We’re excited to join the new strategic collaboration together with Crowdstrike, Netskope and Okta, that will empower organizations to secure today’s dynamic and remote working environments at scale. These collaborative solutions, ranging from email security, cloud security, security awareness training and Zero Trust Network Access, will be instrumental in helping security teams navigate risks and secure their employees no matter where they are.
Due to the sudden shift to a remote workforce, many organizations are investing heavily in optimizing remote collaboration and corporate access, customer service to support different buying behaviors and cloud security. Digital strategies must be architected and deployed at speed—without compromising business continuity.
However, this rapid transition has also forced security and IT teams to find more robust security solutions quickly—with fewer resources and without the practical guidance they need to execute successfully.
Our new collaboration is designed to help organizations overcome the many obstacles they face in ensuring comprehensive protection across their remote workforces.
Challenges in Securing a Remote Workforce
There are many challenges to securing a remote workforce. Below, we explore three: increased attack surface, lack of training and compliance.
Increased Attack Surface
The growing sophistication of cyber threats and the fact that working remotely increases attack surfaces means that legacy solutions designed for an office-based corporate environment are no longer effective. Your people are still the target of attackers, and securing a remote workforce requires a strong layered defense approach and a modern Zero Trust security architecture to help keep organizations’ users, endpoints, data and networks safe from modern attacks. Ensuring users have only access to what they need to do their job regardless of their device, preventing as many threats as possible from impacting the endpoint and being able to remediate threats as quickly as possible provides resiliency and flexibility without compromising productivity.
Lack of Training
Given the speed of change required by shelter-in-place directives, companies have been forced to allow workers to use their personal devices in lieu of company-provided assets, and also ensure they could access corporate assets, data and hundreds of apps from anywhere in the world. However, many organizations are struggling to provide the same level of security and access to their newly remote workforce, along with the same seamless experience their employees are used to—and it is becoming increasingly clear that many do not have adequate awareness of the cybersecurity threats facing a remote workforce.
Compliance Challenges
While the need for remote access increases, compliance requirements in regulated industries still must be met. The number of collaboration channels and the amount of cloud data dispersed within and across SaaS applications have increased exponentially, leaving sensitive data unprotected and exposed to cyberattacks.
A Powerful Collaboration That Simplifies Zero Trust Security
Together with these security leaders, we are fundamentally changing the way organizations approach Zero Trust security architecture, bringing a comprehensive, best-of-breed security stack to your organization enabling your team to secure every remote workforce—regardless of app, data, endpoint or location. Our product integrations help keep your distributed workforce productive, collaborative and in compliance by hardening your defenses against today’s sophisticated attacks. Here’s how.
Crowdstrike, Netskope, Okta and Proofpoint make remote work as simple and secure as on-premises work.
- CrowdStrike protects all endpoints that access the enterprise, providing advanced threat hunting, next-generation antivirus protection, and tools for proactive incident response.
- Netskope provides web, cloud and data-centric security to protect enterprise assets anywhere, and delivers contextual understanding that helps you secure proprietary information everywhere.
- Okta establishes Zero Trust that secures frictionless access for remote and on-premises teams, enabled by an intuitive single sign-on backed by adaptive multifactor authentication.
- Proofpoint enables people-centric security by rapidly providing secure remote access to managed and unmanaged devices with Zero Trust Network Access, robust cloud security, cloud account compromise protection, educating employees on risks to the corporate environment, and in-depth visibility into threats targeting organizations.
“Better Together” Integrated Solution Benefits
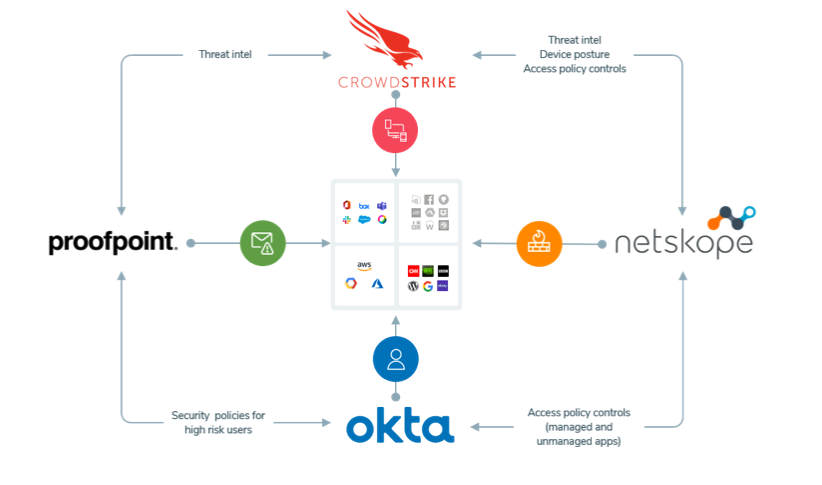
This integrated collaboration provides:
Safe access to applications and data, from anywhere, on any device
Organizations can move beyond legacy VPNs for remote network access with this modern, secure application-specific solution. Replacing legacy VPN solutions with Zero Trust network access solutions is an important first step to enable secure access for remote users. In addition, organizations need modern identity and access management capabilities along with strong and embedded endpoint security to secure applications and network resources. You’ll reduce the attack surface by adhering to Zero Trust access for all users.
Layers of data protection with enhanced cloud and web security
You’ll gain a comprehensive understanding of where data is within your cloud and web environment, regardless of device, network or location. Extra layers of protection when users browse the web or use cloud apps provides visibility into potentially risky behaviors (which may increase now that corporate resources are more easily accessible and more of your employees are working remotely). With strong data loss prevention and protection solutions, combined with identity and device controls, this collaboration helps organizations defend against cyberthreats and meet compliance requirements.
Strong and integrated endpoint security
This solution allows you to enhance security for all endpoints and integrate threat signals to quickly detect and respond. It combines strong endpoint security with identity and data security from to protect against known and unknown malware, including malware-free attacks on corporate and personal devices.
Streamlined remediation capabilities
You can exchange threat forensics between cloud and endpoints to enhance your organization’s security posture. Get streamlined shared intelligence across tools, automates response workflows and takes a proactive approach to defense in depth.
Make the end user an asset to your security team.
Educate end users on modern threats and the best ways to respond, while ensuring their access to IT tools and apps are uninterrupted. Turn your users into a strong last line of defense—regardless of where they work—with security awareness training.
Learn More
The integrated solution provides a powerful, proactive approach to enterprise defense, ensuring that you seamlessly share intelligence, exchange forensic data, automate threat response and continually evolve to future-proof your organization’s overall security posture.
Learn more about the joint collaborative solution by clicking here. And learn more about Proofpoint’s specific remote working and business continuity solutions here.











