Since its inception, email has been a favorite target for cyber criminals hoping to steal sensitive data, user credentials, and company funds. In response, organizations have deployed a wide range of email security tools like Proofpoint's Email Fraud Defense.
But despite increased investment in defense, email fraud is still on the rise. Last quarter, the number of email fraud attacks rose 85% year-over-year. One of the most pervasive and effective tactics? Email fraud, also known as Business Email Compromise (BEC).
What Is Email Fraud?
Email fraud, or Business Email Compromise (BEC), refers to highly-targeted, low volume email attacks that impersonate corporate identities to solicit fraudulent wire transfers, steal company data, access customer credentials and capture other confidential information.
What Does an Email Fraud Attack Look Like?
There are several ways to launch email fraud or Business Email Compromise (BEC) attacks. Here are three top techniques attackers use:
1) Spoofing Email Fields
Unfortunately, it’s very easy to spoof visible email fields. And criminals leverage this vulnerability to:
- Change the reply-to email address in a way that makes it look like the email is coming from within the organization
- Spoof the display name (which is especially effective on mobile devices that hide the reply-to email address)
- Use a “lookalike domain”, a domain that looks like the company’s but is slightly different (such as using a numeral zero in place of the letter ‘o’)
- Pretend to be a legitimate business partner or supplier
2) Targeting a range of employees
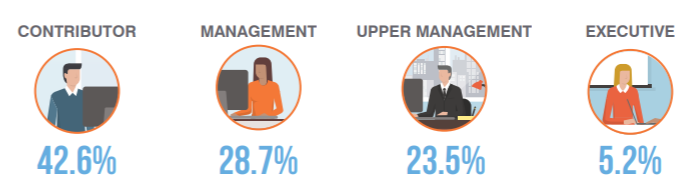
When BEC scams first appeared, cyber criminals usually focused on targeting the CEO/CFO relationship. Now they target a range of corporate employees. In fact, individual contributors and lower-level management account for about 60% of highly-targeted attacks.
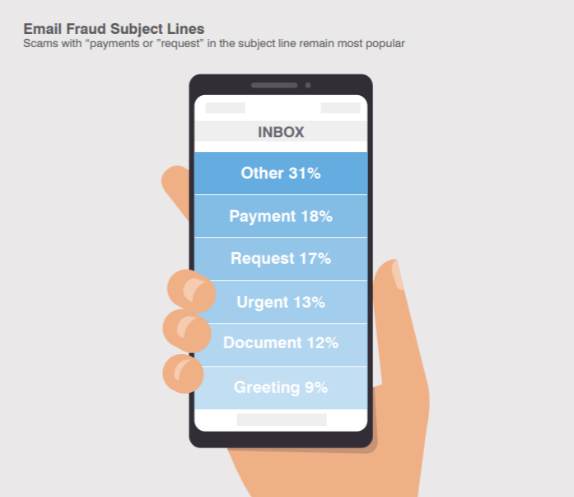
3) Getting Creative with Subject Lines
Using “clickbait” subject lines is another favorite email fraud tactic. Urgent language is the most popular—employees are more likely to pay attention to a fraudulent reply-to address if the subject line suggests that someone in authority needs something from them.
Our most recent quarterly analysis reveals that “Payment” and “Request” are the most popular subject lines among email fraud attacks.
How Can You Fight Email Fraud?
There are five key steps to securing your email channel from dangerous email fraud attacks.
1) Get visibility
To defend your organization effectively from email attacks, you must understand the threats you face. Robust threat intelligence that can detect the full scale of malicious emails is an important first step, but it’s not enough. Implement a solution that can correlate and analyze your threat data, revealing who is being targeted, who is attacking you and what information they are trying to steal.
2) Deploy core email control and content analysis
Maintaining control over what messages get into your environment is critical when it comes to email security. Your solution must offer granular classification that doesn’t just look for spam or malware but also identifies all distinct types of email (malicious or not) targeting your employees.
3) Authenticate your email
Email authentication, specifically DMARC (Domain-based Message Authentication Reporting and Conformance), ensures that legitimate email is properly authenticating against established SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) standards. It reveals who is sending email on your behalf and blocks any fraudulent activity from domains under your organization’s control.
4) Prevent data loss
There’s a lot we can do to stop threats from coming in. But you should also prevent sensitive data from leaving your gateway. An effective email security strategy prepares for any threats that make it through your defenses—and employees who inadvertently expose sensitive data.
5) Respond to threats in real time
No security solution can stop all attacks. Real-time threat response must be a pillar of your email security strategy. Failing to prepare for the worst case scenario can wreak havoc on your business and brand reputation when an attack circumvents your defense system.
Ready to start fighting email fraud? Understand your ecosystem. Request an email threat assessment from our cybersecurity experts today.











