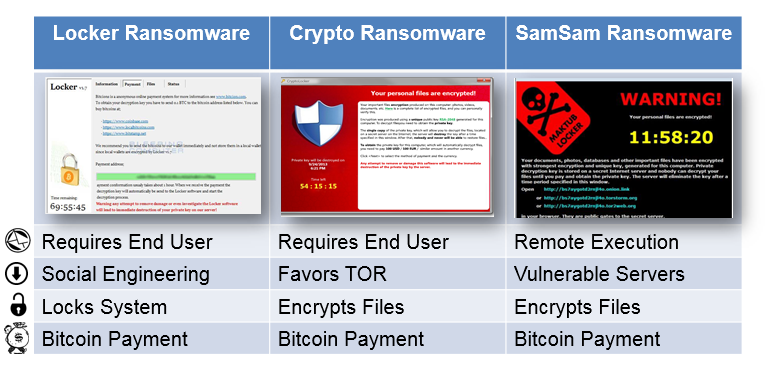
Types of Ransomware
Ransomware takes many forms, but the most common types are as follows:
How Ransomware Works
The majority of ransomware attacks start with an email that includes a link or attachment that looks legitimate, and are often part of a social engineering scheme. From an end-user perspective, ransomware works in the following way:
- User clicks on ransomware link or attachment
- Malware has anti-sandboxing techniques enabled
- Ransomware message is deployed from other infected computers
- Ransomware payment screen appears
While ransomware is a threat to all organizations and industries, the general lack of overall data and information security have made the healthcare industry a prime target for ransomware attacks. The sensitive nature of patient data puts officials in a very tough position, as resources are often focused on HIPAA compliance rather than security. A recent Kaspersky poll indicated that 84 percent of U.S. business owners would not pay if attacked by ransomware, even if it meant losing data permanently.
Ransomware Response and Prevention
According to Webroot, there is a 50% chance end users will encounter a phishing site in 2016. Our 2016 State of the Phish™ report found that 85% of security professionals surveyed indicated they had been the victim of a phishing attack in 2015, a 13 increase from the prior year.
In the case of a ransomware incident, a fast response time is crucial to having any chance of recovering data. It is important to immediately disconnect your device from all available networks it is connected to, turn off any wireless capabilities, and unplug any external hard drives or USBs. Once this step is complete, assessment of the scope and strain of the attack can begin in order to determine a response. The Crypsis Group employs a strategy called the Crypsis I.C.E. Methodology™, which is a useful response tool if ransomware hits.
In an ideal world, your end users shouldn’t be falling for ransomware, as phishing attacks are the primary infection vector. The following best practices will equip your organization to be prepared in the event one of your end users falls prey to ransomware:
- Develop an Incident Response Plan
- Conduct regular back-ups and monitor back-up systems
- Deploy frequently updated anti-virus and content filtering rules
- Perform regular perimiter vulnerability scans and pen tests
We recommend putting a comprehensive security awareness and training program into place as an effective means to educating employees on best practices and habits. Good anti-phishing behaviors are, by extension, the best ransomware prevention money can buy. Our portfolio of 18 interactive training modules can help improve your organization’s cybersecurity posture. Explore our training portfolio to learn how we can help protect your end users from ransomware and other threats.