Last Friday, January 22, our worldwide threat intelligence system detected the largest sustained Dridex campaign on record—66 percent greater than the previous high. Attackers leveraged tens of thousands of different IP addresses with an array of auto-varied subjects, senders and multiple attachments. This banking malware campaign accounted for roughly 10 percent of all inbound business email traffic we monitor (see image below).
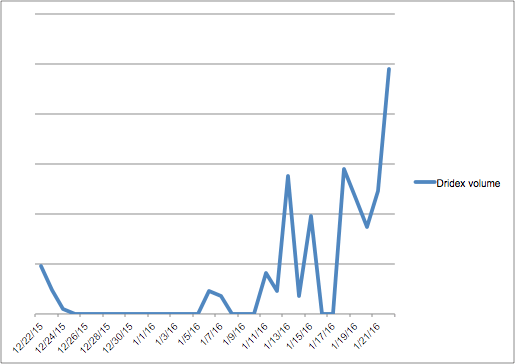
Designed to steal banking credentials, Dridex attackers hide malicious macros in e-mail attachments, specifically Word documents, to access systems. Our correlated threat intelligence systems indicate that Dridex continues to pass through legacy reputation-based and signature-based anti-spam and anti-virus defense systems. The Dridex message variation, volume and velocity contributed to the campaign’s ability to outmaneuver legacy defense systems.
Proofpoint Targeted Attack Protection customers continue to be protected from Dridex. We have the proven ability to stop more than 99 percent of attachment-based email attacks including banking Trojans like Dridex, Dyre and Shifu, ransomware like Cryptowall, and more highly targeted attack campaigns.
Last week’s surge is just the tip of the story; Dridex is expanding to other vectors. For more information, please visit the Proofpoint Threat Insight Blog.











