There’s an old saying that only two things are certain: death and taxes. And in 2020 you can add tax scams to that list. With April 15 quickly approaching, people in the United States are starting to think about their taxes and attackers are as well. Proofpoint researchers have already seen attackers aggressively jumping into tax season. So far we’ve seen attacks fall into two categories:
- Tax-themed emails with malicious attachments
- Legitimate tax-focused websites that are compromised to deliver malware
The focus on compromising legitimate tax-focused websites this year is noteworthy. In our research, we’re seeing these attacks target small businesses that specialize in tax preparation. If you have the word “tax” in your domain name; you're a target this year. And while the tax-themed email attacks hit businesses in all sectors, we also saw financial firms and construction industries targeted disproportionately. The construction industry targeting in particular is a reminder that no one sector is immune.
Tax-themed emails with malicious attachments
Attackers have used tax-themed emails to deliver malicious attachments for years. The technique isn’t new and the attacks don’t have to be novel to work. Attackers often use what has been successful for them in the past to find another payday. Everyone should exercise caution around tax-themed emails: this is a threat that is certain.
The tax-themed email and malicious attachment examples below demonstrate that attackers are increasingly making their fake tax-themed emails look better and better. In some cases, they use data they’ve stolen or bought to tailor it to the recipient to make it more believable.
In figures 1 and 2 below an email attacker is attempting to get the recipient to open a Word document and enable macros. When they do, the document installs TeamViewer which is a legitimate remote control application that attackers frequently abuse. In this case, once TeamViewer is installed, the attackers are able to completely control the recipient’s computer, giving them complete access to all the information on that computer including banking and investment accounts.
In Figure 1 we see an email with an attached .ZIP file named Tax_File_2042.zip. This email uses a plausible (fake) sender address and explains who the (fake) sender is, what the attachment is, and why the recipient should open it.
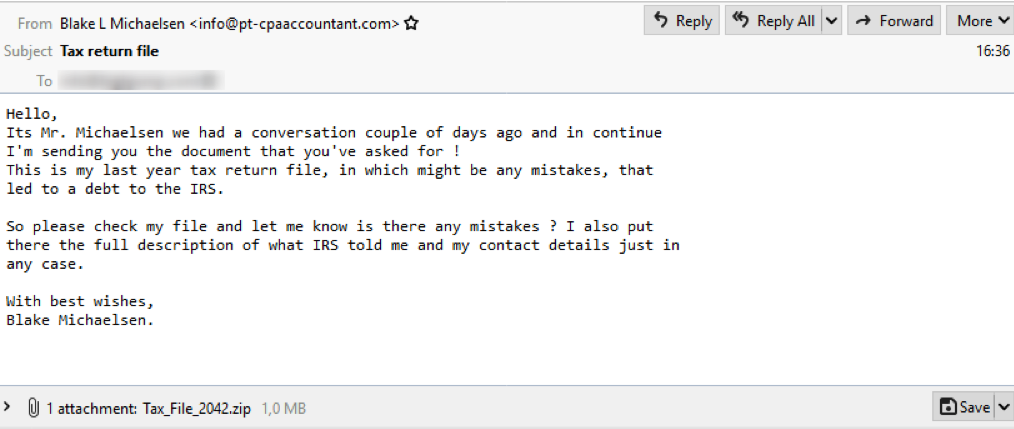
Figure 1 Malicious Tax-Themed Email with Attachment
Attached to the message is a .ZIP file which has a Microsoft Word document with macros. The attached Word document has the logo of one of the largest tax preparation agencies in the United States (redacted). These attackers have good attention to detail because the name in the “Prepared for” section matches the (fake) name in the email. The document also matches what’s described in the email.
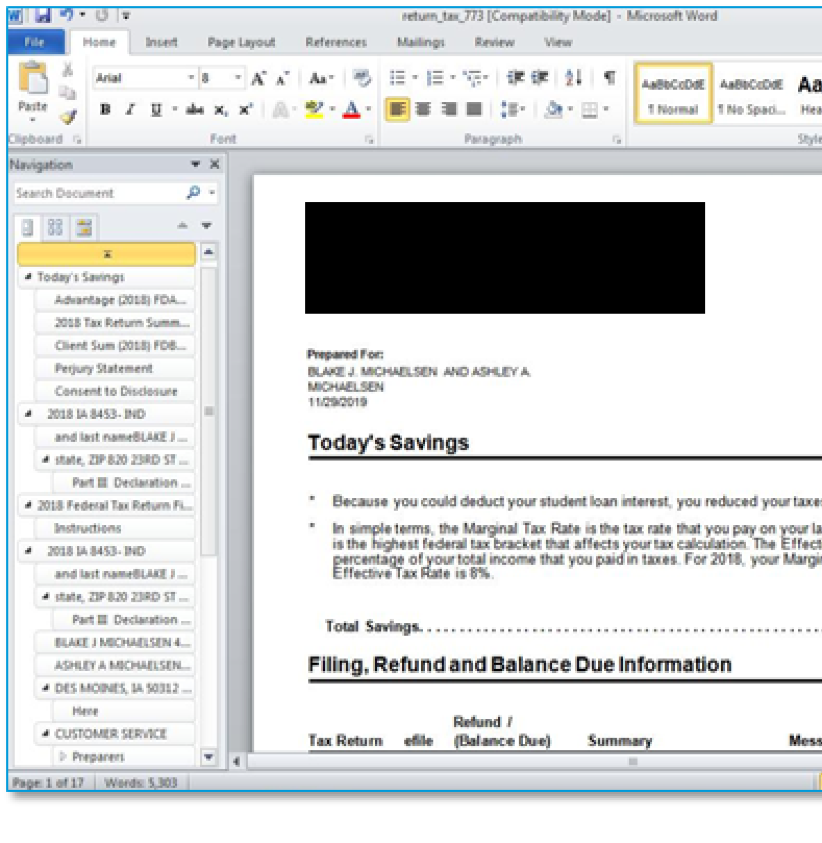
Figure 2 Malicious Tax-Themed Word Attachment
The attacker’s goal in using a more plausible email and attachment is to help ensure the recipient doesn’t notice the malicious installation of TeamViewer. Because TeamViewer is a legitimate application, it also has the benefit of not being flagged as malware by security software. Once it’s installed, the recipient would need to look more carefully to locate it (more than just running an antimalware scan).
This is only one example of this particular attack we’ve seen. Some of the other attachment names we’ve seen recently include:
- calculation of corporate tax for december 2019_v2.xls
- tax-invoice--99999.pdf
- return_tax_2333.doc
- tax_file_6535.zip
- return_tax_773.doc
- file_tax_8846.doc
TeamViewer is also just one technique used in these attacks, others use more traditional malware or other legitimate applications that are being misused. We’ve also seen more traditional malware attacks that use malicious attachments within messages claiming to have attached W2, W4, and 1099 tax forms.
In one campaign like this, we saw over 5,000 messages over the span of three days targeting financial firms and manufacturing companies. These messages had subjects like:
- Important changes, filing due date and charges to form 1099
- Important adjustments, filing due date and fees to form 1099
- Significant adjustments, submitting deadline and fees to form 1099
- IRS. Taxes
The messages had an attached Microsoft Word document with macros. When the document is opened, the recipient is urged to enable the macros as shown in Figure 3.
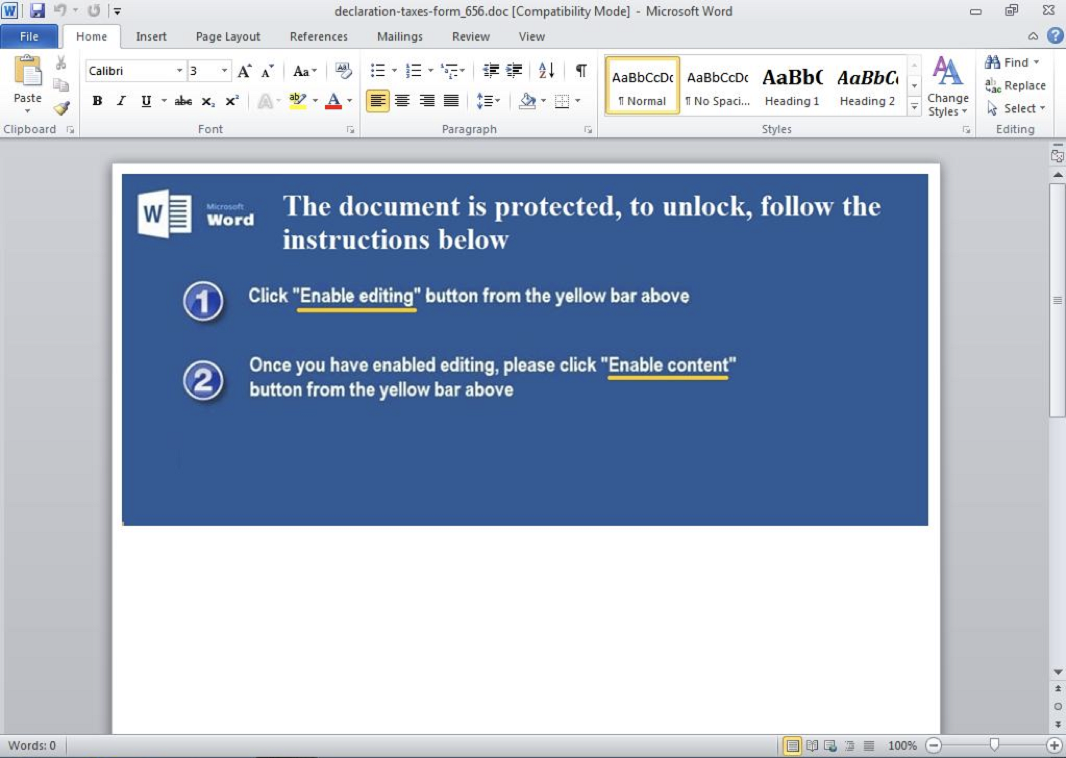
Figure 3 Fake Tax-themed Word document with message to enable macros
When the macros are enabled, the document downloads “The Trick,” a commonly used banking Trojan that steals banking and other financial information.
A different campaign we’ve seen using tax forms as its lure comes with the subject line “Tax Form W-4" and targets retailers.
Unlike other attacks, these criminals aren’t trying to plant malware on the system. Instead, they are taking the recipient to fake Office 365 login pages to capture and later abuse the recipients Office 365 logins. This can give those attackers full access to the target’s online Microsoft Office documents and email which can be lucrative for other forms of financial theft.
Compromised Legitimate Tax-focused Websites
This year, a big trend we’re seeing is the compromising of legitimate tax-focused websites. These are websites that are owned and run by legitimate companies but have been taken over by attackers who are using them to distribute malware to people who visit these sites.
Attackers are accomplishing this by targeting sites that have unpatched and out-of-date WordPress and other content management system installations. Attackers use these vulnerabilities to get access to the site, make changes to the sites’ webpages in ways that can only be seen if you view the sites raw HTML. This hides the compromise from visitors as well as site owners who don’t know HTML well enough to recognize the change or what it means. Attackers plant this code on the sites and that code will try to download malware on to the systems of people who visit the sites. To better cover their tracks, attackers will frequently have the malware hosted somewhere else, making it even harder to detect that the site has been compromised and is serving up malware.
In these attacks, we’ve seen the sites of smaller tax preparation and accounting firms targeted and compromised. This makes sense because smaller companies often have fewer resources and less expertise to prevent these attacks and detect them when they’ve happened.
Better Protecting Yourself this (and every) Tax Year
There are ways that you can better protect yourself this year, and every year.
First, treat all tax-themed attachments as potentially malicious. These days, many tax preparation and accounting companies don’t send information as attachments through regular email. They’re increasingly using secured email and document sharing portals. If you get an email with a tax-themed attachment, even one you may be expecting, verify with the sender before opening it.
Second, if you are a smaller tax preparation or accounting firm and you have a website, make the security of your website a top priority. Even if it’s just a website with your address and information, it’s still a bigger target for attackers than other websites, especially this time of year. Look at hosting your website somewhere where the hosting company will handle the updates and security for you. Unless you have the time, resources, and expertise to do the security yourself, this is the best and easiest way to ensure your site is safe for your customers and visitors.











