Last week, we explored messages using voter registration themes to entice users to share various pieces of personal information, such as their Social Security Number (SSN), Tax ID, and driver’s license details. We’ve identified additional efforts from the same actor, attempting to collect banking credentials and account numbers, along with the recipient’s “Vehicle licence Number [sic],” possibly a license plate or vehicle identification number (VIN) value.
Hundreds of messages with links to the credential phishing landing page were sent to recipients across multiple organizations, though there is no clear targeting of any specific industry.
Lures
The lures associated with this credential phishing site are similar to others sent by this actor, though they no longer mention any specific U.S. state.
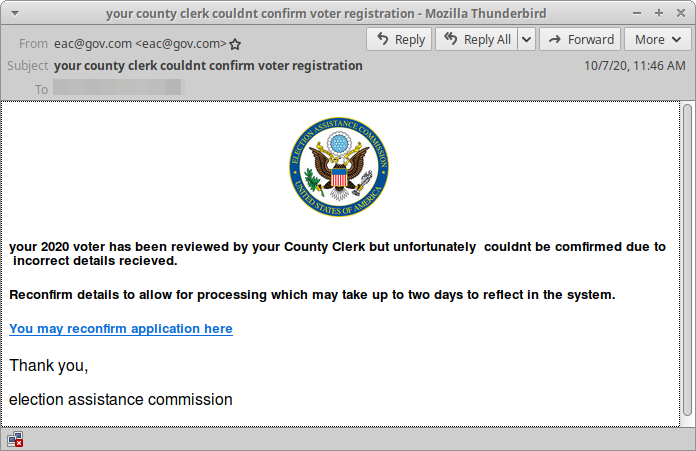
Figure 1: Email lure impersonating the Election Assistance Commission
Upon clicking the “You may reconfirm application here” link, the user is taken to a landing page that requests a variety of information, including name, contact information, and bank and email credentials.
Landing page
The UI of this information and credential phishing landing page is reminiscent of the previous pages we’ve observed from this actor. This supports our theory that they are making small changes to rebrand or soliciting slightly different information with each iteration of their landing pages. With this iteration, the theme and branding appear to shift throughout each page of the form.
The landing page initially requests the same information as in previous iterations: name, address, contact information, as well as SSN, Tax ID, and driver’s license number, issue date, and expiration date. It also has the same branding–the Election Assistance Commission (EAC) logo–as observed previously.
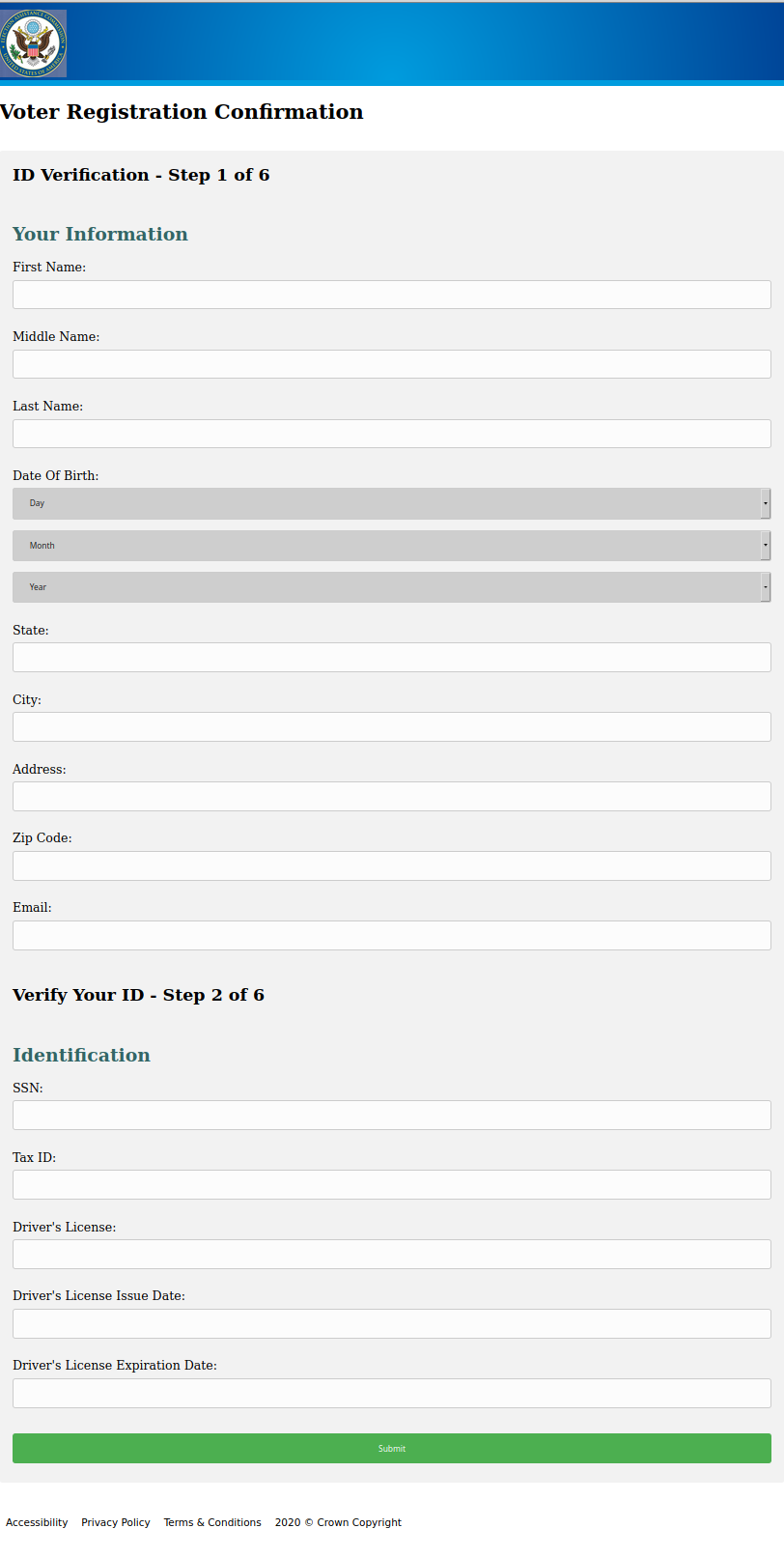
Figure 2: Initial information phishing landing page, collecting the same information previously observed
The second page of the form shifts to a stimulus theme, possibly COVID-19-related, suggesting that the user should fill in their bank name, account number, and routing number to claim their stimulus. The branding in the upper left corner of the page shifts from the EAC logo to the U.S. government’s official web logo.
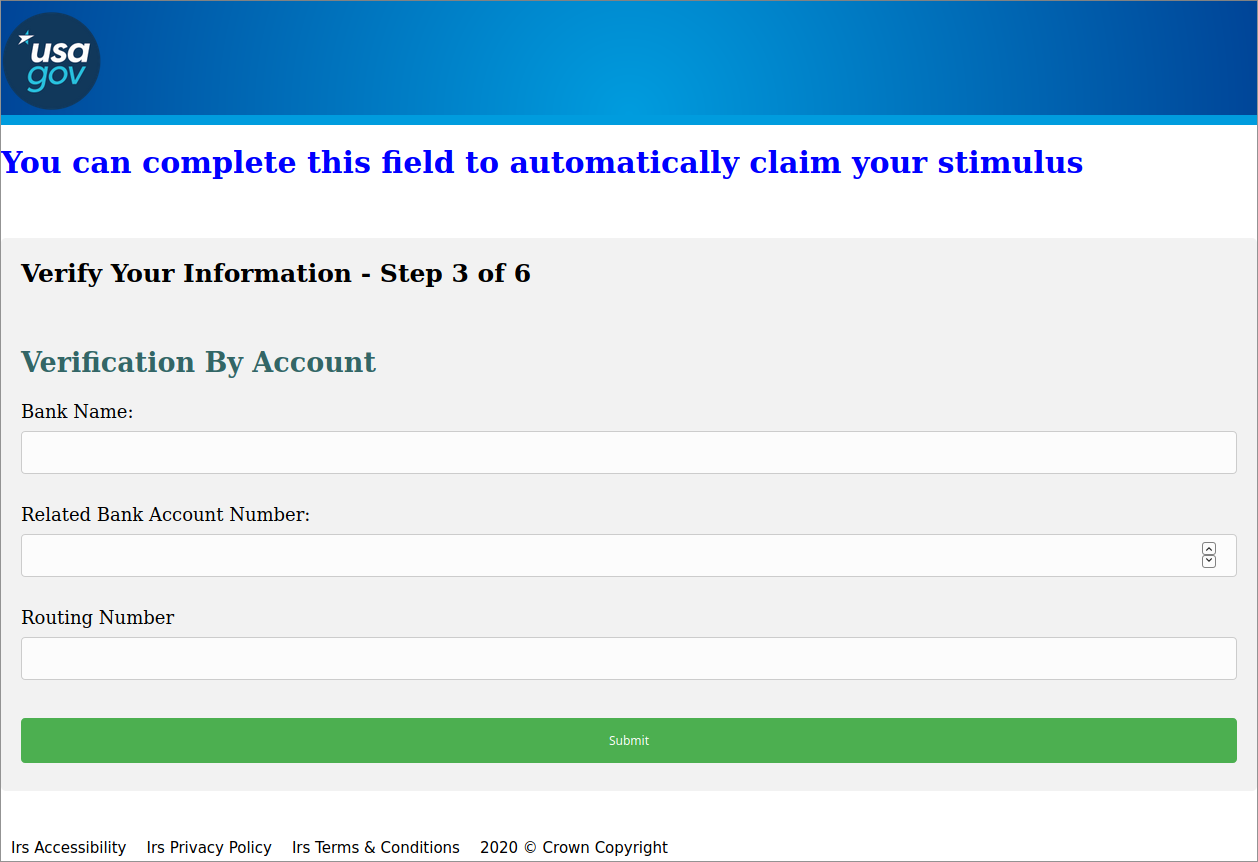
Figure 3: Second page of the form collecting bank account information
The third page requests “Bank username or ID” and “Password.” still using the “claim your stimulus” messaging.
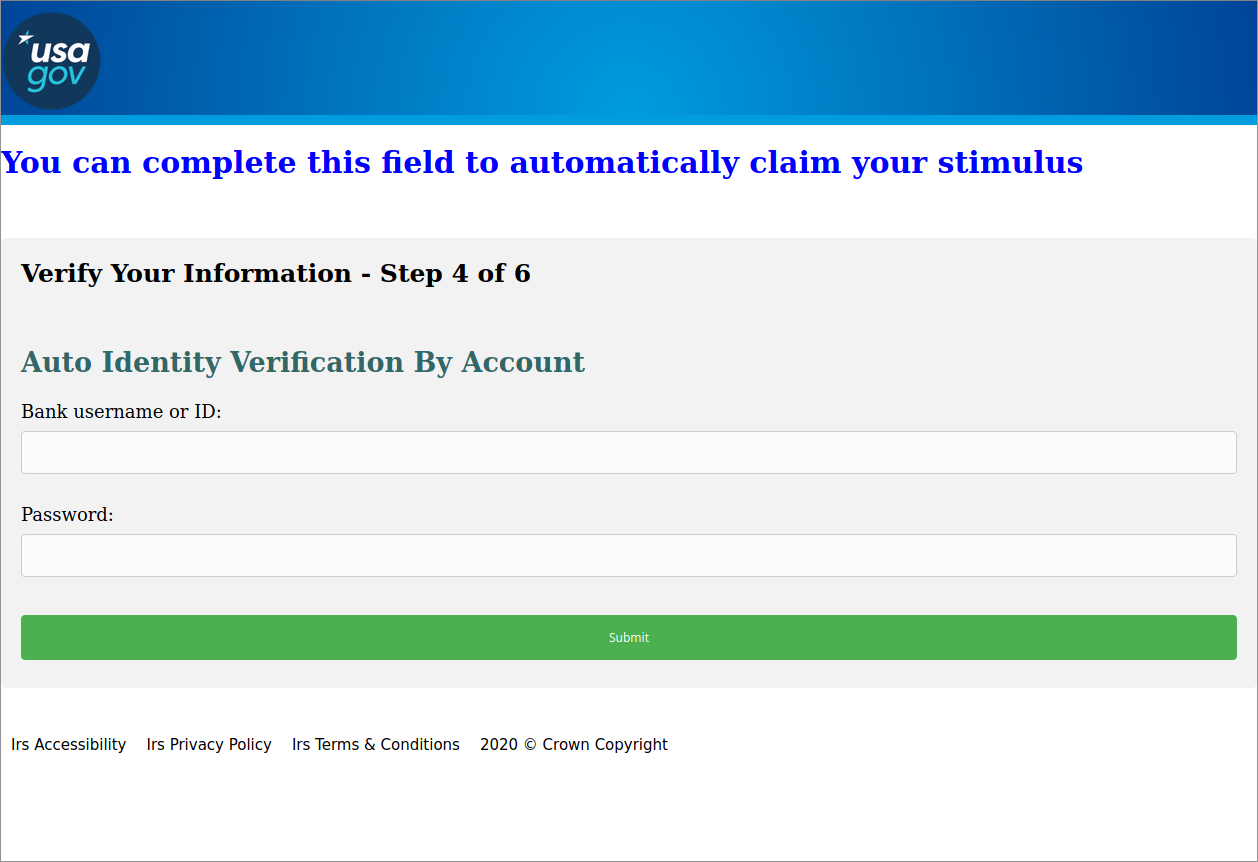
Figure 4: Third page of the form, now collecting bank account credentials
The following page is nearly identical to the previous page, aside from changing “Bank username or ID” to “Email” in an attempt to collect email credentials.
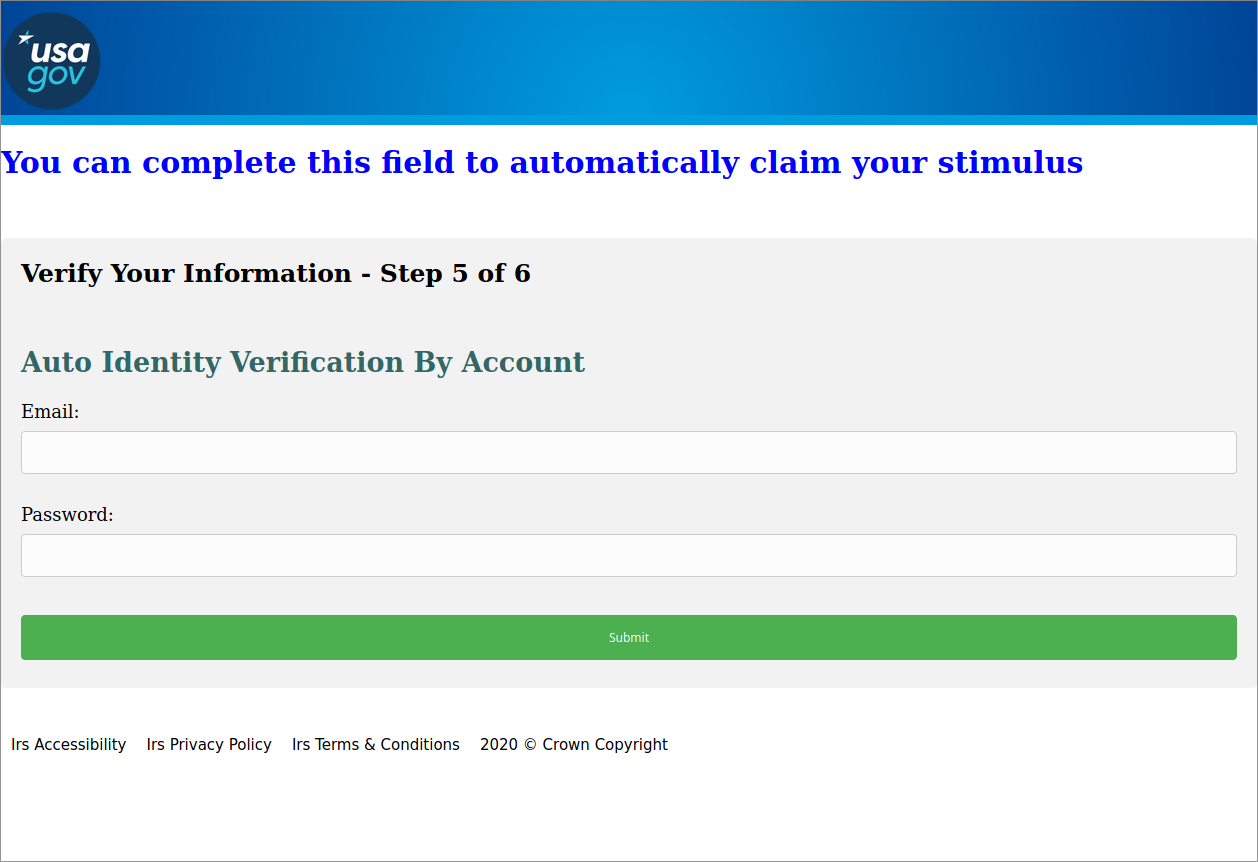
Figure 5: Fourth page of the form collecting email credentials
Finally, the page title changes to “Voter Registration,” though the user is asked for the “Vehicle licence Number” [sic] of their automobile.
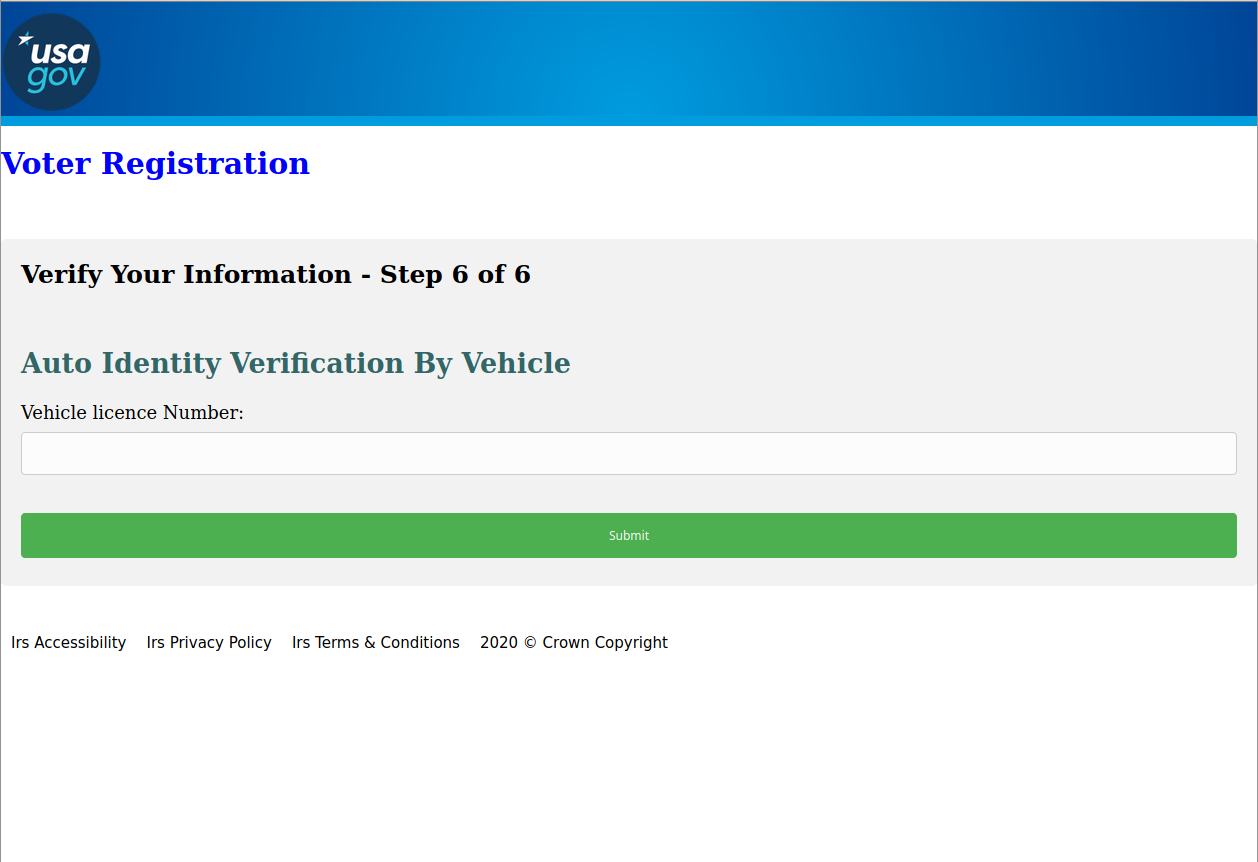
Figure 6: Fifth page of the form, collecting vehicle information
Upon submission of the fifth and final page of the form, the user is sent to the official voter information lookup page for a western US state.
Conclusion
Threat actors often convince users to give up their credentials, banking details, and other sensitive information via sites like the one detailed above. This phishing site is particularly interesting because it cycles through several themes within the same form––verification of voter information and claiming a “stimulus”––and collects a variety of information that isn’t always congruent with those themes. The driver’s license and vehicle license number are out of place on voter registration or stimulus claim pages. Further, the branding at the top of the site isn’t consistent, switching from the EAC logo to the U.S. government’s web logo on the second page of the form.
The information collected in this form is enough to assume someone’s identity, take over their bank accounts, and commandeer other assets connected to the email address they provide. Actors are agile and opportunistic, and this site is an excellent example of how quickly they adjust, even if they don’t always get the details right.











