Overview
Proofpoint researchers have tracked attackers leveraging the coronavirus pandemic since January 29. This blog serves as an update of the overall threat landscape and includes selected examples to highlight what we are seeing.
Currently, attackers are using coronavirus themes for nearly all types of attacks, including (but not limited to) business email compromise (BEC), credential phishing, malware, and spam email campaigns.
The targeting of these attacks has ranged from extremely broad to narrowly focused and campaign volumes have fluctuated between small and large. Attribution includes both well-known and unknown threat actors. Some of the well-known threat actors include TA505 and TA542.
We’ve observed attacks around the world, most notably in Italy, the Czech Republic, Japan, United States, Canada, Australia, and Turkey. In addition to English, attackers have used Italian, Czech, Japanese, Spanish, and French languages within their messages.
While all industries have been targeted, we’ve seen specific targeting of healthcare, education, manufacturing, media, advertising, and hospitality organizations in certain campaigns.
Attackers are actively abusing the names and logos of many companies and organizations within these campaigns in an attempt to manipulate recipients. Of particular note is the spoofing and brand abuse of national and international health organizations around the world, including the World Health Organization (WHO), the United States Centers for Disease Control (CDC), and Canadian and Australian national health organizations.
Threat actors have launched coronavirus campaigns to spread remote access Trojans (RATs), keyloggers, information stealers, and bankers. We are also seeing credential phishing campaigns with this theme. For example, we observed attempts to harvest credentials for Facebook, DocuSign, Microsoft Outlook Web Access (OWA), Microsoft OneDrive, and universities around the world.
We expect attackers will continue to leverage coronavirus themes in their attacks for some time to come. Proofpoint researchers will continue to track closely and provide updates on our blog and through our Threat Insight Twitter handle.
Below are several notable examples of what we’ve seen.
BEC Attempt: “People tested positive downtown so I can’t go out right now”
Key Points: BEC attackers use the claim of positive coronavirus tests in their area to start email conversation.
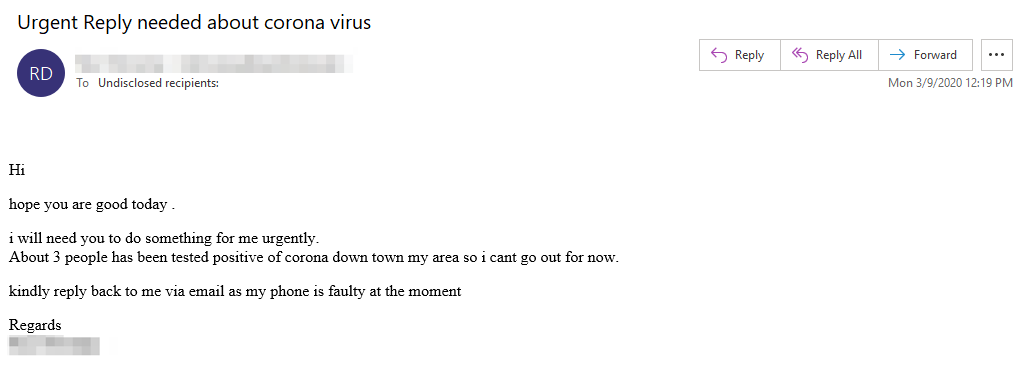
BEC Attempt Summary:
This BEC email attempts to capitalize on current events and the global shift towards quarantine to prevent further spreading of coronavirus. BEC actors often try to convey a sense of urgency or immediate need. In this attack, the urgency is present in the subject line used here: "Urgent Reply needed about corona virus"[SIC].
BEC attacks are often delivered in stages. The first email sent is typically innocuous, meaning that they do not contain the attacker's end goal. The attackers craft plausible scenarios in hopes the recipient will reply. Once they’re on the hook, the attacker will send their true ask. (I need you to buy gift cards, wire transfer funds, etc.)
These coronavirus-themed BEC attacks often come with spoofed display names, which are likely real people known to the recipient. In the body of this message, the actor attempts to eliminate the possibility of voice-verification, in hopes of ensuring a higher success rate, by saying their phone is "faulty at the moment."
Credential Phish: Microsoft Office
Key Points: Attackers use credible, customized, fake internal emails for credential phishing attacks targeting the healthcare industry.
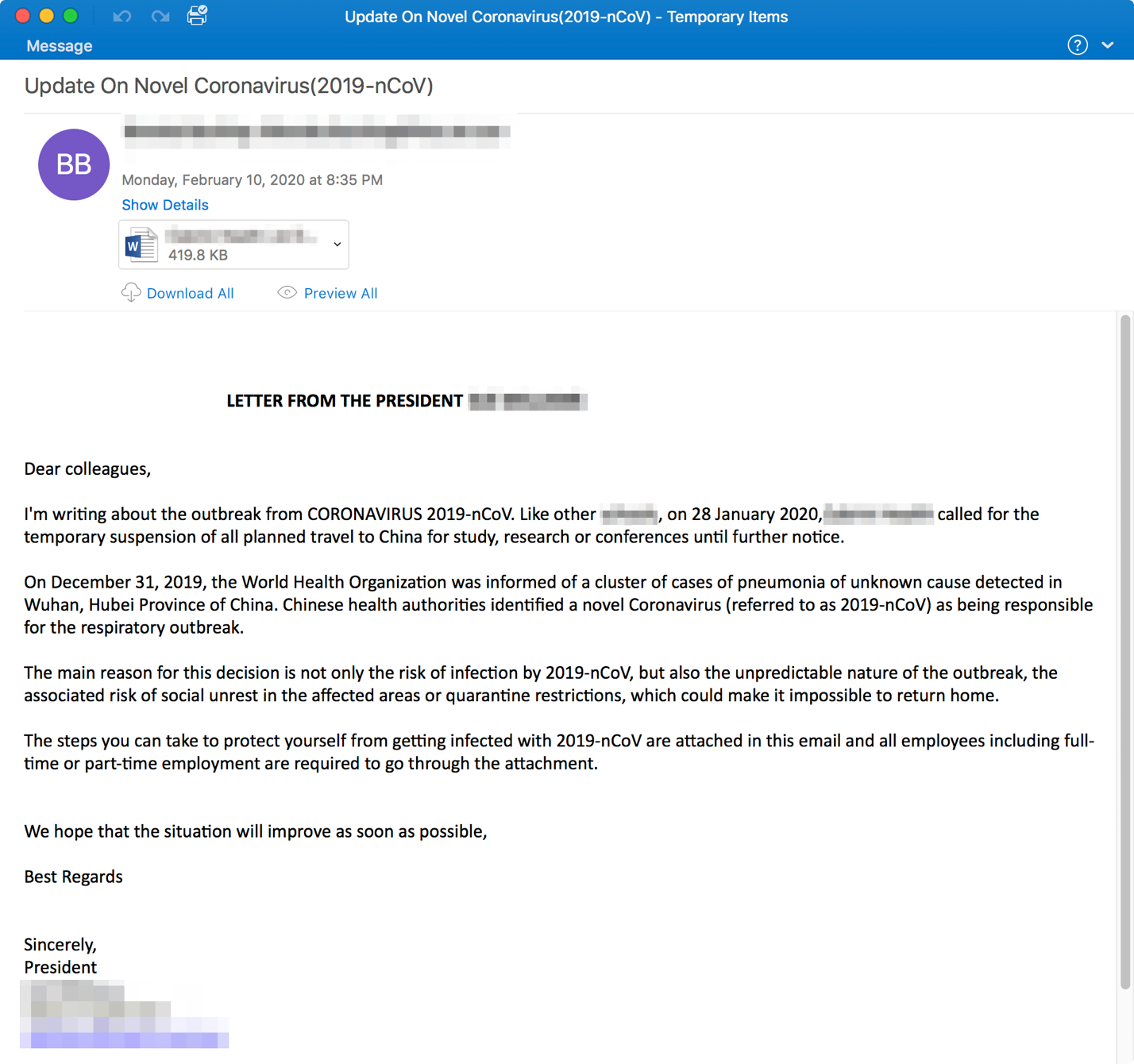
Microsoft Office Credential Phish Summary:
These specific Coronavirus cyber attacks targeted companies in the healthcare industry. Our researchers found that the emails were highly customized to each target to increase their credibility. They claimed to be from the targeted company's actual president and used the targeted company name and president’s name multiple times in the email.
The messages conveyed information about halting all travel to China and contained an attached Word document with a link inside of it. If a user clicked the link, they would be brought to a spoofed Microsoft Office branded credential phishing site that asks for email login and password.
Credential Phish: Outlook Web Access (OWA)
Key Points: Attackers use an employee survey about coronavirus to target Outlook Web Access credentials.
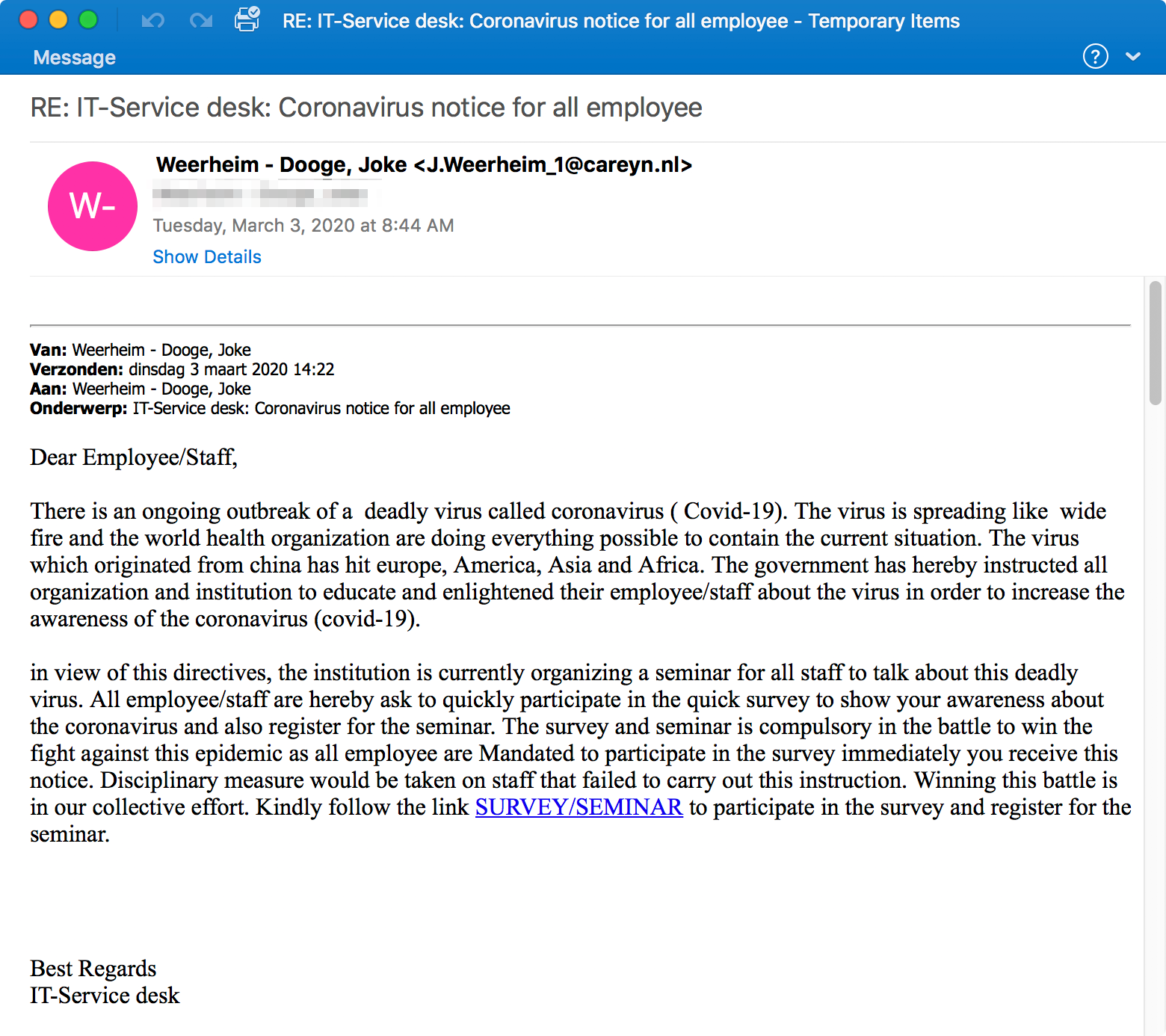
Outlook Web Access Credential Phish Summary:
These Coronavirus cyber threats claim to be from an organization’s IT department and poses as an awareness and education email for employees around coronavirus. The email asks the recipient to click on the link to take a survey and register for a health safety awareness seminar. If a recipient clicks the link, they’re taken to a credential phishing page that asks for their Outlook Web Access (OWA) credentials.
Credential Phish: Italian Email Credential Phish
Key Points: Attackers use an Italian language lure around the spread of coronavirus to capture email credentials.
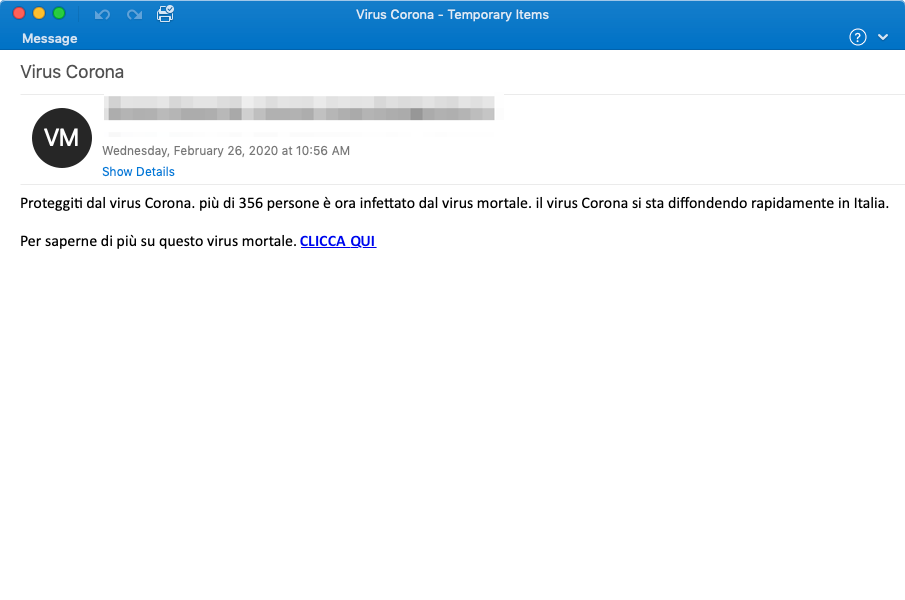
Italian Email Credential Phish Summary:
On February 26, 2020, Proofpoint researchers observed an email credential phishing campaign targeting Italy. It was written in Italian language and urged recipients to protect themselves as the virus was spreading and many were infected. If they clicked on the URL in the email, they were presented with an email credential phishing page. The credential phishing landing page also used custom coronavirus-themed graphics.
Malware: Ostap / The Trick Banker
Key Points: Campaigns targeting Italy and Czech Republic with WHO lures.
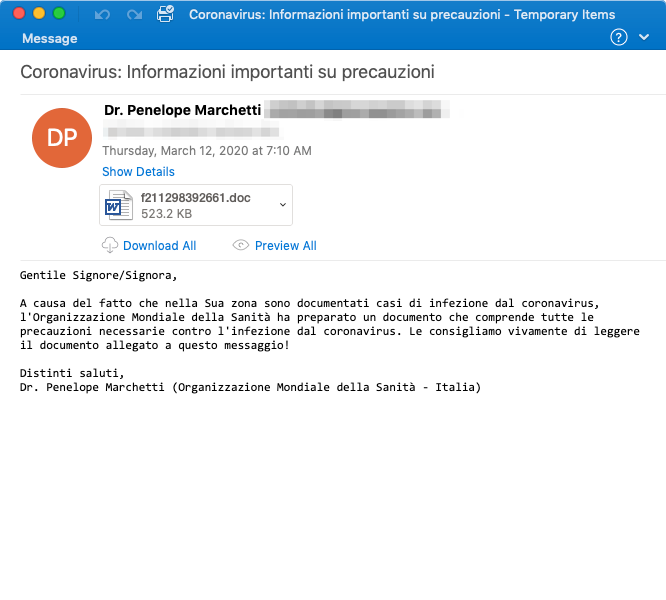
Ostap / The Trick Banker Malware Summary:
In March 2020, we’ve seen multiple instances of attackers attempting to deliver malicious Word macro documents in Italy and Czech Republic. These emails claim to come from local medical professionals, for example, “Dr. Penelope Marchetti (World Health Organization - Italy)” with an attachment that contains an update on infection cases in their area.
If the recipient enables macros from the attachment, the documents would drop and run Ostap JavaScript downloader, which in these instances downloaded The Trick “red5” banker.
To note, Italy is currently one of the most targeted regions we’ve observed within this attack theme, with multiple malware and phishing threat actors attempting to deliver malicious emails using Coronavirus lures.
Malware: Get2 Downloader
Key Points: Threat actor TA505 targets pharmaceutical and manufacturing industries in the United States.
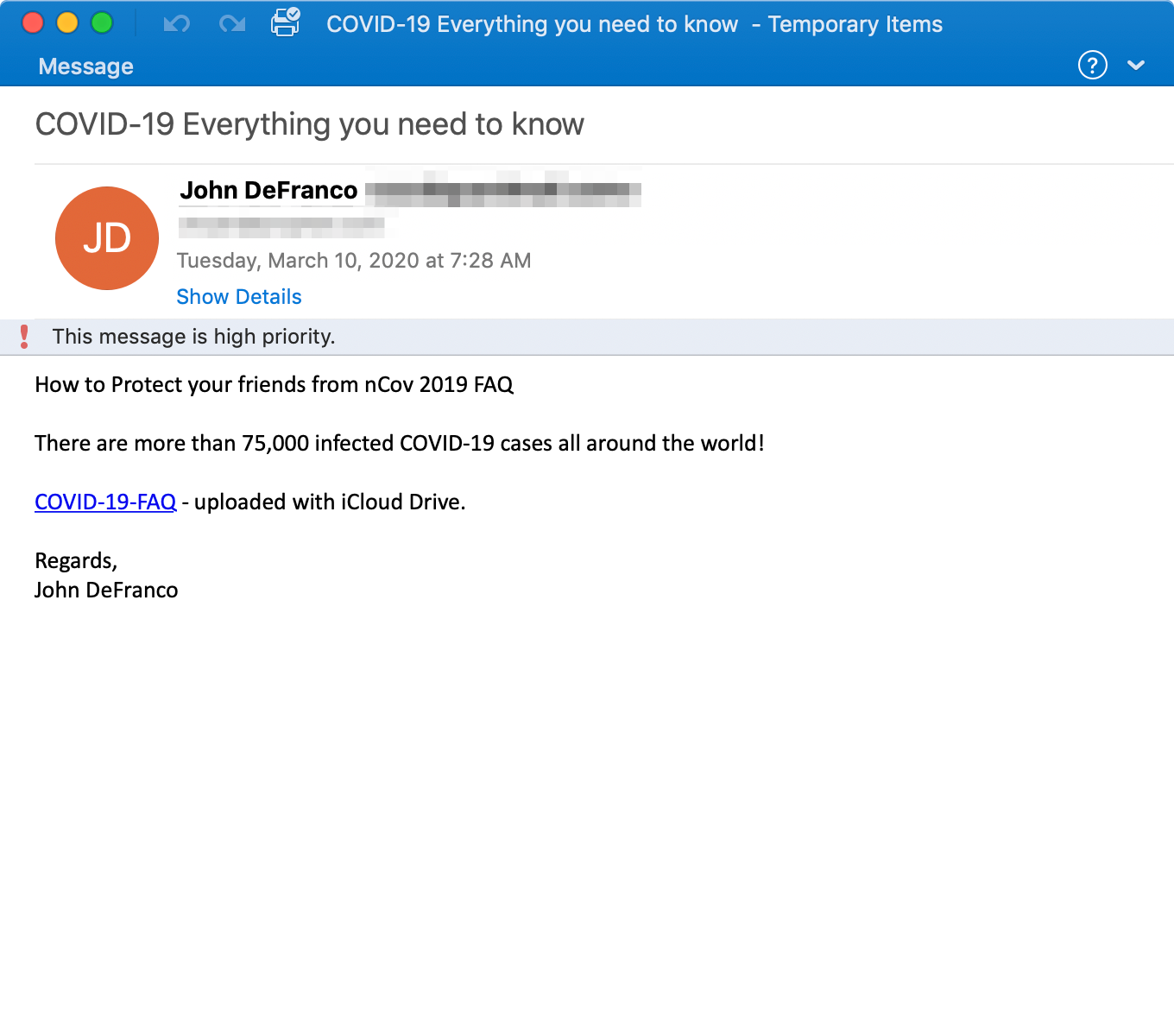
Get2 Downloader Malware Summary:
On March 10, 2020, Proofpoint researchers observed thousands of emails primarily targeting pharmaceutical and manufacturing companies in United States. The emails claimed to contain information about how to “protect your friends” from coronavirus and urged the recipient to click on a link.
If the recipient clicked on the link, they would be taken to a web page where they had to click on another link, which would then download a malicious Excel document. After downloading the malicious Excel document, if the recipient also enabled macros, the macros executed an embedded Get2 loader. Get2 typically downloads SDBbot RAT.
While the email lure is simple and not particularly compelling compared to others we observed, this campaign was distributed by TA505, a threat actor tracked by Proofpoint. The group is known for their large campaigns, experimentation with a variety of delivery mechanisms, and distribution of ransomware, bankers, and RATs.
Malware: Urnsif Banker
Key Points: Threat actor TA564, who regularly targets Canada, launches email campaign targeting “parents and guardians” and spoofs Public Health Agency of Canada.
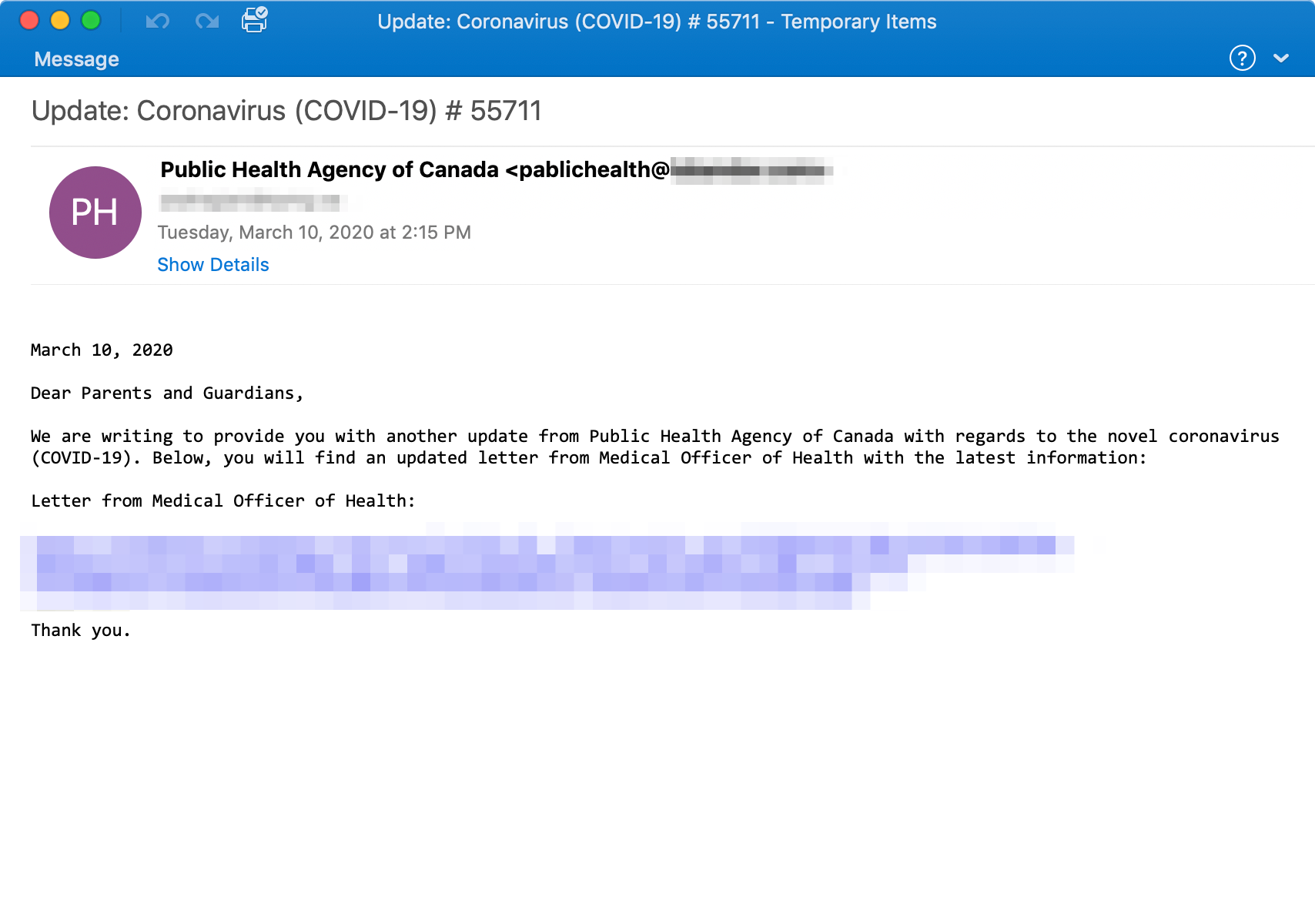
Urnsif Banker Malware Summary:
Proofpoint researchers observed on March 10, 2020 an email campaign targeting Canadian users claiming to be from the Public Health Agency of Canada. It addressed "parents and guardians" with an update from the spoofed health agency. This clearly sought to leverage parents’ emotions about their children’s wellbeing and increase the attack’s success rate.
The email contained a URL, linking to a compressed Microsoft Word document (named Coronavirus_disease_COVID-19__461657952561561.doc) with macros. If the recipient enabled the macros, they would download and install Ursnif banker.
We attribute this activity to threat actor TA564. This threat actor typically targets Canada with false shipping lures, such as CanadaPost and DHL, and have attempted to deliver Ursnif, DanaBot, and Nymaim in the past.
Malware: GuLoader and Agent Tesla
Key Points: Campaign exploits Equation Editor vulnerabilities to load GuLoader and Agent Tesla.
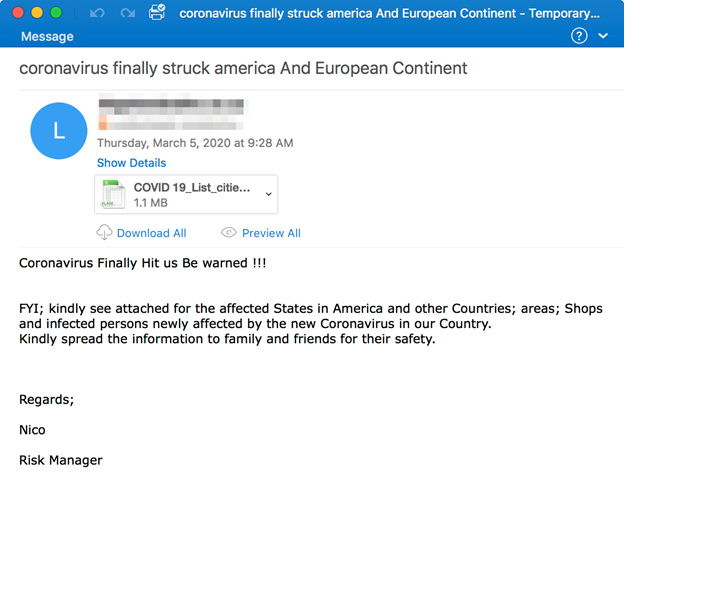
GuLoader and Agent Tesla Malware Summary:
Proofpoint researchers found this email, dated March 5, 2020, that seeks to capitalize on fears around the spread of coronavirus in the United States. It contained a message about affected areas in America (and the European continent), including shops. The malicious attachment titled “COVID 19_List_cities_names.xlam” supposedly contained a list of impacted city names.
When the recipient opened the malicious attachment, it attempted to exploit Equation Editor vulnerabilities to download GuLoader, which in turn would download Agent Tesla.
Malware: Remcos
Key Points: Campaign impersonating Philippines Customs to deliver Remcos.
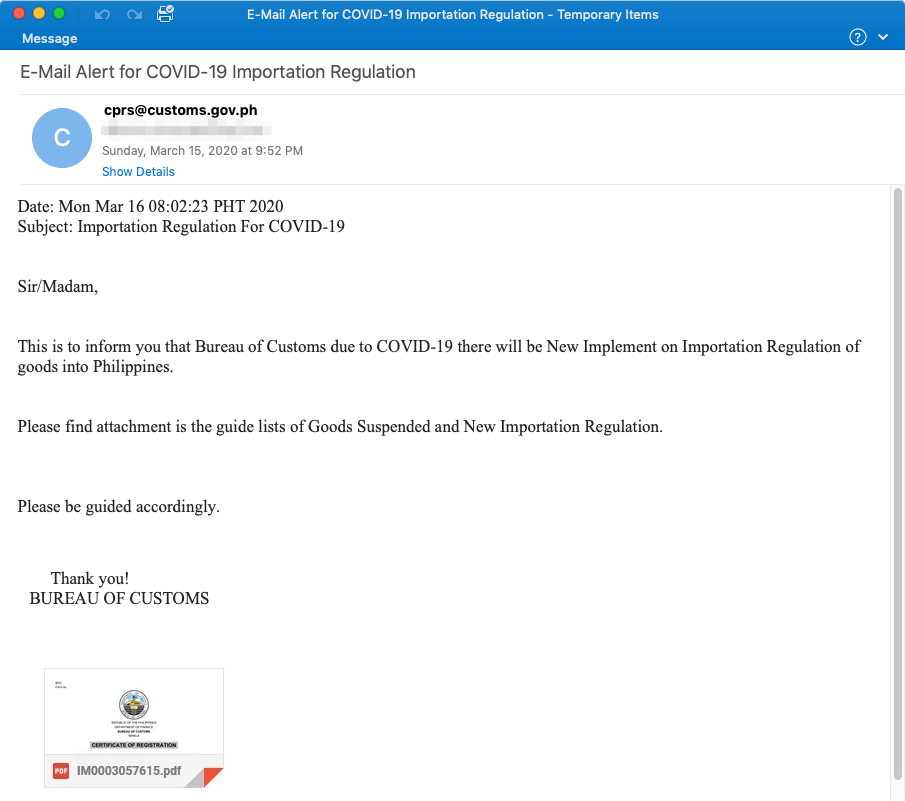
Remos Malware Summary:
On March 16, 2020 Proofpoint researchers observed an email campaign targeting various international companies. The emails impersonated the Philippines customs agency and claimed to contain information about new regulation of imports as well as suspended goods. This was an interesting lure since trade suspensions and regulations have potentially greater impact compared to even travel restrictions.
These emails contained Microsoft OneDrive URLs leading to a compressed Remcos RAT executable.
Spam: Pandemic Survival Course
Key Points: Spam campaign promoting a survival course containing everything you supposedly need to know about the coronavirus pandemic for $37.
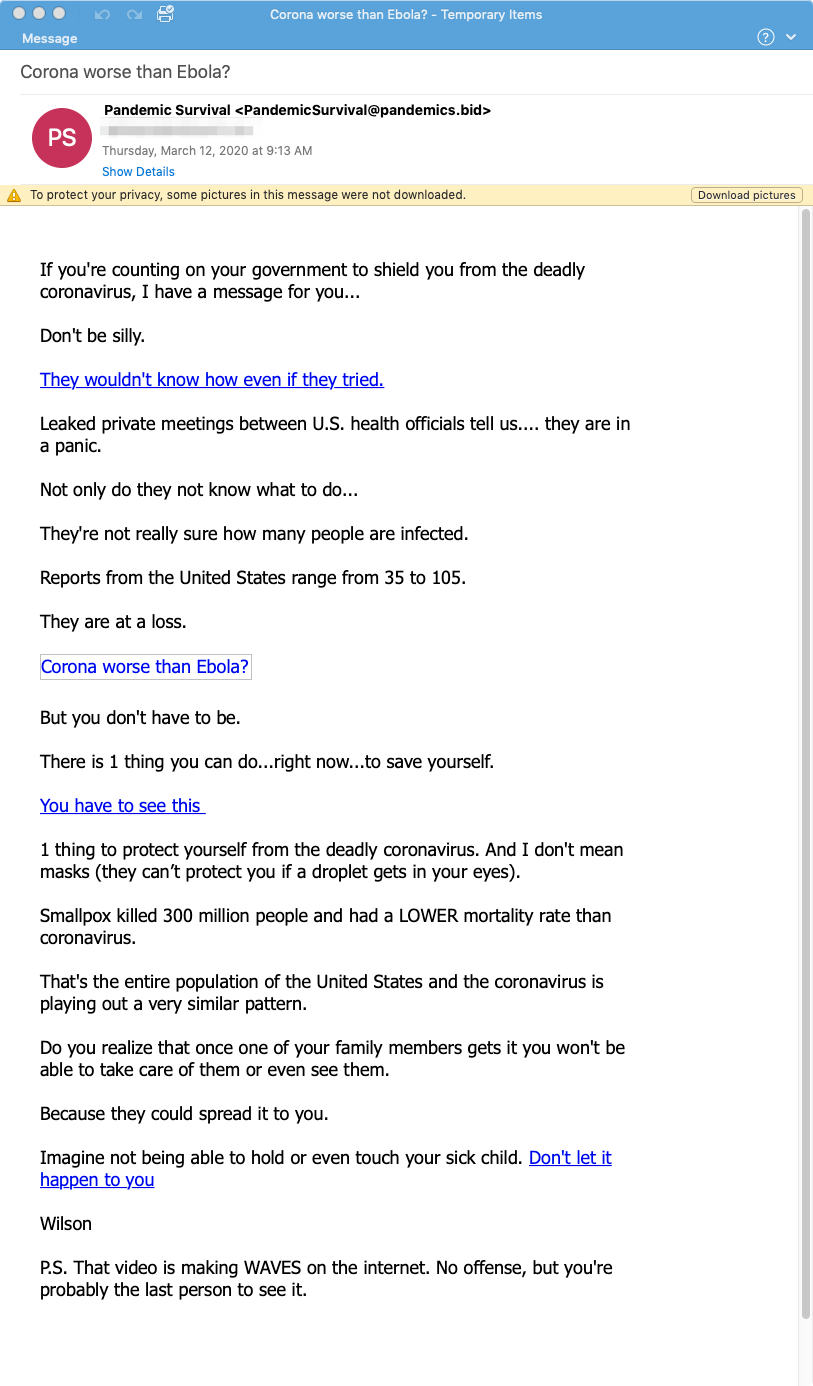
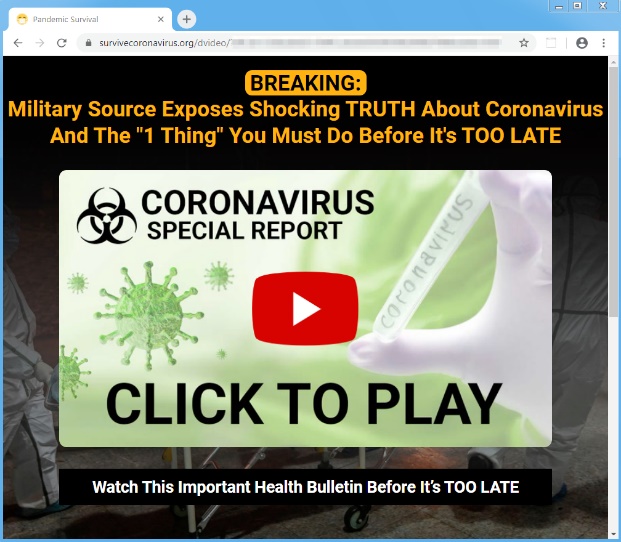
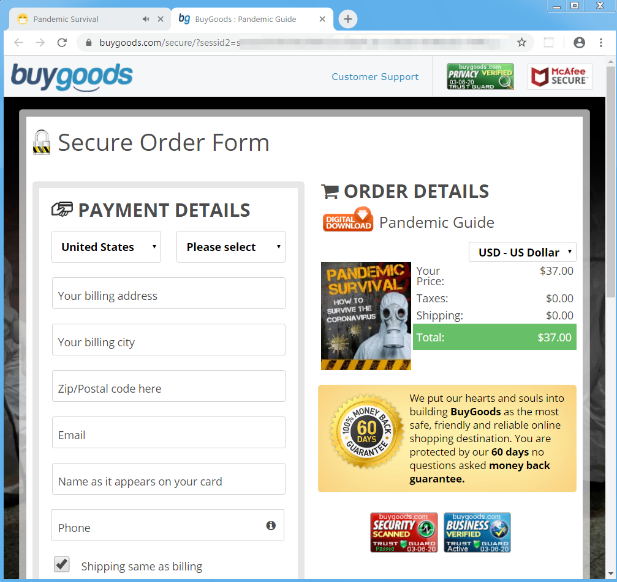
Pandemic Survival Course Spam Summary:
In March 2020, Proofpoint researchers observed multiple spam campaigns peddling an informational course for US$37. The recipient must first watch a 30+ minute long video before getting the link to purchase the course.
The email and the video try to seed fear, uncertainty, and doubt into the recipient about the government's ability to respond to the situation. They describe a coming pandemic and other events (millions of people dead, forced quarantine by the military, drug companies experimenting on humans with vaccines and so on).
The course supposedly offers information around dozens of topics such as: How to make a hazmat suit; should you own a gun; how to keep the army out of your home; what to do if urban warfare breaks out; what to do if an infected neighbor knocks on your door. We did not verify what happens after the payment, but we recommend to everyone to keep their money and not take the bait.
Spam: Coronavirus Testing Kit
Key Points: Spam campaign asking media and advertising companies to promote a malicious website that supposedly sells testing kits in exchange for US$100.
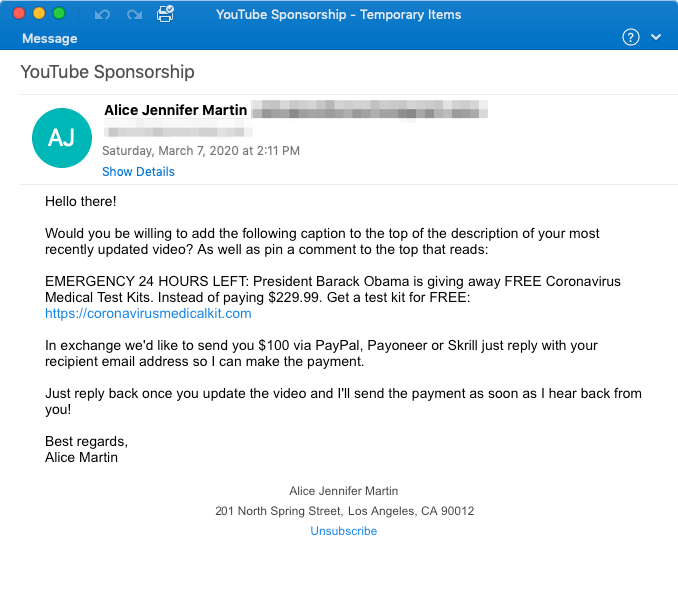
Coronavirus Testing Kit Spam Summary:
In early March, Proofpoint researchers observed a small spam campaign targeting media and advertising companies in the United States. The email did not try to get the recipient to open the malicious URL, but instead asked the recipients to spread a website URL to their audience. Specifically, it asked them to place the URL and a short message on top of their most recent YouTube video description. The sender offered a payment of $100 in exchange for this.
The website, coronavirusmedicalkit[.]com, offered to sell free COVID-19 testing kits. However, at the end of the ordering process a $10 fee was added (likely for shipping). As Better Business Bureau put it, a lot of times “these phony sellers take victims’ money and never deliver anything at all…These sites use tricks like limited time deals to entice you into ordering more.” This campaign is interesting because we do not often see direct outreach like this via email.
Spam: Masks
Key Points: One of the most common spam types with Coronavirus as a lure are offers for masks.
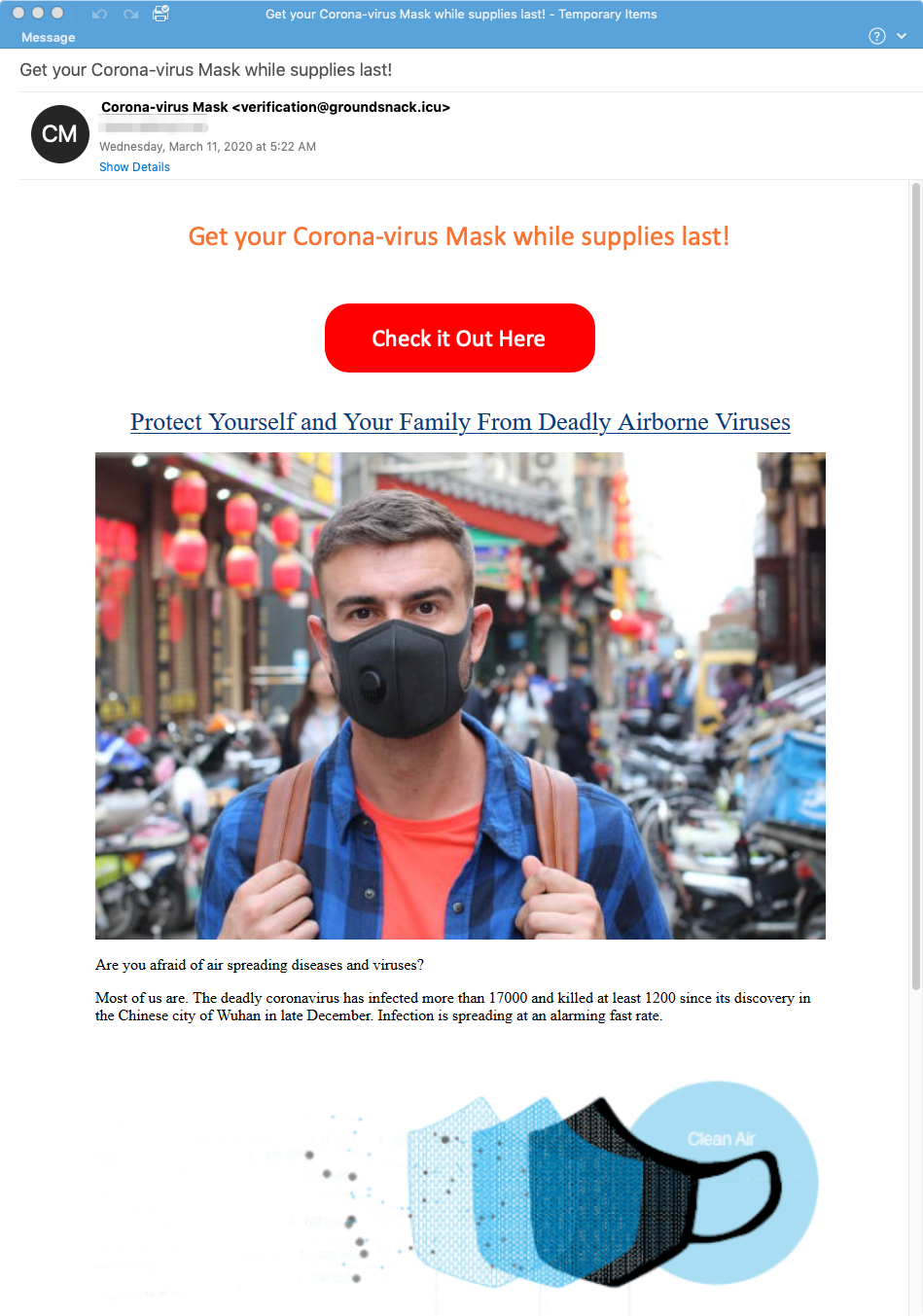
Masks Spam Summary:
The sale of masks is one of the most popular types of spam campaigns capitalizing on the coronavirus situation by volume. In this example, the email urged recipients to act urgently while supplies last. It offers to sell mask for $49 each. Once again, as the BBB article puts it, recipients are likely to never receive anything if they pay.
Conclusion
This sampling shows just how broad and diverse the Coronavirus cyber threat landscape has become. Attackers of all kinds across the globe are now using coronavirus for nearly every type of attack possible.
These examples are just a fraction of what our researchers have seen. We are continuing to monitor closely and will continue to update with notable changes in attacks, attacker tactics, or trends in the threat landscape.
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
4616c3a50e0393ababc925b496f04f3687664e9d1c4b7966485a7a9124047214 |
SHA256 |
Word document delivered in the Italian Ostap campaign in 2020-03-12 |
|
hxxp[:]//www[.]agt[.]net/~mnpicker/2jgmu9r/h9a6kn.html |
URL |
Example URL leading to Get2 on 2020-03-10 |
|
hxxp[:]//adsign[.]lk/wp-admin/tkennedy.php?t=[Redacted Base64] |
URL |
Example URL leading to Tordal on 2020-03-11 |
|
hxxp[:]//davidrothphotography[.]com/zHzrr |
URL |
Example URL leading to Ursnif on 2020-03-10 |
|
hxxps[:]//bitbucket[.]org/example123321/download/downloads/foldingathomeapp.exe |
URL |
URL hosting RedLine on 2020-03-07
|
|
4f630d3622d1e17c75aac44090b3b5bd47d5b2ae113434cde5708bbb7cffef49 |
SHA256 |
COVID 19_List_cities_names.xlam attachment leading to GuLoader & AgentTesla on 2020-03-05 |
|
c9a8dd42a46e2c6849564576f96db6741ad0036726f98d7b43641907f953d3f3 |
SHA256 |
“Rapport sur les coronavirus.doc” attachment leading to Ave Maria of 2020-03-06 |
|
hxxps[:]//toyswithpizzazz[.]com[.]au/service/coronavirus |
URL |
OWA phish on 2020-03-03 |
|
Www[.]pandemicsurvival[.]bid |
Hostname |
"Pandemic Survival" Course Spam on 2020-03-07 |
|
coronavirusmedicalkit[.]com |
Domain |
“Coronavirus Testing Kit “ Spam on 2020-03-04 |
|
groundsnack[.]icu |
Domain |
Mask Spam on 2020-03-11 |

