Spearfishing and spear-phishing may be homonyms, but they have vastly different meanings and apply in very different contexts. Spearfishing is a form of fishing in which the fisherman attempts to impale a fish upon a spear, which can be thrust or thrown by hand, or fired from a spear gun. “Spear phishing” on the other hand is, of course, the by now well-documented technique of sending targeted phishing emails to a user or organization for the purpose of infecting the client and/or stealing logins and other credentials in order to gain a foothold inside the targeted organization – the targeted nature of the threat distinguishes it from longline and other broad-based phishing campaigns.
This targeting was on display again in a phishing email recently detected by Proofpoint that seemed to answer the question: What could be more ironic than a “Tex-Mex taco salad” web page that pulls in the Fiesta exploit kit? How about a targeted phishing campaign that included a link to a malware-laden website for… spearfishing?
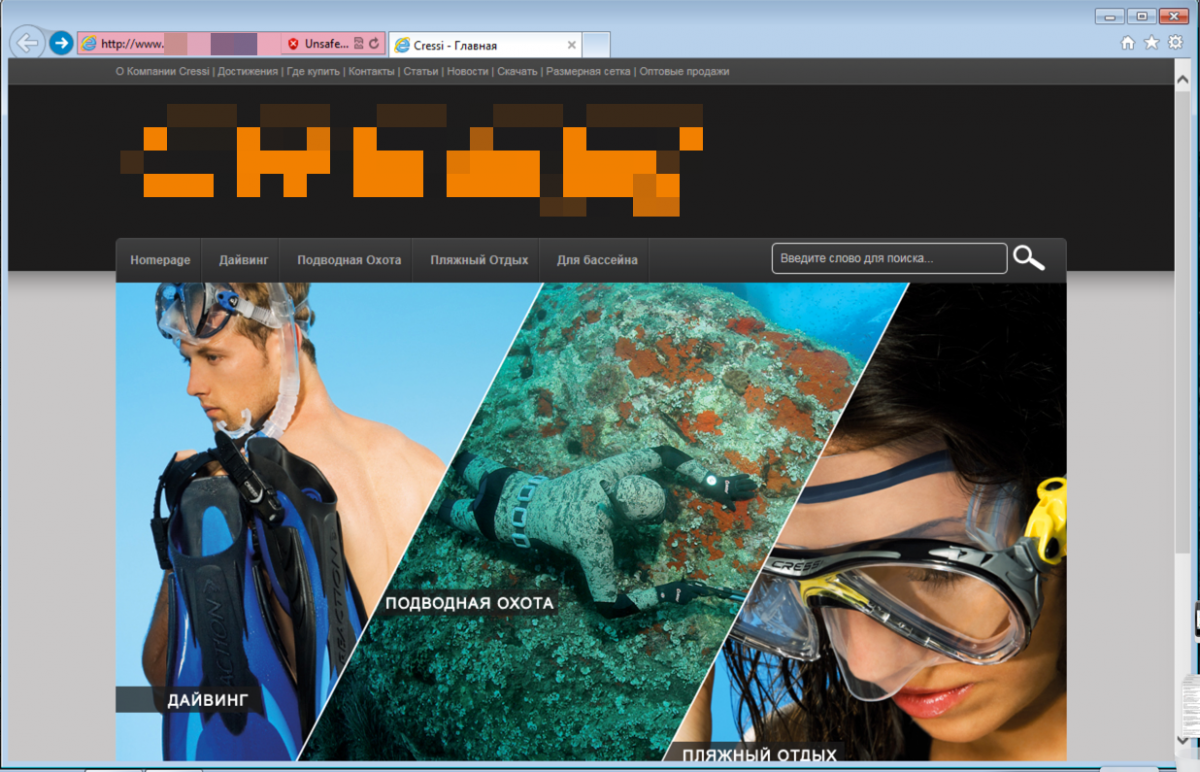
In this case, a phishing campaigner compromised a Russian website for spearfishing enthusiasts, then used it to host a credential-stealing Outlook Web Access page.
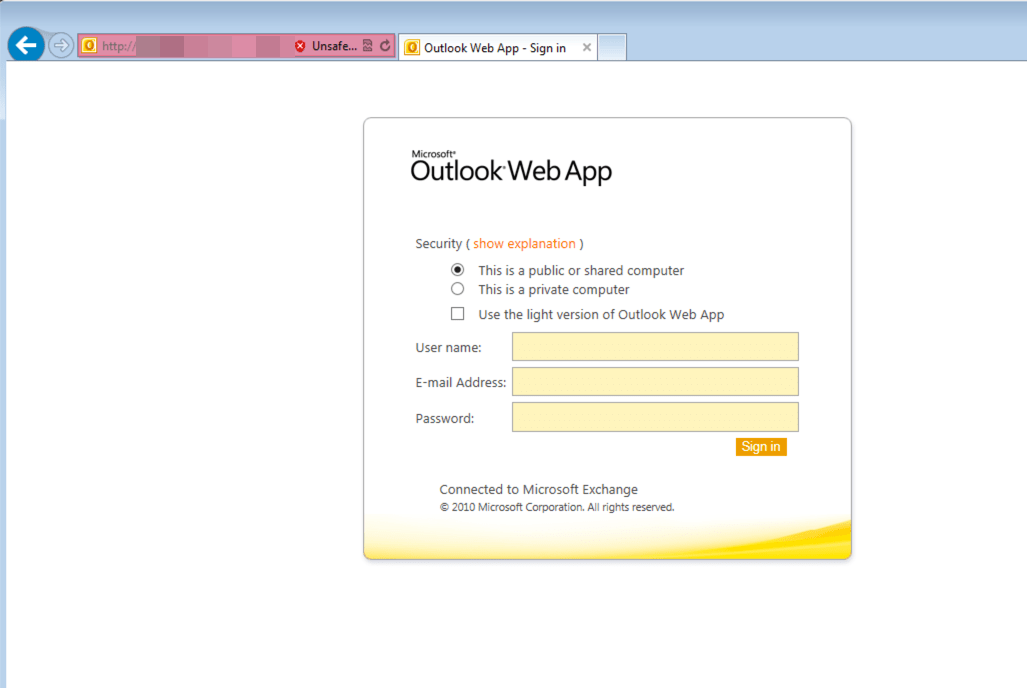
The link to the compromised spearfishing site was included in emails targeted specifically at recipients within universities. The payload was a very realistic looking form that could easily trick unsuspecting students, faculty, or staff at the targeted organizations into providing their Outlook Web Access credentials, which frequently double as their domain and other logins. An attacker who spears even a single user would gain valuable access to email addresses, Inbox contents, calendaring and potentially other services that would enable them to move laterally within the targeted university to higher value resources, such as financial and health care records, research data and other prizes.
Universities are a rich repository of user and research data, with a fluid student body and a user base that demands openness and access. Leveraging a compromised Russian spearfishing site to carry out a credential-stealing campaign, this phishing email targeted at universities highlights a valuable lesson about the dangers of seemingly harmless email: to borrow from The Dude – and with apologies to our Russian colleagues for the reversal -- some days you spear the fish; but some days the phish can spear you.











