"Verified accounts" are a powerful tool on Twitter to help brands differentiate themselves from fraudulent, impersonation, and parody accounts on the social media site. When an account is officially verified, it displays a special badge intended to reassure Twitter users that they are interacting with a genuine brand and not an impostor. Recently, however, threat actors are using the promise of verified accounts to lure users into a credit card phishing scheme.
Account verification is a process that Twitter manages for "accounts of public interest" and requires brands to go through multiple verification steps. The promise, then, of a quick verification process is attractive, especially to smaller businesses that potentially lack the resources to meet Twitter's requirements for account verification. In this phishing attack, discovered by Proofpoint researchers in December, attackers place legitimate ads targeting brand managers and influencers with a link to a phishing site purporting to offer account verification.
The ads themselves come from an account that mimics the official Twitter support account, @support. The fraudulent account, @SupportForAll6, uses Twitter branding, logos, colors, etc., to increase the sense of authenticity, despite a very low number of followers and a suspect name.
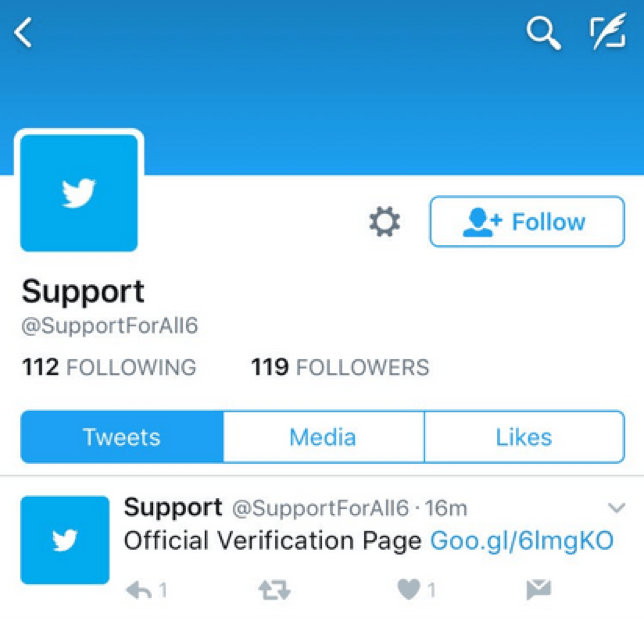
Figure 1: Fraudulent support account used to run the phishing scheme
A key element of this scam is the use of Twitter-sponsored advertisements, which appear in user feeds without any interaction, need to follow, or direct messaging requirement. One such advertisement with a link to the phishing site appears at the bottom of the fraudulent profile in Figure 1.
After clicking the link, users find themselves taken to a domain titled twitterhelp[.]info. The domain name should be a red flag, but otherwise appears legitimate. The page itself also mimics Twitter with color schemes and wording matching that of the official site.
![Fraudulent 'Twitter verification' phishing site at lookalike domain twitterhelp[.]info](/sites/default/files/twitter-2.png)
Figure 2: Fraudulent "Twitter verification" phishing site at lookalike domain twitterhelp[.]info
The domain twitterhelp[.]info was registered on December 13. Although the registration is private, we found that the URL resolves to an IP address previously used for phishing activities.
When users follow the process started in the form shown in Figure 2, a new form appears asking for a variety of personal information including the Twitter username, email address, phone number, and, most importantly, the account password.
After a user provides this information, they are met with another form asking for a credit card number and security code for “verification purposes”. The form states that the user will not be charged for this process but the form includes a template for extracting payment information lifted from Github (Figure 3). While there is no validation on the form asking for account information, allowing users to submit empty values, this is not the case with the financial information; this cannot be submitted without providing the requested credit card information.
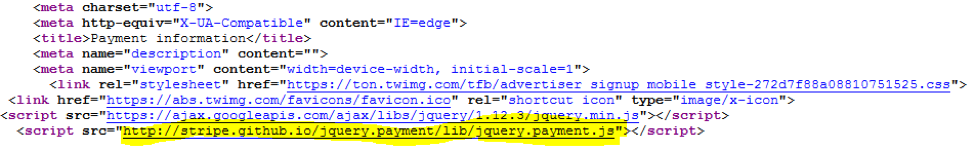
Figure 3: Phishing form using a payment template loaded from Github
Finally, users are thanked and reassured they will receive an email shortly with verification details. They are then redirected to the official twitter.com domain, extending the ruse by further reinforcing the apparent legitimacy of the process.
This scheme, though not especially sophisticated technically, is an excellent example of how attackers are combining traditional phishing methods, social engineering, and social impersonation to ultimately make money in new ways. And while we observed this attack on Twitter, such a scam could be run on any social media platform that implements some form of account verification.
We contacted Twitter with details about this attack.











