Email fraud is one of the most dangerous threats facing organizations today, accounting for 90% of all data breaches, according to Verizon, and costing companies $6 billion in business email compromise, according to the FBI.
The ease with which anyone can manipulate the “From” field of an email makes it a valuable tool for marketers and internal operations. But this convenience also represents email’s greatest vulnerability, making it the weapon of choice among cybercriminals.
Click here to see our data visualization.
Gaining visibility into who is sending email on your behalf and why is the first step in protecting your organization. But that exercise is much more difficult than it sounds.
Most organizations have hundreds if not thousands of servers around the world sending email on their behalf. Some of these servers are owned by their own organization. But much of it is sent from third parties, including companies like MailChimp, that send bulk email purporting to be from various brands.
The first challenge for organizations like yours is to categorize the myriad IPs sending email on your behalf into authorized and unauthorized senders. For larger companies, doing so can be difficult. One of Proofpoint’s customers, for example, has more than 157,000 sending IPs to categorize.
The second challenge is to identify malicious activity among all unauthorized senders without blocking legitimate email traffic and damaging your brand and business operations. Here too, looks can be deceiving. Some unauthorized senders may appear suspicious at first glance but in fact, send legitimate email. And other senders seem legitimate but are malicious.
For example, we regularly see cybercriminals hijack vulnerable infrastructure of “well-respected” companies to relay spoofed email attacks. The receiver should not assume that, just because the sending IPs were owned by “well-respected” companies, all email emanating from those IPs should be trusted.
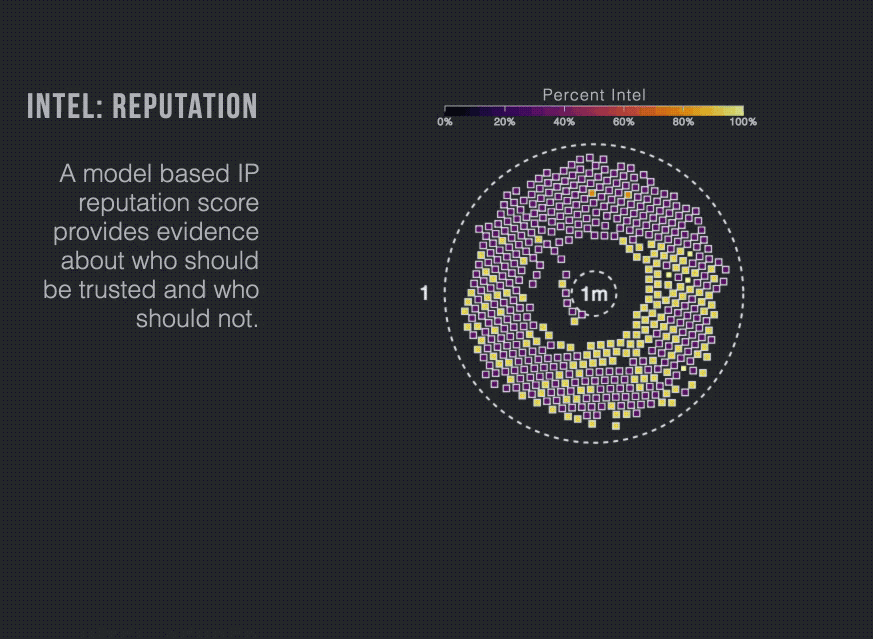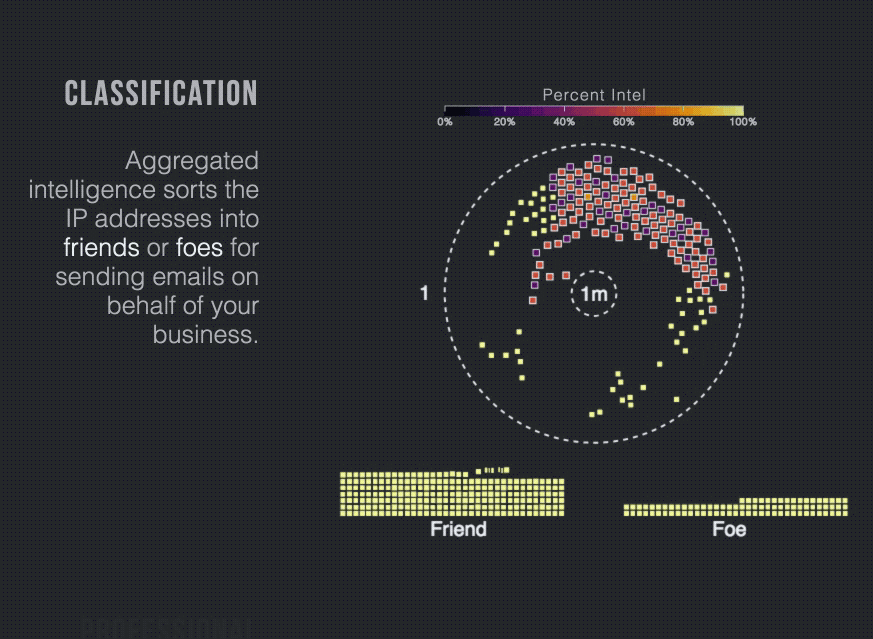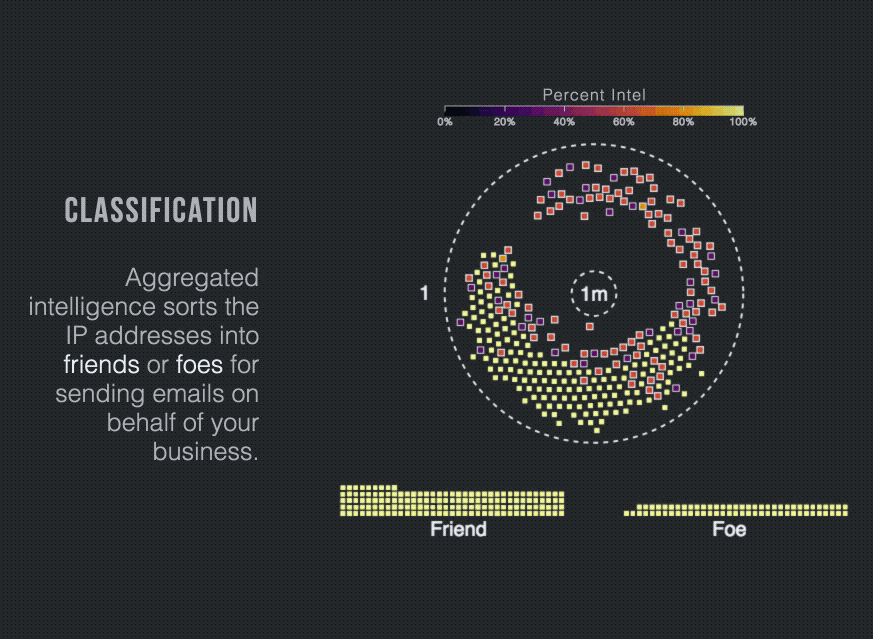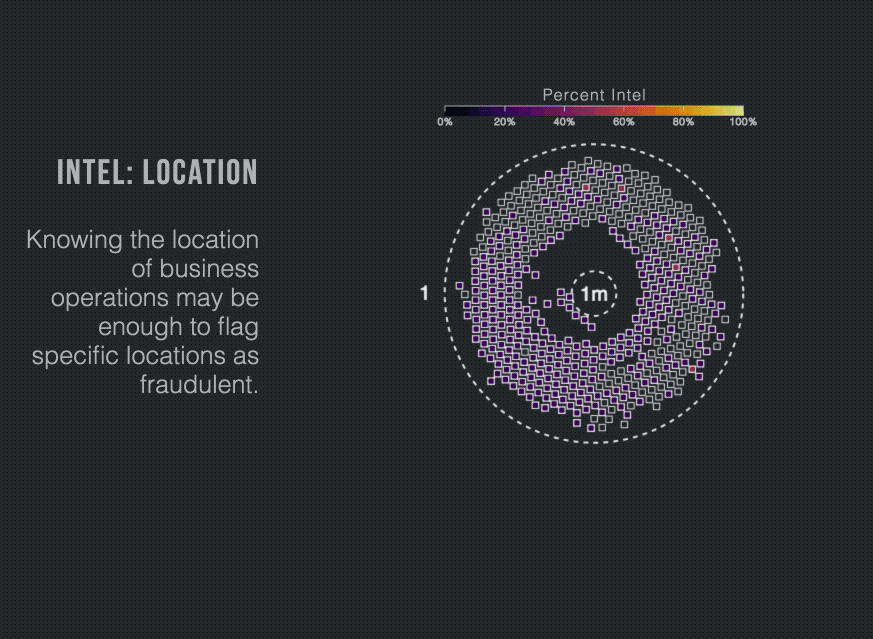
So how can you identify and block the bad senders from the noise of sending IPs? The first step is to leverage email intelligence to enrich your understanding of your sending ecosystem.
Proofpoint understands the importance of this kind of analysis, which is why we work hard to bring the greatest amount of email intelligence and present it to our customers in a way that they find truly valuable.
Check out our latest interactive data visualization, "Dark Orbits: Threat Visibility Explained", to understand our process for differentiating between authorized and unauthorized senders in a sea of sending IPs.