Overview
As in 2016, the third quarter of 2017 was marked by peak year-to-date malicious message volumes. In this case, high-volume campaigns were led by ransomware, particularly Locky and, to lesser extents, Philadelphia and GlobeImposter, as well as The Trick banking Trojan. Notably, the majority of malicious email campaigns came from a single actor: TA505, whose extensive history was profiled in a recent Threat Insight blog.
Throughout Q3, actors also favored URL-based malware distribution over the document attachment campaigns that have dominated the email threat landscape since late 2014. At the same time, we continued to observe evolving social engineering and targeting techniques in email fraud and in BEC attacks that did not use any malware payloads at all.
Social media remained fruitful territory for threat actors, who increased their presence in support fraud accounts used for so-called “angler phishing” while our first public report on lookalike domains registered for Fortune 50 brands showed suspicious domain registrations far outpacing defensive registrations by brand owners.
Here are key takeaways from this quarter’s Proofpoint Threat Report:
Malicious email volume soared in Q3, increasing 85% from the prior quarter. Much of this increase was driven by an explosion of email with malicious URLs linking to hosted malware, the volume of which rose 600% from the previous quarter and more than 2,200% from the year-ago quarter. This represents the highest proportion of malicious URL messages (compared to attachment-based email attacks) that we have seen since 2014. However, attachment campaigns were still very present, with malware hidden in compressed-file archive attachments comprising much of the volume in these campaigns.
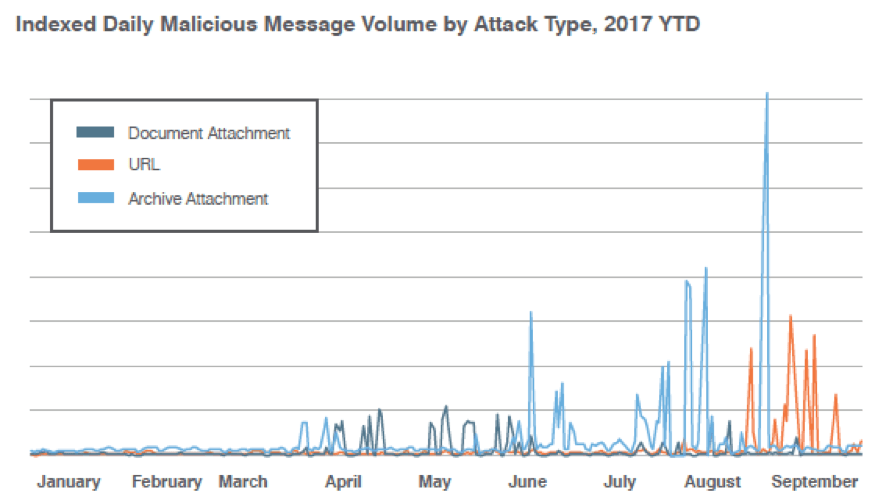
Figure 1: Year-to-date indexed attack types
Across our global customer base, ransomware appeared in almost 64% of all malicious email. New ransomware strains appeared daily, but Locky remained the top payload, both in terms of ransomware and across all malware families.
Banking Trojans, on the other hand, represented 24% of all malicious email volume, with The Trick accounting for 70% of banking Trojan payloads and displacing Dridex as the top banker in Q3. Dridex—along with Ursnif, Bancos, and Zloader—continued in regionally focused campaigns. A new version of Retefe also appeared using a leaked exploit from the U.S. National Security Agency known as EternalBlue to spread across internal networks, echoing the use of NSA exploits in destructive ransomware attacks from Q2.
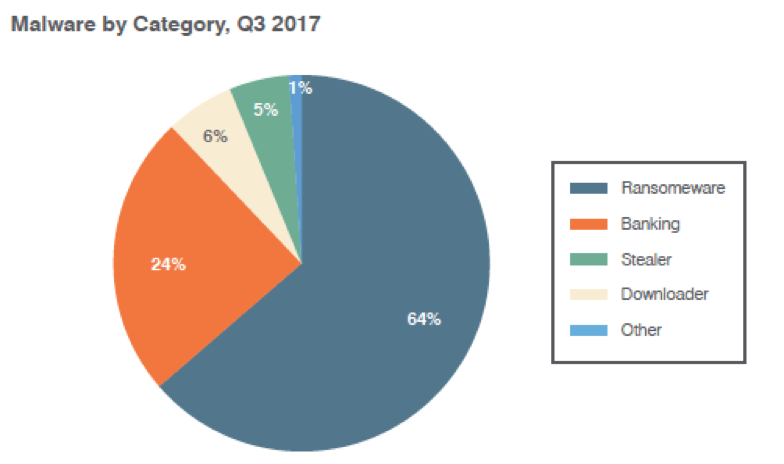
Figure 2: Malware payloads by category during Q3
Email fraud rose 29% versus the previous quarter, while attack frequency also increased, with 12% more email fraud attempts per targeted organization than in Q2.
Exploit Kits And Web-based Attacks
Exploit kits (EKs) suffered a well-publicized decline in 2016 and we continue to observe traffic levels hovering around 10% of their 2016 peak. However, attackers are layering social engineering schemes into their EK campaigns, a trend suggesting they are looking beyond increasingly scarce exploits to monetize EK activity.
Threat actors continue to make use of lookalike and typosquatted “suspicious domains” to perpetrate fraud and trick unsuspecting users. Registrations of suspicious domains outnumbered defensive registrations by brand owners 20 to 1 in Q3.
At the same time, fraudulent support accounts, used for so-called “angler phishing,” doubled from the year-ago quarter as actors continue to capitalize on social engineering across the threat landscape.
Proofpoint Recommendations
This report provides insight into the shifting threat landscape that can inform your cybersecurity strategy. Here are our top recommendations for how you can protect your data, people, and brand in the coming months.
Combat typosquatting on the web
Defensive domain registration is a simple and cost-effective tactic to keep attackers from creating lookalike domains for email fraud and credential phishing. Work with your business leaders to define a list of potential look-alike domains to register. Include conference and marketing campaign websites, which are frequent targets.
Deploy email authentication to stop domain spoofing techniques used in email fraud
With protocols such as DMARC (Domain-based Message Authentication, Reporting & Conformance), you can stop fraudsters from using your email domain. For email attacks that use lookalike domains, your solution should be able to find domains that could be mistaken for yours—and work with third-party services to take them down.
Protect your users from email attacks of all types
Whether they’re malware attachments, malicious URLs or socially engineered email fraud, your email defenses should cover the widest range of email-based threats. Robust protection includes robust analysis capabilities to preemptively identify and sandbox suspicious URLs and attachments. It should use multistage sandbox analysis to identify malicious attachments and URLs—at the delivery point and later when employees click. And it should identify and block non-malware threats, such as emails that could trick your employees from sending money and sensitive information to impostors.
Partner with a threat intelligence vendor
Smaller, more targeted attacks call for sophisticated threat intelligence. Leverage a solution that brings together analysis data with threat intelligence, combines static and dynamic techniques to detect new attack tools, tactics, and targets—and then learns from them. By correlating analysis results with threat intelligence feeds, these difficult-to-detect emails can be caught before a user has a chance to click.
Protect your brand from impostors on social media
Look for a security solution that alerts you to lookalike social media accounts, especially those offering fraudulent “customer-support” services. The solution should not just detect infringing accounts but work with takedown services to stop them from defrauding your customers and partners.
For more details about Q3 threats and trends, download the full report.

