In recent years, the real estate market has become a prime target for phishing and business email compromise (BEC) attacks. Buyers and agents in highly competitive housing markets can find themselves under tremendous pressure to seal the deal before someone else swoops in. That pressure to make quick decisions — combined with the relative complexity of real estate transactions — creates opportunities that cybercriminals can exploit.
The following insights, tips, and examples of actual phishing attacks can help you stay safe during real estate transactions.
Understanding the Threat
Closing on a house often occurs 30-60 days after an offer is accepted. In the US, house hunting generally peaks in late spring and early summer, which means an abundance of closing transactions take place in June, July, and August. Phishing attacks that target these transactions have resulted in significant losses for homebuyers, realtors, and other parties who could be found negligent. And the severity of these attacks is on the rise.
This fast-growing form of real estate cybercrime is a type of BEC that leads to wire transfer fraud. During these attack campaigns, a cybercriminal infiltrates or mimics communications related to a real estate transaction, and ultimately uses social engineering techniques to trick the buyer into wiring funds to the criminal’s account. Victims have lost anywhere from tens of thousands to millions of dollars.
According to the US Federal Bureau of Investigation (FBI), nearly $1 billion in purchase transactions was “diverted or attempted to be diverted” in fiscal year 2017. This represents a massive increase over the $19 million the FBI recorded in 2016. (Some of this growth may be attributable to increased reporting of attacks.)
Creating Opportunities for Credential Theft and Malware
The number of documents and parties involved in closing a real estate transaction creates many openings for BEC attacks, and phishing emails are commonly used to request a fraudulent wire transfer. These attacks can be difficult to spot, because the individuals involved in real estate transactions receive a wide variety of email communications — sometimes from barely known parties — which often contain attachments to download and links to follow. These include:
- Emails from realtors with links to a document signing platform
- Emails from lenders and/or mortgage brokers, with attachments and links to document signing platforms
- Emails automatically generated by document signing platforms
- Emails from building inspectors and contractors, with attachments
- Emails from appraisers and title companies, with attachments
Cybercriminals see opportunity within this flurry of documentation. Some quick snooping online or via social media can turn up identifying details about individuals who are currently in the buying or selling process. Attackers then craft phishing emails that seem to include legitimate documentation and/or logical web links. The goal? To infect computers with malware, such as keyloggers that can steal login information, or to direct people to look-alike phishing web pages designed to steal credentials.
Phishing campaigns tracked by Proofpoint over the past year revealed large numbers of document lures purporting to come from realtors, closing companies, DocuSign, and other organizations that could be involved in home sales. According to research shared on Proofpoint’s Threat Insight blog, these lures generally direct recipients to phishing landing pages that abuse familiar brands, and which are designed to steal a person’s email credentials.
This phishing landing page builds on the common DocuSign lure to target specific victims, abusing real estate brands (blurred at the bottom of the image) to increase the illusion of legitimacy. Source: Proofpoint Threat Insight Blog
Preying Upon Urgency
Once a cybercriminal has compromised the email account of a buyer, realtor, or lender, they can simply snoop through messages to obtain the closing date and transaction details for a property sale, as well as contact information for the other parties involved. (Not to mention, users who are less cyber-aware may not think twice about sending the password for a document or signing site through unencrypted email.) Armed with that information, the cybercriminal can time his or her BEC attack to coincide with important dates in the transaction.
During a sale, documents are sent back and forth for responses and signatures with scant time for careful review. And as a closing date draws near, the urgency ramps up; the parties involved don’t want to miss any detail that could jeopardize the deal. It’s a perfect time for a cybercriminal to make a simple request: a last-minute change to the instructions for wiring funds from the buyer.
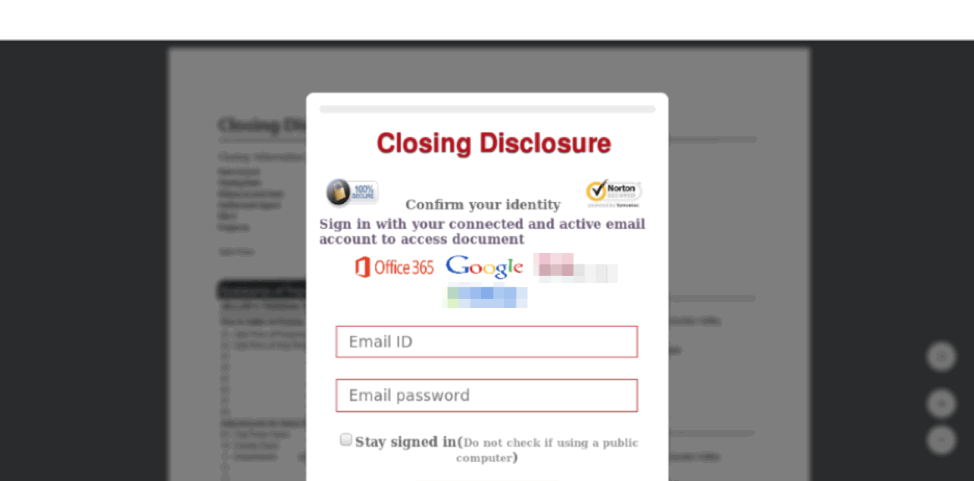
With urgency building, it’s easy for buyers and sellers to let down their guard and fall for a phishing site like this, which abuses the brands of two national retailers. Source: Proofpoint Threat Insight Blog
Spotting a BEC attack can be very difficult. According to REALTOR® Magazine, fraudulent communications “may include detailed and accurate information pertaining to the real estate transaction, including existing wire and banking information, file numbers, and key dates, names, and addresses.” In addition to containing intercepted details that lend credibility, “the emails may come from what appears to be a legitimate email address, either because the thief has successfully created a sham account containing a legitimate business’s name, or because he or she is sending the email from a truly legitimate — albeit hacked –– account.”
Given the complexity of a home purchase, the sensitive information involved, the time pressure, and the legitimate-seeming emails, it’s no wonder that many buyers fall for this type of attack, sending thousands of dollars into a cybercriminal’s bank account.
Attacking Real Estate Businesses in Addition to Buyers
Beyond the BEC and phishing attacks against buyers themselves, real estate businesses are also directly targeted, albeit to a lesser extent. According to Proofpoint’s Threat Insight blog:
These include email attacks on realtors, homeowners insurance agencies, and more, in which the primary payloads included remote access Trojans (RATs). Because of the nature of the transactions in which these business engage, RATs and information stealers offer additional opportunities for threat actors to steal a range of personal and banking information.
Real estate businesses, mortgage companies, brokers, title companies, and others collect personal data that could be highly profitable for criminals, from Social Security numbers, bank account information, and personal checks, to credit card information, drivers’ license numbers, and more.
Tips for Safer Real Estate Transactions
Here are our tips to help buyers stay safe when conducting real estate transactions:
- Protect your email account. Make sure you are following best practices for creating strong passwords and enable multifactor authentication whenever possible.
- Carefully examine any email that contains attachments and embedded links. Take extra steps to verify that the communication is legitimate before taking action on it.
- Don’t use free WiFi networks while conducting financial business.
- Be wary of any closing or wiring instructions sent via email, especially if they request last-minute changes to the process.
- Verify instructions with settlement personnel either in person or by phone to make sure they are correct. Remember to independently verify the phone number — the number in an email you receive could simply connect you to a fraudster.
- If you are the victim of wire fraud, contact the authorities immediately, such as a local FBI office.
Real estate professionals can find cybersecurity resources on the National Association of Realtors website, including advice about protecting their clients from cybercrime and controlling the damage caused by any successful scams, as well as a Data Security and Privacy Toolkit.



