Email fraud rose to new levels in 2017 and in the first quarter of 2018 and we continue to see an increase in both the size and scope of the problem. These socially engineered attacks, which target people rather than technology, are leveraging many different tactics to successfully lure money and other valuable information away from unsuspecting victims. According to the FBI, business email compromise (a common form of email fraud) cost organizations over $675 million in 2017, an 87.5% increase over the previous year.
To better understand this ever-evolving threat, Proofpoint analyzed the email fraud attacks we blocked that targeted thousands of organizations around the globe. Here are some of our findings for Q1 2018.
Email Fraud Volume Grew 103% Year-Over-Year
More than 90% of organizations were targeted in the first quarter of 2018. The total number of email fraud attacks rose 55% over the previous quarter and 103% year-over-year. And while these attacks are sent in low volumes, organizations were targeted with greater frequency than we have previously seen. The average number of malicious emails directed at a given company was 28. This is a 36% increase over the previous quarter and is up 28% year-over-year.
Organizations of all sizes, across all countries, and in all industry verticals are at risk. We found no statistical correlation between the size of the company and how frequently it was targeted by email fraud. While larger organizations may be richer targets, small companies may be more vulnerable.
The United States saw the largest total volume of email fraud attacks in Q1, but organizations in the United Kingdom were targeted most frequently – with an average of 36 malicious emails directed at a given company. The Netherlands saw the lowest number of email fraud – both in terms of total volume of attacks and in the average number of times an organization was targeted, being nine.
Nearly all industry verticals saw an increase in attacks over the previous quarter. The Entertainment/Media industry saw the largest quarter-over-quarter rise, at nearly 73%, and the real estate industry was targeted most often in Q1. This information stands to reason as fraudsters seek to insert themselves into high-value, time-sensitive transactions.
Socially Engineered for Success
The top three subject line categories used in email fraud attacks were “Request”, “Payment”, and “Urgent”. This is consistent with previous quarters and aligns with the fact that wire transfer scams are the most frequent form of email fraud. We have seen a spike in W2 scams during the first quarter in each of the past 3 years due to the U.S. tax deadline. These specific attacks rose 800% over the previous quarter.
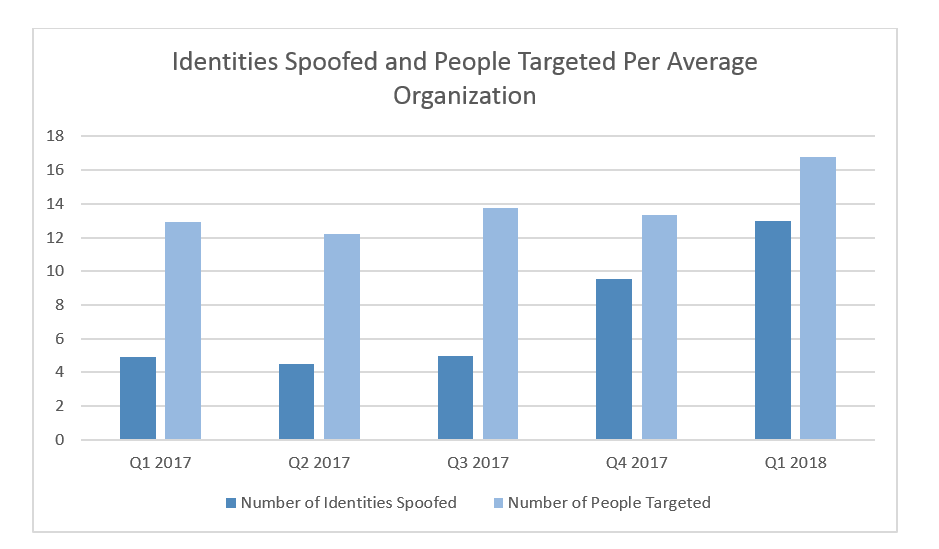
Criminals are becoming more sophisticated and are inserting themselves into more business processes. On average, about 13 identities were spoofed and nearly 17 people were targeted within a given organization. Email fraud has truly become a multi-dimensional problem as 41% of companies had more than 5 people’s identities spoofed and more than 5 people targeted.
Attackers Leverage Multiple Fraud Tactics to Evade Detection
Display name spoofing is the most common fraud tactic used and is often used in tandem with other tactics. In Q1, 98.42% of all impostor email attacks used this tactic. Webmail domains, such as gmail.com or aol.com, were the most common sending domains seen – making up 53% of these attacks. Display name spoofing attacks sent from webmail addresses accounted for 40% of all email fraud in Q1.
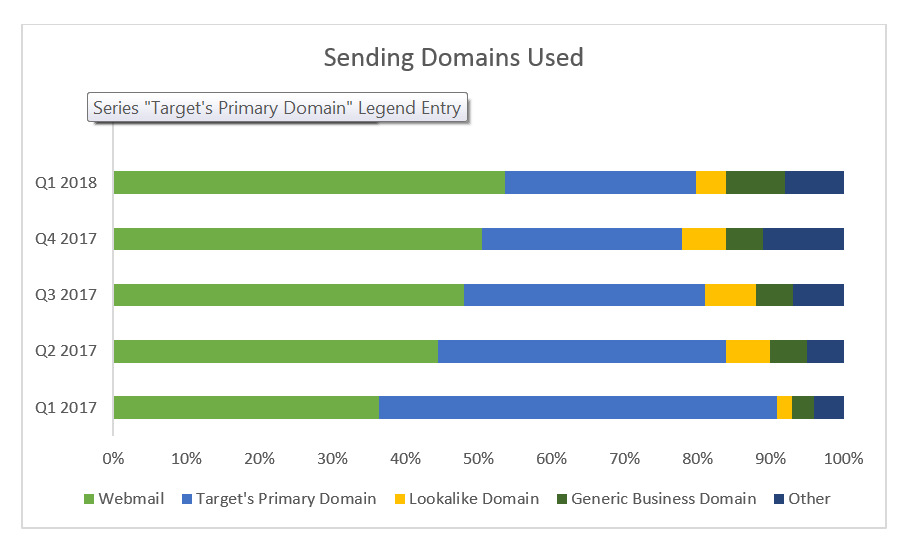
Domain spoofing, where an attacker hijacks an organization’s trusted domain, accounted for about 27% of all email fraud attacks, but 70% of the organizations that were targeted in Q1, were targeted by at least one domain spoofing attack.
Lookalike domains, or cousin domains, represented 4% of the domain types used in Q1. Of these attacks, the most common technique used was to swap individual characters (i.e. replacing a “5” for an “s” or a “0” for an “o”). Other leading techniques included adding or removing the leading/trailing characters (i.e. adding an “s” at the end of a domain) and inserting an additional character (i.e. using “rn” to replace “m”).
Recommendations for Solving Email Fraud
Email fraud continues to rise at unprecedented rates. Cybercriminals can leverage multiple tactics to try and evade detection, leaving your employees, customers, and business partners as the last line of defense. Organizations need to solve this problem with multiple layers of security that include:
- Dynamic classification. Analyze the content and context of the email and stop display name and lookalike domain spoofing at the email gateway.
- Email authentication. Validate the identities of email senders that use an organization’s trusted domains and instruct the gateway what to do with messages that fail authentication.
- Lookalike domain monitoring. Identify and flag potential risky domains outside of your control.
Proofpoint’s 360-degree email fraud protection gives you visibility and control to stop all email fraud attacks– regardless of the tactic used or the person being targeted. Learn more here.











