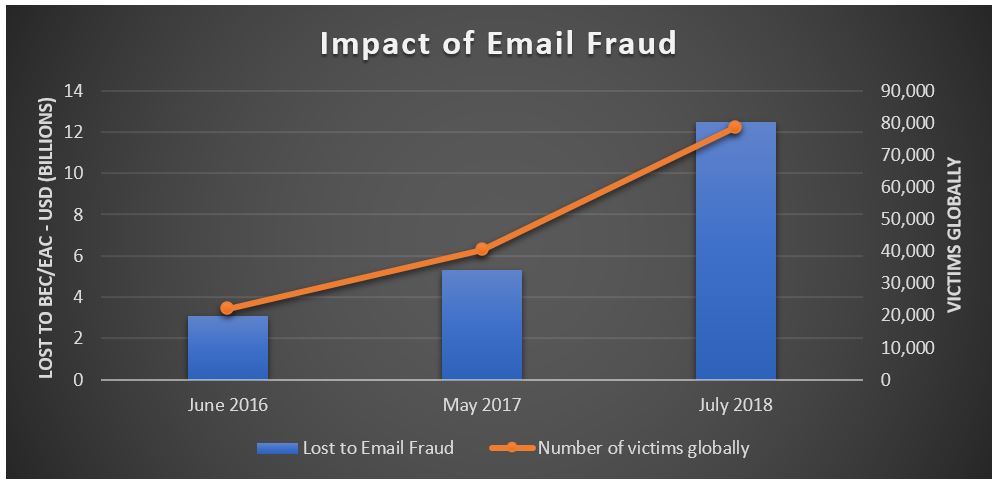
While malware attacks receive media attention because of their large scale, highly targeted email fraud has been quietly costing organizations around the globe billions of dollars every year. According to the Federal Bureau of Investigation (FBI)’s latest report, losses due to business email compromise (BEC) and email account compromise (EAC) scams have reached $12.5 Billion worldwide.
These new figures compound our recent research findings that email fraud attacks hit more than 90% of organizations in the first three months of this year and the total number rose 103% year-over-year. While these numbers are substantial, it’s worth noting that many cyberattack incidents of this nature are either underreported or unreported each year.
This most recent FBI report details a significant jump in financial loss from May 2017 when losses associated with business email compromise (BEC) alone had cost organizations globally $5.3B between October 2013 and December 2016. In May 2018, the FBI’s Internet Crime Report indicated more than $675M BEC losses occurred in 2017.
Email has remained a top attack vector for BEC/EAC attackers because it is a much more effective, easier path for criminals to navigate than hacking into a targeted organization’s infrastructure. Exploiting the email communication channel through highly personalized, social engineering messages allows them to easily impersonate a trusted employee or partner.
Increasingly, organizations are also experiencing EAC attacks where cybercriminals can impersonate their victims even more convincingly as they can log in with phished or otherwise stolen credentials and send email from a genuine, trusted account. In fact, we just recently released information detailing that malicious actors are increasingly compromising corporate email systems by using brute force attacks to steal Microsoft Office 365 login credentials of corporate users and then logging in as an imposter on the system. Through this method, attackers can often gain access to accounts even if the company has deployed single sign on or multi-factor authentication (MFA) as part of their security system.
Credential reuse, brute force attacks, and credential-stealing malware are all favored EAC cybercrime tactics. EAC attacks create a scenario where even the best security solution is going to struggle – a legitimate email from an internal source that doesn’t contain any malware is difficult to detect.
The FBI attributes these new loss figures to BEC actors targeting the real estate sector in order to steal money being used in the purchase of a property. Title companies, law firms, real estate agents as well as buyers and sellers have all been targeted. Given the large sums of money that are at risk when purchasing property, this can be a large win for an attacker if they are successful.
We are focused on solving this problem for our customers, and this isn’t a silver bullet approach, but a problem that must be attacked on many different facets:
- Identify and block fraudulent emails entering the organization that claim to be from an internal source
- Prevent email that uses the organization domain from being sent by unauthorized senders to external recipients such as partners and customers
- Examine all internal email to remove content that might be coming from compromised accounts such as spam and malware
- Analyze account access activity to be able to identify if an account compromise event is underway
- Review account access to identify any unexpected or suspicious behavior
For more information on how to stop email fraud, please review our Stopping Email Fraud guide: https://www.proofpoint.com/us/resources/white-papers/stopping-email-fraud











