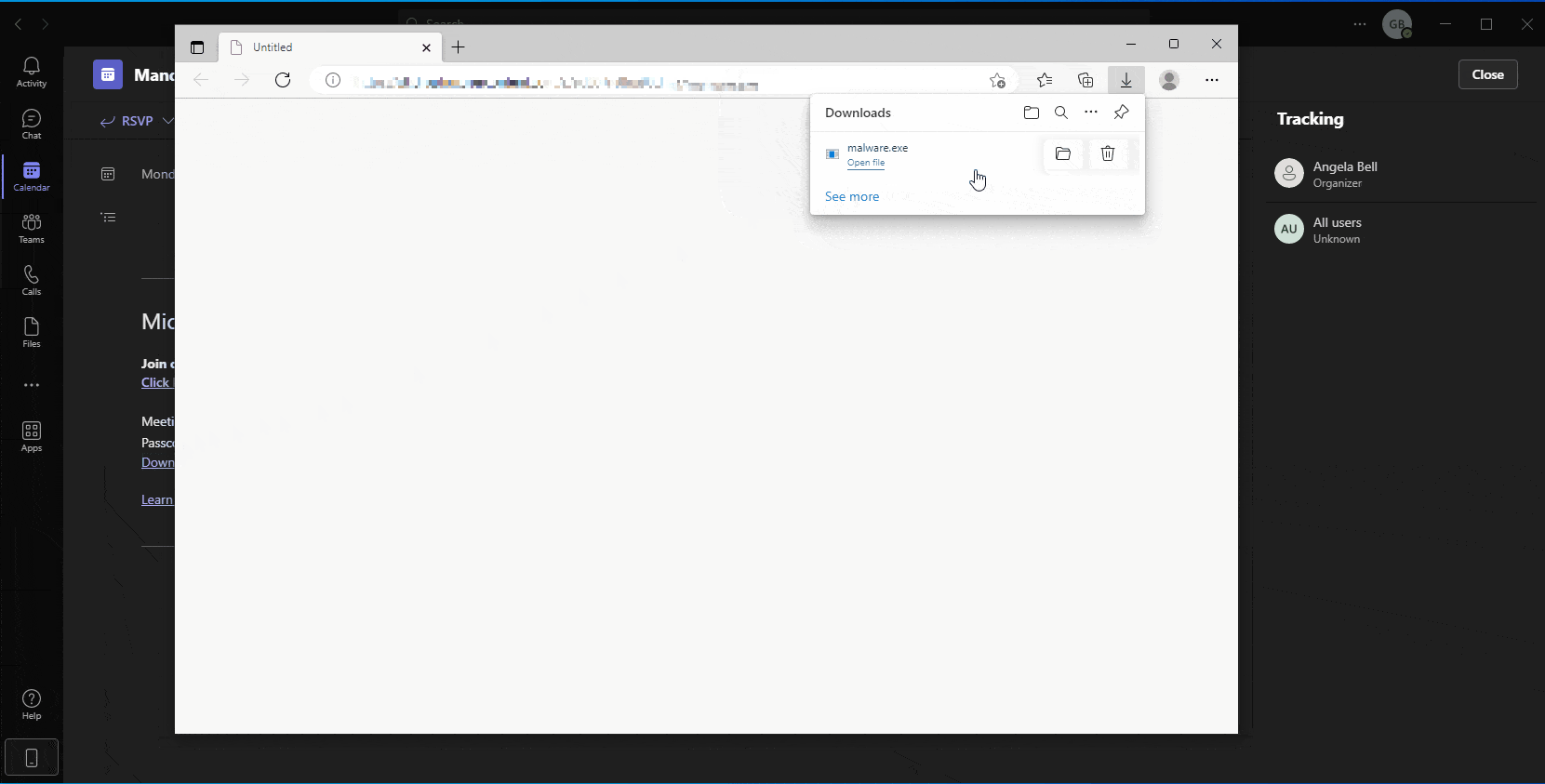
Figure 9 – Simulation showing creation of a meeting invite containing hidden malicious URLs that refer to malicious web pages
Weaponizing Hyperlinks in Messages
A different approach that attackers can utilize, given access to a user’s Teams token, is using Teams’ API or user-interface to weaponize existing links in sent messages. This could be done by simply replacing benign links with links pointing to nefarious websites or malicious resources. In this scenario, the presented hyperlink would not be changed, even though the URL behind it was modified (Figure 10).
Given that Teams API allows for the rapid and automatic enumeration and editing of links included in private or group chat messages, a simple script run by attackers could weaponize countless URLs within seconds. Subsequently, a sophisticated threat actor might utilize social engineering techniques and send new messages, encouraging unsuspecting users to click (or “re-visit”) the edited, and now weaponized, link.
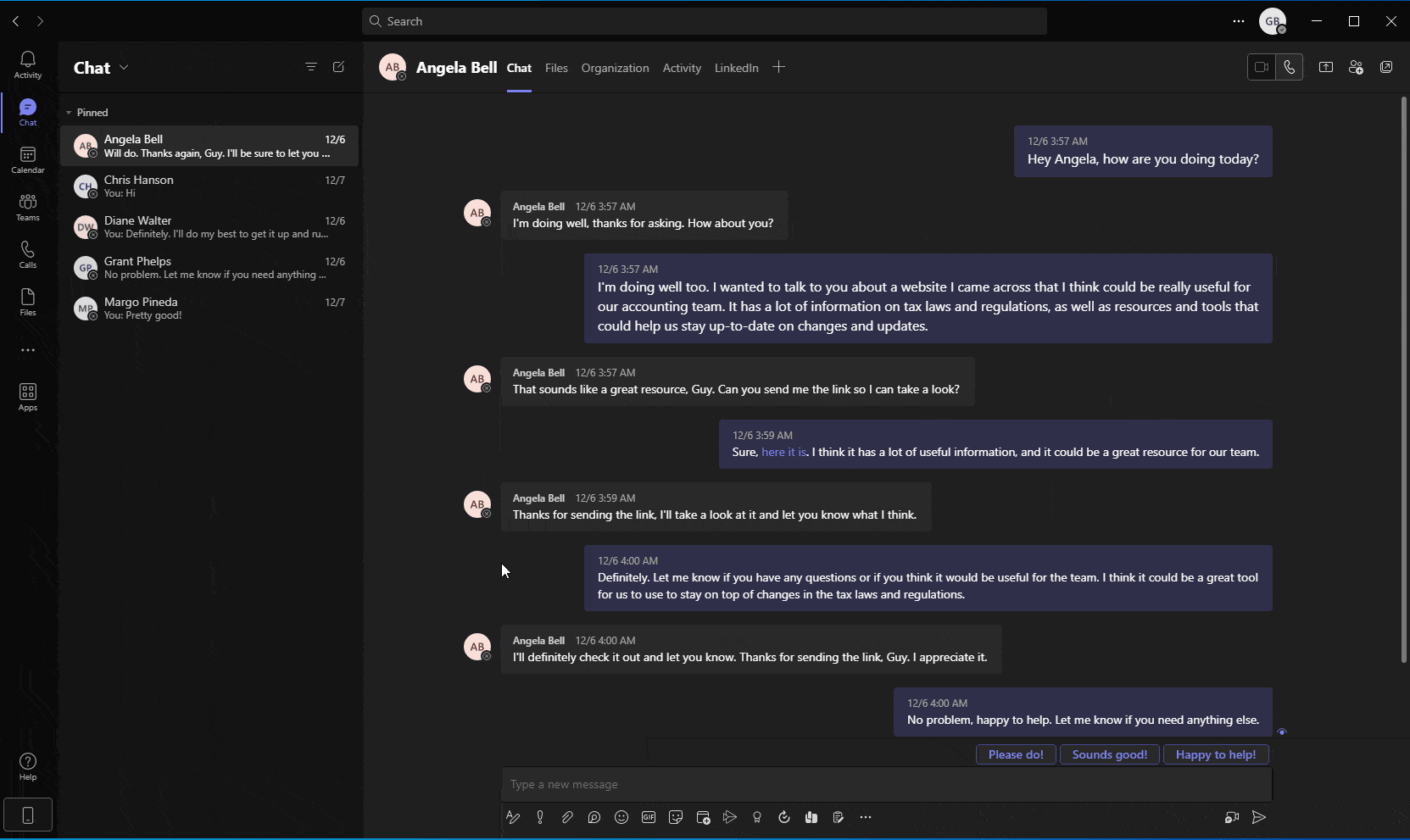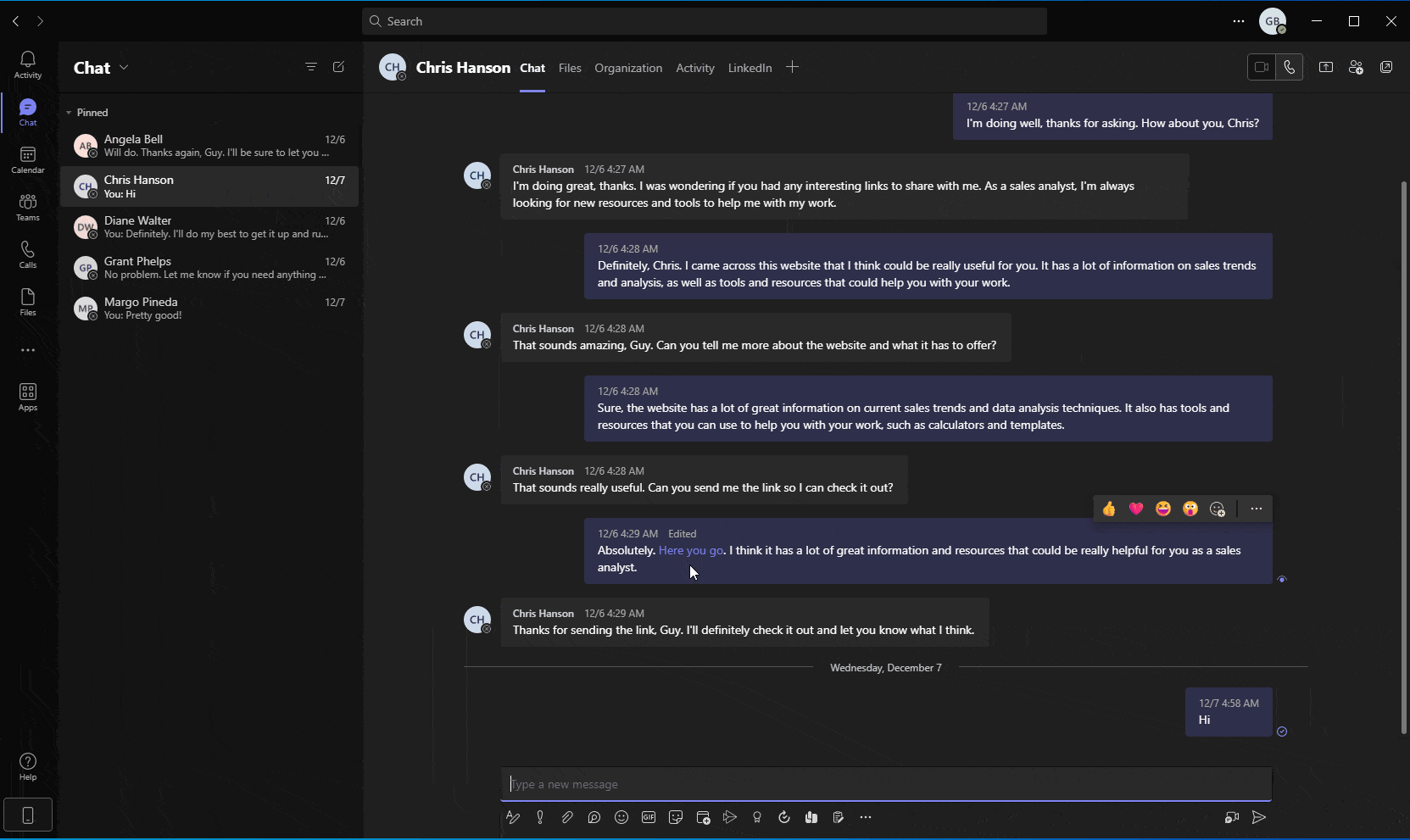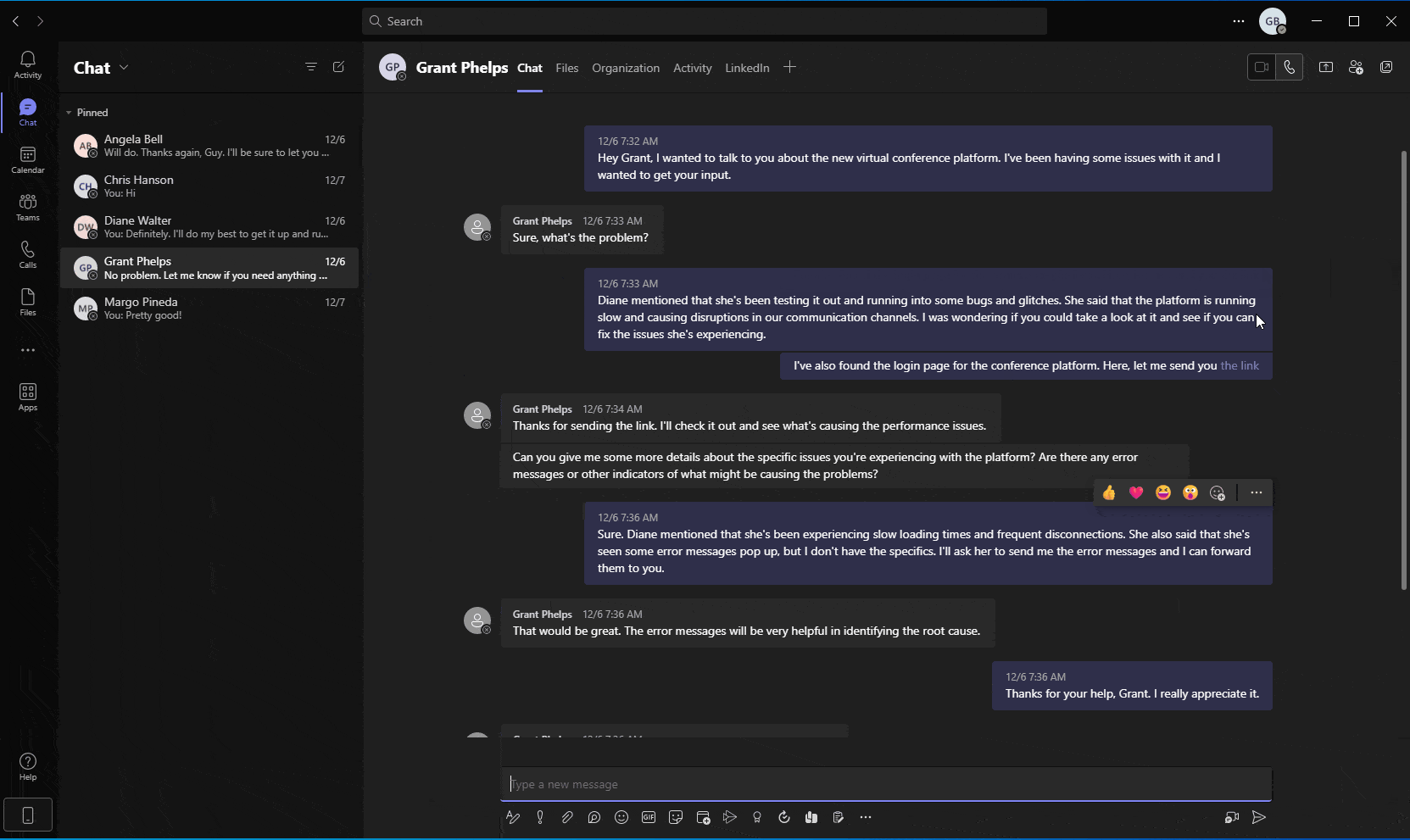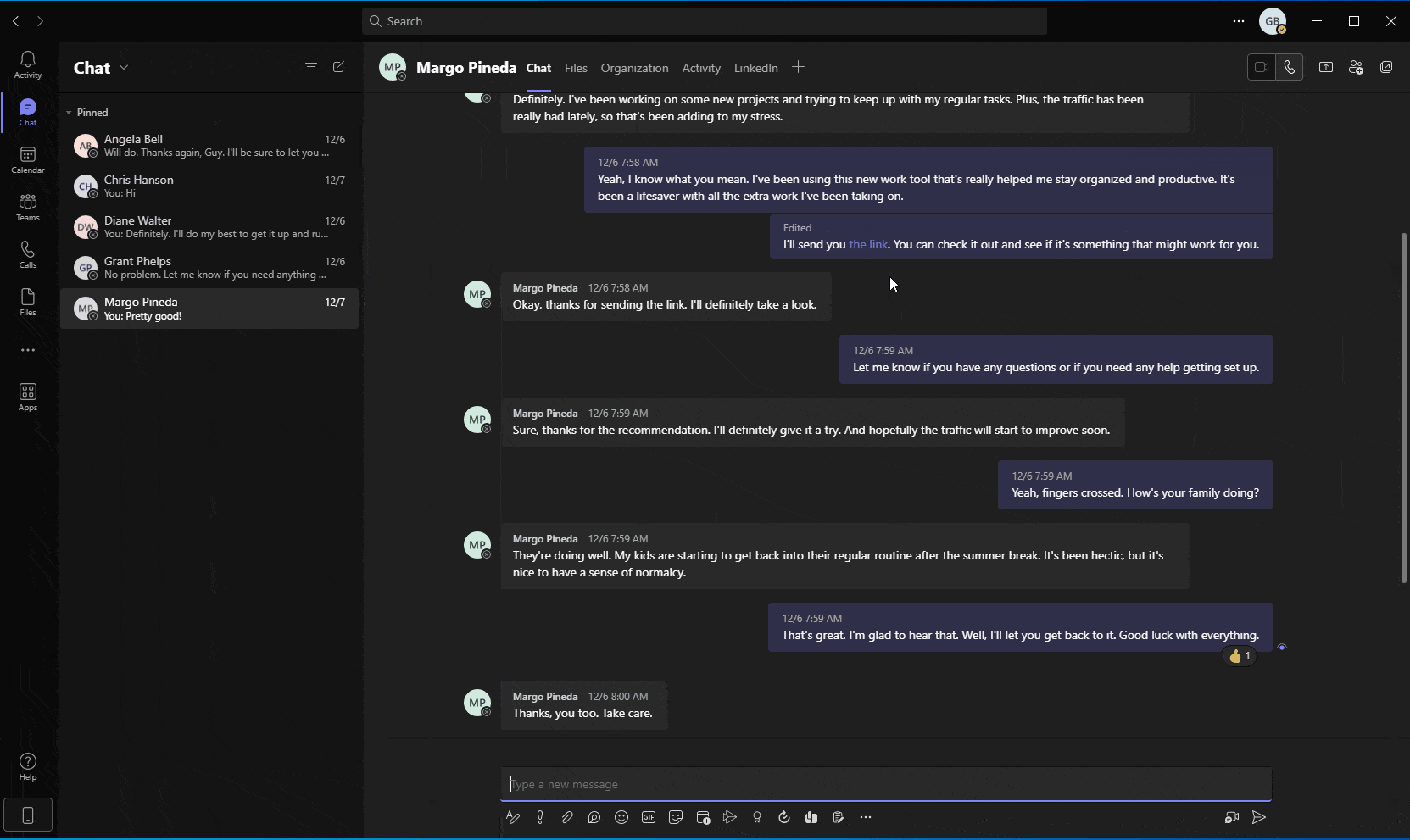
Figure 10 - Simulation showing automatic enumeration and manipulation of existing links within messages, using Teams API
Potential Impact
It is important to note that the aforementioned abuse methods require pre-existing access to a compromised user account or Teams token. Nevertheless, approximately 60% of Microsoft 365 tenants suffered at least one successful account takeover incident in 2022. Consequently, the potential proliferation of these methods would provide threat actors with effective possibilities for post-compromise lateral movement.
Our analysis of past attacks and ongoing trends within the dynamic cloud threat landscape indicates that attackers progressively pivot to more advanced attack vectors. The adoption of new attack techniques and tools, when combined with apparent security flaws, including dangerous functionalities in 1st-party apps, exposes organizations to a variety of critical risks.
Recommendations to Protect Your Organization
Following are ways to help your organization defend against Microsoft Teams-based phishing and malware risks:
- Security awareness: Educate users to be aware of these risks when using Microsoft Teams.
- Cloud security: Identify attackers accessing Teams within your cloud environment. This requires accurate and timely detection of the initial account compromise, and the visibility into the impacted sign-in application.
- Web security: Isolate potentially malicious sessions initiated by links embedded in Teams messages.
- Review Microsoft Teams usage: If you’re facing targeting attempts on a regular basis, consider limiting usage of Microsoft Teams in your cloud environment.
- Restrict access: Make sure your Teams service is internal only if possible and not exposed to communication with other organizations.
Threat actors constantly seek new ways to steal users’ credentials and acquire access to users’ accounts. As this blog illustrates, Microsoft Teams could be leveraged as a platform for various forms of cloud attacks since it is a legitimate and popular cloud application.
Contact Proofpoint to learn more about how we can help your organization protect cloud apps and secure cloud environments.
In response to Proofpoint’s disclosure of these findings, Microsoft has offered the following guidance: “Microsoft encourages users to observe security best practices in Microsoft Teams and to adopt industry-standard best practices for security and data protection including embracing the Zero Trust Security model and adopting robust strategies to manage security updates, antivirus updates, and authentication. More information on Zero Trust Security is available at https://aka.ms/zerotrust.”











