Proofpoint researchers have been tracking the dramatic decline in exploit kit (EK) activity since early 2016. Once a source of considerable angst for web surfers worldwide, EKs delivered “drive-by downloads” and fueled malvertising at massive scale for years. As EKs increased in sophistication, users often had only to visit a compromised website or a page displaying a malicious advertisement to find themselves infected with malware delivered by one of several high-profile exploit kits. By May of 2016, however, EK activity had dropped by 94% from January highs. Activity rebounded slightly later in the year, but even in the first quarter of 2017, remained steady at roughly 10% of what we observed early last year.
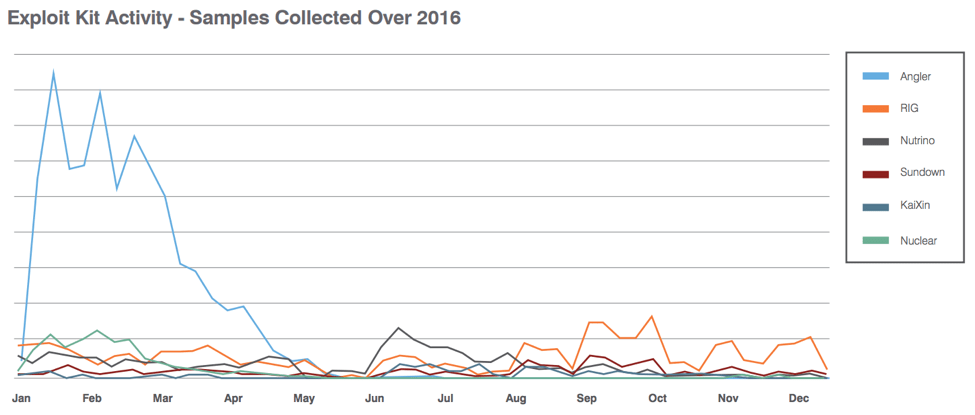
Figure 1: Exploit kit activity throughout 2016
The reasons for this decrease are manifold: the high-profile arrest of actors connected to Angler exploit kit, the most popular and widespread EK for much of the first half of 2016, certainly contributed significantly. However, in most areas of cybercrime, the disappearance of one actor generally leaves a vacuum filled by other actors. In this case, we saw some moderate increases in RIG and Neutrino, but activity overall has remained low.
A more significant reason for the decline in EK activity is that exploitable vulnerabilities are aging quickly. The most effective exploits are based on zero-day vulnerabilities, infecting the most victims in the days before patches become available and in the period shortly thereafter, before they have been widely applied by potential victims. Fewer zero-days, of course, mean fewer opportunities to infect large numbers of users. Moreover, as more websites phase out vulnerable media platforms like Flash, Silverlight, and Java and both browser and operating system vendors issue patches more rapidly, threat actors must invest much more time and effort identifying and exploiting vulnerabilities.
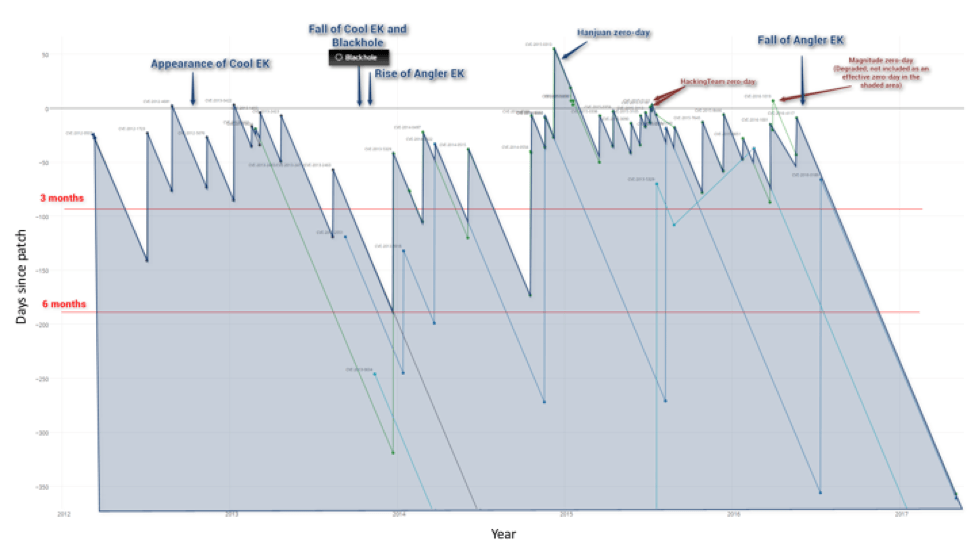
Figure 2 tracks major vulnerabilities in Internet Explorer, Flash, Java, and Silverlight over the last five years. Each spike is a new vulnerability labeled with its CVE identifier. Those spikes that rise above the 0 gridline represent exploited zero-days - positive numbers on the y-axis show how many days will pass before a patch becomes available. Negative numbers show how many days have passed after the patch was released, but unpatched computers remain vulnerable.
Figure 2: Graph of vulnerabilities vs. days-since-patch; positive numbers depict true, exploited zero-days.
Looking more closely at Figure 2, note that many of the vulnerabilities aren’t exploited in EKs until after a patch is available -- as depicted here, their spike never crosses the 0 gridline. In the past, it was quite common for PCs to go weeks or months without updates, such that the occurrence of a true zero-day was not necessary to infect large numbers of PCs. EK operators only had to implement exploits within generally lengthy patching windows.
The red lines in Figure 2, labeled “3 months” and “6 months” show common patching windows. Vulnerabilities with spikes above the “3 month” line show that any PCs not updated within three months are vulnerable to infection by the associated exploit. Viewed from this perspective, we can see why 2015 represented the recent peak of EK activity: a regular flow of exploits in the wild close to or even before patches became available created an vital condition for success for exploit kits.
Friday, May 12, was the one-year anniversary of the last patch associated with a vulnerability used in an EK. In this case, CVE-2016-4117, a Flash vulnerability, was patched on May 12, 2016. That one-year anniversary means that virtually any computer fully updated within the last year will not be vulnerable to commercial EKs.
While there are many computers, particularly consumer PCs, that are not regularly updated and are therefore vulnerable, when it comes to exploit-based attacks this is the safest time in several years to browse the open web. This also explains why many EKs are more effective in regions where software piracy is common since unlicensed versions of Windows do not receive regular updates.
Unfortunately, we are aware of upticks in activity among some EK operators, suggesting that actors are again beginning the hard work of finding and exploiting new vulnerabilities. The Astrum exploit kit in particular, which was used extensively in the massive AdGholas malvertising campaigns, has introduced new filtering methods and has recently begun abusing the Diffie-Hellman key exchange algorithm to deter analysis. We have also seen social engineering make its way into the EK space, reducing the reliance on increasingly rare zero-days.
However, the rapid aging of EKs and web-based exploits has also increased the emphasis on social engineering in email-based threats, social media, and mobile malware. Threat actors have shown remarkable adaptability and always follow the money. When one activity is no longer lucrative, they move elsewhere. Exploiting humans through social engineering has proven far more effective recently than exploiting systems through browser vulnerabilities.